How to protect your PC from the Meltdown and Spectre CPU flaws

A pair of nasty CPU exploits have serious ramifications for home computer users. Meltdown and Spectre let attackers access protected information in your PC’s kernel memory, potentially revealing sensitive details like passwords, cryptographic keys, personal photos and email, or anything else you’ve used on your computer. These are serious flaws. Fortunately, CPU and operating system vendors pushed out patches fast, and you can protect your PC from Meltdown and Spectre to some degree. It’s not a quick one-and-done deal, though. They’re two very different CPU flaws that touch every part of your operating system, from hardware to software to the operating system itself. Check out PCWorld’s Meltdown and Spectre FAQ for everything you need to know about the vulnerabilities themselves. We’ve cut through the technical jargon to explain what you need to know in clear, easy-to-read language. We’ve also created an overview of how the Spectre CPU bug affects phones and tablets.

“While it is perhaps no surprise to learn that use of Facebook both inside and outside the workplace would be affected, this story certainly appears to have had a broader impact,” wrote Chris Ross, international senior vice-president at Barracuda, in blog post. Almost two-thirds of respondents (62%) said that as a result of the revelations about Facebook, they had reviewed their corporate policy for allowing user access to non-business-related sites and apps, either in terms of providing new guidance or restricting access. Only 20% planned to maintain a policy to allow free access to non-business sites and apps. “While restricting access to non-business apps from the workplace can improve productivity, it may not impact Facebook’s ability to collect and share the personal information of users,” said Ross. “However, these privacy concerns have raised some strong feelings in the business community around Facebook’s viability as a business tool. Our recommendation is that organisations that continue to leverage Facebook as a business platform should review some basic controls.”
What should define an enterprise encryption strategy?
This year’s statistics are encouraging, but the report does show areas of challenge. Data discovery rates as the top data encryption planning/execution challenge by 67% of respondents, a number that is 8% higher than 2017. Respondents from the UK, Germany, the US and France have the most challenges, which likely points to activities associated with preparation and compliance of data privacy regulations such as GDPR which comes into effect in May this year. When considering the majority of organisations polled are using more than one public cloud provider, the report also raises questions about how organisations are enforcing consistent encryption and key management policies across multiple cloud vendors. Securing data in a multi-cloud environment can be especially problematic for organisations seeking compliance, particularly if they are attempting to instantiate a single organisational policy using different native tools from multiple cloud providers.

To spot a potential threat, a cybersecurity team must have a deep, nuanced understanding of its organization’s standard IT protocols, including the behavior of privileged users, accounts, and access points and the normal flow of authentication attempts. Simply put, a threat only appears as a threat if it deviates from standard practices. An AI cybersecurity platform could do a great deal to minimize the number of false positives and enable IT teams to focus their energies on combating real threats. When an AI algorithm is given access to an organization’s internal log and monitoring systems, it can evaluate the usage patterns of each individual employee, create a series of baseline activity profiles, and keep an eye on all network activity 24 hours a day. AI is tremendously useful as this type of catch-all mechanism, but it becomes truly invaluable once it starts to recognize threats in micro-deviations that are all but invisible to the human eye. As an AI tool is fed more and more data over time, it becomes capable of maintaining a constantly moving standard by which to judge potential threats.
Generation Z Is Already Bored by the Internet

To a parent or the casual observer, a phone-bored teen may appear engaged. After all, they’re on their phone, which many people consider an inherently engaging activity. In reality, they’re bored out of their mind. “I can be in my bed for hours on my phone, and that’s me being bored,” said Maxine Marcus, a 17-year-old and founder of The Ambassadors Company, a teen consulting business. “You think that we’re so entertained because we’re on our phones all the time, but just because we’re on it, doesn’t mean we’re engaged or excited. I get bored on my phone all the time. “When you’re bored on your phone, you’re just sitting with your own thoughts. You’re on it, but it’s just an action so your brain still goes wherever it wants to go. You get bored and you start thinking and daydreaming,” she added. It’s important to note that the majority of time users spend on their phones, they spend engaged. Tech companies go to exorbitant lengths to keep users active and attentive.
How artificial intelligence and machine learning can revolutionize ecommerce
To start with, it is a high-technical debt undertaking and requires high quality data, timely decisioning at scale, and a hypothesis-based approach to marketing. Before any machine learning can be successfully applied, it needs data. And not just any type of data. Firstly, the data must be useful, in a way that reflects first-party behavior on digital channels, such as web pages and single-page applications. Secondly, the data must be processed quickly. Thanks to the latest cloud technology, data can be processed in an almost real-time fashion, with latency of a couple of minutes, rather than hours. Finally, and by definition, personalization is personal, that means that it’s unlikely that a specific set of machine learning approaches for one brand will translate to another. In order to achieve success with this, marketing teams need to employ a hypothesis-based approach to marketing, where they use the inferred signals from machine learning in conjunction with creative brand experiences.
Malicious IoT hackers have a new enemy
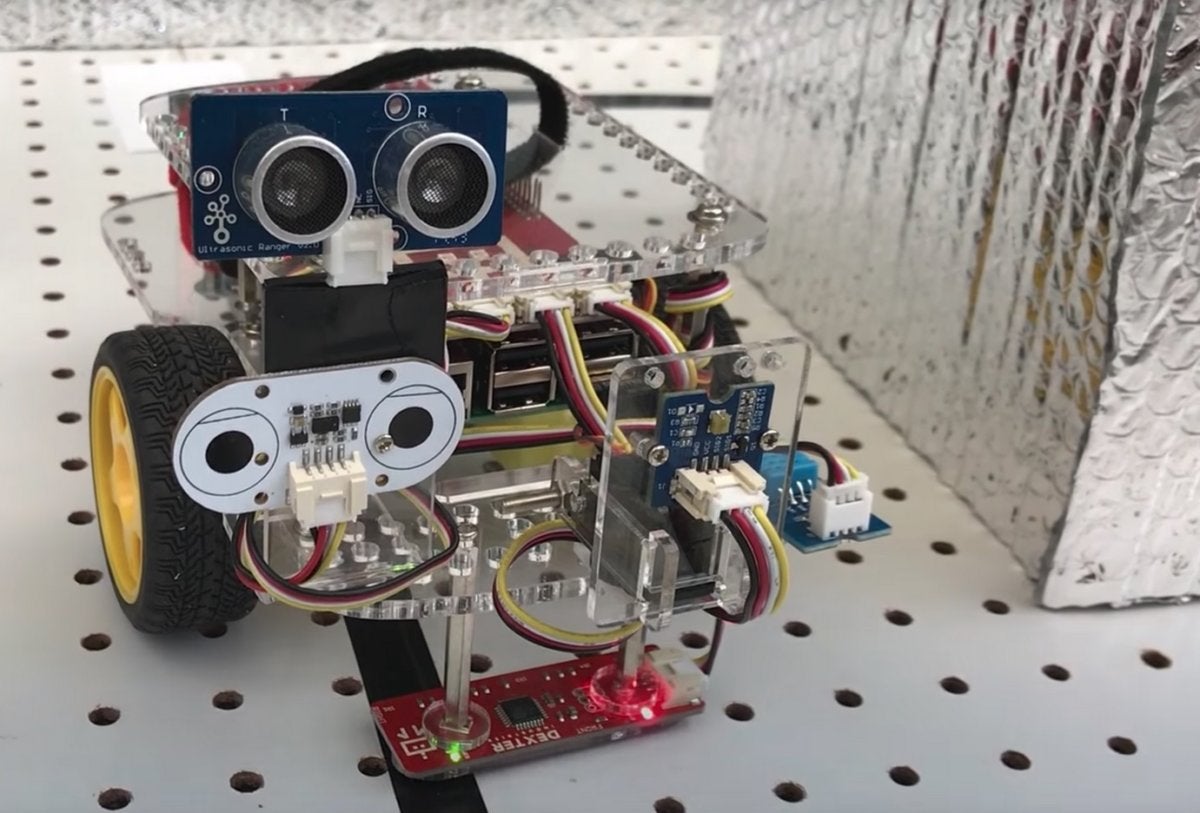
IoT security is about the farthest thing from a laughing matter in the world of technology today, threatening global trade, privacy and the basic infrastructure of modern society. So you could be forgiven for being taken aback that the newest defender of vulnerable systems against bad actors looks a little like Johnny 5 from the movie Short Circuit. Researchers at Georgia Tech’s School of Electrical and Computer Engineering rolled out the HoneyBot robot late last week. In essence, it’s a canary in the digital coal mine, offering an early warning that someone is trying to compromise an organization’s systems. HoneyBot is designed to look like a perfectly ordinary remote-controlled robot to anyone attempting to access it remotely, providing sensor data and movement information to that remote user. Where it differs, however, is if a user tries to get it to do something the owner doesn’t want it to do – HoneyBot can provide simulated responses to those commands without enacting them in the real world.
So What's Microsoft SQL Operations Studio?

From the information provided so far in a PASS keynote and accompanying blog post, it appears to be a blending of those two tools, with some container and DevOps functionality thrown in along with some Visual Studio Code goodness -- and apparently built on Electron. In the blog post, Microsoft SQL Operations Studio (MSOS from here on, for brevity) was described as a cross-platform, lightweight tool for modern database development and operations. Along with SQL Server, it will be used to work with other Microsoft data offerings like Azure SQL Database and Azure SQL Data Warehouse. Like VS Code and other editors, MSOS will provide easy access to code snippets (in the T-SQL language, in this case) and dashboards to monitor performance in the cloud or on the Azure cloud. As for more of that VS Code goodness, Microsoft said "You'll be able to leverage your favorite command line tools like Bash, PowerShell, sqlcmd, bcp and ssh in the Integrated Terminal window. Users can contribute directly to SQL Operations Studio via pull requests from the GitHub repository."
The dream job that's all the rage across America

There are several factors fueling the growth of these fully virtual companies, experts say. The most obvious is technology. Tools such as Slack, Zoom, Dropbox and Quip, a document-sharing and editing platform, make it easier than ever to communicate with far-flung employees and track their performance and workflow more accurately, said Trina Hoefling, author of Working Virtually: Transforming the Mobile Workplace. "Technology is the enabler," she added, "so people starting businesses are realizing that they can launch a company without a physical location quite easily." But perhaps the bigger driver in this new way of working is the demand from employees for a better quality of life. According to Gallup's "State of the American Workplace" survey, more than one-third of the respondents said they would change jobs in order to be able to work remotely some of the time. Younger employees — so-called millennials — especially start their careers fully expecting to find a position that offers more flexibility in how and where they work.
Google killing Chrome extensions for mining cryptocurrency
Up until now, Google has allowed Chrome extensions that mine cryptocurrency as long as the user is informed and the extension's only purpose is to mine cryptocurrency. That only accounts for 10% of Chrome extensions that mine cryptocurrency, however. The other 90% are doing it behind the scenes, not informing users, or both. Google said it has rejected many of the 90% of guilty extensions, and beginning now it is no longer accepting new Chrome extensions that mine cryptocurrency. The 10% of legitimate extensions aren't long for the world either: They'll be delisted from the Chrome web store starting in late June. In short, if mining cryptocurrency is any part of a Chrome extension you use or develop it's game over. Chrome extensions that use blockchain technology for other purposes, like cryptocurrency wallets, are unaffected. Just because an extension is removed from the official Chrome Web Store doesn't mean you can't install and use it—you just have to perform a few steps to load Chrome extensions manually.
Quote for the day:
"Always bear in mind that your own resolution to succeed is more important than any one thing." -- Abraham Lincoln
No comments:
Post a Comment