Urban Digital Twins: AI Comes To City Planning

Urban digital twin technology involves various tools and methods at each lifecycle phase, and because it is still an emerging field, there's a wide range of variability in available solutions. Different providers may focus on different aspects of the technology, offer varying levels of complexity, or specialize in specific use cases or lifecycle phases. Therefore, it's essential for organizations to carefully evaluate their requirements and compare the offerings of different providers to find the best fit for their specific needs. To make the most of urban digital twin technology, city officials and urban planners should first get a solid grasp on what it can do and the benefits it offers throughout a city's development. By aligning city goals to the capabilities of digital twin solutions at each lifecycle stage, teams can make sure they're picking the right tools for their specific needs. This way, cities can tailor their approach to urban digital twins, ensuring they're making the best choices to reach their desired outcomes and create a smarter, more efficient urban environment.
Empowering Citizen Developers With Low- and No-Code Tools
Whether you are building your own codeless platform or adopting a ready-to-use solution, the benefits can be immense. But before you begin, remember that the core of any LCNC platform is the ability to transform a user's visual design into functional code. This is where the real magic happens, and it's also where the biggest challenges lie. For an LCNC platform to help you achieve success, you need to start with a deep understanding of your target users. What are their technical skills? What kind of applications do they want to use? The answers to these questions will inform every aspect of your platform's design, from the user interface/user experience (UI/UX) to the underlying architecture. The UI/UX is crucial for the success of any LCNC platform, but it is just the tip of the iceberg. Under the hood, you'll need a powerful engine that can translate visual elements into clean, efficient code. This typically involves complex AI algorithms, data structures, and a deep understanding of various programming languages.
Will AI replace cybersecurity jobs?

While AI and ML can streamline many cybersecurity processes, organizations
cannot remove the human element from their cyberdefense strategies. Despite
their capabilities, these technologies have limitations that often require human
insight and intervention, including a lack of contextual understanding and
susceptibility to inaccurate results, adversarial attacks and bias. Because of
these limitations, organizations should view AI as an enhancement, not a
replacement, for human cybersecurity expertise. AI can augment human
capabilities, particularly when dealing with large volumes of threat data, but
it cannot fully replicate the contextual understanding and critical thinking
that human experts bring to cybersecurity. ... AI can automate threat detection
and analysis by scanning massive volumes of data in real time. AI-powered threat
detection tools can swiftly identify and respond to cyberthreats, including
emerging threats and zero-day attacks, before they breach an organization's
network. AI tools can also combat insider threats, a significant concern for
modern organizations.
Decoding OWASP – A Security Engineer’s Roadmap to Application Security
While the OWASP Top 10 provides a foundational framework for understanding and
addressing the most critical web application security risks, OWASP offers a
range of other resources that can be instrumental in developing and refining an
application security strategy. These include the OWASP Testing Guide, Cheat
Sheets, and a variety of tools and projects designed to aid in the practical
aspects of security implementation. OWASP Testing Guide – The OWASP Testing
Guide is a comprehensive resource that offers a deep dive into the specifics of
testing web applications for security vulnerabilities. It covers a wide array of
potential vulnerabilities beyond the Top 10, providing guidance on how to
rigorously test and validate each one. ... OWASP Cheat Sheets – The OWASP Cheat
Sheets are concise, focused guides containing the best practices on a specific
security topic. They serve as handy guides for security teams and developers to
quickly reference when implementing security measures.Cheat sheets can be used
as training materials to educate developers and security professionals on
specific security issues and how to mitigate them.
Intel Demonstrates First Fully Integrated Optical I/O Chiplet
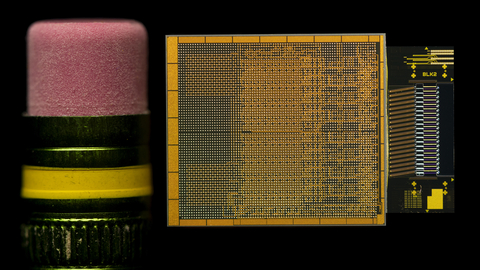
The fully Integrated OCI chiplet leverages Intel’s field-proven silicon
photonics technology and integrates a silicon photonics integrated circuit
(PIC), which includes on-chip lasers and optical amplifiers, with an
electrical IC. The OCI chiplet demonstrated at OFC was co-packaged with an
Intel CPU but can also be integrated with next-generation CPUs, GPUs, IPUs and
other system-on-chips (SoCs). This first OCI implementation supports up to 4
terabits per second (Tbps) bidirectional data transfer, compatible with
peripheral component interconnect express (PCIe) Gen5. The live optical link
demonstration showcases a transmitter (Tx) and receiver (Rx) connection
between two CPU platforms over a single-mode fiber (SMF) patch cord. ... The
current chiplet supports 64 channels of 32 Gbps data in each direction up to
100 meters (though practical applications may be limited to tens of meters due
to time-of-flight latency), utilizing eight fiber pairs, each carrying eight
dense wavelength division multiplexing (DWDM) wavelengths.
Artificial General Intelligence (AGI): Understanding the Milestones

It was first proposed in the early 1900s to create a machine or a program that
was capable of thinking and acting more like a person. The Turing Test,
designed by Alan Turing in 1950 to assess intelligence comparable to that of
humans, established the scenario. ... Machine learning emerged in the 1950s
and 1960s as a result of statistical algorithms that could identify patterns
in data and use them to make future decisions without external supervision.
... The Expert systems and symbolic AI centered on the encoding of knowledge
and the application of rules and symbols in human reasoning. ... Deep
learning, a subset of machine learning, has been a crucial breakthrough in the
journey toward AGI. In tasks like speech and image recognition, Convolutional
Neural Networks and Recurrent Neural Networks perform at a human-level of
intelligence. ... AGI research has produced numerous important results,
ranging from theoretical foundations to deep learning advances. Even if AGI
remains ideal, present AI research is pushing the envelope, imagining a time
when AI would fundamentally revolutionize our way of life and work for the
better.
Unlocking Innovation: How Critical Thinking Supercharges Design Thinking
Critical thinking involves the objective analysis and evaluation of an issue
to form a judgment. It's about questioning assumptions, discerning hidden
values, evaluating evidence, and assessing conclusions. This methodical
approach is crucial in professional environments for making informed
decisions, solving complex problems, and planning strategically. ... Design
thinking is a human-centered approach to innovation that integrates the needs
of people, the possibilities of technology, and the requirements for business
success. It involves five key stages: Empathize, Define, Ideate, Prototype,
and Test. Design thinking promotes creativity, collaborative effort, and
iterative learning. Merging critical thinking into the design thinking process
enhances each stage with thorough analysis and robust evaluation, leading to
innovative and effective solutions. ... Critical thinking provides the
analytical rigor needed to identify core issues and evaluate solutions, while
design thinking fosters creativity and user-centered design.
DAST Vs. Penetration Testing: Comprehensive Guide to Application Security Testing
Dynamic Application Security Testing (DAST) and penetration testing are
crucial for identifying and mitigating security vulnerabilities in web
application security. While both aim to enhance application security, they
differ significantly in their approach, execution, and outcomes. ... Dynamic
Application Security Testing (DAST) is an automated security testing
methodology that interacts with a running web application to identify
potential security vulnerabilities. DAST tools simulate real-world attacks
by injecting malicious code or manipulating data, focusing on uncovering
vulnerabilities that attackers could exploit. DAST evaluates the
effectiveness of security controls within the application. ... Penetration
testing is a security assessment process by skilled professionals, often
called ethical hackers. While comprehensive and carried out by experienced
professionals, manual testing can be time-consuming and expensive. These
experts simulate real-world attacks to identify and exploit application,
network, or system vulnerabilities.
There is no OT apocalypse, but OT security deserves more attention

The whole narrative surrounding attacks on OT environments is therefore
quite exaggerated as far as Van der Walt is concerned. “We are not in the OT
apocalypse,” in his words. This is important to know, he believes. “In fact,
there is a narrative in the market that is out to get organizations to take
action and invest.” In other words, we hear more and more that OT
environments are under constant attack. At the end of the day, these are
actually attacks on organizations’ IT environments. ... “There does exist a
very frightening risk that attackers can take over the OT environment,” as
Derbyshire puts it. To demonstrate that, he has set up an attack and
published about it in scientific circles. This should result in a better
understanding of a real OT ransomware attack. ... Finally, it is worth
noting that OT security does need more attention. Above all, they want
to contribute to the discussion about what an OT attack really is. As Van
der Walt summarizes, “IT security has been around for about 25 years, OT
security is still very young. We should have learned from our mistakes, so
it shouldn’t take another 25 years to get OT security to where IT security
is today.”
Manage AI threats with the right technology architecture

Amidst the dynamic market conditions, choosing a future-proof technology
architecture for threat management becomes almost inevitable. This
underscores the necessity of selecting the best technologies and the right
strategic approach. ... The best-of-breed approach allows companies to
respond flexibly to new threats and changes in business requirements. When a
new technology comes to market, companies can easily integrate it without
overhauling their entire security architecture. This promotes agile
adaptation and quick implementation of new solutions to stay current with
the latest technology. ... Managing an integrated platform is less complex
than managing multiple independent systems. This reduces the training
requirements for security staff and minimizes the risk of errors arising
from the complexity of integrating different systems. ... Ultimately, the
choice should efficiently meet the company’s security goals. It is crucial
to invest in advanced technologies and ensure that expenditures are
proportionate to the risk. This means that investments should be carefully
weighed without incurring unnecessary costs.
Quote for the day:
"Most people live with pleasant
illusions, but leaders must deal with hard realities." --
Orrin Woodward
No comments:
Post a Comment