The SingularityNET Foundation continues to provide and maintain tools, such as a command-line interface (CLI), to help AI developers create and publish services on the platform directly, irrespective of whether these services appear on the Marketplace. This is key to the decentralized methodology, vision and ethos which has guided SingularityNET since its founding. However, AI services that appear on the platform via routes other than the Publisher Portal will not be listed on the Marketplace UI and cannot make use of the Marketplace’s tools for easy deployment, monitoring, maintenance, fiat/crypto conversion and so forth. The AI Publisher Portal enables developers to register themselves and submit their services for curation, seamlessly validates developer identities, and provides a guided and intuitive way to create and manage services on the Marketplace. Only services curated and published via the Publisher portal, and in this way approved by the Foundation, will appear on the Marketplace.
COVID-19 Has United Cybersecurity Experts, But Will That Unity Survive the Pandemic?

“A nurse or doctor can’t do what we do, and we can’t do what they do,” Espinosa said. “We’ve seen a massive rise in threats and attacks against healthcare systems, but it’s worse if someone dies due to a malicious cyberattack when we have the ability to prevent that. A lot of people are involved because they’re emotionally attached to the idea of helping this critical infrastructure stay safe and online.” Using threat intelligence feeds donated by dozens of cybersecurity companies, the CTC is poring over more than 100 million pieces of data about potential threats each day, running those indicators through security products from roughly 70 different vendors. If at least 10 of those flag a specific data point — such as a domain name — as malicious or bad, it gets added to the CTC’s blocklist, which is designed to be used by organizations worldwide for blocking malicious traffic. “For possible threats, meaning between five and nine vendors detect an indicator as bad, our volunteers manually verify that the indicator is malicious before including it in our blocklist,” Espinosa said. ... Mark Rogers, one of several people helping to manage the CTI League’s efforts, told Reuters the top priority of the group is working to combat hacks against medical facilities and other frontline responders to the pandemic, as well as helping defend communication networks and services that have become essential as more people work from home.
Machine Learning Playing An Important Role In Data Management

With advances in machine learning, cloud computing and storage, enterprises are finally breaking the data-management logjam. In question are breakout upgrades in business proficiency, revenue realization, product innovation and competitive differentiation. The outcomes driven here could be transformational. For CIOs and CISOs stressed over security, compliance and scheduling SLAs, it’s basic to understand that ever-expanding volumes and varieties of data, it’s not humanly workable for an administrator or even a team of administrators and data scientists to tackle these challenges. Luckily, machine learning can help. A variety of machine learning and deep learning strategies might be utilized to achieve this. Comprehensively, machine/deep learning methods might be named either unsupervised learning, supervised learning, or reinforcement learning The decision of which strategy will be driven by what issue is being fathomed. For instance, supervised learning mechanisms, for example, random forest might be utilized to build up a gauge, or what comprises “typical” behavior for a system, by observing applicable traits, at that point utilize the benchmark to identify inconsistencies that stray from the standard.
How can businesses ensure ROI from 5G services?

The unprecedented speed and capacity of 5G will dramatically increase the productivity of a typical business, paying dividends in terms of increased efficiency and therefore tangible ROI. In the short-term, 5G will enable agile and fast fixed wireless connections that will enable organisations to “cut-the-cord” while extending the reach and reliability of their WAN. While businesses today operate networks as many individual domains (branch, mobile and IoT), an advanced orchestration and automation system can make the entire network operate as a single unified network fabric. Looking further ahead, the power of edge computing will provide the processing power that will move artificial intelligence-powered solutions from the niche to the mainstream. From a cost-benefit perspective, AI automates and simplifies data analysis of any type, which can clearly offload work from human staff and increase productivity. While AI solutions are currently housed mainly in data centres, 5G will enable rapidly accelerated data processing at the network edge, providing the real-time and ubiquitous connectivity that AI requires to function.
Data-Driven Decision Making – Optimizing the Product Delivery Organization

With the Indicators Framework defined, it was clear to us that its introduction to the organization of 16 development teams could only be effective if sufficient support could be provided to the teams. We introduced Hypotheses first. Six months later we introduced SRE. And six months after that we introduced Continuous Delivery Indicators to the organization. We chose a staged approach to introducing these changes in order to have the organization focus on one change at a time. In terms of preparation for the introduction, Hypotheses were the easiest; it took an extension of our Business Feature Template and a workshop with each team. To prepare for the SRE introduction, we implemented basic infrastructure for two fundamental SLIs - Availability and Latency. The infrastructure is able to generate SLI and Error Budget Dashboards for each service of each team. Most importantly, it is able to do alerting on Error Budget Consumption in all deployment environments.
Is a free VPN a good idea for your IoT devices?

While some of the free VPNs available are secure, a few others aren’t. Some free VPNs have been reported to sell out the user’s data to third-parties, thereby undermining your privacy. There are also a few cases where VPNs have been used to facilitate malware attacks by housing the malware elements. Some may also try to access apps that they should not, such as Maps. For these reasons, it is recommended to use free VPNs from tried and tested reliable providers. Various VPN providers throw in different features to their free version products. Generally, most include basic functionalities, i.e. privacy and encryption. The rest of the advanced features are reserved for the premium plans. Truth to tell, you can hardly find a free VPN that has all the features you need. You might be forced to forego some features. It goes without saying then that the best free VPN is one that brings you the most of the features you need. The Commonwealth Scientific and Industrial Research Organization conducted a study on over 280 Android VPN apps. The study revealed that 67% of the apps had trackers embedded in their codes.
The Way Forward: Digital Resiliency Wins

McKinsey & Company advised CIOs to keep their focus on stabilizing emergency measures by strengthening remote working capabilities, improve cybersecurity, adjust ways of working with agile teams and prepare for a breakdown of parts of the vendor ecosystem (supply chain). In the interim, CIOs need to address immediate IT cost pressures to reduce costs, and creatively redeploy the IT workforce, while also pivoting to new areas of focus in the future. According to McKinsey & Company, many organizations are successfully digitally engaging with customers, and cited a government in Western Europe who embarked on an “express digitization” of quarantine-compensation claims to deal with a more than 100-fold increase in volume. “Sometimes this effort is about taking loads from call centers, but more often it addresses real new business opportunities. To engage with consumers, for example, retailers in China increasingly gave products at-home themes in WeChat,” McKinsey & Company wrote.
Windows 10 turns five: Don't get too comfortable, the rules will change again

Despite the occasional twists and turns that Windows 10 has taken in the past five years, it has accomplished its two overarching goals. First, it erased the memory of Windows 8 and its confusing interface. For the overwhelming majority of Microsoft's customers who decided to skip Windows 8 and stick with Windows 7, the transition was reasonably smooth. Even the naming decision, to skip Windows 9 and go straight to 10 was, in hindsight, pretty smart. Second, it offered an upgrade path to customers who were still deploying Windows 7 in businesses. That alternative became extremely important when we zoomed past the official end-of-support date for Windows 7 in January 2020. In mid-2019, when I checked usage data from the U.S. Government's Data Analytics Program, the migration to Windows 10 appeared to be stalled. As of July 31, 2019, Windows 7 still accounted for 26% of all visits to U.S. government websites from Windows PCs. Nine months later, that number has been cut in half. For the six weeks ending April 15, that same metric shows the number of visits from Windows 7 PCs is down to 12.7% and continuing to slide.
What is TypeScript? Strongly typed JavaScript

TypeScript is a superset of JavaScript. While any correct JavaScript code is also correct TypeScript code, TypeScript also has language features that aren’t part of JavaScript. The most prominent feature unique to TypeScript—the one that gave TypeScript its name—is, as noted, strong typing: a TypeScript variable is associated with a type, like a string, number, or boolean, that tells the compiler what kind of data it can hold. In addition, TypeScript does support type inference, and includes a catch-all any type, which means that variables don’t have to have their types assigned explicitly by the programmer; more on that in a moment. TypeScript is also designed for object-oriented programming—JavaScript, not so much. Concepts like inheritance and access control that are not intuitive in JavaScript are simple to implement in TypeScript. In addition, TypeScript allows you to implement interfaces, a largely meaningless concept in the JavaScript world. That said, there’s no functionality you can code in TypeScript that you can’t also code in JavaScript. That’s because TypeScript isn’t compiled in a conventional sense—the way, for instance, C++ is compiled into a binary executable that can run on specified hardware.
Fostering Smart Cities based on an Enterprise Architecture Approach
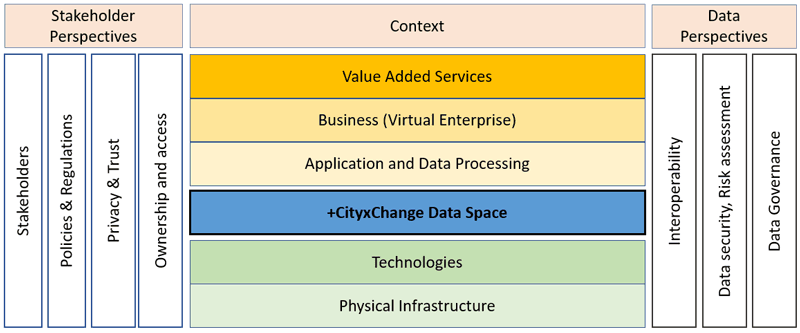
The research aims to develop an overall ICT architecture and service-based ecosystem to ensure that service providers of the +CityxChange project can develop, deploy and test their services through integrated and interconnected approaches. For the purpose of this research, a city can be seen as a big enterprise with different departments. With its ability to model the complexities of the real world in a practical way and to help users plan, design, document, and communicate IT and business-oriented issues, the Enterprise Architecture (EA) method has become a popular domain for business and IT system management. The decision support that it offers makes EA an ideal approach for sustainable smart cities, and it is being increasingly used in smart city projects. This approach allows functional components to be shared and reused and infrastructure and technologies to be standardised. EA can enhance the quality and performance of city processes and improve productivity across a city by integrating and unifying data linkages.
Quote for the day:
"Don't believe what your eyes are telling you. All they show is limitation. Look with your understanding." -- Richard B
No comments:
Post a Comment