Indian IT desperately needed a new business model and coronavirus gave it one

Some IT companies have implemented "employee productivity trackers like webcam-based movement capture, hourly timesheet entry, tracking of keyboards, and so on, to ensure employees are working at home," Yugal Joshi, vice-president at Texas-based consultancy Everest Group, told Quartz. "This indicates a deep-rooted malaise in Indian IT/ITes industry where the senior management generally mistrusts people," he added. Two, unlike the retail or manufacturing sectors that cannot operate with current social distancing norms, the top-tier Indian IT companies and their mid-sized brethren are responsible for keeping the lights on for a large collection global companies -- some of whom are depended on people every second of the day. This includes banks, utility companies, retailers, and, of course, pharmaceuticals. With the ongoing coronavirus outbreak, all of these industries are now being serviced from the apartments and houses of India's IT workforce, which as you can imagine, is a supremely difficult and exasperating task for everyone involved. Most of IT's clients have ironclad regulatory and privacy riders that have needed to be tweaked considerably in light of coronavirus.
How a basic cross-training program can ease disruptions on the IT team
If the coronavirus hasn't disrupted your business operations yet, there's a good chance it will soon. This first wave of illness will not be the last time the coronavirus disrupts daily business operations. First companies had to adjust to remote work for all employees. The next challenge may be filling in for colleagues who are out sick or caring for family members or friends who are ill. A cross-training program can make this transition go smoothly. Sam Maley, an IT operations manager at Bailey & Associates, an IT consultancy, said cross-training can minimize disruptions and reduce stress levels due to absenteeism. "Cross-training programs are designed to build versatility and skill overlaps in your team members," he said. Jeff Fleischman, CMO at the consulting firm Altimetrik, said cross-training needs to be part of business continuity plans. "To receive buy-in from top management, quantify the impact disruption has on the business such as revenue loss, reputational risk, defaulting on contractual obligations, and failing to meet regulatory requirements, and then explain how cross-training would eliminate these risks," Fleischman said.
Kubernetes vs. VMware: Drive the choice with IT architecture

The choice to run either containers in VMs vs. VMs in containers is an architectural design decision. This is because there's a line of thought that containers are the ideal abstraction for multi-cloud application delivery. Though VMware assures admins containers and VMs are the same in vSphere, it's difficult to draw a similar comparison for Kubernetes and VMs. Kubernetes is an orchestration product that admins use primarily for containers. In theory, Kubernetes could manage compute resources other than containers. However, a container as the primary abstraction layer means that traditional VM management tools don't map directly. Though networking can help solve this issue, KubeVirt could be the answer. KubeVirt uses Kubernetes network architecture and plugins rather than hypervisor abstractions, such as vSwitches, to manage networking. As a result, products must switch to network management based on Kubernetes namespaces. That's not necessarily a bad thing; it's just an overall change in operations mode from a VM-centric operating model to a container-centric operating model.
Researchers Release Open Source Counterfactual Machine Learning Library
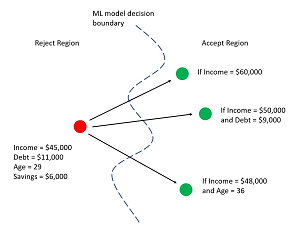
Exactly what machine learning counterfactuals are, and the reasons why they are important, are best explained by example. Suppose a loan company has a trained ML model that is used to approve or decline customers' loan applications. The predictor variables (often called features in ML terminology) are things like annual income, debt, sex, savings, and so on. A customer submits a loan application. Their income is $45,000 with debt = $11,000 and their age is 29 and their savings is $6,000. The application is declined. A counterfactual is change to one or more predictor values that results in the opposite result. For example, one possible counterfactual could be stated in words as, "If your income was increased to $60,000 then your application would have been approved." In general, there will be many possible counterfactuals for a given ML model and set of inputs. Two other counterfactuals might be, "If your income was increased by $50,000 and debt was decreased to $9,000 then your application would have been approved" and, "If your income was increased to $48,000 and your age was changed to 36 then your application would have been approved." Figure 1 illustrates three such counterfactuals for a loan scenario.
What is value stream mapping? A lean technique for improving business processes

Before you can start building a value stream map, you need to objectively evaluate your organization’s business processes, products and systems. Start by talking to leadership, department heads and other key stakeholders who can give you more insight into what can be improved. You’ll need to get hands-on experience with the process, product or system yourself and have other employees walk you through their part. It’s important to collect as much data as possible — for example, any inefficiencies in the process, how many workers are involved, what resources are used and any downtime. Any potentially relevant or noteworthy data is helpful in fleshing out your final VSM flow chart and achieving insights into what can be refined or improved. You’ll then create two separate VSM flow charts — a current state value stream map and a future state value stream map. Your current state VSM will be used to establish how the process currently runs and functions in the business. This is where you will demonstrate issues, significant findings and establish key requirements. The future state VSM, on the other hand, focuses on what your process will look like once your organization has completed all of the necessary improvements.
Ethernet consortium announces completion of 800GbE spec

Based on many of the technologies used in the current top-end 400 Gigabit Ethernet protocol, the new spec is formally known as 800GBASE-R. The consortium that designed it (then known as the 25 Gigabit Ethernet Consortium) was also instrumental in developing the 25, 50, and 100 Gigabit Ethernet protocols and includes Broadcom, Cisco, Google, and Microsoft among its members. The 800GbE spec adds new media access control (MAC) and physical coding sublayer (PCS) methods, which tweaks these functions to distribute data across eight physical lanes running at a native 106.25Gbps. (A lane can be a copper twisted pair or in optical cables, a strand of fiber or a wavelength.) The 800GBASE-R specification is built on two 400 GbE 2xClause PCSs to create a single MAC which operates at a combined 800Gbps. And while the focus is on eight 106.25G lanes, it's not locked in. It is possible to run 16 lanes at half the speed, or 53.125Gbps. The new standard offers half the latency of 400G Ethernet specification, but the new spec also cuts the forward error correction (FEC) overhead on networks running at 50 Gbps, 100 Gbps, and 200 Gbps by half, thus reducing the packet-processing load on the NIC.
Application performance for remote workers becomes primary network issue for businesses

In addition to the top-line finding of dealing with complexity and performance, the study also highlighted that cost had become less of an issue for respondents, who also cited significant investment in automation, security, cloud connectivity and the potential of 5G. Drilling deeper into the pressing issues for firms, Aryaka found that as the number of remote workers increases across the globe, productivity and remote application performance have become more important for organisations across Europe, the Middle East and Africa (EMEA). Some 45% of UK businesses noted that slow application performance led to a poor user experience for remote and mobile users, and that it was a significant issue faced by IT and support teams. Accessing and integrating cloud and software-as-a-service (SaaS) applications was one of the most pressing issues for UK IT departments, cited by 39%.
Ransomware is now the biggest online menace you need to worry about - here's why

One of the reasons why ransomware attacks have risen so much is because cyber criminals are increasingly viewing it as the simplest and quickest means of making money from compromised networks. With ransomware, attackers can lockdown an organisation's entire network and demand a bitcoin payment in exchange for the decryption key. Ransomware attacks are often successful because organisations opt to pay the ransom demand, viewing it as the quickest and easiest way to restore functionality to the network, despite authorities warning never to give into the demand of extortionists. These ransomware demands commonly reach six-figure sums and, because the transfer is made in bitcoin, it's relatively simple for the criminals to launder it without it being traced back to them. "The 'beauty' of the ransomware model is you only need to write the ransomware once and its potential to infect is only limited by its reach, which with the internet is unlimited," Ed Williams, EMEA director of SpiderLabs, the research division at Trustwave, told ZDNet.
Remote business continuity techniques to implement now

This is not just an issue when facing a pandemic. If your business continuity plan addresses only short-term disruptions, such as those that last less than a month, it may not be prepared for an extended outage. Your technology disaster recovery plan may need to be activated, assuming outages occur due to insufficient IT staff available or technology disruptions that occur due to a shortage of vendor personnel. Fortunately, many data centers are designed to operate without human intervention or with remote access to system administration functions. Technology vendors frequently use managed IT resources such as cloud-based systems to support their service offerings. This reduces the likelihood of outages as long as the managed service providers are able to keep their systems operational. As many organizations use remotely hosted applications, users can keep using those systems, so long as their vendors are able to keep their operations working. The real challenge for organizations that have mostly locally hosted systems and databases is to remotely manage those assets.
New Enterprise Graph Framework for Data Scientists Leverages Machine Learning
The new Neo4j for Graph Data Science framework is designed to enable data scientists to operationalize better analytics and machine learning models that infer behavior based on connected data and network structures Frame described. The framework, she said in a statement announcing the product release, is intended to provide the most expeditious way to generate better predictions. "A common misconception in data science is that more data increases accuracy and reduces false positives," she explained. "In reality, many data science models overlook the most predictive elements within data -- the connections and structures that lie within. Neo4j for Graph Data Science was conceived for this purpose -- to improve the predictive accuracy of machine learning, or answer previously unanswerable analytics questions, using the relationships inherent within existing data."
Quote for the day:
"Leadership is the wise use of power. Power is the capacity to translate intention into reality and sustain it." -- Warren Bennis
No comments:
Post a Comment