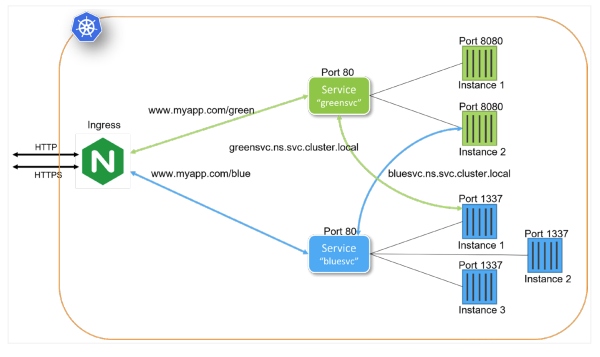
Vaadin CEO: Developers are the architects of the future

Developer passion for a project is the best barometer of its utility and potential. Developers love that Vaadin provides components and tools that make it faster and easier to build modern web apps with a great UX. End users in the enterprise now expect an intuitive and pleasing user experience, just like they are used to in their personal lives as consumers. I’m excited that we are making it easy for developers to deliver a compelling UX for the Java-based applications powering the enterprise. ... Last year, the competition for tech talent was fierce, and many companies learned the hard way that if you’re not intentional about your culture, your talent can quickly find a new workplace that provides something that better meets their culture needs. Part of that is investing in understanding what developers do, understanding the technologies they use, listening to pain points, and smoothing the day-to-day path so they can do what they do best. You need to offer flexibility—not just in terms of work/life balance and autonomy, but also maintaining an agile enough environment to account for new tool preferences and process efficiencies as determined by the developers.
Raising the resilience of your organization
Rather than continually tell teams what to do, leaders in resilient
organizations minimize bureaucracies and foster entrepreneurship among and
within teams. They nearly always put decision making in the hands of small
cross-functional teams, as far from the center and as close to the customer as
possible. They clarify the team’s and the organization’s purpose, provide some
guardrails, and ensure accountability and alignment—but then they step back and
let employees take the lead. The Disney theme parks provide a good example:
every employee is dubbed a cast member, and their clear objective is to create
“amazing guest experiences” within a set of guardrails that includes, among
other responsibilities, ensuring visitor safety and fostering family-friendly
behaviors. ... Another characteristic of resilient organizations is their
ability to break down silos and use “tiger teams” to tackle big business
problems. These are groups of experts from various parts of an organization who
come together temporarily to focus on a specific issue and then, once the issue
is addressed, go back to their respective domains.
Government ups cyber support for elderly, vulnerable web users

The Department for Digital, Culture, Media and Sport (DCMS) said research had
shown many people struggle to engage and benefit from the range of digital media
literacy education that is available for reasons such as limited experience or
lack of confidence in going online, lack of awareness of how to access such
education, and lack of availability of same. It created the Media Literacy
Taskforce Fund earlier this year as one of two funding schemes pitched at
targeting hard-to-reach or vulnerable groups through community-led projects. The
other scheme, the Media Literacy Programme Fund, is set to deliver training
courses, online learning, tech solutions and mentoring schemes to vulnerable web
users. Grant recipients from the first fund include: Fresherb, a social
enterprise working with young people to develop podcasts – aired on local radio
stations – that explore issues around online dis- and misinformation; Internet
Matters, a Manchester-based charity providing media literacy training for care
workers and school leavers
Dell, AMD, IBM, and Strangeworks Dig into Quantum’s Future

Besides simply getting quantum computers to work, there are many questions about
what financial applications will be able to actually do better on quantum
systems than classical resources. Optimization is often touted, but perhaps
wrongly so, said IBM’s Prabhakar. “There are basically three areas which are
interesting: there’s simulating nature, there is optimization, and then there is
machine learning,” said Prabhakar. “Initially, when we started working with
banks, right – JPMC is a client of ours as is Goldman Sachs and others – they
started looking at optimization. But it was very clear that there are classical
methods which are actually advancing as quickly in optimization. So, if you’d
asked me three years ago, my answer would have been optimization. Now we are
realizing it’s not optimization, it’s probably machine learning-based analysis,
which are going to have first early use cases. “If you look at the work our
clients are doing, you will see that a lot of them are actually not making the
decision right now on which of these three areas they want to work on.
Tech in turmoil: Talent disruption in India’s IT sector and the ‘M’ word

The issue of ‘moonlighting’ has been doing the rounds of late. It got wider
attention after Wipro chief Rishad Premji equated it to cheating. Several other
companies have also raised their concern, with a few of them even sacking
employees for moonlighting. Wipro recently fired 300 employees for moonlighting.
Additionally, it has announced to open offices four days a week with employees
needing to attend office physically at least three days in a week. This was done
to adopt a flexible approach to make teams experience and build meaningful
relationships at work. CN Ashwath Narayan, the IT minister of Karnataka, asked
those who moonlight to leave the state, saying freelancing beyond office hours
is “literally cheating”. IT and tech giant IBM, too, sent a strong note to its
employees over moonlighting. In a note to employees, Sandip Patel, India and
South Asia head of IBM, wrote: “A second job could be full time, part time or
contractual in nature but at its core is a failure to comply with employment
obligations and a potential conflict of interest with IBM’s interest.”
Cyber Ratings as Measures of Digital Trust
Companies have added cyber reputation management practices to their
cybersecurity organizations to manage these public cyber ratings. Several firms
provide services in the security rating category, each with its own models and
algorithms. Cybersecurity teams subscribe to one or more of these services to
manage the data used in such ratings. They also subscribe to monitor their
ever-growing list of third parties and look for weaknesses that might bring
about cyber incidents. Proxy advisors use these same rating services to
supplement financial data in annual proxy statements. Other use cases include
cyber insurance underwriters looking for evidence-based reasons to reject
applications and assist clients in improving their control environments. At the
core, such practices increase trust in the digital economy. Credit ratings are
an apt model for implementing trust models. Like corporate credit ratings, they
can be done with or without involvement from the rated entity. They can also be
made available to the public (like a security rating). In-depth analyses can
also be done and shared privately (think of this as a pen test or security
assessment).
Introduction to Cloud Custodian

By automating a lot of the tedious policy management away, Cloud Custodian
could reduce risk and accidents through more streamlined cloud governance. “It
solves the natural problems when infrastructure is in everyone’s head,” says
Thangavelu. By aggregating ad-hoc scripts and unifying policies across an
organization, you could immediately instigate new rules without manually
reminding all members of an organization, which could take years. For those
familiar with Open Policy Agent (OPA), you may notice some overlap in the
objectives, as both are engines for enacting cloud-native policies. Compared
to OPA, Cloud Custodian has some developer experience perks. For one, you
don’t have to use Rego, as the policies are written in YAML, which is a
familiar configuration language for DevOps engineers. Cloud Custodian uses
abstractions on event runtimes for each cloud provider. Furthermore, compared
to OPA, you don’t need to bind the engine for a particular problem domain,
says Thangavelu, as Cloud Custodian is specifically bounded to cloud
governance and management.
Data Security Takes Front Seat In Industrial IoT Design
Even apparently mundane applications, such as smart home utility meters, are
targets of opportunity for thieves looking to steal power from the grid.
Thankfully, data breaches have appeared in the headlines often enough that
customers are awakening to the need for security as a core component of their
technology solutions. Increasingly, my group is engaging earlier in the design
process to help customers better understand how to adequately provision and
scale their devices with a combination of hardware-accelerated cryptography,
secure key storage, and some form of physical protection. ... It is important
to understand which tools to use and when, starting with the basic building
blocks and moving on to complete solutions. It’s the equivalent of buying a
four-digit combination lock from the hardware store. They all come set to
“zero,” and we help customers find the best way to program the lock. As the
world’s devices, systems, appliances and IIoT networks adopt more technology
layers, it’s crucial to ensure that, as these building blocks are assembled,
their attack surface is as small as possible.
The Challenges of Ethical Data Stewardship

A real challenge for businesses is how to manage third-party data. It often
has no control over how that data was gathered or how its partners use the
data it provides. Another challenge that is often overlooked is data that
comes as part of an acquisition of a company. How do you extend ethical
controls to that? Langhorne believes that Precisely is aligned in thinking
about these different aspects, needs and requirements. Although she is new to
the company, she sees Precisely’s privacy journey continuing to mature. In the
short term, she says, “we have principles that we follow and compliance
expectations. In considering the suppliers of our data, we do due diligence.
We also have contracts with obligations, and we are very concerned about the
quality of our data because that is part of our brand promise. It is about
data integrity, and that means having data you can trust. These same
principles extend to our M&A activity, an area we have a lot of experience
in having acquired seven businesses in the past two years!
Technology Feeds Sustainable Agriculture

For now, Ganesan says, the biggest problem is the lack of a holistic loop to
address sustainability. While farmers are open to innovation, particularly
through technology, they often have difficulty embracing sustainability
because their suppliers -- which sell seeds, chemicals, and other products --
are slow to adopt lower carbon practices. “We’re seeing progress but it’s
still a bit of the wild, wild west,” he says. “In many cases, there’s a lack
of coordination within industries and by governments.” There are some
encouraging signs, however. For instance, in February 2022, the United States
Department of Agriculture announced that it is investing US $1 billion in
companies in order to reduce greenhouse gas emissions and fuel innovation
related to climate-based technologies. Ganesan believes that the agricultural
industry has only scratched the surface about what’s possible with precision
technology and analytics. “A key is to develop technologies that not only
drive improvements but also create value for farmers. This will accelerate
sustainability,” he notes.
Quote for the day:
"Don't be buffaloed by experts and
elites. Experts often possess more data than judgement." --
Colin Powell