Addressing the Complexities of Cybersecurity at Fintech Enterprises

Effective IT governance is the cornerstone of cybersecurity as it is about
leadership: how leaders treat IT as a cost-center vs. as an enterprisewide
strategic asset. Governance is made more complex for central banks and
regulatory and complex supervisory authorities due to regulation, supervision
and compliance. There are many global models, frameworks and standards that
can be referenced for complete cybersecurity governance and management, but
ultimately, a mature organization chooses its own preferred guidance. The US
National Institute of Science and Technology (NIST) Cybersecurity Framework
(CSF). the US Federal Financial Institutions Examinations Council
(FFIEC) Cybersecurity Assessment Tool, the International Organization for
Standardization (ISO) standard ISO 27000 and COBIT® are valuable resources for effective IT governance. These
frameworks clearly describe roles and responsibilities of top management,
importance of IT strategic alignment to achieve the enterprise objectives,
importance of leadership and top management support to address IT and
cybersecurity issues, importance of effective IT risk management, and proper
reporting strategies.
CIO Guy Hadari on the management skills that set IT leaders apart
As Hadari sees it, “The challenge is that most up-and-coming IT professionals
are trained to be technology implementers and innovators, and so are ill
equipped for the management aspects of the job,” something that he experienced
personally. In his first few years as CIO, Hadari’s comfort zone was data,
analytics, and statistics, and that was the lens he used to lead IT. ...
Hadari encourages his team to use data, surveys, and conversations to
understand the perceptions of IT, and the problems that create those
perceptions. He finds that comparing how IT rates itself to how the business
rates IT reveals a great deal about where IT needs to focus. “Collecting all
of that information is not an easy process, but it is the beginning of
change,” says Hadari. “It means that we can accept our challenges, bring them
out into the open, and do something about them.” At Biogen, Hadari’s extended
leadership team, which is one level below his senior IT leadership team, owns
the strategy and plan for IT improvement. “They build it, execute on it, and
own it,” he says.

Different employee segments will require different messaging. The IT group
will benefit from different messaging than the sales group. Don’t make the
mistake, though, of believing IT employees don’t need security awareness—they
do. Security teams should take steps to understand employees’ current
comprehension of security messaging and where gaps may exist. And, of course,
security awareness marketers need to understand the social and behavioral
drivers of employee actions. What’s important to them? What motivates them?
What are they concerned about? You can then create messaging to address
employees’ pain points or motivators—to give them some reason to act, or not
act, based on what they hear and learn. ... Security is a journey and a
conversation, not a destination and a directive. Thinking like a marketer and
taking steps to segment, understand and effectively connect with employees
based on their needs, interests and concerns can help to better engage the
organization in its cybersecurity efforts.
Young people in tech unhappy despite inclusion push

Almost half of younger people in the tech sector have at some point felt
uncomfortable at work because of their gender, ethnicity, background or
neurodivergence. Young people not already in the sector claimed they’re not
confident about how to make tech their career, with a number of misconceptions
about what is involved in a tech career still acting as a deterrent. Almost
15% of the young people asked who were not already in the sector said they
know nothing about tech careers, with 29% believing they don’t have the right
qualifications for a job in the sector. Women have more doubts about the
sector than men – 23% of women believe their maths and science skills aren’t
up to scratch enough for a tech job, compared with 13% of men; and 19% of
women doubt they’re smart enough for the sector, compared with 13% of men. ...
Only 5% of young people said that a lack of ethnic diversity is a deterrent to
pursuing a tech career, although this varies based on the ethnicity of the
person asked, with the breakdown being: 9% of young people from mixed raced
backgrounds, 10% of people from an Asian background, and almost 36% of people
from a black background.
4 Reasons Why Talent Development Is So Important To Your Business

In the age of employee turnover and the Great Resignation, organizations in
nearly every field are finding it more difficult than ever to attract and
retain top talent. As a leader, you need to make talent development a personal
priority to stay competitive in recruiting and keeping the best people. Have a
solid plan and communicate it widely to both prospective recruits and current
employees. A truly thoughtful talent developing program lets people know how
much you value them. It strengthens talent in new directions. Employees want
to know that their leader sees their potential, and it’s important to be
intentional about recognizing and reinforcing the strengths of your people. A
one-size-fits-all approach to talent development isn’t good enough—you need to
design a program for each individual based on their strengths, their goals and
the organization’s needs. When you strengthen your talent, you strengthen your
leadership. It improves productivity. According to a recent Gallup study,
helping your employees make full use of their employees skills and strengths,
and providing them with opportunities for growth and improvement, can make
them up to six times more productive.
8 ways to get out of a career rut

Consider the millennial who felt stuck at a small company with no room for
growth. Or the older generation of workers who thought they should retire
early because the future was so uncertain and accepting a complete shift to
digital felt daunting. For Gen Z, the prospect of never meeting managers or
colleagues – because of virtual interviews and remote jobs – was foreign and
left some without a sense of belonging. Not only were we physically absent
from workspaces, but many of us also struggled mentally with the sudden,
enormous changes to our daily routines and goals. It became a time of
contemplation, where many professionals began reassessing their careers (and
lives). And the realization for many? They felt stuck. What are your options
if you want to take a big leap out of your current situation? How do you find
motivation, especially after a couple of very stressful years outside of your
control? What inspires you to take on a new challenge?
The Dark Side of Open Source

Lack of interest, patience, and time; change of profession and creative
differences are some of the issues that push developers to close an
open-source project. But the biggest reason why developers quit is that they
drain out of energy. People like John Resig, creator of jQuery, and Ryan Dahl,
creator of Node.js, too have most likely exited from their respective OSS
project because they couldn’t keep up with the energy it demanded. Fakerjs’
Mark Squires’ sentiment was understandable. It’s very difficult to offer
non-paid work for a long period of time and at a certain point an open-source
project can become more hassle than it’s worth. It also depends, of course, on
your motivations for developing open-source software, but more on that later.
The best open-source projects are typically those that are maintained by
developers who are compensated for their work on them and can maintain a
work-life balance. Those who can devote their entire attention on enhancing
them.
Back to Basics: Cybersecurity's Weakest Link
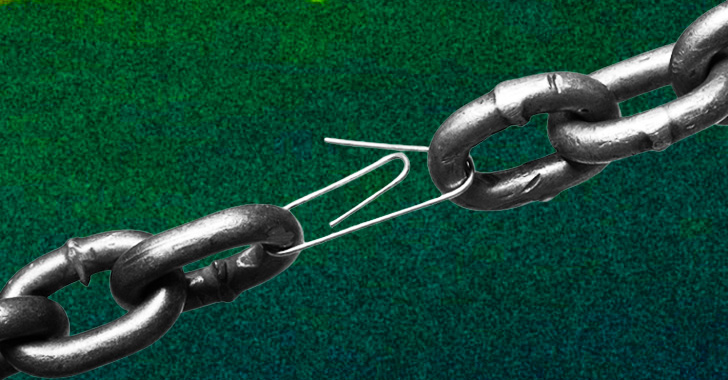
Social engineering was a driver for hacking over 20 years ago and, apparently,
we still haven't moved away from it. Adding insult to injury, successful
social engineering isn't restricted to non-technical organizations. It's very
plausible that an unsavvy user in a backwater government department might fall
for social engineering, for example, but much less so someone working at a
leading tech firm – and we see that both Uber and Rockstar Games were impacted
by social engineering. At some point, as a cybersecurity practitioner with the
responsibility of educating your users and making them aware of the risks that
they (and by extension the organization) are exposed to, you'd think that your
colleagues would stop falling for what is literally the oldest trick in the
hacking playbook. It's conceivable that users are not paying attention during
training or are simply too busy with other things to remember what someone
told them about what they can click on or not. However, social engineering
attacks have so consistently been in the public news – not just cybersecurity
news – that the excuse "I didn't know I shouldn't click email links" is
getting harder and harder to accept.
Cyber insurance explained: What it covers and why prices continue to rise

For technology and compliance lawyer Jonathan Armstrong, the most significant
driver of change in cyber insurance is demand for financial protection from
litigation against organizations in the wake of cyber incidents. “We have seen
that an attack or breach can be followed in the next day or so by lawyers
claiming that they are investigating litigation against the company that has
been hit.” This issue has been under the spotlight recently in the Lloyd v
Google case in the UK. Richard Lloyd alleged that Google collected data from
around 4 million iPhone users between 2011 and 2012 regarding their browsing
habits without their knowledge or consent for commercial purposes, such as
targeted advertising. He looked to bring representative action on behalf of
all affected individuals against Google for compensation, which Google
opposed. The UK Supreme Court sought to establish whether such a claim for a
breach of data protection legislation can succeed without distinctive personal
damage and if claimants can bring group action on behalf of unidentified
individuals, including people who may not even be aware that they were
affected.
Achieving faster time-to-market with data management

When companies manage their product data efficiently, they can be flexible
while launching their new products. With error-free product data of new items,
brands can customise information as per the marketplace and the promotion
period. PIM possesses high-quality product information that is scalable, and
offers complete freedom to be deployed across any technology environment.
Product data can be easily imported from various vendors in multiple file
formats and mapped to a single point of truth. ... In the wake of
technological advances, fluctuating consumer expectations, competitive
pressures, and turbulent market dynamics, operational agility is vital to
survive and succeed. Faster time-to-market is one of the parameters that
determines business agility. To continuously deliver high-quality, novel, and
faster services, companies need to deploy PIM, which enhances product
information, and improves conversion rates and customer retention. Businesses
can also make data-driven decisions and create joyous customer journeys with
the available data.
Quote for the day:
"If you don't demonstrate leadership
character, your skills and your results will be discounted, if not
dismissed." -- Mark Miller
No comments:
Post a Comment