Firms urged to gear up for new malware and tactics as threats proliferate

As network defences increase in sophistication, so do the anonymity of attacks that now include the targeting of non-standard ports to ensure payloads are concealed upon delivery, the SonicWall researchers warned. Based on a sampling of more than 700 million malware attacks, SonicWall found that 19.2% of malware attacks used non-standard ports, up 8.7% compared with 2017. “The concern over security and privacy is more prevalent than ever before. Industry and government must collaborate to build a more secure environment, mitigate risk, and build citizen trust in government and consumer trust in business,” said Michael Chertoff, executive chairman and co-founder of The Chertoff Group, and former US secretary of homeland security. “This report provides critical analysis into the evolution of cyber adversaries’ threat tactics and methods. As organisations increasingly rely on metrics to understand and forecast risk, this intelligence will help enterprises and governments make informed decisions on their security investment.”
Maintaining security control in the age of the mobile workforce
The ability to do our jobs from outside the corporate walls keeps workers productive and helps businesses remain operational. Or in some cases, saves the organization travel fees – especially those caused by rescheduling or canceling hotels and airfare during inclement weather. Beyond the seasonal spikes, many organizations are adopting more flexible work policies. The number of U.S. mobile workers is expected to grow to 105.4 million, or more than 70 percent of the population, by 2020. The composition of the modern workforce is changing. Not to mention that, as an always-on society, we have a problem disconnecting. Fast forward from this brutal winter and 42 million people are expected to travel over Memorial Day weekend, with a majority of them still tethered to work communications on their devices. When only 11 percent of end users access business applications from the corporate office 100 percent of the time, the growth of the mobile workforce places a lot of strain on data security. Data now sits on endpoints spread around the globe.
'Operation ShadowHammer' Shows Weakness of Supply Chains
While the exact scope and purpose of installing these backdoors remains unclear, researchers say the APT group does appear to have targeted a very specific set of Asus PC users. These victims were identified through their MAC addresses. Specifically, the attackers hardcoded MAC addresses into the trojanized software samples recovered by Kaspersky Lab, which says this list was used to target specific machines and their users. Once the backdoor was installed on a victim's machine, it would signal back to a command-and-control server and then receive additional malware to plant in the PC, according to Vice Motherboard, which first reported the story. If the PC was not on the target list, the malware did not initiate a call to the C&C server. One reason why the operation continued for so long without being detected is that attackers used legitimate certificates, such as "AsusTeK Computer Inc.," as part of the trojanized updates, researchers say. The updater software was also hosted on legitimate domains.
Have we reached “peak” chief digital officer?

Our latest CDO study found that CDOs with a market-facing background had dropped to 18 percent, down from 39 percent two years ago, and that 41 percent of organizations had attracted CDOs with a solid technology background, up from 32 percent in 2016. And 28 percent had a strategy, business development, or consulting background — a surge from 2016, when just 21 percent had such credentials. Indeed, a key study finding was that a third of CDO positions saw turnover in 2018. This reflects the need for new skill sets and experience as digital transformation programs move beyond pilots in specific corners of the business to play a central part in everyday operations. Looking ahead, we think that as transformation becomes part of the core business, the next step will be for the CDO to disappear. Digital transformation will become the responsibility of every member of the executive team. We are not there yet. But where organizations have a CDO in place today, the priority should be to ensure that the person in this role still has the appropriate perspective and capabilities to move the digital transformation agenda forward, by embedding it both deeply within operations and at scale across the organization.
How blockchain is becoming the 5G of the payment industry

On the heels of JPMorgan Chase & Co. creating its own stable coin token for use on blockchain distributed ledgers, IBM last week launched its Blockchain World Wire, which will enable banks to transfer tokens and cryptocurrency in near-real time, cutting out banking intermediaries and lowering capital costs and clearing fees. The distributed ledger technology (DLT) network will initially enable cross-border payments and settlements based on the Stellar protocol, a decentralized payment network that uses its own cryptocurrency, Stellar Lumens (XLM). While the IBM network will support XLM, it will primarily use stable coin backed one-for-one by the U.S. dollar and other national currencies. In other words, IBM will run the blockchain infrastructure – the computer nodes and software – and the banks will transmit digital tokens tied to fiat currency over the network. The Rizal Commercial Banking Corporation (RCBC), one of the Philippines' top 10 banks by assets, will be among the first of four using the Blockchain World Wire for remittance payments services.
ProBeat: Google’s Stadia is all about the cloud and AI

The cloud conversation is straightforward. Stadia is a cloud gaming service, after all. But what about AI? The consumer-facing part is of course Google Assistant. Google is positioning YouTube as Stadia’s killer app, but Google Assistant also has a role to play. The Stadia Controller has a Google Assistant button. When you get stuck, instead of scouring YouTube for the right walkthrough explanation, you’ll supposedly be able to push the Google Assistant button for help. How rudimentary or how complex this is will depend on how good the AI is. The developer-facing part is Style Transfer ML. Style transfer is a machine learning technique that recomposes images in the aesthetic of other images, letting game developers map textures and color palettes from artwork, photos, and still images to game environments automatically. Google needs to woo developers to Stadia, and it’s naturally leaning on its AI chops to do so. But like everything Google does, Stadia is really about data collection.
Artificial intelligence making major inroads into Russian banking

According to the Expert RA study, those obstacles include discrepancies with data in information systems, but once the issue of data consistency is resolved, finding qualified personnel to process data is set to be a major challenge. Industry insiders have already been complaining about difficulties in finding qualified personnel to operate AI-based solutions. “The main factors that are impeding the adoption and development of AI are shortages of qualified professionals and problems with the infrastructure of information systems,” said Smirnov. Putyatinsky agreed, saying: “The acutest issue is training of qualified personnel.” To help resolve this challenge, CBoM has been running an internship programme called IB Universe for the past 12 months. “This allows students and recent graduates to acquire practical experience in various areas of investment business,” added Putyatinsky. According to Putyatinsky, educational programmes of that kind will eventually allow banks to train personnel in the working environment, producing a new wave of employees who will already be prepared to deal with new technologies, such as AI and machine learning.
EU Seeks Better Coordination to Battle Next Big Cyberattack
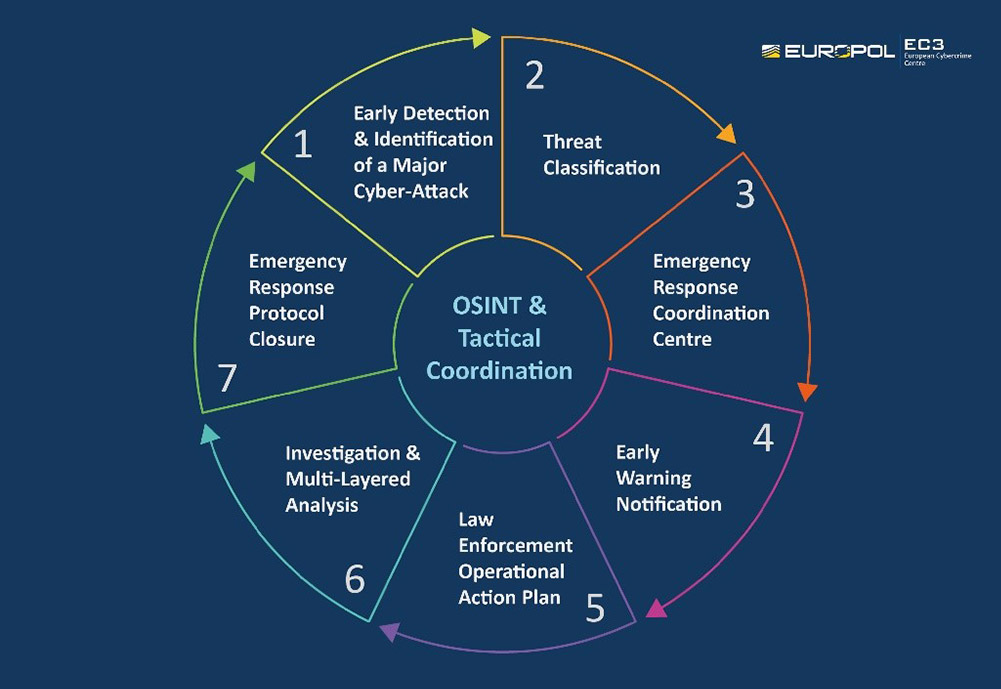
The news that Europol is trying to better prepare EU member states for the next big cyberattack comes as fresh warnings are being sounded that Russia is looking to interfere in upcoming EU parliamentary elections scheduled for May. On Thursday, CNBC reported that FireEye has found evidence that two advanced persistent threat groups are gearing up for more attacks in the coming months. The CNBC report specifically pointed to increasing activity from APT 28, the Russian-backed group that is also known as Fancy Bear and which is believed to been involved in different disruption campaigns around the world, including Sandworm, which has been linked to the NotPetya wiper-malware attack that was unleashed in July 2017. To help governments better defend themselves against such attacks, numerous vendors - including Cloudflare, Google, Microsoft and Symantec - have moved to offer free services. In February, Microsoft announced that it would expand its AccountGuard, which provides protection and threat detection geared to blocking nation-state and APT activity, to 12 more European countries in preparation for the 2019 elections.
Pivoting to digital maturity

Transformation initiatives are only as valuable as the business impact they drive. In our analysis of the survey results, therefore, we adopted a simple measure of digital maturity: the extent to which respondents said an organization’s digital transformation efforts are delivering business benefit. We then classified respondents into three segments—lower, median, and higher—according to the degree of business benefit they said they were achieving from their actions. Digital transformation is a continual process, and digital maturity is a moving target. So we present these as relative rather than absolute classifications. ... Achieving data mastery can entail an organization wide effort, sometimes under the direction of a chief data officer, to identify and evaluate data assets and build or acquire the necessary platforms and competencies. Eighty-eight percent of higher-maturity companies in our survey reported that they were obtaining a significant positive impact from their use of data, compared to just 24 percent of lower-maturity companies.
Algorithms have already taken over human decision making

In fact, algorithms operating without human intervention now play a significant role in financial markets. For example, 85% of all trading in the foreign exchange markets is conducted by algorithms alone. The growing algorithmic arms race to develop ever more complex systems to compete in these markets means huge sums of money are being allocated according to the decisions of machines. On a small scale, the people and companies that create these algorithms are able to affect what they do and how they do it. But because much of artificial intelligence involves programming software to figure out how to complete a task by itself, we often don’t know exactly what is behind the decision-making. As with all technology, this can lead to unintended consequences that may go far beyond anything the designers ever envisaged. ... But the algorithms that amplified the initial problems didn’t make a mistake. There wasn’t a bug in the programming. The behaviour emerged from the interaction of millions of algorithmic decisions playing off each other in unpredictable ways, following their own logic in a way that created a downward spiral for the market.
Quote for the day:
"At the heart of great leadership is a curious mind, heart, and spirit." -- Chip Conley
No comments:
Post a Comment