Australia becoming hotbed for cyber attacks

“Cyber criminals are targeting the personal data of Australians for financial
gain – to sell, to hold to ransom, or to commit financial fraud and scams,” said
Reinhart Hansen, director of technology at Imperva’s CTO office. “During the
pandemic, many organisations inadvertently created more opportunities for these
bad actors. Many rushed their online implementations and transformation
projects, taking shortcuts that left them vulnerable to exploitation. “Now we’re
seeing a large uptick in common, off-the-shelf and automated type attacks that
hackers are continuously recycling and using against Australian targets,” he
added. Hansen noted that threat actors have also been looking for known
weaknesses and vulnerabilities in applications and application programming
interfaces (APIs) to gain access to the data repositories that sit behind them.
“Their ultimate aim is to exfiltrate data at scale that will allow them to build
citizen profiles that are used as the basis of their illegal activity,” he said.
The most heavily targeted industries in Australia were financial, retail and
business services.
To Recruit and Retain a Strong Team, Live the Culture You Talk About
As leaders, if we talk about communication and expect people to follow, that
communication needs to start with me. We need to be open to it, like lanes of
fluid traffic in both directions, not stocked up silos hoarding information
for ourselves. I need to communicate what will happen to my team and stay open
to taking their feedback. ... We look for similar values when building
personal relationships, but this idea is more difficult as a company. I may
not expect everyone to share the same politics, but I expect team alignment
around certain values. We should all acknowledge the importance of diversity
and respect the humanity of each other. We should share a sense of optimism
for the company and a desire to contribute to its growth. As leaders, we need
to live the story we tell when a great contributor to our team crosses the
line. When the behavior is illegal, that decision is a little easier, but
determining when behavior crosses an immoral or unethical line can be in the
eye of the beholder. However, if something is clearly over the line in my or
my employees' minds, I need to take action and be consistent about those
opinions.
Waterfall won the war with Agile!

The dream of a decentralised democratic organisation with low atrophy that can
swiftly respond to the needs of our markets is not a pipe dream. To do so we
need to shift from an Alpha model for business to a Beta model. However, we
continuously allow Alpha to prevail. The focus of agile on the decentralised
dream failed because we allowed it to. We, and by we I mean agile
practitioners, allowed and continue to allow organisations to believe that
they don't have to really change, that this is just a team thing, and to keep
the departments and the steering committees and yearly budgets. We are
complicit in these continued malformed practices. ... We need to reshape our
focus from sustaining the Alpha models to keep people complacent and happy to
challenging them and actively promoting Beta models and practices that work in
those models. We already have the building blocks to do this in the Agile
Manifesto, the Scrum Guide, the Kanban Guide, the Nexus Guide, LESS,
Scrum@Scale, and many more. What we need to add is the tools that we need to
change the organisation; changing teams is easy.
Making product inclusion and equity a core part of tech
I think the world has had a reckoning over the past two years, with many
candid conversations kicking off. There’s been a lot of vulnerability and
accountability, frankly, around making sure that people have inclusive and
equitable experiences across the board in everything they do. When product
teams start to think about product inclusion and equity, I talk to them about
the “curb cut effect.” The curb cut in sidewalks was originally made in the
‘70s for wheelchair users, but we all use it now, whether it’s people with
skateboards, suitcases, or shopping carts. The critical thing to understand is
that building for a historically marginalized group results in better outcomes
for everyone. There are a lot of examples of that throughout history; another
is closed captioning. So even though it feels amplified now, decades of work
have helped to ensure that those who have historically not been at the center
of development and design can have their voices involved throughout critical
points in the process.
8 Reasons Scrum Is Hard to Learn (but Worth It)

The idea of estimating in story points can definitely be a challenge for many
team members. I can almost hear them thinking, “I have a hard estimating in
days and now I have to estimate in an abstract relative unit I’ve never heard
of before?” Story points are a definite challenge, yet they’re worth the
effort. As abstract relative estimates of effort, story points enable better
conversations about how long work will take. Without story points, a senior
programmer and junior programmer have conversations that devolve into, “That’s
how long it will take you, but it would take me twice as long.” And then the
two pick an estimate that is horrible for one of them or, perhaps even worse,
they split the difference. With story points, the senior and junior
programmers can consider adding a new feature and both agree it will take
twice as long as doing a simpler feature. They then give the bigger item an
estimate twice that of the simpler item. Estimating in this relative manner
allows developers to agree even if they would never be able to agree on how
many hours or days something would take.
Design Thinking Improves Your Data Science
As data scientists, our first instinct is to begin to understand the data we
are going to use to solve our problems. However, we need to understand what is
beyond the data to the people involved in this problem. We can have all of the
data in the world but if we do not know how users or stakeholders interact
with the product and understand it in their terms, we cannot possibly make a
solution that is going to fully solve their problem. ... My favorite way to
approach generating problem statements is to use HMW statements. In this
process, everyone writes down problem statements starting with the phrase “How
might we…”. They are usually generated individually and voted on by the group
to obtain the best problem statement. HMW statements are written positively to
make sure how we remember how the user should feel. ... Now that you have our
problem statement, you will need to think about the different ways the problem
can be solved. In this step, any idea is a good idea, focusing on quantity
over quality.
JIT vs. AOT: How to Pick the Right Approach
What a just-in-time compiler can't do is compile ahead-of-time. What an
ahead-of-time compiler does is it takes all the code and it compiles it to
your binary before you ever run the program. It could do all that and avoid
all the later work of doing this. What ahead-of-time compiler can't do is
compile just-in-time. The annoying thing is the choice. If you have to choose
between them, I am definitely on the just-in-time side. I've got some strong
arguments for why, because you just get faster code, period. It's provable.
The real question is, why do we have to choose? ... It's absolutely true that
with ahead-of-time compilation, people feel like they can afford to throw a
lot more analysis power at the optimizations, and therefore lots of times
people will say, this analysis we can do ahead-of-time. In reality, anything
an ahead-of-time compiler can do a just-in-time compiler can do. It's just a
question of, can you afford doing? Do you want to spend the time while you're
running the program to also do that? That's one direction.
Chaos theory eliminates quantum uncertainty

The most important reason stems from a quantum phenomenon that Schrödinger
himself named entanglement. Specifically, two particles can be emitted from a
source, such that the properties of the two particles – e.g., their angular
momenta (also known as spins) are correlated. This itself is not necessarily
strange. However, the Northern Irish physicist John Bell showed that, under
seemingly reasonable assumptions, these correlations, suitably combined, are
limited in size. This is called Bell’s theorem. The 2022 Nobel Physics Prize
was given to three physicists (Alain Aspect, John Clauser and Anton Zeilinger)
who showed that in practice, the combined correlations can exceed this limit.
Hence one or more of these seemingly reasonable assumptions must be wrong. The
standard interpretation of this experimental result is that it confirms that
quantum uncertainty is ontological, not epistemological. That is, uncertainty
is a feature of reality itself, not a reflection of the limits of our
knowledge. Of course, this is such a startling conclusion that physicists have
looked for other ways to explain Bell’s theorem.
Get used to cloud vendor lock-in

Granted, now the game is a bit different with higher stakes. Many cloud
providers offer the same operating systems and processor options, the same
databases, and even the same ops and security tools. So, why is vendor lock-in
still a trade-off? As an aside, if you just announced that you’re off to build
systems that completely avoid vendor lock-in, I will wish you good luck.
However, unless you want consistently crappy applications, you’ll have to
leverage native security, native infrastructure as code, serverless systems,
etc., that are usually supplied by different providers as native services,
which is why you’re on a public cloud in the first place. If we move to the
most feature-rich public cloud platforms, it’s to take advantage of their
native features. If you use their native features, you lock yourself in to
that cloud provider—or even lock yourself in to a subplatform on that cloud
provider. Until there are alternatives, you better get used to
lock-in.
Understanding the Four Domains of Enterprise Architecture
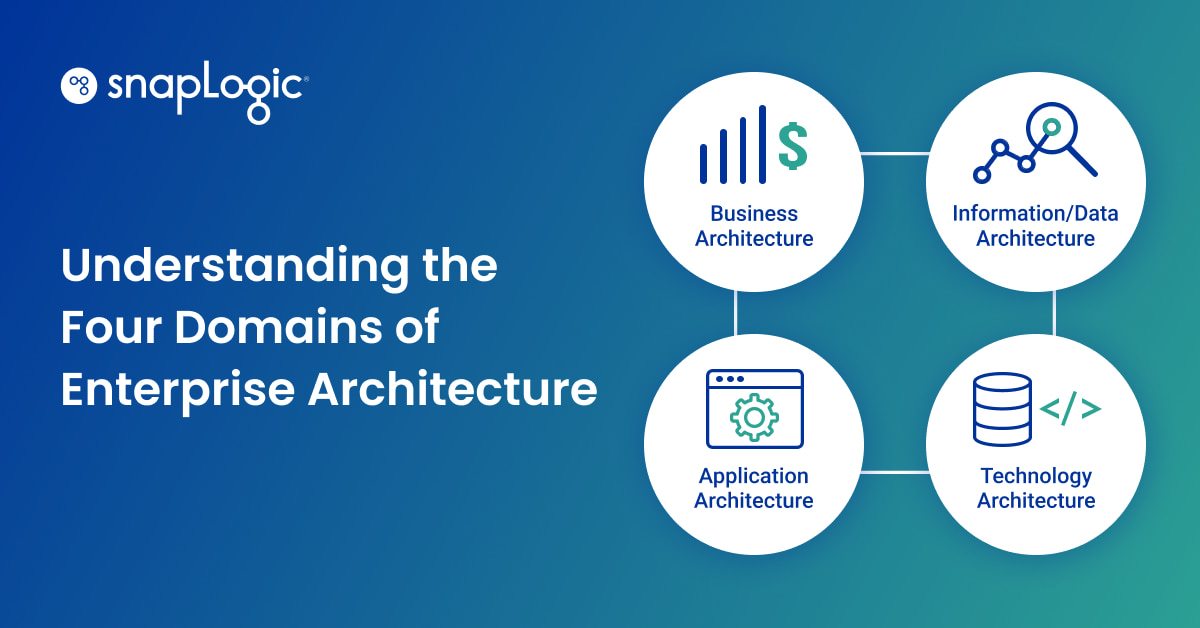
The technology architecture domain encompasses all infrastructure and
enterprise uses to support the goals and execution of the business,
information and application processes. It covers all logical hardware and
software apps, including front-end systems, back-end infrastructures, cloud
and on-site platform technologies, IoT, networks and communications. To
demonstrate the difference between application and technology architectures,
let’s consider an enterprise in the e-commerce industry. The e-commerce app
falls under the technology architecture domain because it generates the data
for the business — the number of visitors per day or sales per day. An
analytics tool like
Tableau, which helps
translate the data generated into a comprehensible form and distributes it to
where it’s needed, is under the application architecture domain. An enterprise
architect in this domain would define the requirements of the hardware and
software infrastructure needed to power the resources in the application and
data architectures that enable and optimize business processes.
Quote for the day:
"Always be yourself, express yourself,
have faith in yourself, do not go out and look for a successful personality
and duplicate it." -- Bruce Lee
No comments:
Post a Comment