Digital State IDs Start Rollouts Despite Privacy Concerns

To assuage security fears that come with storing people’s identity on its
devices, Apple is asserting that state DLs and IDs stored in Wallet on iPhone
and Apple Watch will “take full advantage of the privacy and security” built
into the devices, the company said. Apple’s mobile ID implementation supports
the ISO 18013-5 mDL, or mobile driver’s license standard being used by the
government for storing digital identities. Apple played an active role in
developing the standard, which the company said sets clear guidelines for the
industry about how to protect consumers’ privacy when presenting an ID or
driver’s license through a mobile device, the company said. Moreover, Apple
devices will encrypt ID data to protect it against potential theft by threat
actors, with DLs and IDs stored in Wallet presented digitally through encrypted
communication directly between the device and the identity reader, the company
said. This precludes the need for users to unlock, show or hand over their
device to someone. Additionally, the use of Face ID and Touch ID will ensure
that only the person who added the ID to the device can present it or view it on
the device, according to Apple.
6 cybersecurity training best practices for SMBs

SMB owners and staff may know what cybersecurity risks are making the
rounds—phishing, for example—but do they understand why these risks matter to
the organization and themselves? Do they know what's required to reduce the
risk? "It's important to note that raising security awareness is the goal,"
Poriete said. "Security communication, culture and training are different types
of methods that can be used to help SMEs get there." Each company has to decide
whether to develop the training in-house or find a consultant specializing in
cybersecurity to recommend or create a training program specific to the
company's needs. ... Learning about cybersecurity can be complex, and
instructors provide too much information more often than not. The person
responsible for training must avoid overloading employees with information
they're unlikely to remember. "Training shouldn't be a one-off exercise but a
regular activity to help maintain employees' level of awareness," Poriete said.
"Think short, sharp exercises so as not to interrupt their core work or create
security fatigue."
How Uber is Leveraging Apache Kafka For More Than 300 Micro Services
Uber has overcome the pub-sub message queueing system issues by implementing
features via a client-side SDK. In addition, the team chose a proxy-based
approach. The engineering team has taken a multiple programming approach with
Go, Java, Python, and NodeJS services. While traditionally different services
would be written in other languages for the various client libraries, Consumer
Proxy makes it possible to implement only one programming language applicable to
all services. This approach also makes it easier for the team to manage the 1000
microservices that Uber runs. Since the message pushing protocols remain
unchanged, the Kafka team can upgrade the proxy at any time without affecting
other services. Consumer Proxy also assists in limiting the blasting radius of
rebalancing storms as a result of the rolling restart. It rebalances the
consumer group by decoupling message consuming nodes from the message processing
services. The service can eliminate the effects of rebalancing storms itself by
implementing its group rebalance logic.
Deleting unethical data sets isn’t good enough

Scraping the web for images and text was once considered an inventive strategy
for collecting real-world data. Now laws like GDPR (Europe’s data protection
regulation) and rising public concern about data privacy and surveillance have
made the practice legally risky and unseemly. As a result, AI researchers have
increasingly retracted the data sets they created this way. But a new study
shows that this has done little to keep the problematic data from proliferating
and being used. The authors selected three of the most commonly cited data sets
containing faces or people, two of which had been retracted; they traced the
ways each had been copied, used, and repurposed in close to 1,000 papers. In the
case of MS-Celeb-1M, copies still exist on third-party sites and in derivative
data sets built atop the original. Open-source models pre-trained on the data
remain readily available as well. The data set and its derivatives were also
cited in hundreds of papers published between six and 18 months after
retraction. DukeMTMC, a data set containing images of people walking on Duke
University’s campus and retracted in the same month as MS-Celeb-1M, similarly
persists in derivative data sets and hundreds of paper citations.
Cleveland Clinic develops bionic arm that restores ‘natural behaviors’
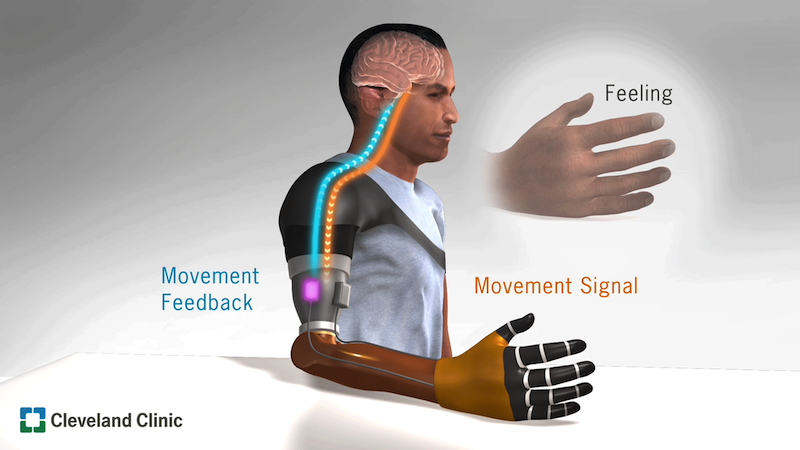
It enables patients to send nerve impulses from their brains to the prosthetic
when they want to use or move it, and to receive physical information from the
environment and relay it back to their brain through their nerves. The
artificial arm’s bi-directional feedback and control enabled study participants
to perform tasks with a similar degree of accuracy as non-disabled people.
“Perhaps what we were most excited to learn was that they made judgments,
decisions and calculated and corrected for their mistakes like a person without
an amputation,” said Dr Marasco, who leads the Laboratory for Bionic
Integration. “With the new bionic limb, people behaved like they had a natural
hand. Normally, these brain behaviors are very different between people with and
without upper limb prosthetics.” Dr Marasco also has an appointment in Cleveland
Clinic’s Charles Shor Epilepsy Center and the Cleveland VA Medical Center’s
Advanced Platform Technology Center.
Can healthcare avoid another AI winter?
"AI winter" refers to a period of disillusionment with AI, marked by reduced
investments and progress, which follow periods of high enthusiasm and interest
in AI technology. There have been two AI winters: one between the mid-1980s and
early 1990s and another in the late 1970s and early 1980s, in which expert
systems and practical artificial neural networks rose to prominence. However, it
became clear that these expert systems had limitations that prevented them from
living up to expectations. This resulted in the second AI winter, a period of
decreased AI research funding and a decline in general interest in AI. According
to the Gartner Hype Cycle, we now are at risk of another AI winter in healthcare
due to several AI solutions falling short of their initial hype, including
natural language processing, deep learning and machine learning, which is
decreasing trust in AI by users. Recent examples that highlight the growing
concern over inappropriate and disappointing AI solutions include racial bias in
algorithms supporting healthcare decision-making, unexpected poor performance in
cancer diagnostic support or inferior performance when deploying AI solutions in
real-world environments.
These 'technology scouts' are hunting for the next big thing in tech. Here's how they do it

Setting up a strategy for discovering emerging technologies might seem like a
daunting task, especially for smaller organisations, but a growing number of
tools are now being built to help. Mergeflow, for example, is a Germany-based
startup that automates the process of hunting for innovation. "People come to us
because they know that there is something somewhere," Florian Wolf, the founder
of Mergeflow, tells ZDNet. "It's pretty much all in the web, but you can't
collect and analyse all of the data by yourself. It takes too long. You need
automation to do that." Mergeflow's software, which was used by BMW to build the
company's tech radar, scans thousands of scientific and technological
publications, patents, news, market analyses, investor activities and other data
every day. Users can search for a concept or a category and immediately access
hundreds of potential innovations that are related to their query. The company's
algorithm also looks at startups and companies working on each specific
innovation to find out how mature they are, based on data like venture funding
or collaborations with other researchers and inventors.
How to manage the growing costs of cyber security
Technological solutions aren’t the be all and end all of cyber security, but
they do play a major role in an organisation’s defences. This is truer now than
ever, as organisations find innovative ways to use tech. Cloud services have
shifted into the mainstream in recent years, and they will only become more
popular as businesses embrace remote working. Consider the fact that employees
are now spread across the country or even across the globe, meaning countless
new organisational endpoints, each of which is vulnerable to an attack and must
be protected. These defences rely on continuous, end-to-end monitoring and the
ability to analyse threat data from multiple sources in real time. Threat
monitoring tools should work in combination with a variety of other technologies
– including anti-malware, encryption tools and firewalls as part of a holistic
approach to security. But that’s only one part of the equation. For these tools
to be effective, organisations need experts to implement them correctly and
respond appropriately to the data they gather.
IT Leadership: 10 Ways to Unleash Enterprise Innovation

Innovation never sleeps. It evolves, it accelerates, it takes different forms.
In fact, organizations that want to unleash innovation are wise to discover
what stifles it so they can remove the constraints. For example, innovation
historically resided in research and development (R&D) departments, but
now organizational leaders are more inclined to behave as through innovation
can come from anywhere. In fact, some organizations believe in democratizing
innovation so much that they encourage experimentation, host competitions and
may even provide financial incentives. According to Jeff Wong, global chief
innovation officer at multinational professional services network
EY, CEOs are realizing they can't rely
on a traditional innovation team when the context of company's competition has
changed. For example, retail banks used to compete against each other by
stealing each other's accounts, but the same tactic won't work when the new
competition is cryptocurrencies or a social network that offers stored value
or investment alternatives.
Applying Genetic Engineering to your Organization Culture
Organizational culture is the organization’s behavioural blueprint; we can
also call it Organization DNA. It includes the unspoken instructions of how
one should behave as part of the organization, those are the human behaviour
boundaries in the working environment. This concept of hidden behavioural
codes that are unique for each organization has been demonstrated many times;
when an employee from one organization joins another organization, they sense
those codes and change their behavior. One of the greatest challenges in
finding a suitable mechanism for manipulating the behavioural codes was that
most of the genetic engineering concepts did not work at scale. Many of the
methods needed very specific indicators in order to allocate specific cells
that were candidates for manipulation. Deepening the investigation, we came
across a field of science called epi-genetic. This field explored the
environmental influence on DNA replication, and scientifically proved that
cell manufacturing is influenced not only by the DNA blueprint, but also by
the cell environment.
Quote for the day:
"A leadership disposition guides you
to take the path of most resistance and turn it into the path of least
resistance." -- Dov Seidman
No comments:
Post a Comment