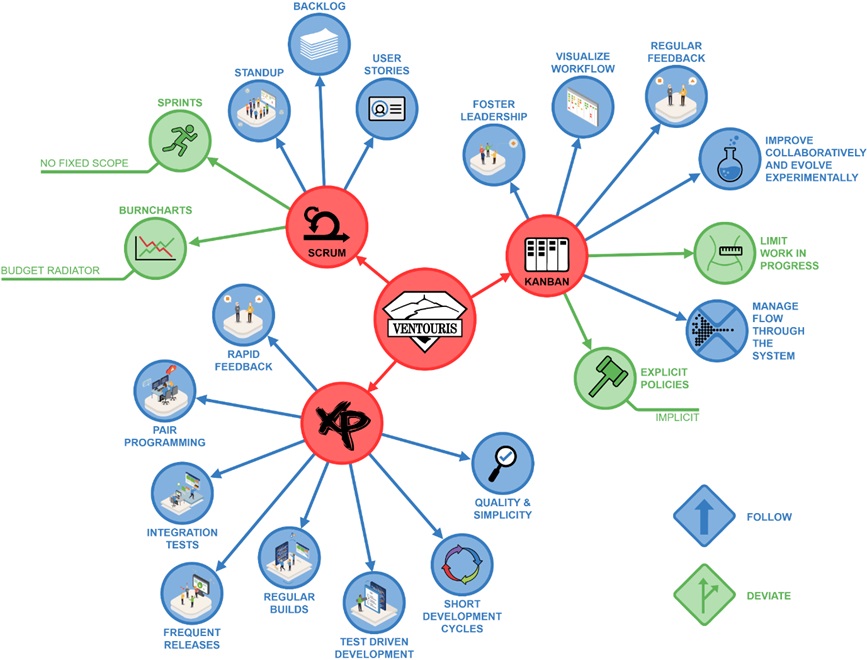
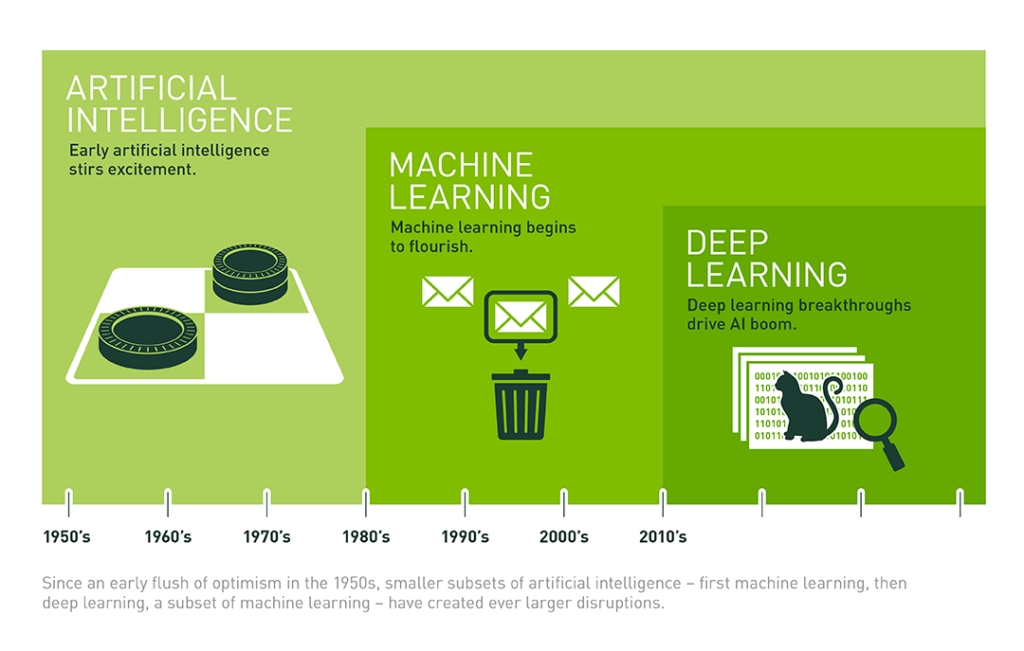
10 reasons to love the secret Surface Phone

Microsoft phones failed. Windows Mobile, Windows Phone, Windows 10 Mobile — all too little, too late.But I think Microsoft could succeed with its next device.Rumor has it that Microsoft is working on a two-screen clamshell mobile device code-named Andromeda that may be branded the “Surface Phone.” (The more likely branding may be “Surface Pad,” or something like that, to de-emphasize the phone function.) I believe the rumors are true and predict this device could even be teased at Microsoft’s Build Conference in Seattle May 7. From Microsoft’s perspective, creating a new mobile device is an existential necessity. Apple is threatening Microsoft’s enterprise business with a steady infiltration by iPhone and iPad. These client devices invite all kinds of non-Microsoft solutions into the enterprise. Something must be done. Microsoft would likely fail in a fair fight against Apple with conventional phones or tablets. So Microsoft needs to offer a very appealing, business-friendly device that breaks all the rules. Going further, I think the Surface Phone is just what the mobile market needs — just what you need — and for the following 10 reasons
No internet: The unbearable anxiety of losing your connection

So, that was Tuesday. Remember, I work from home. Getting my job done was a major challenge with minimal internet. While I could take my laptop to one of the many coffee shops Oregon has to offer, some work required being hooked up to my dual large-screen monitors and giant tank of directly-attached media asset storage. Watching TV at night was a crapshoot. Sometimes it would work. Other times, not so much. Now, you have to understand, I have a relatively large offline video collection, much of it digitized on one of my NAS boxes. So, even if the internet was fully down, my wife and I could watch movies or TV shows. But did we? No, if Netflix or Hulu or HBO Now or CBS All Access or Prime Video or Showtime or -- heaven forbid! -- YouTube was offline, it was a Category Five level of distress. Being intermittently disconnected from the internet created a level of separation anxiety that, in some ways, eclipsed constructive problem-solving. We didn't have to watch Netflix. We could have just as easily watched something on our own media tank.
Juniper battles Cisco, VMware with Contrail cloud tools

Contrail Enterprise Multicloud simplifies networking through its Contrail Command console. Companies, for example, can use the software's graphical user interface to request workload-to-workload connectivity without knowing the underlying components, like ports, switches, routers and subnets. AppFormix reduces complexity further by providing intelligence on the different cloud infrastructures and the overlay services running across them. The information is useful for planning and diagnostics. Casemore expects Juniper to eventually create a single Contrail-based software console that unifies data center, cloud and branch networks. "They're looking at extending this over the WAN," he said. Piling as much networking as possible into a single management console is also Cisco's strategy. So, to differentiate itself, Juniper is positioning its product as more open than Cisco's Application Centric Infrastructure (ACI). ACI requires the use of at least some Cisco switches. Contrail Enterprise Multicloud, on the other hand, supports Juniper, Arista and Cisco hardware.
7 Reasons Why Open-Source Elassandra (Cassandra + Elasticsearch) Is Worth a Look
For organizations that rely on the Cassandra NoSQL database but require more efficient search capabilities, Elassandra offers a compelling open-source solution. Elassandra combines the powers of Elasticsearch and Cassandra by utilizing Elasticsearch as a Cassandra secondary index. While companies may use both Elasticsearch and Cassandra on their own (and unite them by developing their own custom integration or synchronization code), Elassandra negates the challenges of implementing these measures and managing that software separately. By closely integrating Elasticsearch with Cassandra, Elassandra provides search latencies that approach real-time responsiveness. Better yet, it achieves this while also delivering access to all the advantages of Elasticsearch’s established ecosystem of REST APIs, plugins, and other solutions. Through these tools — such as the powerful Kibana UI that allows users to search, analyze, and visualize data quickly and easily — database ops can be carried out with much more efficiency than is possible using Cassandra and Elasticsearch independently.
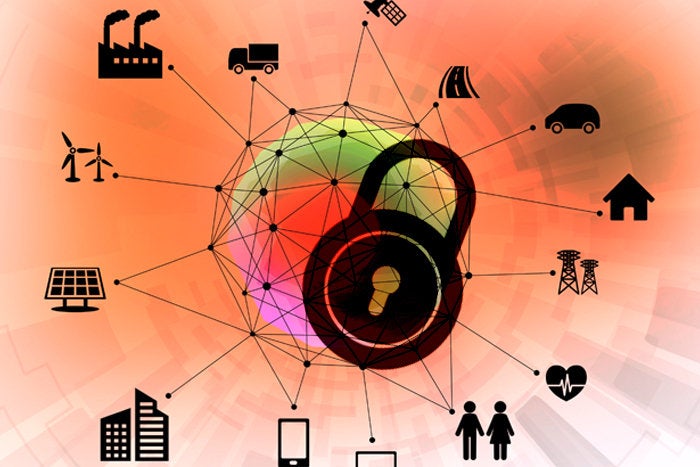
Why intent-based networking is important to the Internet of Things

To date, the driving forces behind the change have been things like moving apps to the cloud, the erosion of the enterprise perimeter, and an increase in mobility. But none of these will have the impact that IoT will have on the enterprise network. IoT adds orders of magnitude more devices, many of which are not owned by the IT department. Also, many IoT devices have no inherent security capabilities and often have old operating systems and embedded passwords, making them easy to breach and creating backdoors into other critical systems. IBN can solve many of those challenges. One could argue that organizations could continue to run a data center without IBN, as companies could throw more people and money at that part of the network. It would be difficult, but it might be doable. However, IoT deployments at scale are likely to fail without IBN, and one could argue that the concept of an IBN was designed with something like IoT in mind where unpredictability and randomness are the norms. The more variables in the network equation, the harder the problem is to solve — and that's happening to the network right now.
'Cyber blindspot' threatens energy companies spending too little

Companies are aware of the need protect raw data, but they’re often less sophisticated about the need to protect recently computerized systems for operational assets, according to Stegall. “When you get to a discussion on locking down the operations issues, they kind of look like deer caught in the headlight,” he said. Based on analysis developed over 15 years, energy companies that earn $1 billion in revenue a year generally spend about $1 million for cybersecurity, Precision found. In comparison, companies within the financial industrial with $1 billion in revenue could spend as much as $3 million. according to the data. Financial services and retailers have been in the limelight for data breaches. Walker, who works directly with energy executives, said he’s found it surprising how many believe the Defense Department or Homeland Security is defending them. They can’t, Walker said, because the government lacks the capability, expertise and, importantly, the legal standing to defend civilian assets before they’re attacked.
The 14 Soft Skills Every IT Pro Needs

Hiring managers and recruiters bemoan a soft skills gap in IT, and recent data backs up the sentiment. A LinkedIn report conducted with consulting firm Capgemini found that more employers say their organization lacks soft skills (nearly 60 percent) than hard digital skills (51 percent). Some firms, such as Vodafone and Citi, find soft skills important enough that they’re using surveys and AI in their interview process to assess communication skills, according to this year’s Global Recruiting Trends report from LinkedIn. ... If you’re a candidate with any or all of these skills, they’re useful talking points in your next interview. If not, you may find some areas worth brushing up. And if you’re doing the hiring, these are the skills your peers value most on their teams. ... “At a certain level, irrespective of whatever role you might have, you’re in sales,” says Jay Jamison, vice president of strategy and product management at Quick Base. “Selling people on your ideas or vision for the future — or whether you’re carrying a quota and need to close out a month. Communication skills, self-awareness and the capacity to sell and influence are the top three soft skills I’m looking for.”
To improve network throughput, scrap the ones-and-zeros system

Improvements proposed, in addition to the aforementioned abandonment of binary, is to match dodgy signals that are harder to decode to customers close by who don’t need particularly clean signals, then create good signals, which are easier to decode, for the distant customers. By doing that, you optimize the pipe for everyone. Throughput improves, too, as capacity goes up — everyone needs less time to communicate. Van der Linden says one does this by making changes to the actual signal levels. “Normally you would go for four or eight equidistant levels. But if you position the levels with unequal intermediate spaces, you open up larger gaps between pairs of levels that are closer together. The bit encoded within the large distance is easier to decode and thus can handle a worse signal quality,” he says. He says that his “smarter” fiber optimization ideas, which produce better data rates, are based on technology already used in wireless, cable, and DSL. Other proposals he makes in his thesis include more colors in the same fiber — that makes more data streams — and three different clock rates.
BDD Tool Cucumber is 10 Years Old
The difference in productivity between a programmer who has to wait 1-5 seconds for test feedback and 30+ seconds is significant. At 1-5 seconds you can attain (and stay) in state of flow where you're hyper productive, for hours. That just doesn't happen if you're interrupted all the time. We've become so accustomed to slow feedback that we've invented and adopted practices to work around them rather than fixing them. The test pyramid is one such workaround. Conventional wisdom tells us that full-stack tests that go through the UI are slow and brittle. Therefore, we'll have fewer of the slow, flaky tests, and more of the fast, consistent ones. A much better way to address this is to make slow tests fast and make flaky tests stable. What's not to like about confidence *and* speed? Nat Pryce and Josh Chisholm have independently explored ways to make full stack tests run sub-second by removing all I/O and running everything in-process. This used to be something we only knew how to do with domain level tests.
Ericsson and HPE accelerate digital transformation
It is more bespoke than we would like. It’s not as easy as just sending one standard shipping container to each country. Each country has its own dynamic, its own specific users. The other item worth mentioning is that each country needs its own data center environment. We can’t share them across countries, even if the countries are right next to each other, because there are laws that dictate this separation in the telecommunications world. So there are unique attributes for each country. We work with Ericsson very closely to make sure that we remove as many itemized things as we can. Obviously, we have the technology platform standardized. And then we work out what’s additionally required in each country. Some countries require more of something and some countries require less. We make sure it’s all done ahead of time. Then it comes down to efficient and timely shipping, and working with local partners for installation.
Quote for the day:
"I wish that we worried more about asking the right questions instead of being so hung up on finding answers." -- Madeleine L'Engle


![app svcs dev wants soad18_thumb[2]](https://f5.com/Portals/1/Users/038/38/38/app_svcs_dev_wants_soad18_thumb%5B2%5D_thumb.png?ver=2018-03-14-084407-557)