Work from home, phase 2: What comes next for security?

From a security perspective, forward-thinking CISOs are now on to phase 2 focused on situational awareness and risk assessment. This is directly related to the fact that a lot of LAN traffic has been rerouted to WANs and internet connections. The goal? Scope out the new realities of usage patterns and the attack surface. To gain this level of visibility, organizations are deploying endpoint security agents to assess device posture and system-level activities. Think Tanium agents and EDR software from vendors like Carbon Black, CrowdStrike, and Cybereason. Security pros also recognize that employee home networks may be populated with insecure IoT devices, out-of-date family PCs, etc., so I’ve heard of instances where security teams are doing home network scans as well. Finally, there is an increased focus on network traffic monitoring travelling back-and-forth on VPNs or directly out to SaaS providers and the public cloud. Leading organizations are also ramping up monitoring of cyber-adversaries and threat intelligence, looking for targeted attacks, COVID-19 tactics, techniques, and procedures (TTPs), IoCs, etc.
.NET for Apache Spark brings enterprise coders and big data pros to the same table

Microsoft has worked hard to make the Spark.NET barrier-to-entry quite low. Case in point: The .NET for Apache Spark Web site provides a big white "Get Started" button that guides developers through the process of installing the framework, creating a sample wordcount application and running it. It takes the developer through the installation of all required dependencies, configuration steps, installation of .NET for Apache Spark itself, and the creation and execution of the sample application. The entire guided procedure is designed to take 10 minutes, and assumes little more than a clean machine as the starting environment. In large part it succeeds (with the caveat that I had to research and manually set the SPARK_LOCAL_IP environment variable to localhost to get the sample to run on my Windows machine), and I have to say it's quite a rush to get it working. ... You can deploy your .NET assembly to your Spark cluster and run it on a batch basis from the command line if you wish. But, for C# developers, Microsoft has also enabled the very common scenario of working interactively in a Jupyter notebook. That support includes a Jupyter notebook kernel that leverages the C# REPL (read-eval-print loop) technology which, is highly innovative in and of itself. Microsoft provides an F# kernel as well.
CI/CD Pipeline: Demystifying The Complexities
CD can help you discover and address bugs early in the delivery process before they grow into larger problems later. Your team can easily perform additional types of code tests because the entire process has been automated. With the discipline of more testing more frequently, teams can iterate faster with immediate feedback on the impact of changes. This enables teams to drive quality code with a high assurance of stability and security. Developers will know through immediate feedback whether the new code works and whether any breaking changes or bugs were introduced. Mistakes caught early on in the development process are the easiest to fix. CD helps your team deliver updates to customers quickly and frequently. When CI/CD is implemented, the velocity of the entire team, including the release of features and bug fixes, is increased. Enterprises can respond faster to market changes, security challenges, customer needs, and cost pressures. For example, if a new security feature is required, your team can implement CI/CD with automated testing to introduce the fix quickly and reliably to production systems with high confidence.
Run .Net Core on the Raspberry Pi

The .NET Core Framework also runs on ARM systems. It can be installed on the Raspberry Pi. I’ve successfully installed the .NET CORE framework on the Raspberry Pi 3 and 4. Unfortunately it isn’t supported on the Raspberry Pi Zero; ARM7 is the minimum ARM version supported. The Pi Zero uses an ARM6 processor. Provided you have a supported system you can install the framework in a moderate amount of time. The instructions I use here assume that the Pi is accessed over SSH. To begin you must find the URL to the version of the framework that works on your device. ... The current version of the .NET Core framework is 3.1. The 3.1 downloads can be found here. For running and compiling applications the installation to use is for the .NET Core SDK. (I’ll visit the ASP.NET Core framework in the future). For the ARM processors there is a 32-bit and 64-bit download. If you are running Raspbian use the 32-bit version even if the target is the 64-bit Raspberry Pi; Raspbian is a 32-bit operating system. Since there is no 64-bit version yet the 32-bit .NET Core SDK installation is necessary. Clicking on the link will take you to a page where it will automatically download.
Remote working, now and forevermore?

Companies that realize the benefits of remote work during the current crisis will be more likely to continue it long term, said Zapier’s Foster. These organizations are more likely to have a good remote working strategy in place already, he said, as well as the right tools and processes to make the transition easier. “In terms of [the Covid-19 crisis] accelerating the movement, I’m fairly optimistic, but I think it will go one of two ways,” he said. “Companies with good communication systems in place that are already used to using things like chat, documents, and videoconferencing systems will see the benefits right away and will perhaps do more remote working in the future.” The opposite is also true, said Foster. “Companies who don’t have effective systems in place are winging it in a lot of areas right now. They’re going to have a hard time with this sudden transition. They are being thrust into an environment where they have no structure.” In these cases, he said, the “wrong type of management, misaligned culture, and lack of essential tools” could contribute to negative remote work experiences.
Is Edge Computing a Thing?
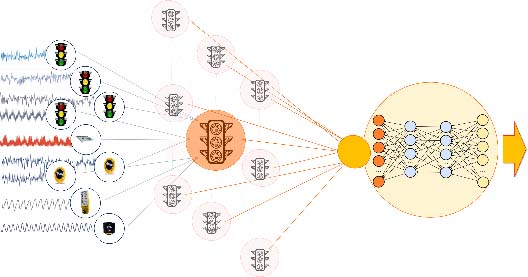
The term “edge computing” implies a generic capability that is different from cloud computing. While there are often requirements such as data volume reduction, latency or security/compliance concerns that dictate an on-prem component of an application, other than these, does edge computing have unique requirements? It does: Real-time analysis of streaming data demands that we kick the REST + database habit. But there is nothing that is unique to the physical edge. This is great news because it means that “edge applications” can run on cloud infrastructure, or on prem. “Edge computing” is definitely a thing, but it’s about processing streaming data from the edge, as opposed to running the application at the physical edge. ... Real-world relationships between data sources are fluid, and based on computed relationships such as bad braking behavior, the application should respond differently. Finally, effects of changes are immediate, local and contextual (the inspector is notified to stop the truck). The dynamic nature of relationships suggests a graph database – and indeed a graph of related “things” is what is needed.
JSON Is Case Sensitive but You Don't Have to Be
You must have learned capitalization rules in your grammar school, but the real-world search is not so sensitive to capitalization. Charles de Gaulle uses lower case for the middle "de," Tony La Russa uses upper case for "La," and there may be etymological reasons for it, but it's unlikely for your customer service agent to remember. Databases have a variety of sensitivities. SQL, by default, is case insensitive to identifiers and keywords, but case sensitive to data. JSON is case sensitive to both field names and data. So is N1QL. JSON can have the following. N1QL will select-join-project each field and value as a distinct field and value. ... In this article, we'll discuss dealing with data case sensitivity. Your field references are still case sensitive. If you use the wrong case for the field name, N1QL assumes this is a missing field and assigns MISSING value to that field.
Check Point sounds alarm over double extortion ransomware threat

“Double extortion is a clear and growing ransomware attack trend,” said Check Point threat intelligence manager Lotem Finkelsteen. “We saw a lot of this during Q1 2020. With this tactic, threat actors corner their victims even further by dripping sensitive information into the darkest places in the web to add weight to their ransom demands. “We are especially worried about hospitals having to face this threat. With their focus on coronavirus patients, addressing a double extortion ransomware attack would be very difficult. We are issuing a caution to hospitals and large organisations, urging them to back up their data and educate their staff about the risks of malware-spiked emails.” The first known case of such an attack was in November 2019 on the systems of Allied Universal, a US-based supplier of security and janitorial services to large enterprises, and involved Maze ransomware.
COVID-19 Pandemic Puts Privacy at Crossroads
It's possible to develop a contacts tracing system that protects the personal data of those infected with the virus and those who have been around them, says Vanessa Teague, a Melbourne-based cryptologist and CEO of Thinking Cybersecurity. Proximity-based location technology, such as Bluetooth, can ensure that precise location data isn't revealed while enabling an effective warning tool by knowing where people have been in close contact, Teague says. Also, it would be possible to do that so that a government couldn't identify people, either, she says. But maximizing privacy could also deprive government of a means to reach out to people and deliver important messages if someone has been exposed, she says. There's also a question of whether such a system should be mandated by a government or voluntary. "You could imagine some kind of a hybrid system, for example, where you might volunteer to notify an epidemiologist or the Department of Health if you found that you had been exposed," Teague says.
Government investigates perceptions about data sharing of health and social care

According to the National Data Guardian for health and adult social care, Fiona Caldicott, planning for this had started “long before the outbreak of the Coronavirus Covid-19 pandemic, so it’s not a reaction to it”. “However, we are already thinking about how the knowledge and attitudes of our public participants may have been affected,” she said in an article published on 14 April 2020. Caldicott then went on to explain that the NHS and social care services hold a lot of information about individuals that can be used for a number of purposes, including identify patterns and develop new ways to predict, diagnose or treat illness. However, she noted these organisations don’t always have the expertise to do so and that collaboration can be enabled by sharing data, citing he government’s efforts to encourage data-driven research and innovation. “Organisations which hold health and care data already assess public benefit or interest when deciding whether to allow it to be used to develop new medicines and technologies,” she said.
Quote for the day:
"Problem-solving leaders have one thing in common: a faith that there's always a better way." -- Gerald M. Weinberg
No comments:
Post a Comment