
One aspect is to implement change management on the automation, including the
scripts, config files, and playbooks, used to manage the network. The use of
code management tools helps with this: check-out and check-in events help
staff remember to follow other parts of proper process. Applying change
management at this level means describing the intended modifications to the
automation, testing them, planning deployment, having a fallback plan to the
previous known-good code where that is applicable, and determining specific
criteria by which to judge whether the change succeeded or needs to be rolled
back. ... Putting in place automation to lock-in a network state is a change
management event, and in a sense, a change to the architecture; creating it
and putting it into production needs to go through the whole approval and
deployment process, and all future changes need to be made with its presence
and operation in mind—considering it has to be part of future change
management evaluations.
The Impact of Cybersecurity on Consumer Behavior

In addition to imperiling consumers’ PII, cyberattacks also cause consumers to
feel helpless about their ability to protect their own data. According to
ISACA’s survey report, about one in five consumers in the US, UK and Australia
experience a sense of resignation that there is nothing they can do to protect
themselves from cybercrimes. Nearly half of consumers in the US, UK and
Australia think that they are likely to be a victim of cybercrimes. Although the
initial cyberattack occurs just once, the lasting impacts of that attack
continue for an unknown amount of time. If consumers’ data are stolen during
cybercrimes and are subsequently sold to malicious actors, one attack can turn
into a headache of fraud, identity theft and social engineering scams for the
foreseeable future. Cyberattacks that compromise personal medical information in
the healthcare industry or important account details in the financial services
industry can cause emotional and financial stress. In the United States, the
public is beginning to worry about state-sponsored cyberattacks against national
security and defense systems and government agencies, in addition to their own
personal information.
Digital transformation is brewing at Heineken

Heineken says it is fully committed to the path to net zero – and that there are
efforts around the organisation to achieve this goal. Sustainability is top of
mind in the strategies and tactics for digital transformation. “We have several
fully green breweries,” said Osta. “This started in Austria a few years back
with Goesser and is now being replicated in markets including France and Brazil.
We also have 3D printers in 40 breweries, with 25 more in plan for this year. 3D
printing on-site is very effective when it comes to spare parts management as it
reduces carbon emissions. “There is also an incredible effort being made on the
data side in terms of what we can estimate and measure. We are always looking at
emerging data standards for better quality data to exchange across the ecosystem
with our suppliers. The challenge is that often in sustainability we are faced
with dark data – data that is critical but not collected or visible. “The
corporate value chain (Scope 3) reporting requires an ecosystem approach of data
exchange.
Digital Identity Bill Passes Key Senate Milestone
The legislation stops short of mandating national IDs. It would create a task
force to create standards and recommend a voluntary program for states, local,
tribal and territorial governments to verify identities online for "high-value
transactions." About a half-dozen states have already rolled out mobile drivers
licenses in the pilot phase. Nationwide standards would help ensure these new
IDs are secure and provide a guide for others states. Grant says online
verification could be offered in a variety of forms, such as on-demand
validation services, which could become part of the credit card application
process, or a mobile app on smartphones that people could carry in their
pockets. "Identity is very personal," Grant says. "You're probably going to need
to create a few different channels for Americans to be able to tap into these
authoritative sources. I'd be thrilled to have a mobile driver's license app on
my phone. Others would say, 'I don't want to have an app from the government on
my phone.'"
Do You Fit Cybercriminals’ Ideal Victim Profile?

The Bad Actors Know About You. And they know exactly why you keep putting off
addressing your cybersecurity vulnerabilities. Don’t give attackers any more
advantages when it comes to breaching your law practice. My advice?Be more
reticent when it comes to sharing personal information on social media. (For
example, if you work from home, register as an online business when you set up
your Google Business profile so that your physical address and photos of your
home won’t show up on Google Maps.) Be less trusting of seemingly
friendly messages and emails that cross your transom. While technology
solutions can greatly improve your defenses, humans are the last line of
defense. Don’t click on attachments from unknown senders. If a large file
arrives from someone you haven’t heard in for a long time, call them to say
hello and ask about the email before you click. Be more vigilant in general —
including asking qualified cybersecurity professionals to assess your current
level of protection and recommend safeguards. Rereading this, even I got
stressed.
Five Data-Loading Patterns To Boost Web Performance
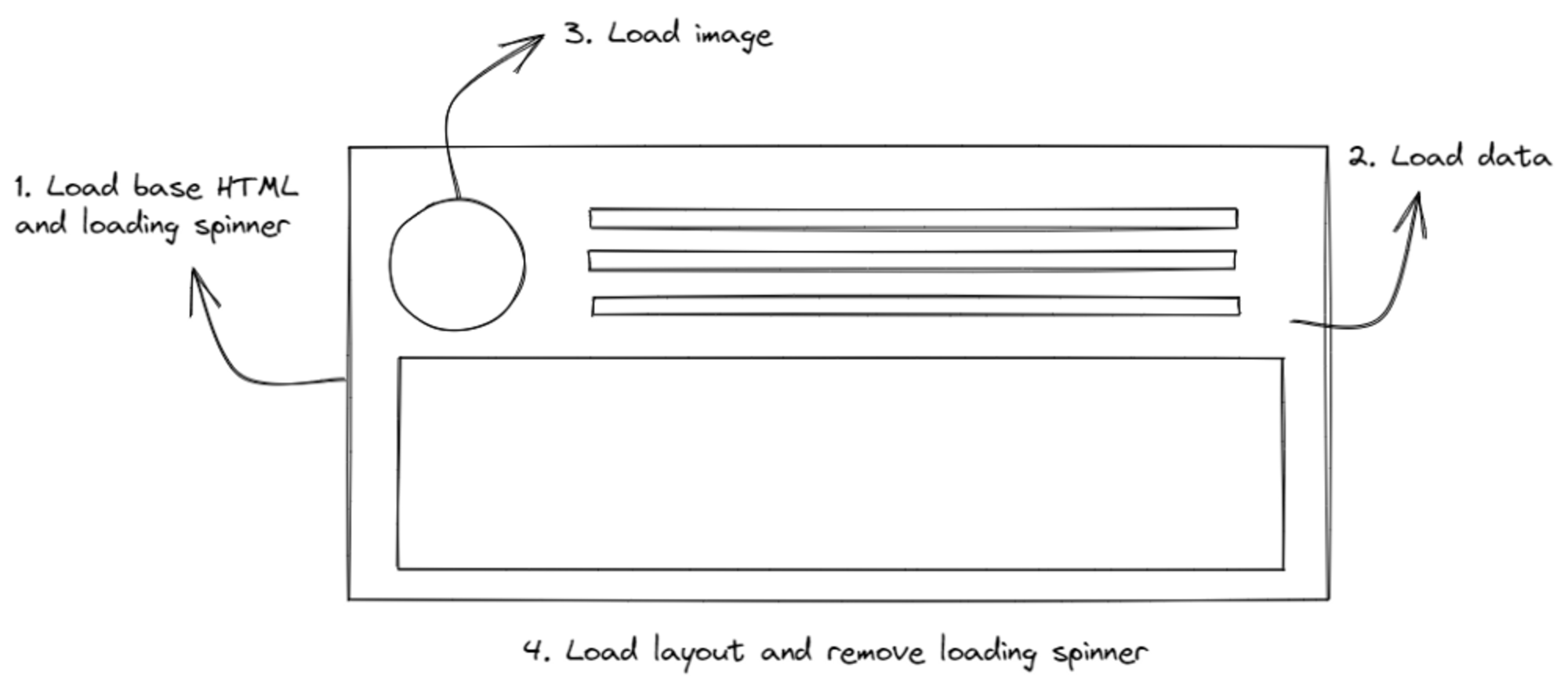
No one likes a white blank screen, especially your users. Lagging resource
loading waterfalls need a basic placeholder before you can start building the
layout on the client side. Usually, you would use either a spinner or a
skeleton loader. As the data loads one by one, the page will show a loader
until all the components are ready. While adding loaders as placeholders is an
improvement, having it on too long can cause a “spinner hell.” Essentially,
your app is stuck on loading, and while it is better than a blank HTML page,
it could get annoying, and visitors would choose to exit your site. ... Modern
JavaScript frameworks often use client-side rendering (CSR) to render
webpages. The browser receives a JavaScript bundle and static HTML in a
payload, then it will render the DOM and add the listeners and events triggers
for reactiveness. When a CSR app is rendered inside the DOM, the page will be
blocked until all components are rendered successfully. Rendering makes the
app reactive. To run it, you have to make another API call to the server and
retrieve any data you want to load.
What Will it Take to End the Public Sector’s Cybersecurity Talent Gap?

The public sector can be deliberately hard to understand. From the multiple
terms and acronyms used to describe programs and agencies, to an incredibly
complex technological infrastructure, beginning a career in government can
seem daunting. That is compounded when realizing even entry-level roles often
require at least five years of experience. Many cybersecurity job descriptions
highlight requirements for certifications and achievements, which can only be
earned after a certain amount of time in the field. Instead of having such
high expectations for entry-level candidates, which will only continue to
leave hundreds of jobs unfilled, government agencies need to update their job
descriptions to be truly entry-level and seek out college graduates or
individuals who might have just completed a cybersecurity bootcamp or training
program—and who have yet to gain any experience. It would also be beneficial
to look at talent that might not come from a STEM field. Candidates with
backgrounds in history or English can bring skills like analytical thinking
and communication to the table—skills that are often a lot harder to teach
than computer science.
8 strange ways employees can (accidently) expose data

Video conferencing platforms such as Zoom and Microsoft Teams have become a
staple of remote/hybrid working. However, new academic research has found that
bespectacled video conferencing participants may be at risk of accidently
exposing information via the reflection of their eyeglasses. ... Users may not
associate posting pictures on their personal social media and messaging apps
as posing a risk to sensitive corporate information, but as Dmitry Bestuzhev,
most distinguished threat researcher at BlackBerry, tells CSO, accidental data
disclosure via social apps such as Instagram, Facebook, and WhatsApp is a very
real threat. “People like taking photos but sometimes they forget about their
surroundings. So, it’s common to find sensitive documents on the table,
diagrams on the wall, passwords on sticky notes, authentication keys and
unlocked screens with applications open on the desktop. All that information
is confidential and could be put to use for nefarious activities.”
Used servers: Bargain or too good to be true?

Used equipment can run as well as new equipment “when you find the right
seller,” says Peter Strahan, founder and CEO of Lantech, a managed IT services
provider. “This allows you to rapidly cut the costs of a data center with used
equipment.” In addition, deploying used IT equipment is generally good for the
environment, Strahan says. “While the equipment could theoretically be
recycled, it takes a lot of manpower,” he says. “Finding a use for it after it
becomes obsolete saves a lot of time and money when it comes to recycling and
stops the equipment going to the landfill.” A lot of companies “value the
‘green’ benefits of redeploying hardware,” says Cameron James, executive vice
president of CentricsIT, a global IT services provider. “The best way to
reduce IT waste is to use any product to its maximum lifespan, without
compromising on performance. This is easy to do. Many used products are
N-1—just one generation back from the latest OEM lines.” It can also make
sense to buy used equipment if an organization has moderate powering needs in
its data center, Strahan says. “If you have large powering needs, you will
need the most efficient equipment,” he says.
Carbon copies: How to stop data retention from killing the planet

So what can be done about it? It is a question that has been plaguing the IT
industry for years, and the lack of a definitive answer often makes it easier
to just turn on another air-conditioning unit and look the other way. But
that’s causing even more harm. So what are the alternatives? Storing less data
appears to be an obvious answer, but it would be almost impossible to
implement, because who decides what parameters are worth recording and what
are not? The BBC learned this the hard way when it trashed much of its TV
archive during the 1970s and 1980s, assuming that it would be no use. Then
came the VCR, the DVD player and, of course, streaming. Ask any Doctor Who fan
and they will grimace at the number of early episodes of the long-running
Sci-Fi series that have been lost, perhaps forever, because of a lack of
foresight. So, that’s the case to justify digital hoarding. But it all has to
be stored somewhere, and those facilities have to be environmentally
controlled.
Quote for the day:
"Leadership cannot really be taught.
It can only be learned." -- Harold S. Geneen
No comments:
Post a Comment