This Hardware-Level Security Solution for SSDs Can Help Prevent Ransomware Attacks

Dubbed the SSD Insider++ technology, the new security solution can be integrated
into SSDs at the hardware level. So, the ransomware prevention feature will be
built right into the SSD drives and will automatically detect unusual encryption
activities that are not user-triggered. Now, getting into some technical
details, the SSD Insider++ technology uses the inherent writing and deletion
mechanisms in NAND flash to perform its task of preventing ransomware attacks.
It leverages the SSD controller to continuously monitor the activity of the
storage drive. The system triggers when any encryption workload is detected that
is not initiated by the authorized user. In that case, the firmware prevents the
SSD to take any write requests, which in turn suspends the encryption process.
The system then notifies the user about abnormal encryption activities via its
companion app. The app also allows users to recover any data that was encrypted
before the system stopped ongoing the process.
Graph Databases VS Relational Databases – Learn How a Graph Database Works
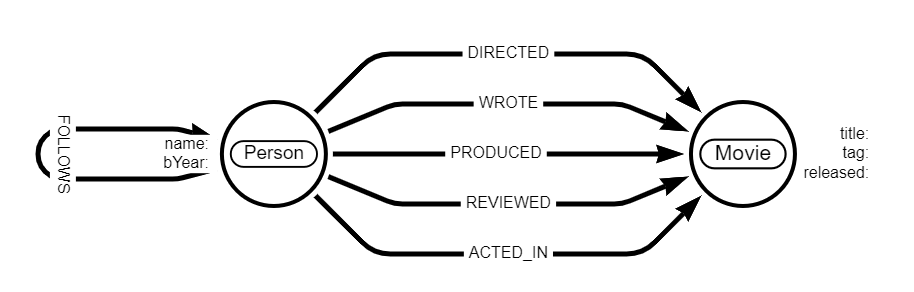
Graph databases are a type of “Not only SQL” (NoSQL) data store. They are
designed to store and retrieve data in a graph structure. The storage mechanism
used can vary from database to database. Some GDBs may use more traditional
database constructs, such as table-based, and then have a graph API layer on
top. Others will be ‘native’ GDBs – where the whole construct of the database
from storage, management and query maintains the graph structure of the data.
Many of the graph databases currently available do this by treating
relationships between entities as first class citizens. There are broadly two
types of GDB, Resource Descriptive Framework (RDF)/triple stores/semantic graph
databases, and property graph databases. An RDF GDB uses the concept of a
triple, which is a statement composed of three elements:
subject-predicate-object. Subject will be a resource or nodes in the graph,
object will be another node or literal value, and predicate represents the
relationship between subject and object.
Microsoft Warns of Cross-Account Takeover Bug in Azure Container Instances
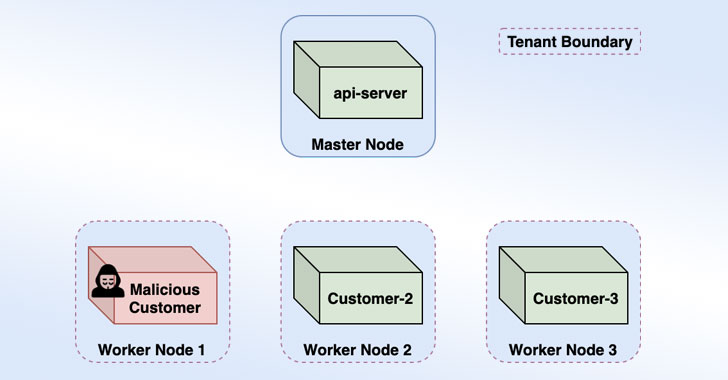
An attacker exploiting the weakness could execute malicious commands on other
users' containers, steal customer secrets and images deployed to the platform.
The Windows maker did not share any additional specifics related to the flaw,
save that affected customers "revoke any privileged credentials that were
deployed to the platform before August 31, 2021." Azure Container Instances is a
managed service that allows users to run Docker containers directly in a
serverless cloud environment, without requiring the use of virtual machines,
clusters, or orchestrators. ... "This discovery highlights the need for
cloud users to take a 'defense-in-depth' approach to securing their cloud
infrastructure that includes continuous monitoring for threats — inside and
outside the cloud platform," Unit 42 researchers Ariel Zelivanky and Yuval
Avrahami said. "Discovery of Azurescape also underscores the need for cloud
service providers to provide adequate access for outside researchers to study
their environments, searching for unknown threats."
Credit-Risk Models Based on Machine Learning: A ‘Middle-of-the-Road’ Solution
The low explainability of ML-driven models for credit risk remains, perhaps,
their greatest drawback. A visual inspection of, say, a random forest is
impossible, and although there are some tools (like feature importance) that
provide information about the inner workings of this type of model, ML model
logic is significantly more complicated than that of a traditional logistic
regression approach. However, we’re increasingly seeing “middle-of-the-road”
solutions that incorporate ML-engineered features within an easier-to-explain
logistic regression model. Under this approach, ML is used to select
highly-predictive features (for, say, probability of default), which are then
integrated with the so-called “logit” model. This hybrid model would include
both original and ML-engineered features, and an automated algorithm would
select the features for forecasting PD. Performance-driven features can be
added to this model through Sequential Forward Selection (SFS), one of the
most widely-used algorithms for feature selection.
DevOps Productivity: Have We Reached Its Limits?

As we have established, DevOps engineers are not babysitters. They are highly
qualified and talented engineers who thrive by building new and innovative
technologies. The grunt work of cloud management, therefore, is often seen as
an obstacle to DevOps productivity as it requires constant monitoring,
configuration and adjustments. It doesn’t help that much of this work is
impossible to do 100% effectively. Thankfully, there is a better way. AI
automation is perfectly suited to handle repetitive, routine tasks such as
analyzing real-time data, predicting future scale, adjusting infrastructure to
accommodate changes in requirements and more. Plus, it can do all of this with
perfect accuracy. DevOps teams cannot be as productive as they want if they
are constantly putting out fires in their cloud infrastructure. By automating
the tasks they don’t like doing anyway, your cloud stays fully optimized while
your DevOps engineers are able to work more efficiently on what they enjoy
most.
The three ingredients a software solution for digital payment needs

Above all, payment security is the main priority for consumers when it comes to
payments. Digital payment solutions need to be transparent and compliant with
regulations. As the cryptocurrency industry is growing, governments are taking
note and implement stricter regulations. Those regulations in turn demand higher
degrees of compliance and possibly license requirements. SMEs will want to avoid
the inherent volatility risk of cryptocurrencies. With the right technology,
this is also possible: the purchase amount paid is credited to the merchant in
fiat currency as usual, even if the customer pays using cryptocurrency — unless,
of course, the merchant prefers to keep the purchase amount as cryptocurrency.
In some countries, such as Germany, regulators have introduced specific
legislation to oversee cryptocurrency custodians. As such, to date, the lack of
regulated and supervised custody solutions has been a barrier to entry for SMEs
accepting digital asset payments. Confusion on who to choose as the right
partner has been common and a huge concern for regulatory-compliant
institutions.
Cybersecurity spending is a battle: Here's how to win

It can be difficult to get the board's full attention, especially if
cybersecurity is seen purely as an outgoing with little benefit to the bottom
line. The best way to address this is to explain, in plain language, the
potential threats out there. It could even be a good idea for a CISO to run an
exercise to demonstrate the potential impact of a cyber incident. This shouldn't
be over-dramatised, but presenting the board with an exercise based around a
real-life ransomware incident, for example, and explaining how a similar attack
could affect the company could open a few eyes, showing what measures need to be
taken. This could then lead to extra budget being released. "One of the best
ways to get their attention is to conduct a very thoughtful ransomware exercise.
Pick something very realistic and allow your executive team to walk through the
decision-making process," says Theresa Payton, CEO of Fortalice Solutions and
former chief information officer (CIO) at The White House.
Wanted: Meaningful Business Insights

Companies able to pivot attention to the quality of insights, not just the
quantity of data collected, are starting to reap the rewards of data-driven
business. A prominent oil and gas company that spent more than five years trying
to wrangle traditional analytics solutions to get insights on common metrics
like on-time and full deliveries or days payable outstanding (DPO) was able to
move beyond forensic insights to predictive analysis. Specifically, it was able
to achieve a greater than 40% reduction in inventory on-hand carrying costs by
linking inventory use data with actual planning parameters using the tools of a
context-rich data model. Similarly, a major manufacturer was able to improve its
on-time delivery metrics from the low 80th percentile to the mid-90th percentile
by connecting the dots between production capabilities and shipment results, and
making the necessary adjustments based on the insights. In the retail space,
companies could categorize the effective window for seasonal or perishable
goods—each with limited shelf life—to dramatically reduce obsolete inventory.
What Can the UK Learn From the US Infrastructure Bill Crypto Debacle?

We’re also seeing overreach and wildly sporadic regulatory moves from
non-governing bodies, (e.g. the SEC’s random targeting of Coinbase’s P2P lending
product), who are scrambling to make sense of this technology while concurrently
falling behind even some of the smallest nation-states on earth. Even more,
interestingly, the provision was challenged by a coalition from both the left
and right of the House. Crypto is not a political movement as Jackson Palmer,
one of the creators of Dogecoin, had recently accused it of being. It is a
societal movement. It comes as no surprise that Cynthia Lummis, Wyoming’s
Senator, was the driving force behind killing the bill. Wyoming has been
incredibly supportive of crypto for years now. It was the first state to have a
crypto bank and the first to legally recognise a Decentralised Autonomous
Organisation, a business that uses blockchain to govern itself without the
intervention of a central authority.So too was Ted Cruz, the Republican Senator
for Texas.
HAProxy urges users to update after HTTP request smuggling vulnerability found
"This vulnerability has the potential to have a wide-spread impact, but
fortunately, there are plenty of ways to mitigate the risk posed by this HAProxy
vulnerability, and many users most likely have already taken the necessary steps
to protect themselves," Bar-Dayan told ZDNet. "CVE-2021-40346 is mitigated if
HAProxy has been updated to one of the latest four versions of the software.
Like with most vulnerabilities, CVE-2021-40346 can't be exploited without severe
user negligence. The HAProxy team has been responsible in their handling of the
bug. Most likely, the institutional cloud and application services that use
HAProxy in their stack have either applied upgrades or made the requisite
configuration changes by now. Now it is up to all HAProxy users to run an
effective vulnerability remediation program to protect their businesses from
this very real threat." Michael Isbitski, the technical evangelist at Salt
Security, added that HAProxy is a multi-purpose, software-based infrastructure
component that can fulfill a number of networking functions, including load
balancer, delivery controller, SSL/TLS termination, web server, proxy server and
API mediator.
Quote for the day:
"Leadership is practices not so much
in words as in attitude and in actions." -- Harold Geneen
No comments:
Post a Comment