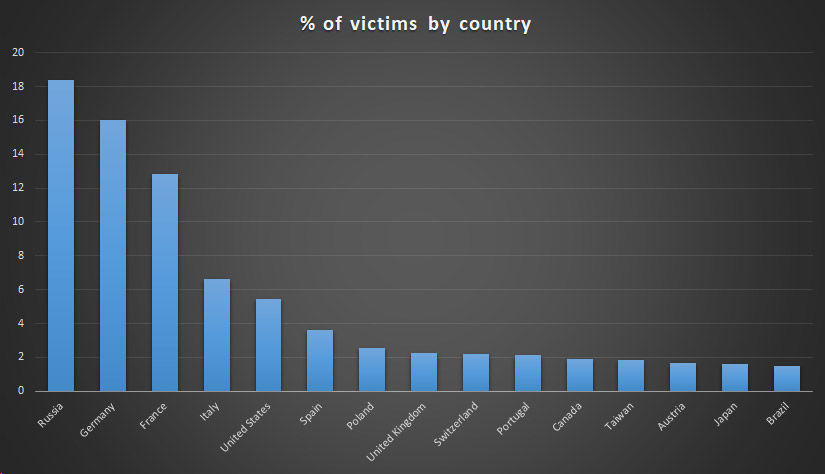
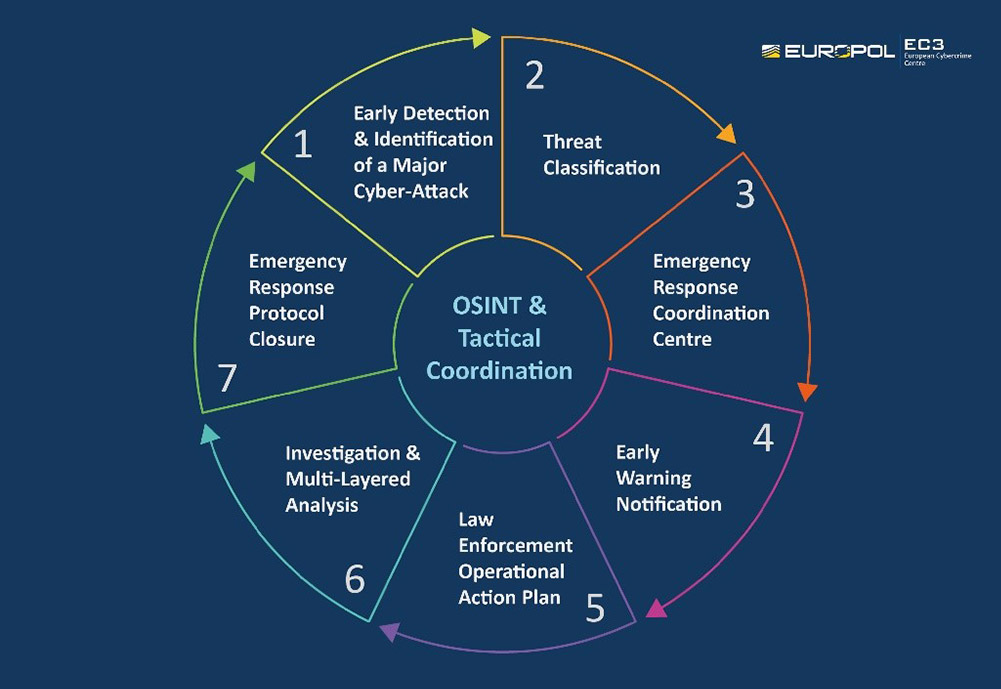
Commonwealth Bank and Westpac cautious on using AI for compliance

"Regtech is at an early stage in its life cycle, but we are trying to get it mature, make it understood and get it linked into the strategic core – that is a big focus for us," Ms Cooper said. At the regtech event, a key frustration from start-ups was the time it took for new, outside technology to be considered by the ultimate decision-makers. "It's extremely hard. I've probably been in Westpac's building 30 times in the last year and a half or so," said SimpleKYC founder Eric Frost, whose system is being used by American Express to reduce customer on-boarding times. Neither he nor Westpac said they could disclose whether Westpac had started using the system. Ms Cooper said Westpac's senior management was encouraging collaboration with start-ups, but at the same time, compliance was an area where there was little room for failure. "There is a very strong strategic focus, right form the top, on partnering, not sitting in our ivory tower thinking we can build it ourselves, which creates the conditions for us to do things like 'minimum viable procurement'," she said.
The point is that you need a lot of quarters. You can’t rely on one of anything. Big dreams start with money because it’s measurable. Your parents told you to be reasonable, to play it safe. Rich people do not say "money is not everything." Don’t be a victim. Don’t appoint blame to anyone other than yourself. Quit making excuses. Get your heart in the deal all the time. Have enough so that nothing can stop you. Embrace this thing called sales. Every business I ever started was built on making sales. No sales equal no business. You don’t need therapy, you need to take action. You don’t need to write a business plan or organize your address book. Without money coming in you’re dead in the water. The healing is in the doing, not the thinking. Sales is about doing. It’s the ask, the follow-up. Were you told not to be too persistent when you were a kid? Money doesn’t grow on trees is code for I don’t know how to bring money in. Replace the excuses with the truth. The truth is you’re lost when it comes to income.
Wiring financial organisations for regulatory success
Technology can help tie regulations to internal processes. Structured data sets mean that it’s possible to connect the dots between policies/procedures and processes, systems, controls and products and services through structured content and ML tagging. A clear link to the broader risk-management framework, governance, and processes is necessary at all levels of the hierarchy, across both large and small companies. No longer is this something presented as a futuristic view at conferences and industry events, but a new reality which regtech is bringing to life. With the use of technology, a huge amount of data that offers significant insight into risk can be captured for evidencing and provided to regulators in a detailed structured format that is easy to understand. Needless to say, such a technology-driven holistic structured approach to data is fast becoming the only viable way to successfully manage policies and stay compliant in the current regulatory landscape.
How Insurers Can Tackle Cyber Threats in the Digital Age

Persistent knowledge gaps hinder the creation of effective cybersecurity cultures. Human error accounts for a significant share of cyber breaches, with phishing schemes alone is responsible for three quarters of malware hitting organizations globally, according to NTT Data. And while there’s broad recognition that cyber-attacks pose a major threat to organizations, there’s a stark divide between IT professionals and corporate leadership regarding the effectiveness of organizational protocols. In one survey, 59 percent of corporate board members said that their organizations’ cybersecurity governance practices were very effective, while only 18 percent of IT professionals agreed. Insurers can work with their clients to achieve a unified understanding of cybersecurity policies and terms. When all stakeholders operate according to a standardized cybersecurity framework, organizations can better manage risk, understand their vulnerabilities, respond to emerging threats and contain the fall-out of breaches.
30+ Powerful Artificial Intelligence Examples you Need to Know
Trading algorithms are already used successfully in world’s markets recognizing the staggering speed with which computer systems have transformed stock trading. Even though automation rules the trading world, the most complex algorithms use basic AI reasoning. Machine learning is poised to change the tradition by putting emphasis on making the decision more hard-data based and lesser grounded on trading theories. While humans will always play a role in regulation and for making the final decisions- more and more financial transactions are making their way to computer systems. Plus, given the competitive nature of this field, investment in AI and machine learning will be one of the most defining aspects of the field. Luckily, these technologies have the potential to stabilize and not disrupt, the financial industry- therefore resulting in better job stability (even reducing the probability of market crashes).
Why a Digital Mindset Is Key to Digital Transformation

While infrastructure and technology are clearly important considerations, digital transformation is as much about the people and changing the way they approach business problems and where they look to find solutions. In fact, according to Gartner research analyst Aashish Gupta, many organizations forget to address the necessary cultural shift needed to change the mindset of workers, without which no digital transformation project is going to succeed. "The culture aspect and the technology demand equal attention from the application leader, because culture will form the backbone of all change initiatives for their digital business transformation. Staff trapped in a 'fixed' mindset may slow down or, worse, derail the digital business transformation initiatives of the company,” he said in a statement. To encourage a change in mindset from traditional to digital, Gartner has developed a four-step plan which it outlines in its report "Digital Business Requires a New Mindset, Not Just New Technology," due to be released soon.
The new third-party oversight framework: Trust but verify
There is a need to identify risk at different points in the third-party life cycle: at the commencement of the relationship, and on a regular basis thereafter, based on a number of factors that influence the risk the third party generates, such as privacy, regulatory compliance, business continuity planning, and information security. However, there also needs to be an early warning system that can alert management to a potential increase of risk outside of these scheduled assessments. This is where the link to risk appetite, key performance, and risk indicators comes into play. The risk oversight functions need to work together to build a set of factors that can assess the inherent risk associated with an activity plus any increase in risk associated with outsourcing the activity to a third party, the mitigating effect of existing measures employed by the institution and the third party to control that risk, and the determining of the remaining risk,or residual risk that the institution continues to bear.
What data dominance really means, and how countries can compete

A lot of the current debate approaches data from the supply side, asking about ownership and privacy. These are no doubt important questions. But countries need to think deeply about the demand side: are they growing local industries that will make use of data? If not, they will find themselves forever exporting raw data and importing expensive digital services. People say data is like oil. But it isn’t, really. For one thing, data isn’t “fungible”: you can’t swap one piece of information for something else. Knowing my Amazon purchase history won’t help a self-driving car identify a stop sign. This is true even when data is the exact same type: my browsing history may not be as valuable as yours. This non-fungible nature shows up in my estimations of Facebook’s average monthly revenue-per-user, which shows that the average Canadian user generates 100 times more revenue than the average Ethiopian user.
5 Ways Marketers Can Gain an Edge With Machine Learning

In the past -- and occasionally today -- these recommendations were manually curated by a human. For the past 10 years, they have often been driven by simple algorithms that display recommendations based on what other visitors have viewed or purchased. Machine learning can deliver substantial improvements over these simple algorithms. Machine learning can synthesize all the information you have available about a person, such as his past purchases, current web behavior, email interactions, location, industry, demographics, etc., to determine his interests and pick the best products or the most relevant content. Machine learning-driven recommendations learn which items or item attributes, styles, categories, price points, etc., are most relevant to each particular person based on his engagement with the recommendations -- so the algorithms keep improving over time. And machine learning-driven recommendations are not limited to products and content. You can recommend anything -- categories, brands, topics, authors, reviews vs. tech specs etc.
Why DevOps Fails: Some Key Reasons To Consider
It is important to know why culture is important. Culture is a set of practices, standards, beliefs, and structure that reinforce the organizational structure. DevOps is not only a set of tools; you must create a culture of DevOps in your organization to get the results you seek. A U.S. government agency that adopted DevOps for continuous deployment failed to identify the importance of people and process, which led to misconduct and confusion among developers and key people. ... every organization is a technology-driven organization regardless of the domains. The journey from digital transformation to continuous digital journey demanded flexibility, agility, and quality as most-focused aspects. DevOps has become a need for organizations that are associated with software delivery or often releasing an update or new features in order to serve their customers with quality and superiority. There is no doubt that DevOps can make software development faster, but every organization has a different set of requirements, and each company's DevOps adoption must be tailored to that set of requirements.
Quote for the day:
"Leadership is the other side of the coin of loneliness, and he who is a leader must always act alone. And acting alone, accept everything alone." -- Ferdinand Marcos