Tech jobs are changing. But don't expect a boom in IT salaries just yet
 While companies may not be planning large wage incentives for staff, Robert Half
found that many were readdressing the benefits packages they offer, with the
inclusion of perks such as flexible hours, remote-working options and allowances
for home office equipment. Clamp suggests that this focus on the employee
experience, rather than substantial pay increases, is what's likely to shape
compensation packages in the months ahead. "We think it's part of the employee
proposition, and part of the experience that is now pretty common among larger
employers, and perhaps smaller ones too -- giving people fulfilment of their
work," he says. Meerah Rajavel, CIO at Citrix, agrees. "When it comes to
attracting and retaining talent, companies need to look beyond pay," Rajavel
tells ZDNet. "Benefits programs should focus on total rewards that support
employees in a holistic way, providing not only for their financial security,
but their physical, intellectual, social, and environmental well-being." Rajavel
points out that pay has always been at a premium in the tech space, but adds
that the speed at which the market is currently moving is putting pressure on
companies to up the ante.
While companies may not be planning large wage incentives for staff, Robert Half
found that many were readdressing the benefits packages they offer, with the
inclusion of perks such as flexible hours, remote-working options and allowances
for home office equipment. Clamp suggests that this focus on the employee
experience, rather than substantial pay increases, is what's likely to shape
compensation packages in the months ahead. "We think it's part of the employee
proposition, and part of the experience that is now pretty common among larger
employers, and perhaps smaller ones too -- giving people fulfilment of their
work," he says. Meerah Rajavel, CIO at Citrix, agrees. "When it comes to
attracting and retaining talent, companies need to look beyond pay," Rajavel
tells ZDNet. "Benefits programs should focus on total rewards that support
employees in a holistic way, providing not only for their financial security,
but their physical, intellectual, social, and environmental well-being." Rajavel
points out that pay has always been at a premium in the tech space, but adds
that the speed at which the market is currently moving is putting pressure on
companies to up the ante.Becoming a Cybersecurity or Privacy Lawyer: Tips for Young Attorneys
A keen interest in technology is helpful, however, as lawyers in this space
need to stay abreast of rapid developments in both the law and the underlying
space. And taking some classes in IT can be useful to develop a functional
tech vocabulary, as you may often find yourself tasked with translating
between IT professionals and business leaders within your client’s
organizations. If you are already a practicing lawyer, seek out relevant CLE
content from the Pennsylvania Bar Association, Practicing Law Institute,
Privacy + Security Forum, or other provider; these providers offer annual
seminars that provide valuable crossover between tech and legal content. ...
“The cyber field is always evolving, from risk vectors, to newly enacted laws
(or courts’ interpretation of them), to techniques employed by threat actors.
Privacy also is in a state of continual change and updates. Collaboration and
dialogue with your peers is an important component of the practice, and the
Committee offers an opportunity for young lawyers to do just that,” says
Joshua Mooney
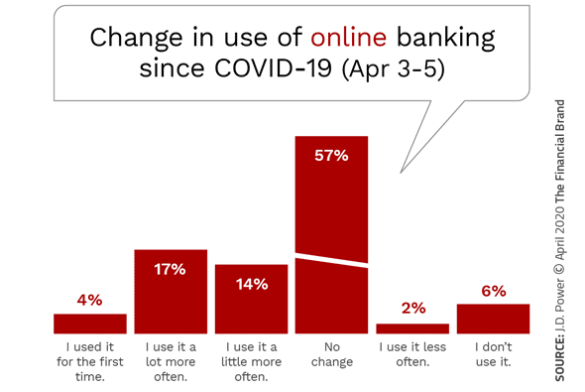 One challenge that smaller financial institutions face is that they have older
customer bases, which impacts the penetration of digital banking solutions.
But there is more than just an age differential. Even taking age out of the
equation the largest banks outperform smaller institutions. For instance,
midsize banks were found to lag in several digital product usage metrics, such
as: Paying bills via online and mobile; Internal funds transfers via
mobile app; Using P2P payments in the mobile app; and Receiving
alerts via mobile app. Of greater concern is that consumers who do use either
online banking or mobile banking are less satisfied with both the design and
functionality of the websites and mobile tools. They also report lower
satisfaction with the range of services that can be performed with the mobile
apps. Beyond redesigning the online banking website or mobile banking app,
organizations should focus on the lowest-hanging fruit for increased
engagement. This would include linking P2P payments to one of the many
available services.
One challenge that smaller financial institutions face is that they have older
customer bases, which impacts the penetration of digital banking solutions.
But there is more than just an age differential. Even taking age out of the
equation the largest banks outperform smaller institutions. For instance,
midsize banks were found to lag in several digital product usage metrics, such
as: Paying bills via online and mobile; Internal funds transfers via
mobile app; Using P2P payments in the mobile app; and Receiving
alerts via mobile app. Of greater concern is that consumers who do use either
online banking or mobile banking are less satisfied with both the design and
functionality of the websites and mobile tools. They also report lower
satisfaction with the range of services that can be performed with the mobile
apps. Beyond redesigning the online banking website or mobile banking app,
organizations should focus on the lowest-hanging fruit for increased
engagement. This would include linking P2P payments to one of the many
available services.
 “E-waste is the world’s fastest growing waste stream,” said Fred White,
commercial manager at Argo Natural Resources. “Just looking at the market
size, it’s quite significant, and the rate of growth is enormous – it’s
projected to grow by 40% over the next 10 years. A lot of recycling capacity
needs to come online to deal with that growth. “We see it as a big
opportunity. Global demand for electronic goods is soaring – how many phones
and laptops do you have today, compared to 10-15 years ago? And how long do
you keep those phones?” Argo is commercialising Deep Eutectic Solvents (DES),
a chemistry that has been under research and development at the University of
Leicester for nearly 20 years. DES consists of non-toxic, environmentally
benign and chemically stable ionic liquids that can be used to extract a wide
range of metals. “DES is a platform chemistry of millions of different
combinations of salts and simple organic compounds,” White explained. “They
can be combined in certain ways to do a wide variety of things.”
“E-waste is the world’s fastest growing waste stream,” said Fred White,
commercial manager at Argo Natural Resources. “Just looking at the market
size, it’s quite significant, and the rate of growth is enormous – it’s
projected to grow by 40% over the next 10 years. A lot of recycling capacity
needs to come online to deal with that growth. “We see it as a big
opportunity. Global demand for electronic goods is soaring – how many phones
and laptops do you have today, compared to 10-15 years ago? And how long do
you keep those phones?” Argo is commercialising Deep Eutectic Solvents (DES),
a chemistry that has been under research and development at the University of
Leicester for nearly 20 years. DES consists of non-toxic, environmentally
benign and chemically stable ionic liquids that can be used to extract a wide
range of metals. “DES is a platform chemistry of millions of different
combinations of salts and simple organic compounds,” White explained. “They
can be combined in certain ways to do a wide variety of things.”
 IoT devices need internet connectivity to work. However, even the strongest
network is bound to experience overload at some point. No matter how
sophisticated technology gets, constantly being connected to a network is a
fundamental weakness, especially on an industrial scale. More companies these
days favor IoT devices that use intermittent connectivity protocols, as
opposed to constant wifi or cellular connections, as a way of overcoming this
challenge. The logistics industry provides a great case study for the
positives of intermittent connectivity. Traditionally, data logger devices
that connect using radio-frequency identification (RFID) transmitters or even
USB cables have been used to collect condition and location information on
stored and shipped materials. But plugging in all those loggers intermittently
is extremely labor intensive, and RFID syncs with unreliable towers that are
dependent on expensive proprietary systems. Finnish firm Logmore's dynamic
e-ink QR code solution is an example of how to use intermittent connectivity
at scale. IoT sensors attached to the tags collect information, which
refreshes a QR code on a small display.
IoT devices need internet connectivity to work. However, even the strongest
network is bound to experience overload at some point. No matter how
sophisticated technology gets, constantly being connected to a network is a
fundamental weakness, especially on an industrial scale. More companies these
days favor IoT devices that use intermittent connectivity protocols, as
opposed to constant wifi or cellular connections, as a way of overcoming this
challenge. The logistics industry provides a great case study for the
positives of intermittent connectivity. Traditionally, data logger devices
that connect using radio-frequency identification (RFID) transmitters or even
USB cables have been used to collect condition and location information on
stored and shipped materials. But plugging in all those loggers intermittently
is extremely labor intensive, and RFID syncs with unreliable towers that are
dependent on expensive proprietary systems. Finnish firm Logmore's dynamic
e-ink QR code solution is an example of how to use intermittent connectivity
at scale. IoT sensors attached to the tags collect information, which
refreshes a QR code on a small display.
 With millions still working from home, cybercriminals are targeting corporate
resources via home networks and in-home smart devices too, according to Red
Canary’s Grant Oviatt. They know organizations haven’t quite gotten used to
the new perimeter — or lack thereof. “Throughout the past 12 months, the lack
of [incident] preparedness has become increasingly evident, especially with
the influx of personal devices logging onto corporate networks, the resulting
reduced endpoint visibility, expanded attack surface and surge in attack
vectors,” he said in a recent Infosec Insider column for Threatpost. In
real-world attacks, the end result of attacks on IoT gear is evolving,
Kaspersky found: Infected devices being used to steal personal or corporate
data as mentioned, and mine cryptocurrencies, on top of traditional DDoS
attacks in which the devices are added to a botnet. For instance, the Lemon
Duck botnet targets victims’ computer resources to mine the Monero virtual
currency, and it has self-propagating capabilities and a modular framework
that allows it to infect additional systems to become part of the botnet
too.
With millions still working from home, cybercriminals are targeting corporate
resources via home networks and in-home smart devices too, according to Red
Canary’s Grant Oviatt. They know organizations haven’t quite gotten used to
the new perimeter — or lack thereof. “Throughout the past 12 months, the lack
of [incident] preparedness has become increasingly evident, especially with
the influx of personal devices logging onto corporate networks, the resulting
reduced endpoint visibility, expanded attack surface and surge in attack
vectors,” he said in a recent Infosec Insider column for Threatpost. In
real-world attacks, the end result of attacks on IoT gear is evolving,
Kaspersky found: Infected devices being used to steal personal or corporate
data as mentioned, and mine cryptocurrencies, on top of traditional DDoS
attacks in which the devices are added to a botnet. For instance, the Lemon
Duck botnet targets victims’ computer resources to mine the Monero virtual
currency, and it has self-propagating capabilities and a modular framework
that allows it to infect additional systems to become part of the botnet
too.
 Using data ethically and securely is critically important in a digital age,
where growing amounts are being created every day. Doing so is no longer just
an optional extra, but a human right all of its own. But too many businesses
still have a lax approach to data security, and it’s inadvertently aiding
cyber criminal efforts. The long list of fines handed out by the ICO is
testament to the fact there isn’t enough being done to protect citizens. While
reputational damage and fines can be big deterrents, data breaches are still a
regular occurrence. Data protection’s plight relies on businesses taking a
proactive stance on this, but once again, technology can step in here and play
an important enabling role. Irrespective of your business size, you need to
look for modern data protection solutions that factor in data security,
compliance and customer privacy requirements from the very start. Read
customer testimonials, conduct your own research and look to respected awards
bodies to help in that decision, rather than just relying on a vendor’s word
that their solutions are secure.
Using data ethically and securely is critically important in a digital age,
where growing amounts are being created every day. Doing so is no longer just
an optional extra, but a human right all of its own. But too many businesses
still have a lax approach to data security, and it’s inadvertently aiding
cyber criminal efforts. The long list of fines handed out by the ICO is
testament to the fact there isn’t enough being done to protect citizens. While
reputational damage and fines can be big deterrents, data breaches are still a
regular occurrence. Data protection’s plight relies on businesses taking a
proactive stance on this, but once again, technology can step in here and play
an important enabling role. Irrespective of your business size, you need to
look for modern data protection solutions that factor in data security,
compliance and customer privacy requirements from the very start. Read
customer testimonials, conduct your own research and look to respected awards
bodies to help in that decision, rather than just relying on a vendor’s word
that their solutions are secure.
 Most SD-WANs simply look at packet types or maybe TCP/UDP port numbers, which
assumes that all voice packets or all packets for a particular application
have the same priority. In many cases, users prioritize specific
worker-to-application relationships, not all users of a given application, so
prioritization may offer less value than you think. If you have specific
reasons for selecting an SD-WAN that has higher header overhead or one that
can’t prioritize as you’d like, you can reduce the impact of both these issues
by using access links with higher bandwidth if they’re available. If not, and
you need to use access bandwidth efficiently, then take the time to assess
your vendor options in light of the overhead and prioritization issues. That
also goes for security. If an SD-WAN can recognize specific
worker-to-application relationships, it can not only prioritize the important
ones, but also recognize which of all the possible worker-to-application
relationships are actually permitted. That means that the SD-WAN can actually
create better security.
Most SD-WANs simply look at packet types or maybe TCP/UDP port numbers, which
assumes that all voice packets or all packets for a particular application
have the same priority. In many cases, users prioritize specific
worker-to-application relationships, not all users of a given application, so
prioritization may offer less value than you think. If you have specific
reasons for selecting an SD-WAN that has higher header overhead or one that
can’t prioritize as you’d like, you can reduce the impact of both these issues
by using access links with higher bandwidth if they’re available. If not, and
you need to use access bandwidth efficiently, then take the time to assess
your vendor options in light of the overhead and prioritization issues. That
also goes for security. If an SD-WAN can recognize specific
worker-to-application relationships, it can not only prioritize the important
ones, but also recognize which of all the possible worker-to-application
relationships are actually permitted. That means that the SD-WAN can actually
create better security.
Quote for the day:
"The leadership team is the most important asset of the company and can be its worst liability" -- Med Jones
Big Banks Benefiting Most From COVID-19 Digital Shifts
 One challenge that smaller financial institutions face is that they have older
customer bases, which impacts the penetration of digital banking solutions.
But there is more than just an age differential. Even taking age out of the
equation the largest banks outperform smaller institutions. For instance,
midsize banks were found to lag in several digital product usage metrics, such
as: Paying bills via online and mobile; Internal funds transfers via
mobile app; Using P2P payments in the mobile app; and Receiving
alerts via mobile app. Of greater concern is that consumers who do use either
online banking or mobile banking are less satisfied with both the design and
functionality of the websites and mobile tools. They also report lower
satisfaction with the range of services that can be performed with the mobile
apps. Beyond redesigning the online banking website or mobile banking app,
organizations should focus on the lowest-hanging fruit for increased
engagement. This would include linking P2P payments to one of the many
available services.
One challenge that smaller financial institutions face is that they have older
customer bases, which impacts the penetration of digital banking solutions.
But there is more than just an age differential. Even taking age out of the
equation the largest banks outperform smaller institutions. For instance,
midsize banks were found to lag in several digital product usage metrics, such
as: Paying bills via online and mobile; Internal funds transfers via
mobile app; Using P2P payments in the mobile app; and Receiving
alerts via mobile app. Of greater concern is that consumers who do use either
online banking or mobile banking are less satisfied with both the design and
functionality of the websites and mobile tools. They also report lower
satisfaction with the range of services that can be performed with the mobile
apps. Beyond redesigning the online banking website or mobile banking app,
organizations should focus on the lowest-hanging fruit for increased
engagement. This would include linking P2P payments to one of the many
available services.Your hybrid cloud model is just a phase
Hybrid cloud, however, is not a long-term solution. It forms part of a pathway towards a reality in which the public and private sectors alike will use a fully integrated public cloud such as international providers like Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform or public sovereign cloud providers, which provides a broad set of infrastructure services, such as computing power, storage options, networking, and databases, delivered on-demand. The need for this is more important than ever before, with challenges including governance, data and security threats rapidly rising as key focus areas that organisational personnel and the public need to be educated about. This transitional phase should last between five to ten years. As this process takes place, there is likely to be resistance from those with lingering concerns – such as the governance issue I noted above. Alleviating these concerns will mean zeroing in on the things that will permit organisations and public sector entities to evolve in the way they want.Urban mining: the hidden value of e-waste
 “E-waste is the world’s fastest growing waste stream,” said Fred White,
commercial manager at Argo Natural Resources. “Just looking at the market
size, it’s quite significant, and the rate of growth is enormous – it’s
projected to grow by 40% over the next 10 years. A lot of recycling capacity
needs to come online to deal with that growth. “We see it as a big
opportunity. Global demand for electronic goods is soaring – how many phones
and laptops do you have today, compared to 10-15 years ago? And how long do
you keep those phones?” Argo is commercialising Deep Eutectic Solvents (DES),
a chemistry that has been under research and development at the University of
Leicester for nearly 20 years. DES consists of non-toxic, environmentally
benign and chemically stable ionic liquids that can be used to extract a wide
range of metals. “DES is a platform chemistry of millions of different
combinations of salts and simple organic compounds,” White explained. “They
can be combined in certain ways to do a wide variety of things.”
“E-waste is the world’s fastest growing waste stream,” said Fred White,
commercial manager at Argo Natural Resources. “Just looking at the market
size, it’s quite significant, and the rate of growth is enormous – it’s
projected to grow by 40% over the next 10 years. A lot of recycling capacity
needs to come online to deal with that growth. “We see it as a big
opportunity. Global demand for electronic goods is soaring – how many phones
and laptops do you have today, compared to 10-15 years ago? And how long do
you keep those phones?” Argo is commercialising Deep Eutectic Solvents (DES),
a chemistry that has been under research and development at the University of
Leicester for nearly 20 years. DES consists of non-toxic, environmentally
benign and chemically stable ionic liquids that can be used to extract a wide
range of metals. “DES is a platform chemistry of millions of different
combinations of salts and simple organic compounds,” White explained. “They
can be combined in certain ways to do a wide variety of things.”The IOT Technologies Making Industry 4.0 Real
 IoT devices need internet connectivity to work. However, even the strongest
network is bound to experience overload at some point. No matter how
sophisticated technology gets, constantly being connected to a network is a
fundamental weakness, especially on an industrial scale. More companies these
days favor IoT devices that use intermittent connectivity protocols, as
opposed to constant wifi or cellular connections, as a way of overcoming this
challenge. The logistics industry provides a great case study for the
positives of intermittent connectivity. Traditionally, data logger devices
that connect using radio-frequency identification (RFID) transmitters or even
USB cables have been used to collect condition and location information on
stored and shipped materials. But plugging in all those loggers intermittently
is extremely labor intensive, and RFID syncs with unreliable towers that are
dependent on expensive proprietary systems. Finnish firm Logmore's dynamic
e-ink QR code solution is an example of how to use intermittent connectivity
at scale. IoT sensors attached to the tags collect information, which
refreshes a QR code on a small display.
IoT devices need internet connectivity to work. However, even the strongest
network is bound to experience overload at some point. No matter how
sophisticated technology gets, constantly being connected to a network is a
fundamental weakness, especially on an industrial scale. More companies these
days favor IoT devices that use intermittent connectivity protocols, as
opposed to constant wifi or cellular connections, as a way of overcoming this
challenge. The logistics industry provides a great case study for the
positives of intermittent connectivity. Traditionally, data logger devices
that connect using radio-frequency identification (RFID) transmitters or even
USB cables have been used to collect condition and location information on
stored and shipped materials. But plugging in all those loggers intermittently
is extremely labor intensive, and RFID syncs with unreliable towers that are
dependent on expensive proprietary systems. Finnish firm Logmore's dynamic
e-ink QR code solution is an example of how to use intermittent connectivity
at scale. IoT sensors attached to the tags collect information, which
refreshes a QR code on a small display.IoT Attacks Skyrocket, Doubling in 6 Months
 With millions still working from home, cybercriminals are targeting corporate
resources via home networks and in-home smart devices too, according to Red
Canary’s Grant Oviatt. They know organizations haven’t quite gotten used to
the new perimeter — or lack thereof. “Throughout the past 12 months, the lack
of [incident] preparedness has become increasingly evident, especially with
the influx of personal devices logging onto corporate networks, the resulting
reduced endpoint visibility, expanded attack surface and surge in attack
vectors,” he said in a recent Infosec Insider column for Threatpost. In
real-world attacks, the end result of attacks on IoT gear is evolving,
Kaspersky found: Infected devices being used to steal personal or corporate
data as mentioned, and mine cryptocurrencies, on top of traditional DDoS
attacks in which the devices are added to a botnet. For instance, the Lemon
Duck botnet targets victims’ computer resources to mine the Monero virtual
currency, and it has self-propagating capabilities and a modular framework
that allows it to infect additional systems to become part of the botnet
too.
With millions still working from home, cybercriminals are targeting corporate
resources via home networks and in-home smart devices too, according to Red
Canary’s Grant Oviatt. They know organizations haven’t quite gotten used to
the new perimeter — or lack thereof. “Throughout the past 12 months, the lack
of [incident] preparedness has become increasingly evident, especially with
the influx of personal devices logging onto corporate networks, the resulting
reduced endpoint visibility, expanded attack surface and surge in attack
vectors,” he said in a recent Infosec Insider column for Threatpost. In
real-world attacks, the end result of attacks on IoT gear is evolving,
Kaspersky found: Infected devices being used to steal personal or corporate
data as mentioned, and mine cryptocurrencies, on top of traditional DDoS
attacks in which the devices are added to a botnet. For instance, the Lemon
Duck botnet targets victims’ computer resources to mine the Monero virtual
currency, and it has self-propagating capabilities and a modular framework
that allows it to infect additional systems to become part of the botnet
too.Adoption of Cloud Native Architecture, Part 3: Service Orchestration and Service Mesh
All applications and services include all the non-functional code inside them. There are plenty of disadvantages with this type of design. There is a lot of duplicate implementation and proliferation of the same functionality in each application and service, resulting in longer application development (time to market) and exponentially higher maintenance costs. With all these common functions embedded inside each app and service, all are tightly coupled with specific technologies and frameworks used for each of those functions, for example for Spring Cloud Gateway and Zipkin or Jaeger for routing and tracing respectively. Any upgrades to underlying technologies will require every application and service to be modified, rebuilt, and redeployed, causing downtime and outages for users. Because of these challenges, distributed systems are becoming complex. These applications need to be redesigned and refactored to avoid siloed development and the proliferation of one-off solutions.How tech is a vital weapon against cyber information warfare
 Using data ethically and securely is critically important in a digital age,
where growing amounts are being created every day. Doing so is no longer just
an optional extra, but a human right all of its own. But too many businesses
still have a lax approach to data security, and it’s inadvertently aiding
cyber criminal efforts. The long list of fines handed out by the ICO is
testament to the fact there isn’t enough being done to protect citizens. While
reputational damage and fines can be big deterrents, data breaches are still a
regular occurrence. Data protection’s plight relies on businesses taking a
proactive stance on this, but once again, technology can step in here and play
an important enabling role. Irrespective of your business size, you need to
look for modern data protection solutions that factor in data security,
compliance and customer privacy requirements from the very start. Read
customer testimonials, conduct your own research and look to respected awards
bodies to help in that decision, rather than just relying on a vendor’s word
that their solutions are secure.
Using data ethically and securely is critically important in a digital age,
where growing amounts are being created every day. Doing so is no longer just
an optional extra, but a human right all of its own. But too many businesses
still have a lax approach to data security, and it’s inadvertently aiding
cyber criminal efforts. The long list of fines handed out by the ICO is
testament to the fact there isn’t enough being done to protect citizens. While
reputational damage and fines can be big deterrents, data breaches are still a
regular occurrence. Data protection’s plight relies on businesses taking a
proactive stance on this, but once again, technology can step in here and play
an important enabling role. Irrespective of your business size, you need to
look for modern data protection solutions that factor in data security,
compliance and customer privacy requirements from the very start. Read
customer testimonials, conduct your own research and look to respected awards
bodies to help in that decision, rather than just relying on a vendor’s word
that their solutions are secure.Tailoring SD-WAN to fit your needs
 Most SD-WANs simply look at packet types or maybe TCP/UDP port numbers, which
assumes that all voice packets or all packets for a particular application
have the same priority. In many cases, users prioritize specific
worker-to-application relationships, not all users of a given application, so
prioritization may offer less value than you think. If you have specific
reasons for selecting an SD-WAN that has higher header overhead or one that
can’t prioritize as you’d like, you can reduce the impact of both these issues
by using access links with higher bandwidth if they’re available. If not, and
you need to use access bandwidth efficiently, then take the time to assess
your vendor options in light of the overhead and prioritization issues. That
also goes for security. If an SD-WAN can recognize specific
worker-to-application relationships, it can not only prioritize the important
ones, but also recognize which of all the possible worker-to-application
relationships are actually permitted. That means that the SD-WAN can actually
create better security.
Most SD-WANs simply look at packet types or maybe TCP/UDP port numbers, which
assumes that all voice packets or all packets for a particular application
have the same priority. In many cases, users prioritize specific
worker-to-application relationships, not all users of a given application, so
prioritization may offer less value than you think. If you have specific
reasons for selecting an SD-WAN that has higher header overhead or one that
can’t prioritize as you’d like, you can reduce the impact of both these issues
by using access links with higher bandwidth if they’re available. If not, and
you need to use access bandwidth efficiently, then take the time to assess
your vendor options in light of the overhead and prioritization issues. That
also goes for security. If an SD-WAN can recognize specific
worker-to-application relationships, it can not only prioritize the important
ones, but also recognize which of all the possible worker-to-application
relationships are actually permitted. That means that the SD-WAN can actually
create better security.Quote for the day:
"The leadership team is the most important asset of the company and can be its worst liability" -- Med Jones
No comments:
Post a Comment