SOCs require automation to avoid analyst fatigue for emerging threats

SecOps needs an immediate shift across industries. Some SecOps teams develop playbooks for an additional layer of training, but when security events occur, it is uncommon to follow every step a playbook describes. The data becomes overwhelming and the resulting alert fatigue leads to analysts overlooking threats entirely, leading to an increase in emerging threats. The typical security analyst is facing a 40 percent increase in persistent threats and data breaches year over year. In the last year, there were over 1,500 breaches in the U.S. alone, exposing close to 179 million records. Additionally, the rising shortage of cybersecurity skills throughout the industry contributes to the threat detection fatigue experienced by current analysts. “In the ever-evolving threat landscape, we know machines can scale very well, but we cannot expect them to outpace human intelligence,” said Kumar Saurabh, CEO at LogicHub. “CISOs need to capitalize on irreplaceable expert human analyst knowledge to enrich security automation and provide the industry with the right training tools. This is the only way enterprises will stand a chance in protecting their most valued data.”
Introduction to Security and TLS
Encryption relies a lot on math, random number generators, and cryptographic algorithms. With encryption, there is the need for "keys:" sequences of bits and bytes which are used to lock (encrypt) and unlock (decrypt) the data. With symmetric encryption, the same key is used to encrypt and decrypt a message. It means that everyone having that (blue) key will be able to decrypt the message. So, security depends how securely I can distribute and keep that key. With asymmetric encryption, I have a pair of mathematically connected keys: a shared green key and a private red key. I keep the red key private and do not disclose and distribute it. The green key is public: everyone can use it. Everyone can encrypt a message with the green public key, but only the one with the red private key is able to decrypt it. The public and private key build a pair of keys. They are different but mathematically related. That way, only the private key is able to decrypt a message encrypted with the public key.
Securing smart factories: How Schneider Electric connects devices and prevents outages

What's happening over time for sure is, as you aggregate that data, as you can start to look at broader trends, you could start to bring in things like machine learning, and the thing that I think that we're seeing today that is the most pronounced, is that you still need quite a bit of human interaction when it comes to machine learning or AI. You need to identify patterns, and then you need to feed those back into machine learning so that you know what that pattern recognition looks like, and then you can start to take proactive measures, and so, just one example. You know a lot of outages or problems that happen in industrial setting, often start, you can actually look at things like partial discharge, or electrical partial discharge that happens in equipment. ... And so today, if you kind of looked at the signatures of what that looks like, a human being can look at that, you know we have thousands of electrical engineers in our company. Incredibly intelligent about what they do. You might not necessarily want to go out drinking with them but, they're a lot of fun too, to actually identify these problems. These guys can look at that, they can look at those signatures, they can instantly say, "You're going to have a problem here."
Is the U.S. headed toward a cashless economy through blockchain?

A government-backed digital currency could do away with banking fees that often target the poor who make many small, electronic payment transfers via services such as Western Union, while at the same time creating greater efficiencies. ... Cryptographic keys controlling funds could be in a consumer's control; the consumer could be issued a private key associated with their electronic funds and be able to use public keys for payments. Sweden's central bank, The Riksbank, is currently considering issuing a digital currency or cryptocurrency similar to bitcoin for mobile payments. Called the e-Krona, the digital currency would be used for smaller payments between consumers, businesses or with government agencies, and it would create safer and more efficient transactions, the government has argued. In 2015, Ecuador created the world's first state-sponsored digital currency, called Sistema de Dinero Electrónico, which was backed by the central bank; it allowed people to have money in accounts that could be traded on their phones. Ecuador, however, shuttered its electronic money system last year "due to lobbying by the banks," Garratt said.
How APIs can help prevent data warehouse hell
The challenges of breaking down data silos is just as much a problem of company culture. Department heads and even individual technicians may become territorial about the data in their care, reluctant to share it with others and suspicious about any plans to end a data silo as is typical during your traditional central warehousing efforts. A mandate from the top of the company can start the process of openig a data silo, but data owners may want to be able to do it at their own pace and comfort level. Adapting to those preferences is all but impossible to accomplish in traditional big data projects. These problems shouldn’t cause despair. There’s a way to open data silos that addresses both the technical and human problems mentioned above. Data owners shouldn’t be forced to immediately dump all of the information together in a warehouse. The process should happen at a deliberate pace, set in part by the owners of the data. The data doesn’t ever have to leave the silo to be shared. The right API inserted into the data silo by the data owner provides access to the information to everyone who might need it.
Becoming a ‘Digital Bank’ More Than Lipstick on a Legacy Pig
To digitally deliver an exceptional customer experience, an organization must build from within, engaging all functional areas and stakeholders, to ensure a seamless and easy journey from shopping to purchase to use. This includes looking at all back-office processes and data flows to make sure they are in alignment with what is required by the digital consumer. For instance, it is virtually impossible to develop a 5-minute consumer loan product for both customers and prospects without completely revamping the process flow behind the scenes. It is obviously even more difficult to match the 30-second delivery offered by leading banks and credit unions worldwide. Beyond just changing the process, data needs to flow between legacy silos from the initiation of the process to the fruition. The digitization is even more difficult for a home loan, where the stakeholders include the realtor, loan underwriter, regulator, builder, insurer and the end customer. To optimize the journey, all of these stakeholders must be aligned and understand the final objective … to remove all friction from the consumer journey.
Artificial Intelligence: 6 Step Solution Decomposition Process
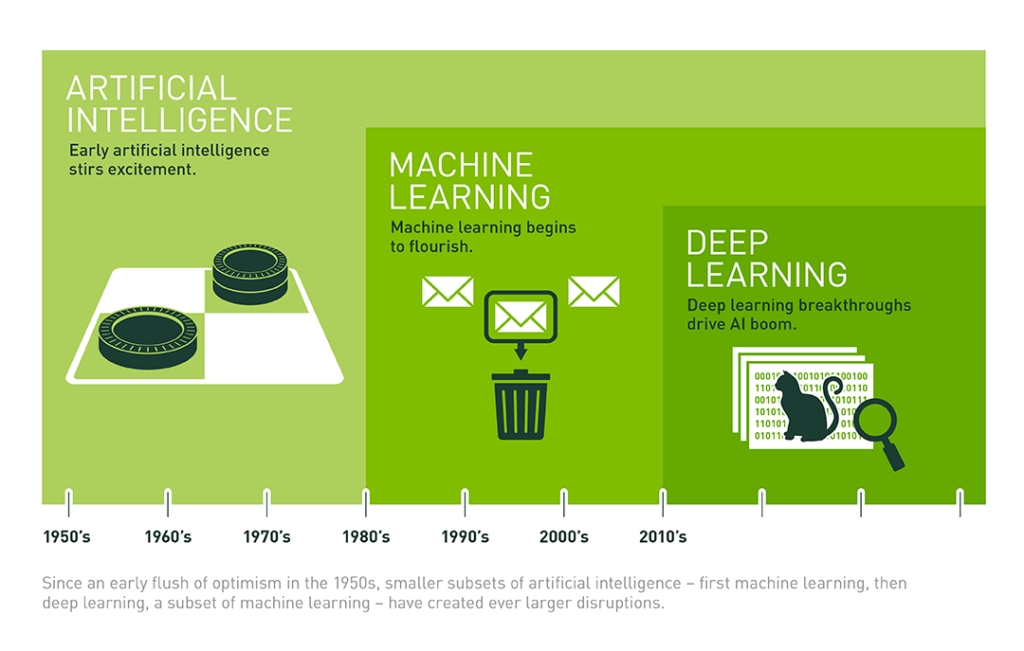
Success with artificial intelligence doesn’t begin with technology, but rather the business, and more specifically the people and processes running the business. Before deploying technology, leaders should seek to understand (envision) how artificial intelligence could power a profitable business, and drive compelling customer and operational outcomes. Collaboration with stakeholders and key constituents is critical to understanding the decisions and needs of the business. While every organization’s needs vary, there exists a consistent, transparent process that can drive a more stable and widespread adoption of artificial intelligence. Note: throughout this blog, when I use the term “artificial intelligence,” I mean that to include other advanced analytics such as deep learning, machine learning (supervised, unsupervised, reinforcement), data mining, predictive analytics, and statistics ... The power of this process is its simplicity. By staying focused on the business or operational objectives and tasks, businesses can successfully transform how they use data and analytics to produce optimal outcomes.
The importance of firmware security
There are several lessons to be taken away from the Fusée Gelée exploit, and they apply to OEMs as well IT professionals. First off, manufacturers need to be sure that their hardware has been properly tested against all possible attacks. Fusée Gelée allows a device owner to hack their own hardware, which isn't a risk itself, but it could also allow an attacker to write code to remotely execute a similar attack. Firmware security is a critical part of device design that can easily be exploited—just look at Spectre and Meltdown. Had Intel been diligent in seeking out vulnerabilities, it might not be facing a vulnerability in nearly every single processor it ever created. For IT support staff and security professionals, Fusée Gelée paints a whole other set of complications: hardware security. In the case of the Nintendo Switch, hardware modification was necessary to force the device to boot into recovery mode. Doing so isn't complicated though: It just requires the bending of an exposed pin.
Introduction to GraphQL
GraphQL was created directly for different APIs. Its main purpose is to use flexible syntax and systems that simply describe the data requirements and interactions. Throughout its history, GraphQL became an example of properly functioning and reliable software, which could be used in a pretty simple way — even by junior-level programmers. Thanks to its features and opportunities, which have been implemented by the creators, GraphQL was able to replace other earlier customized tools, which have been designed for the same purpose. When we discuss the functions and aspects of GraphQL, it is essential to present those key opportunities. ... As you may have already noticed, one of the main benefits of GraphQL is that you, as a potential user, can do some development things much more quickly. For example, instead of writing huge texts of code, it may be enough just to use one or two primary functions to achieve what you need.
Data protection is critical for all businesses
“Personal data is considered to be one of the most sensitive categories of data an organisation has access to, and perhaps it is the most valuable,” he says. “As the value of personal data increases, so should the controls needed to protect it. Personal data should be processed only with clear consent given by the data owner, with a transparent agreement and an organisation-wide focus on preventing data theft or misuse.” To identify misuse, he believes firms should constantly analyse their businesses procedures and operations to ensure they are compliant with the latest data protection safeguards. At Netskope, Thacker treats data protection as a constant operation. Firms should not assume that once they have installed or developed a system to protect customer data, they have nothing else to do. “I recommend enterprises continually discover new and amended business processes, working alongside the business to apply the necessary safeguards needed for protection,” he says. “The aim is to understand how employees – and third parties – are using personal data and to ensure it meets the sole purposes for which it was originally collected.
Quote for the day:
"I think the next best thing to solving a problem is finding some humor in it." -- Frank A. Clark
No comments:
Post a Comment