Why the Public Versus Private Blockchain Debate Is the Wrong Conversation
The conversation regarding public versus private blockchain doesn’t have to be a polarizing one. It’s not an either/or debate but rather a question of application. Private blockchains don’t have to be viewed as the enemy, or a replacement for public ones. They are simply a case-specific option. When taken out of the theoretical arena, there is room for both open read-and-write blockchains and those with access restrictions. What we find in practice, having developed numerous blockchain applications for both entrepreneurs and intrapreneurs, is that the apparently different requirements of each tend to converge over time. That is, many applications built by entrepreneurs will integrate with one or more large corporate enterprises at some point, and will therefore need to address their needs. Similarly, many enterprise applications are tackling obstacles that currently prevent them from making their solutions more open and capable of incorporating tokens of some form. Both sides are invested in the value of bringing integrity around data.

It's because of the sudden change in working that 47% of those surveyed say they've found themselves reassigned to general IT tasks as organisations adapt to the new reality. In 90% of cases, the security team is working remotely full-time – the remaining 10% that are still going to an office are doing so either because their organisation is sensitive in nature and the work can't be done from home, or the company doesn't have the capability to allow full-time remote work. In many cases, these people would prefer to stay home, but as some respondents put it, "duty calls". In a significant number of cases, those duties involve dealing with a rise in the number of cyberattacks and other security incidents: overall 23% said the number of these had gone up since the transition to remote work and in some cases security teams are tracking double the number of incidents. Worryingly, 30% of those security professionals who've been reassigned to IT say there's been a rise in security incidents against their organisation, compared to 17% who haven't changed roles but say they're dealing with more attacks.
Shade Ransomware Operation Apparently Shuts Down

Jornt van der Wiel, another security researcher at Kaspersky, notes that even though the decryption keys are real, the true motive behind why the Shade operators decided to end their operations may never be known. "Keys can be stolen by a rival gang who put the message on Github, or it can be the real authors," van der Wiel tells Information Security Media Group. "We will never know until law enforcement agencies do some arrests." Those who say they are the operators of Shade, which is also known as Troldesh or Encoder.858, say in their GitHub post that they shut down their operations at the end of 2019 and that they were publishing their decryption keys, which can help security companies create their own tools to help remove the malware and recover any other crypto-locked files. "We are also publishing our decryption; we also hope that, having the keys, anti-virus companies will issue their own more user-friendly decryption tools. All other data related to our activity was irrevocably destroyed," according to the GitHub post. "We apologize to all the victims of the Trojan and hope that the keys we published will help them to recover their data."
Designing software to include older people in the digital world

“If you design for older people, you’re making inclusive choices for design and accessibility for everyone,” says Froso Ellina, product design manager at software development consultant VMware Pivotal Labs. On text, Ellina says that as well as using high colour contrasts and larger sizes, the choice of typography is important. A small number of simple fonts – with sans-serif ones such as Arial often the more accessible choice – can increase readability. Subtitling online videos means they can be used by those with poor hearing or no ability to hear, but also makes these work for those who are in a location where they can’t use audio. Older people can also find it harder to use touch screens due to declining motor skills. Ellina says that one centimetre is a good minimum length for a target area such as a button or link, and it makes sense to leave plenty of space between them. Short-term memory tends to decline with age, which has implications for how software is updated.
AI cannot be recognised as an inventor, US rules

The US Patent and Trademark Office rejected two patents where the AI system Dabus was listed as the inventor, in a ruling on Monday. US patent law had previously only specified eligible inventors had to be "individuals". ... Dabus designed: interlocking food containers that are easy for robots to grasp; and a warning light that flashes in a hard-to-ignore rhythm. And its creator, physicist and AI researcher Stephen Thaler, had argued that because he had not helped it with the inventions, it would be inaccurate to list himself as the inventor. But patents offices insist innovations are attributed to humans - to avoid legal complications that would arise if corporate inventorship were recognised. Some academics, however, have previously suggested this should no longer apply. The European Patent Office has seen a surge in AI-driven filings, according to Powell Gilbert LLP intellectual property law specialist Penny Gilbert. "AI is a fast-evolving field, set to revolutionise many industries, and raises many untested issues around patentability and ownership of inventions that are made using it," she told BBC News.
Reinforcement Machine Learning for Effective Clinical Trials
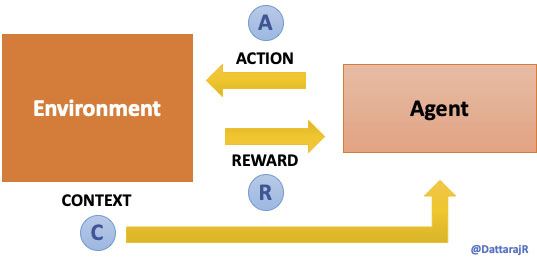
Machine Learning (ML) is often thought to be either Supervised (learning from labeled data) or Unsupervised (finding patterns in raw data). A less talked about area of ML is Reinforcement Learning (RL) – where we train an agent to learn by “observing” an environment rather than from a static dataset. RL is considered to be more of a true form of Artificial Intelligence (AI) – because it’s analogous to how we, as humans, learn new things – observing and learning by trial and error. ... A simpler abstraction of the RL problem is the Multi-armed bandit problem. A multi-armed bandit problem does not account for the environment and its state changes. As shown in figure 2 below, here the agent only observes the actions it takes and rewards it receives and tries to devise the optimal strategy. The idea in solving multi-armed bandit problems is to try and explore the action space and understand the distribution of the unknown rewards function.
Get to know edge storage and the technology around it
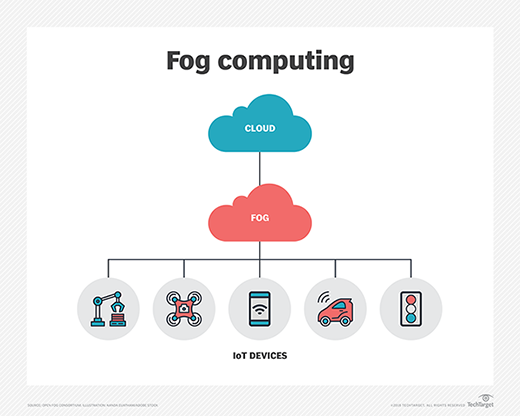
Edge computing: Data is rarely static and often moves from where users are collecting and using it to the cloud or to a central data center for analysis, processing and storage. But data centers and clouds are often far from where the data is collected. Transmission takes time and inserts latency and inefficiencies into the processing equation. That's time that most organizations using IoT functionality just don't have. For instance, an autonomous vehicle can't wait for an answer on whether to swerve right or left; it needs a real-time response. Edge computing closes that data transmission distance and puts compute and storage closer to where the data is collected. This approach essentially decentralizes the traditional data center. Fog computing: Fog computing refers to a decentralized computing infrastructure in which data, applications, compute and storage sit between where the data originates and the cloud. Fog computing brings the cloud's intelligence, processing, compute and storage capabilities closer to the data for faster analysis and processing. Like edge computing, fog eliminates inefficiencies that come with data transmission and solves privacy and security issues inherent in data transmission.
Data governance matters now more than ever
Records Management is built into the Microsoft 365 productivity stack and existing customer workflows, easing the friction that often occurs between enforcing governance controls and user productivity. For example, say your team is working on a contract. Thanks to built-in retention policies embedded in the tools people use every day, they can continue to be productive while collaborating on a contract that has been declared a record—such as sharing, coauthoring, and accessing the record through mobile devices. We have also integrated our disposition process natively into the tools you use every day, including SharePoint and Outlook. Records versioning also makes collaboration on record-declared documents better, so you can track when edits are made to the contract. It allows users to unlock a document with a record label to make edits to it with all records safely retained and audit trails maintained. With Records Management, you can balance rigorous enforcement of data controls with allowing your organization to be fully productive.

Some of the reasons as to why senior executives in Australia are adopting AI is because 41% believe it frees up more time for employees to focus on more important tasks, another 40% see AI as a way to improve customer experience and service, and 39% agree AI offers businesses the ability to leverage data and analytics. Genpact Australia vice president and country manager Richard Morgan said the adoption of AI by Australian businesses signals that executives understand the potential benefits it could deliver. "I think AI is now a way to try to mine information and drive better outcomes for the company themselves, and to give clients a better experience to get them coming back and using your products and services more frequently -- that's the holy grail," he told ZDNet. Australian executives also believe that integrating AI into the talent process could help reduce gender bias in recruitment, hiring, and promotion, the study showed. On the other end of the spectrum, three-quarters of Australians said they are concerned about AI bias and another 67% fear that AI will make decisions that affect them without their knowledge.
Arming yourself against deepfake technology
Deepfakes are likely to continue causing havoc for politicians in the coming years, but equally, modern enterprises could also find themselves under threat. In 2019, the UK boss of an energy company was tricked over the phone when he was asked to transfer £200,000 to a Hungarian bank account by an individual using deepfake audio technology. The individual believed the call to be from his boss, but actually, the voice had been impersonated by a fraudster who succeeded in defrauding the man out of money. Occasions like this, particularly where there are substantial amounts of capital at risk, are reminders that organisations should be on high alert for deceptive fraudsters and arm themselves accordingly. In sectors such as financial services, vast amounts of customer data are at risk and a breach of information or assets can have detrimental effects on all involved. When data is breached, both the consumer and organisation face potentially large consequences.
Quote for the day:
"When you find an idea that you just can't stop thinking about, that's probably a good one to pursue." -- Josh James