Zero Trust Requires Cloud Data Security with Integrated Continuous Endpoint Risk Assessment
Most of us are tired of talking about the impact of the pandemic, but it was a
watershed event in remote working. Most organizations had to rapidly extend
their existing enterprise apps to all their employees, remotely. And since many
have already embraced the cloud and had a remote access strategy in place,
typically a VPN, they simply extended what they had to all users. CEO's and
COO's wanted this to happen quickly and securely, and Zero Trust was the
buzzword that most understood as the right way to make this happen. So vendors
all started to explain how their widget enabled Zero Trust or at least a part of
it. But remember, the idea of Zero Trust was conceived way back in 2014. A lot
has changed over the last seven years. Apps and data that have moved to the
cloud do not adhere to corporate domain-oriented or file-based access controls.
Data is structured differently or unstructured. Communication and collaboration
tools have evolved. And the endpoints people use are no longer limited to
corporate-issued and managed domain-joined Windows laptops.
What We Can Learn from the Top Cloud Security Breaches

Although spending on cybersecurity grew 10% during 2020, this increase fell far
short of accelerated investments in business continuity, workforce productivity
and collaboration platforms. Meanwhile, spending on cloud infrastructure
services was 33% higher than the previous year, spending on cloud software
services was 20% higher, and there was a 17% growth in notebook PC shipments. In
short, cybersecurity spending in 2020 did not keep up with the pace of digital
transformation, creating even greater gaps in organizations’ ability to
effectively address the security challenges introduced by public cloud
infrastructure and modern containerized applications: complex environments,
fragmented stacks and borderless infrastructure, not to mention the
unprecedented speed, agility and scale. See our white paper, Introduction to
Cloud Security Blueprint, for a detailed discussion of cloud security
challenges, with or without a pandemic. In this blog post, we look at nine of
the biggest cloud breaches of 2020, where “big” is not necessarily the number of
data records actually compromised but rather the scope of the exposure and
potential vulnerability.
When is AI actually AI? Exploring the true definition of artificial intelligence

Whatever the organisation, consumers insist on seeing instant results – with
personalisation being ever more important. If this isn’t happening, businesses
will start seeing ‘drop off’ as customers seek an alternative, which, in today’s
competitive market, could prove disastrous. There is an opportunity now for
businesses to combat this by implementing true, bespoke AI models that can sift
through vast amounts of data and make its own intelligent decisions. After all,
the amount of data being generated across the globe is skyrocketing, and
organisations are continuing to share their data with one another – so
organisation and analysis at this level is a must. However, it’s important to
note that AI isn’t for everyone. The move to AI is a huge leap, so businesses
must consider whether they actually need AI to achieve their goals. In some
cases, investing in advanced analytics and insights is sufficient to help a
business run, grow and create value. So, if advanced analytics does the job, why
invest in AI? Most AI projects fail because there is no real adoption after the
initial proof of concept.
How DevOps teams are using—and abusing—DORA metrics
DORA stands for DevOps Research and Assessment, an information technology and
services firm founded founded by Gene Kim and Nicole Forsgren. In Accelerate,
Nicole, Gene and Jez Humble collected and summarized the outcomes many of us
have seen when moving to a continuous flow of value delivery. They also
discussed the behaviors and culture that successful organizations use and
provide guidance on what to measure and why. ... Related to this is the idea
of using DORA metrics to compare delivery performance between teams. Every
team has its own context. The product is different with different delivery
environments and different problem spaces. You can track team improvement and,
if you have a generative culture, show teams how they are improving compared
to one another, but stack-ranking teams will have a negative effect on
customer and business value. Where the intent of the metrics is to manage
performance rather than track the health of the entire system of delivery, the
metrics push us down the path toward becoming feature factories.
Intel AI Team Proposes A Novel Machine Learning (ML) Technique, MERL

What is unique about their design is that it allows all learners to contribute
to and draw from a single buffer at the same time. Each learner had access to
everyone else’s experiences, which aided its own exploration and made it
significantly more efficient at its own task. The second group of agents,
dubbed actors, was tasked with combining all of the little movements in order
to achieve the broader goal of prolonged walking. Since these agents were
rarely close enough to register a reward, the team used a genetic algorithm, a
technique that simulates biological evolution through natural selection.
Genetic algorithms start with possible solutions to a problem and utilize a
fitness function to develop the best answer over time. They created a set of
actors for each “generation,” each with a unique method for completing the
walking job. They then graded them according to their performance, keeping the
best and discarding the others. The following generation of actors was the
survivors’ “offspring,” inheriting their policies.
Backend For Frontend Authentication Pattern with Auth0 and ASP.NET Core
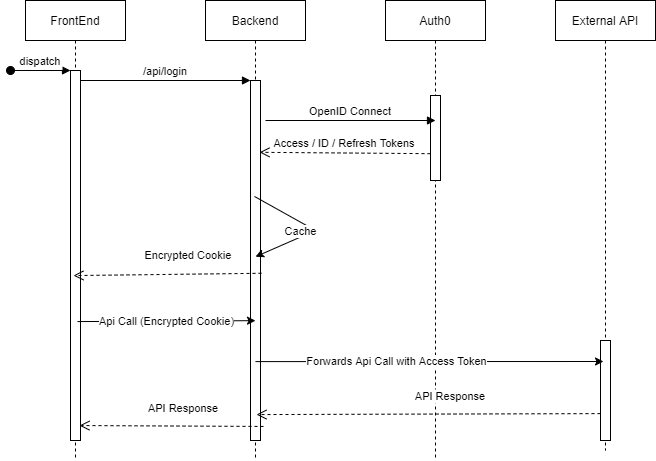
The Backend For Frontend (a.k.a BFF) pattern for authentication emerged to
mitigate any risk that may occur from negotiating and handling access tokens
from public clients running in a browser. The name also implies that a
dedicated backend must be available for performing all the authorization code
exchange and handling of the access and refresh tokens. This pattern relies on
OpenID Connect, which is an authentication layer that runs on top of OAuth to
request and receive identity information about authenticated users. ... Visual
Studio ships with three templates for SPAs with an ASP.NET Core backend. As
shown in the following picture, those templates are ASP.NET Core with Angular,
ASP.NET Core with React.js, and ASP.NET Core with React.js and Redux, which
includes all the necessary plumbing for using Redux. ... The authentication
middleware parses the JWT access token and converts each attribute in the
token as a claim attached to the current user in context. Our policy handler
uses the claim associated with the scope for checking that the expected scope
is there
REvil/Sodinokibi Ransomware Universal Decryptor Key Is Out

While Bitdefender isn’t able to share details about the key, given the fact
that the firm mentioned a “trusted law enforcement partner,” Boguslavskiy
conjectured that Bitdefender likely “conducted an advanced operation on
REvil’s core servers and infrastructures with or for European law enforcement
and was somehow able to reconstruct or obtain the master key.” Using the key
in a decryptor will unlock any victim, he said, “unless REvil redesigned their
entire malware set.” But even if the reborn REvil did redesign the original
malware set, the key will still be able to unlock victims that were attacked
prior to July 13, Boguslavskiy said. Advanced Intel monitors the top actors
across all underground discussions, including on XSS, a Russian-language
forum created to share knowledge about exploits, vulnerabilities, malware and
network penetration. So far, the intelligence firm hasn’t spotted any
substantive discussion about the universal key on these underground forums.
Boguslavskiy did note, however, that the administrator of XSS has been trying
to shut down discussion threads, since they “don’t see any use in the
gossip.”
What to expect from SASE certifications

Secure access service edge (SASE) is a network architecture that rolls SD-WAN
and security into a single, centrally managed cloud service that promises
simplified WAN deployment, improved security, and better performance.
According to Gartner, SASE’s benefits are transformational because it can
speed deployment time for new users, locations, applications and devices as
well as reduce attack surfaces and shorten remediation times by as much as
95%. ... The level one certification has twelve sections, and it takes about a
day to complete. Level two has five stages, takes about half a day, and
requires that applicants first complete level one. The training and testing
are delivered on the Credly platform. “It integrates with LinkedIn, so it’s
automatically shared on your LinkedIn profile,” Webber-Zvik says. As of Sept.
1, more than 1,000 people have earned level one certification, and they
represent multiple levels of professional experience and job categories. Half
are current Cato customers, and some of the rest may be considering going with
Cato, says Dave Greenfield, Cato’s director of technology evangelism.
The difference between physical and behavioural biometrics, and which you should be using

The debate around digital identity has never been more important. The COVID-19
pandemic pushed us almost entirely online, with many businesses pivoting to
become e-tailers almost overnight. Our reliance on online services – whether
ordering a new bank card, getting your groceries delivered, or talking to
friends – has given bad actors the perfect hunting ground. With the advent of
the internet, the world moved online. However, authentication processes from
the physical world were digitised rather than re-designed for the digital
world. The processes businesses digitised lack security, are cumbersome and
don’t preserve privacy. For example, the password: it is now 60 years old, yet
still relied on today to protect our identities and data. Digitised processes
have enabled the rise in online fraud, scams, social engineering, and
synthetic identities. Our own research highlighted how a quarter of consumers
globally receive more scam text messages than they get from friends and
families, with over half (54%) of UK consumers stating that they trust
organisations less after receiving a scam message.
Resetting a Struggling Scrum Team Using Sprint 0
It is hard to determine in Sprint 0 if you are done. There is a balance to
strike between performing enough upfront planning and agreement to provide
clarity and comfort, and taking significant time away from delivery to plan
for every eventuality that could appear in the sprints that follow Sprint 0.
After running these sessions, we entered our first delivery sprint in the
hopes that the agreed ways of working would help us eliminate any challenges
we found together. However, we encountered a few rocks that we had to navigate
around on our path to quieter seas. One early issue that surfaced was that of
the level of bonding within the team. Despite the new team members settling in
well, and communication channels being agreed upon to help Robin and the
others collaborate, it became clear that the developer group needed to build
trust to work effectively. Silence was a big part of many planning and
refinement ceremonies. This was not a team of strong extroverts, and I had
concerns that the team was not comfortable speaking up.
Quote for the day:
"Leadership is the art of influencing
people to execute your strategic thinking" --
Nabil Khalil Basma
No comments:
Post a Comment