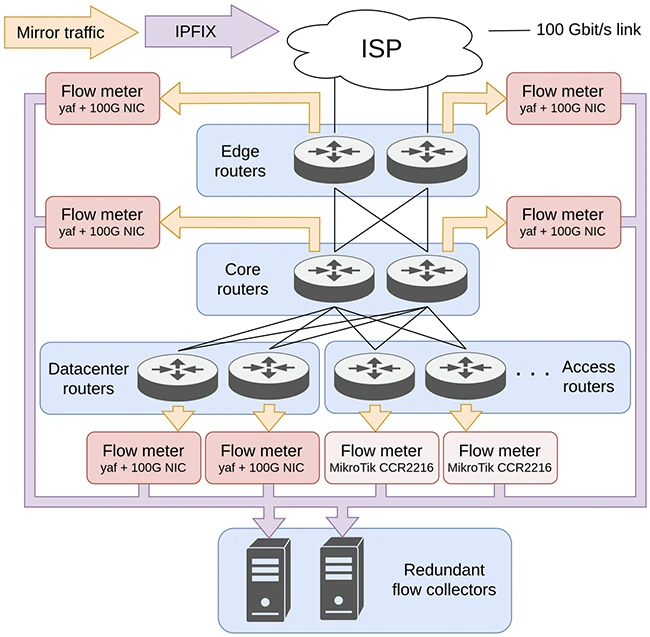
Quote for the day:
"Let no feeling of discouragement prey upon you, and in the end you are sure to succeed." -- Abraham Lincoln
Coding With AI Assistants: Faster Performance, Bigger Flaws
 One challenge comes in the form of how AI coding assistants tend to package
their code. Rather than delivering bite-size pieces, they generally deliver
larger code pull requests for porting into the main project repository. Apiiro
saw AI code assistants deliver three to four times as many code commits -
meaning changes to a code repository - than non-AI code assistants, but
packaging fewer pull requests. The problem is that larger PRs are inherently
riskier and more time-consuming to verify. "Bigger, multi-touch PRs slow review,
dilute reviewer attention and raise the odds that a subtle break slips through,"
said Itay Nussbaum, a product manager at Apiiro. ... At the same time, the tools
generated deeper problems, in the form of a 150% increase in architectural flaws
and an 300% increase in privilege issues. "These are the kinds of issues
scanners miss and reviewers struggle to spot - broken auth flows, insecure
designs, systemic weaknesses," Nussbaum said. "In other words, AI is fixing the
typos but creating the time bombs." The tools also have a greater tendency to
leak cloud credentials. "Our analysis found that AI-assisted developers exposed
Azure service principals and storage access keys nearly twice as often as their
non-AI peers," Nussbaum said. "Unlike a bug that can be caught in testing, a
leaked key is live access: an immediate path into the production cloud
infrastructure."
One challenge comes in the form of how AI coding assistants tend to package
their code. Rather than delivering bite-size pieces, they generally deliver
larger code pull requests for porting into the main project repository. Apiiro
saw AI code assistants deliver three to four times as many code commits -
meaning changes to a code repository - than non-AI code assistants, but
packaging fewer pull requests. The problem is that larger PRs are inherently
riskier and more time-consuming to verify. "Bigger, multi-touch PRs slow review,
dilute reviewer attention and raise the odds that a subtle break slips through,"
said Itay Nussbaum, a product manager at Apiiro. ... At the same time, the tools
generated deeper problems, in the form of a 150% increase in architectural flaws
and an 300% increase in privilege issues. "These are the kinds of issues
scanners miss and reviewers struggle to spot - broken auth flows, insecure
designs, systemic weaknesses," Nussbaum said. "In other words, AI is fixing the
typos but creating the time bombs." The tools also have a greater tendency to
leak cloud credentials. "Our analysis found that AI-assisted developers exposed
Azure service principals and storage access keys nearly twice as often as their
non-AI peers," Nussbaum said. "Unlike a bug that can be caught in testing, a
leaked key is live access: an immediate path into the production cloud
infrastructure."IT Leadership Is More Change Management Than Technical Management
Planning is considered critical in business to keep an organization moving forward in a predictable way, but Mahon doesn’t believe in the traditional annual and long-term planning in which lots of time is invested in creating the perfect plan which is then executed. “Never get too engaged in planning. You have a plan, but it’s pretty broad and open-ended. The North Star is very fuzzy, and it never gets to be a pinpoint [because] you need to focus on all the stuff that's going on around you,” says Mahon. “You should know exactly what you're going to do in the next two to three months. From three to six months out, you have a really good idea what you're going to do but be prepared to change. And from six to nine months or a year, [I wait until] we get three months away before I focus on it because tech and business needs change rapidly.” ... “The good ideas are mostly common knowledge. To be honest, I don’t think there are any good self-help books. Instead, I have a leadership coach who is also my mental health coach,” says Mahon. “Books try to get you to change who you are, and it doesn’t work. Be yourself. I have a leadership coach who points out my flaws, 90% of which I’m already aware of. His philosophy is don’t try to fix the flaw, address the flaw so, for example, I’m mindful about my tendency to speak too directly.”The Anatomy of SCREAM: A Perfect Storm in EA Cupboard
 SCREAM- Situational Chaotic Realities of Enterprise Architecture Management-
captures the current state of EA practice, where most organizations, from
medium to large complexity, struggle to derive optimal value from investments
in enterprise architecture capabilities. It’s the persistent legacy challenges
across technology stacks and ecosystems that need to be solved to meet
strategic business goals and those moments when sudden, ill-defined executive
needs are met with a hasty, reactive sprint, leading to a fractured and
ultimately paralyzing effect on the entire organization. ... The paradox is
that the very technologies offering solutions to business challenges are also
key sources of architectural chaos, further entrenching reactive SCREAM. As
noted, the inevitable chaos and fragmentation that emerge from continuous
technology additions lead to silos and escalating compatibility issues. ...
The chaos of SCREAM is not just an external force; it’s a product of our own
making. While we preach alignment to the business, we often get caught up
in our own storm in an EA cupboard. How often do we play EA on EA? ... While
pockets of recognizable EA wins may exist through effective engagement, a
true, repeatable value-add requires a seat at the strategic table. This means
“architecture-first” must evolve beyond being a mere buzzword or a token
effort, becoming a reliable approach that promotes collaborative success
rather than individual credit-grabbing.
SCREAM- Situational Chaotic Realities of Enterprise Architecture Management-
captures the current state of EA practice, where most organizations, from
medium to large complexity, struggle to derive optimal value from investments
in enterprise architecture capabilities. It’s the persistent legacy challenges
across technology stacks and ecosystems that need to be solved to meet
strategic business goals and those moments when sudden, ill-defined executive
needs are met with a hasty, reactive sprint, leading to a fractured and
ultimately paralyzing effect on the entire organization. ... The paradox is
that the very technologies offering solutions to business challenges are also
key sources of architectural chaos, further entrenching reactive SCREAM. As
noted, the inevitable chaos and fragmentation that emerge from continuous
technology additions lead to silos and escalating compatibility issues. ...
The chaos of SCREAM is not just an external force; it’s a product of our own
making. While we preach alignment to the business, we often get caught up
in our own storm in an EA cupboard. How often do we play EA on EA? ... While
pockets of recognizable EA wins may exist through effective engagement, a
true, repeatable value-add requires a seat at the strategic table. This means
“architecture-first” must evolve beyond being a mere buzzword or a token
effort, becoming a reliable approach that promotes collaborative success
rather than individual credit-grabbing.
How Does Network Security Handle AI?
 Detecting when AI models begin to vary and yield unusual results is the
province of AI specialists, users and possibly the IT applications staff. But
the network group still has a role in uncovering unexpected behavior. That
role includes: Properly securing all AI models and data repositories on the
network. Continuously monitoring all access points to the data and the AI
system. Regularly scanning for network viruses and any other cyber invaders
that might be lurking. ... both application and network teams need to ensure
strict QA principles across the entire project -- much like network
vulnerability testing. Develop as many adversarial prompt tests coming from as
many different directions and perspectives as you can. Then try to break the
AI system in the same way a perpetrator would. Patch up any holes you find in
the process. ... Apply least privilege access to any AI resource on the
network and continually monitor network traffic. This philosophy should also
apply to those on the AI application side. Constrict the AI model being used
to the specific use cases for which it was intended. In this way, the AI
resource rejects any prompts not directly related to its purpose. ... Red
teaming is ethical hacking. In other words, deploy a team whose goal is to
probe and exploit the network in any way it can. The aim is to uncover any
network or AI vulnerability before a bad actor does the same.
Detecting when AI models begin to vary and yield unusual results is the
province of AI specialists, users and possibly the IT applications staff. But
the network group still has a role in uncovering unexpected behavior. That
role includes: Properly securing all AI models and data repositories on the
network. Continuously monitoring all access points to the data and the AI
system. Regularly scanning for network viruses and any other cyber invaders
that might be lurking. ... both application and network teams need to ensure
strict QA principles across the entire project -- much like network
vulnerability testing. Develop as many adversarial prompt tests coming from as
many different directions and perspectives as you can. Then try to break the
AI system in the same way a perpetrator would. Patch up any holes you find in
the process. ... Apply least privilege access to any AI resource on the
network and continually monitor network traffic. This philosophy should also
apply to those on the AI application side. Constrict the AI model being used
to the specific use cases for which it was intended. In this way, the AI
resource rejects any prompts not directly related to its purpose. ... Red
teaming is ethical hacking. In other words, deploy a team whose goal is to
probe and exploit the network in any way it can. The aim is to uncover any
network or AI vulnerability before a bad actor does the same.Lack of board access: The No. 1 factor for CISO dissatisfaction
 CISOs who don’t get access to the board are often buried within their
organizations. “There are a lot of companies that will hire at a director level
or even a senior manager level and call it a CISO. But they don’t have the
authority and scope to actually be able to execute what a CISO does,” says Nick
Kathmann, CISO at LogicGate. Instead of reporting directly to the board or CEO,
these CISOs will report to a CIO, CTO or other executive, despite the problems
that can arise in this type of reporting structure. CIOs and CTOs are often
tasked with implementing new technology. The CISO’s job is to identity risks and
ensure the organization is secure. “If the CIO doesn’t like those risks or
doesn’t want to do anything to fix those risks, they’ll essentially suppress
them [CISOs] as much as they can,” says Kathmann. ... Getting in front of
the board is one thing. Effectively communicating cybersecurity needs and
getting them met is another. It starts with forming relationships with C-suite
peers. Whether CISOs are still reporting up to another executive or not, they
need to understand their peers’ priorities and how cybersecurity can mesh with
those. “The CISO job is an executive job. As an executive, you rely completely
on your peer relationships. You can’t do anything as an executive in a vacuum,”
says Barrack. Working in collaboration, rather than contention, with other
executives can prepare CISOs to make the most of their time in front of the
board.
CISOs who don’t get access to the board are often buried within their
organizations. “There are a lot of companies that will hire at a director level
or even a senior manager level and call it a CISO. But they don’t have the
authority and scope to actually be able to execute what a CISO does,” says Nick
Kathmann, CISO at LogicGate. Instead of reporting directly to the board or CEO,
these CISOs will report to a CIO, CTO or other executive, despite the problems
that can arise in this type of reporting structure. CIOs and CTOs are often
tasked with implementing new technology. The CISO’s job is to identity risks and
ensure the organization is secure. “If the CIO doesn’t like those risks or
doesn’t want to do anything to fix those risks, they’ll essentially suppress
them [CISOs] as much as they can,” says Kathmann. ... Getting in front of
the board is one thing. Effectively communicating cybersecurity needs and
getting them met is another. It starts with forming relationships with C-suite
peers. Whether CISOs are still reporting up to another executive or not, they
need to understand their peers’ priorities and how cybersecurity can mesh with
those. “The CISO job is an executive job. As an executive, you rely completely
on your peer relationships. You can’t do anything as an executive in a vacuum,”
says Barrack. Working in collaboration, rather than contention, with other
executives can prepare CISOs to make the most of their time in front of the
board.From Vault Sprawl to Governance: How Modern DevOps Teams Can Solve the Multi-Cloud Secrets Management Nightmare
Every time an application is updated or a new service is deployed, one or multiple new identities are born. These NHIs include service accounts, CI/CD pipelines, containers, and other machine workloads, the running pieces of software that connect to other resources and systems to do work. Enterprises now commonly see 100 or more NHIs for every single human identity. And that number keeps growing. ... Fixing this problem is possible, but it requires an intentional strategy. The first step is creating a centralized inventory of all secrets. This includes secrets stored in vaults, embedded in code, or left exposed in CI/CD pipelines and environments. Orphaned and outdated secrets should be identified and removed. Next, organizations must shift left. Developers and DevOps teams require tools to detect secrets early, before they are committed to source control or merged into production. Educating teams and embedding detection into the development process significantly reduces accidental leaks. Governance must also include lifecycle mapping. Secrets should be enriched with metadata such as owner, creation date, usage frequency, and last rotation. Automated expiration and renewal policies help enforce consistency and reduce long-term risk. Contributions should be both product- and vendor-agnostic, focusing on market insights and thought leadership.Digital Public Infrastructure: The backbone of rural financial inclusion
 When combined, these infrastructures — UPI for payments, ONDC for commerce, AAs
for credit, CSCs for handholding support and broadband for connectivity form a
powerful ecosystem. Together, these enable a farmer to sell beyond the village,
receive instant payment and leverage that income proof for a micro-loan, all
within a seamless digital journey. Adding to this, e-KYC ensures that identity
verification is quick, low-cost and paperless, while AePS provides last-mile
access to cash and banking services, ensuring inclusion even for those outside
the smartphone ecosystem. This integration reduces dependence on middlemen,
enhances transparency and fosters entrepreneurship. ... Of course,
progress does not mean perfection. There are challenges that must be addressed
with urgency and sensitivity. Many rural merchants hesitate to fully embrace
digital commerce due to uncertainties around Goods and Services Tax (GST)
compliance. Digital literacy, though improving, still varies widely,
particularly among older populations and women. Infrastructure costs such as
last-mile broadband and device affordability remain burdensome for small
operators. These are not reasons to slow down but opportunities to fine-tune
policy. Simplifying tax processes for micro-enterprises, investing in vernacular
digital literacy programmes, subsidising rural connectivity and embedding
financial education into community touchpoints such as CSCs will be essential to
ensure no one is left behind.
When combined, these infrastructures — UPI for payments, ONDC for commerce, AAs
for credit, CSCs for handholding support and broadband for connectivity form a
powerful ecosystem. Together, these enable a farmer to sell beyond the village,
receive instant payment and leverage that income proof for a micro-loan, all
within a seamless digital journey. Adding to this, e-KYC ensures that identity
verification is quick, low-cost and paperless, while AePS provides last-mile
access to cash and banking services, ensuring inclusion even for those outside
the smartphone ecosystem. This integration reduces dependence on middlemen,
enhances transparency and fosters entrepreneurship. ... Of course,
progress does not mean perfection. There are challenges that must be addressed
with urgency and sensitivity. Many rural merchants hesitate to fully embrace
digital commerce due to uncertainties around Goods and Services Tax (GST)
compliance. Digital literacy, though improving, still varies widely,
particularly among older populations and women. Infrastructure costs such as
last-mile broadband and device affordability remain burdensome for small
operators. These are not reasons to slow down but opportunities to fine-tune
policy. Simplifying tax processes for micro-enterprises, investing in vernacular
digital literacy programmes, subsidising rural connectivity and embedding
financial education into community touchpoints such as CSCs will be essential to
ensure no one is left behind.
Cybersecurity research is getting new ethics rules, here’s what you need to know
 Ethics analysis should not be treated as a one-time checklist. Stakeholder
concerns can shift as a project develops, and researchers may need to revisit
their analysis as they move from design to execution to publication.
...“Stakeholder ethical concerns impact academia, industry, and government,”
Kalu said. “Security teams should replace reflexive defensiveness with
structured collaboration: recognize good-faith research, provide intake channels
and SLAs, support coordinated disclosure and pre-publication briefings, and
engage on mitigation timelines. A balanced, invitational posture, rather than an
adversarial one, will reduce harm, speed remediation, and encourage researchers
to keep working on that project.” ... While the new requirements target academic
publishing, the ideas extend to industry practice. Security teams often face
similar dilemmas when deciding whether to disclose vulnerabilities, release
tools, or adopt new defensive methods. Thinking in terms of stakeholders
provides a way to weigh the benefits and risks of those decisions. ... Peng said
ethical standards should be understood as “scaffolds that empower thoughtful
research,” providing clarity and consistency without blocking exploration of
adversarial scenarios. “By building ethics into the process from the start and
revisiting it as research develops, we can both protect stakeholders and ensure
researchers can study the potential threats that adversaries, who face no such
constraints, may exploit,” she said.
Ethics analysis should not be treated as a one-time checklist. Stakeholder
concerns can shift as a project develops, and researchers may need to revisit
their analysis as they move from design to execution to publication.
...“Stakeholder ethical concerns impact academia, industry, and government,”
Kalu said. “Security teams should replace reflexive defensiveness with
structured collaboration: recognize good-faith research, provide intake channels
and SLAs, support coordinated disclosure and pre-publication briefings, and
engage on mitigation timelines. A balanced, invitational posture, rather than an
adversarial one, will reduce harm, speed remediation, and encourage researchers
to keep working on that project.” ... While the new requirements target academic
publishing, the ideas extend to industry practice. Security teams often face
similar dilemmas when deciding whether to disclose vulnerabilities, release
tools, or adopt new defensive methods. Thinking in terms of stakeholders
provides a way to weigh the benefits and risks of those decisions. ... Peng said
ethical standards should be understood as “scaffolds that empower thoughtful
research,” providing clarity and consistency without blocking exploration of
adversarial scenarios. “By building ethics into the process from the start and
revisiting it as research develops, we can both protect stakeholders and ensure
researchers can study the potential threats that adversaries, who face no such
constraints, may exploit,” she said.
From KYC to KYAI: Why ‘Algorithmic Transparency’ is Now Critical in Banking
 This growing push for transparency into AI models has introduced a new acronym
to the risk and compliance vernacular: KYAI, or "know your AI." Just like
finance institutions must know the important details about their customers, so
too must they understand the essential components of their AI models. The
imperative has evolved beyond simply knowing "who" to "how." Based on my work
helping large banks and other financial institutions integrate AI into their KYC
workflows over the last few years, I’ve seen what can happen when these teams
spend the time vetting their AI models and applying rigorous transparency
standards. And, I’ve seen what can happen when they become overly trusting of
black-box algorithms that deliver decisions based on opaque methods with no
ability to attribute accountability. The latter rarely ever ends up being the
cheapest or fastest way to produce meaningful results. ... The evolution from
KYC to KYAI is not merely driven by regulatory pressure; it reflects a
fundamental shift in how businesses operate today. Financial institutions that
invest in AI transparency will be equipped to build greater trust, reduce
operational risks, and maintain auditability without missing a step in
innovation. The transformation from black box AI to transparent, governable
systems represents one of the most significant operational challenges facing
financial institutions today.
This growing push for transparency into AI models has introduced a new acronym
to the risk and compliance vernacular: KYAI, or "know your AI." Just like
finance institutions must know the important details about their customers, so
too must they understand the essential components of their AI models. The
imperative has evolved beyond simply knowing "who" to "how." Based on my work
helping large banks and other financial institutions integrate AI into their KYC
workflows over the last few years, I’ve seen what can happen when these teams
spend the time vetting their AI models and applying rigorous transparency
standards. And, I’ve seen what can happen when they become overly trusting of
black-box algorithms that deliver decisions based on opaque methods with no
ability to attribute accountability. The latter rarely ever ends up being the
cheapest or fastest way to produce meaningful results. ... The evolution from
KYC to KYAI is not merely driven by regulatory pressure; it reflects a
fundamental shift in how businesses operate today. Financial institutions that
invest in AI transparency will be equipped to build greater trust, reduce
operational risks, and maintain auditability without missing a step in
innovation. The transformation from black box AI to transparent, governable
systems represents one of the most significant operational challenges facing
financial institutions today.







/articles/ai-infrastructure-aggregating-agentic-traffic/en/smallimage/ai-infrastructure-aggregating-agentic-traffic-thumbnail-1755682463373.jpg)