Service Brokering & Enterprise Standard - Build Your Competitive Advantage In The Digital World
Implementing service brokering within an organization requires a fundamental change in culture as the focus needs to evolve from function/technology to service and service delivery. Rather than silos focused around technologies, the organization should rally around teamwork to deliver each service in an optimal way as the broker is central in the integration process between provider and consumer. This is the most difficult aspect when implementing brokering. Changing the way people work, evolving their behaviors to be more user focused takes time. Unfortunately, IT departments have no choice, either they are able to deliver the services required by the users through the supply chain they have developed or they will focus on managing the legacy environments, which may not be seen as a very exciting job. Multiple service use cases are documented in the guide. For each of them the roles and responsibilities of each of the players differ, but efficient service delivery can only be assured if the providers work smoothly and transparently together.
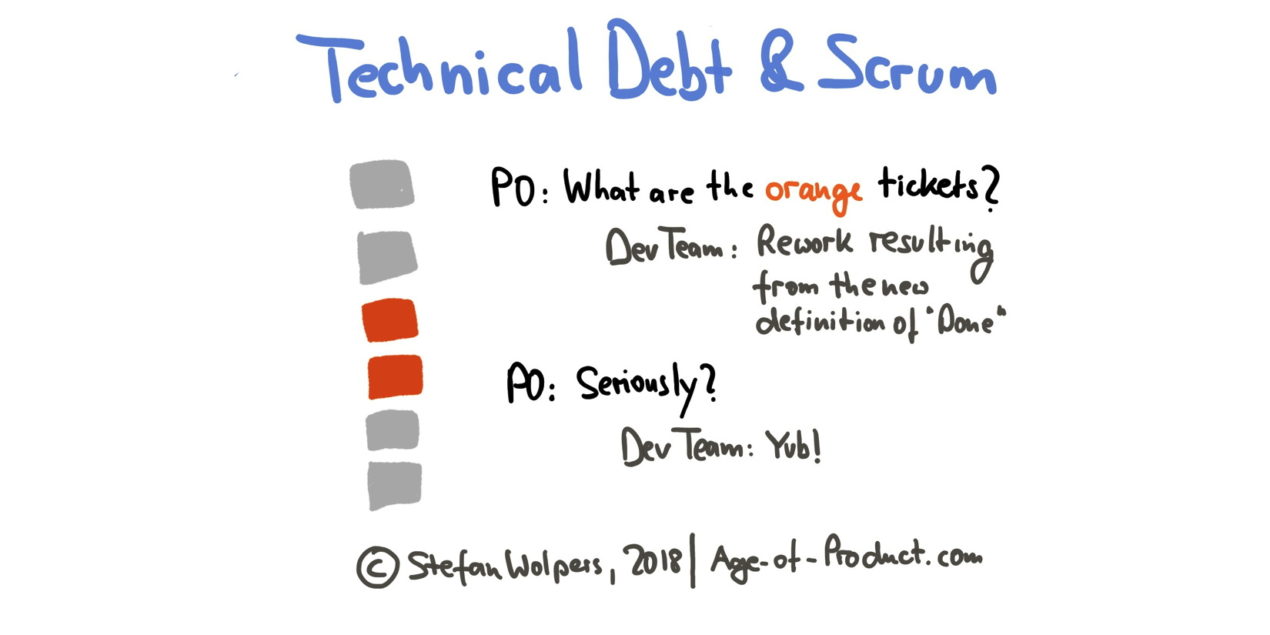
Technical Debt and Scrum: Who Is Responsible?
The issue is that there is not just the typical hack, the technical shortcut that is beneficial today, but expensive tomorrow that creates technical debt. (A not uncommon tactic in feature factories.) There is also a kind of technical debt that is passively created when the Scrum Team learns more about the problem it is trying to solve. Today, the Development Team might prefer a different solution by comparison to the one the team implemented just six months ago. Or perhaps the Development Team upgrades the definition of “Done,” thus introducing rework in former product Increments. No matter from what angle you look at the problem, you cannot escape it, and Scrum does not offer a silver bullet either. ... the Scrum Guide is deliberately vague on the question of who is responsible for the technical debt to foster collaboration and self-organization, starting with the Scrum values — courage, and openness come to mind — leading straight to transparency and Scrum’s inherent system of checks and balances.

Cybersecurity is an attractive career for ambitious people and a great way to make the world a better place. If you want a career in cybersecurity, don’t wait. You don’t need to be of a particular age or gender. You don’t need any particular approval or certification or study place to get going. Just start learning and start doing. Get involved any way you can. Bug bounties is a great way to learn and test your skills. Check out Hacker101. Just know that even if you can jump straight in, you will need skill, tenacity and patience to ultimately reach a rewarding level of proficiency. Bug hunters may need a year or two of learning before the start finding security vulnerabilities worth reporting. Most bug hunters study the Hacktivity feed where vulnerability reports are published once the vulnerability has been fixed. Also note that to go far and to become a technical expert on cybersecurity, a lot of studying will be needed. What you invest in learning will come back as career opportunity. A degree in Computer Science will not hurt.
Three Steps to Regain Control over your IT Landscape
Most IT landscapes of larger companies consist of hundreds of applications that are interconnected via poorly designed interfaces. In most companies, these IT landscapes already have an enormous technical debt (i.e., an ‘unnecessary complexity’). In my experience, a company typically runs between 80% and 90% more IT applications (and therefore also servers, databases, networks, costs) compared to what would be needed if it had implemented the ideal architecture. A tremendous waste of money and resources, and the reason why IT is perceived as tardy and as a cost factor and not as an enabler. From my point of view, there are three major reasons for this disastrous situation ... There is a tendency to blame the IT department for this situation, but that’s not true. It’s a business problem. Requirements are typically not consolidated well across departments. IT has always just been the contractor who had to implement those punctual requirements under time pressure.
Like Football, Your Cybersecurity Defense Needs a Strong Offense

Today, it’s essential to not only build the strongest possible defenses but also to deploy creative strategies to gain information on your attackers and how they are trying to breach your networks and penetrate your systems. This idea that “the best defense is a good offense” is not just a slogan representing the conventional wisdom of the cybersecurity intelligentsia. ... In “The Future of Cybersecurity: The Best Defense Is a Good Offense,” the company speaks directly to all organizations when it waves the following red flag: With the sophisticated techniques threat actors are using to mask their activities, the traditional approach of ‘building bigger fences’ will no longer suffice. The only way organizations can protect themselves is by unleashing offensive cyber techniques to uncover advanced adversaries on their networks. As an example of what going on the offensive might look like, one strategy the company uses is to configure fake computers in a phony, intentionally vulnerable network that functions as “a virtual mousetrap” to lure cyber adversaries; when the hackers bust in, they reveal valuable information about their identities, tactics and intentions.
Cybersecurity: Don’t let the small stuff cause you big problems
Organisations of all sizes in all sectors need to have a cybersecurity strategy, but for healthcare, it's particularly important. Not only do IT networks within hospitals and doctors' surgeries need to be accessible and secure in order to provide patient care, these networks involve medical information – some of the most sensitive data that can be held about people. "What's really important is having control over the data and knowing where it is. It's the same issue that's dealt with in many other industries, but to an extra level of duty of care for the people whose data you've got," said Sian John, chief security advisor for EMEA at Microsoft. "You're talking about privacy: it's one level when you're talking about financial data, it's another level if that's my medical history," she added. What's important for health organisations as a whole is being absolutely sure how data is controlled and how it is accessed – and making knowing a priority.
Some Cybersecurity Vendors Are Resorting To Lies & Blackmail

It’s hard for cybersecurity companies to get noticed. Smaller vendors particularly struggle because top corporations already have contracts or strong customer relationships with the biggest companies. This is where the threat of negative media coverage comes in. Exposing a security flaw, no matter how small, can garner big headlines if it’s at a big company. Enough press coverage can spark weeks of outrage and land top leaders in front of Congress. However, breaches that actually cause damage are relatively rare. As a result, vendors often try to make a big deal out of minor breaches that don’t expose important company or customer information. For instance, all four executives said vendors tried to draw their attention to potentially exposed data on Amazon and Microsoft Azure cloud servers. None of this data included any current material information. In one case, a database housed business plans for a 10-year-old project that had already been reported on and was now irrelevant. In another case, the data included information about customers — but only their names and the fact that they had attended a technology conference several years earlier.
When Scrum Is Not The Right Answer
As organizations have bought into adopting an Agile approach to software development, I've noticed that one corporation's identification with terms like Agile or Scrum may differ from another's. Almost as if they are deciding how they wish to utilize Agile concepts to best meet the needs of their teams. I am really okay with this approach, as I noted in the article, "Agile For the Sake of Being Agile." But, what if Agile or Scrum is not the right answer at all? ... While the flow is certainly more Kanban than anything else, the goal is to keep the flow of work moving forward. Tickets pushed back to the to-do column would not need to go back to the original developer, but could be handled by any other developer, since the code has since been merged. An alternate flow could be that the REVIEW and TEST columns are swapped, delaying the merge until after testing has completed — but that was not suggested initially, since in order to keep the flow of working moving as quickly as possible. After all, the key is to meet the aggressive deadline.

Keep in mind, a cloud move is not as simple as downloading new software. It’s an entirely new and different ecosystem, one that involves a list of risks: legal, financial, commercial, and compliance, to name a few. To make such a move without stopping long enough to become informed of the dangers is not a good idea. It’s also not as simple as learning which vulnerabilities and threats are sitting out there at any particular moment in time. Threats evolve over time. Old ones become less effective or fall out of favor with hackers and new ones emerge. ... The problem is that you don’t have direct access to see where your data is stored and verify that deleted data has actually been deleted. To a large extent, you have to take it on faith that your CSP does what it says. Consider the structure of the cloud. There’s a good chance your data is spread over several different devices and in different physical locations for redundancy. Further, the actual deletion process is not the same among providers.
Why We Are Making Things so Complicated
There are many reasons: First, Joseph is dealing with the laws of physics – in a brilliant way I should add. In the virtual world of software-based solutions, such laws don’t apply. Furthermore, I suspect that Joseph had to go to a dozen stores to buy all this apparatus and spend a lot of time finding the right gizmos to fit his process. In software-based solutions, you just click, download it, resize it, or copy and paste it ad infinitum if you wish. It is usually simple, often effortless. It can also go in all directions, augment the overall complexity, but still your IT staff will find a way to make it work. In other words, the drawback of computer-based solutions is that it is easy to “clog your kitchen” as in the video. Second, after Joseph is done with video-making, he cleans the kitchen before the in-laws come for dinner. Your IT-based solutions support your business and they stay there as long as you’re operating. As easy as it is to fill the kitchen with software-based components, it is proportionately as difficult to empty the room – unless it was planned for.
Quote for the day:
"Brilliant strategy is the best route to desirable ends with available means." -- Max McKeown

No comments:
Post a Comment