 The difference between doing analytics completely on an endpoint device or partially on a device is an important one, according to Gartner research vice president Mark Hung. At the core, the analytics done by IoT implementations is about machine learning and artificial intelligence, letting systems take data provided by smart endpoints and fashion it into actionable insights about reliability, performance, and other line-of-business information automatically. Applying the lessons learned from sophisticated ML is easy enough, even for relatively constrained devices, but some parts of the ML process are much too computationally rigorous to happen at most endpoints. This means that the endpoints themselves don’t change their instructions, but that they provide information that can be used by a more powerful back-end to customize a given IoT implementation on a per-endpoint basis. The case of video analytics for smart city applications like traffic monitoring – using a system where the cameras themselves track pedestrians and motorists, then score that data against a centrally-created AI model – is an instructive one.
The difference between doing analytics completely on an endpoint device or partially on a device is an important one, according to Gartner research vice president Mark Hung. At the core, the analytics done by IoT implementations is about machine learning and artificial intelligence, letting systems take data provided by smart endpoints and fashion it into actionable insights about reliability, performance, and other line-of-business information automatically. Applying the lessons learned from sophisticated ML is easy enough, even for relatively constrained devices, but some parts of the ML process are much too computationally rigorous to happen at most endpoints. This means that the endpoints themselves don’t change their instructions, but that they provide information that can be used by a more powerful back-end to customize a given IoT implementation on a per-endpoint basis. The case of video analytics for smart city applications like traffic monitoring – using a system where the cameras themselves track pedestrians and motorists, then score that data against a centrally-created AI model – is an instructive one.The anatomy of fake news: Rise of the bots
Spreading misinformation has become a mainstream topic to the extent that even the term ‘Twitter bot’ is a well-recognised term establishing itself into the modern lexicon. Whilst the term is well known, it can be argued that the development and inner workings of Twitter bots are less well understood. Indeed, even identifying accounts that are attributed to being a bot is considerably more difficult, and with good reason since their objective to appear as legitimate interactions require constant refinement. This continuous innovation from botnet operators are necessary as social media companies get better at identifying automated accounts. A recent study conducted by SafeGuard Cyber analysed the impact and techniques leveraged by such bots, and in particular looked at bots attributed to Russian disinformation campaigns on Twitter. The concept of bot armies is challenged in the research, of the 320,000 accounts identified the bots were divided into thematic categories presenting both sides of the story.How to retrofit the cloud for security: 2 essential steps

Identity and access management (IAM) can be retrofitted after a cloud migration without a lot of effort. While it depends on the IAM system you use, the native IAM systems found in clouds such as Amazon Web Services and Microsoft Azure are typically both a better choice and a quicker choice. At the end of the day, of course, it’s your particular requirements that will determine your choice of IAM. Keep in mind that IAM systems depend on directory services to maintain identity and to provide the proper authorization to those identities. You must deploy one of those systems if you don’t already have one. Also, keep in mind that IAM is only of value if all applications and data are included in the system, both in the cloud and on-premises. I’m not a fan of shortcuts when it comes to cloud computing security. However, reality sometimes makes these shortcuts a necessary evil. The result is not as good as if security were integrated from the start. However, if security was not implemented, most data and applications are at risk for hackery.
Why Everyone’s Thinking About Ransomware The Wrong Way

If you think your IT systems are the target of ransomware, you’re not alone. But you’re also not correct. Your IT systems are just the delivery mechanism. The real target is your employees. Ransoms rely on psychological manipulation that IT systems aren’t susceptible to (AI isn’t there just yet). The systems are the prisoner being held for money. The psychology of ransomware is complex, and the two main types — locker and crypto — use different tactics and are successful within different populations of people (more on this later). It’s not just a case of getting your workforce to abide by security rules and keep their eyes open for dodgy ransom notes (this just helps prevent the data and system from becoming prisoners). You must recognize their unique psychological susceptibilities and design work practices that prevent individuals within your workforce from becoming attractive targets. As mentioned above, ransomware uses complex psychological tactics to get their targets to pay. The two main types of ransomware play off different psychological vulnerabilities.
Here's what two executive surveys revealed about blockchain adoption

Rajesh Kandaswamy, a Gartner fellow and chief blockchain researcher, had a more sobering analysis of blockchain adoption, saying that while interest among enterprises is high, actual deployments are rare. Even when enterprises do perform proof of concept projects, they're often rolled out under pressure from executives who want to do "something" with blockchain. "Most industries are not close to adoption, and even when they do, they do limited activity to test the technology, not as much because of a strong business case," Kandaswamy said via email. A Gartner CIO survey released in May revealed that fewer than 1% of more than 3,100 respondents had rolled out production blockchain systems. Gartner has since completed a second survey whose numbers have yet to be released, but adopters remain low, Kandaswamy said. ... "The challenge for CIOs is not just finding and retaining qualified engineers, but finding enough to accommodate growth in resources as blockchain developments grow," Gartner Research vice president David Furlonger stated in the report.
Android 'API breaking' vulnerability leaks device data, allows user tracking
All versions of Android, including OS forks -- such as Amazon's Kindle FireOS -- are believed to be affected, potentially impacting millions of users. The cybersecurity firm initially reported its findings to Google in March. ... The patch was confirmed in early August, leading to the public disclosure of the vulnerability. Google has fixed the security flaw in the latest version of the Android operating system, Android P, also known as Android 9 Pie. However, the tech giant will not fix prior versions of Android as resolving the vulnerability "would be a breaking API change," according to the cybersecurity firm. Earlier this month, Google announced the launch of Android 9 Pie, which is already rolling out to Android users on some devices. Android devices manufactured by vendors including Nokia, Xiaomi, and Sony will receive the updated OS by the end of fall. The update includes new gesture navigation, themes, and adaptive settings for screen brightness and battery life, among others. Users able to upgrade to Android 9 are encouraged to do so.Chip shrinking hits a wall -- what it means for you
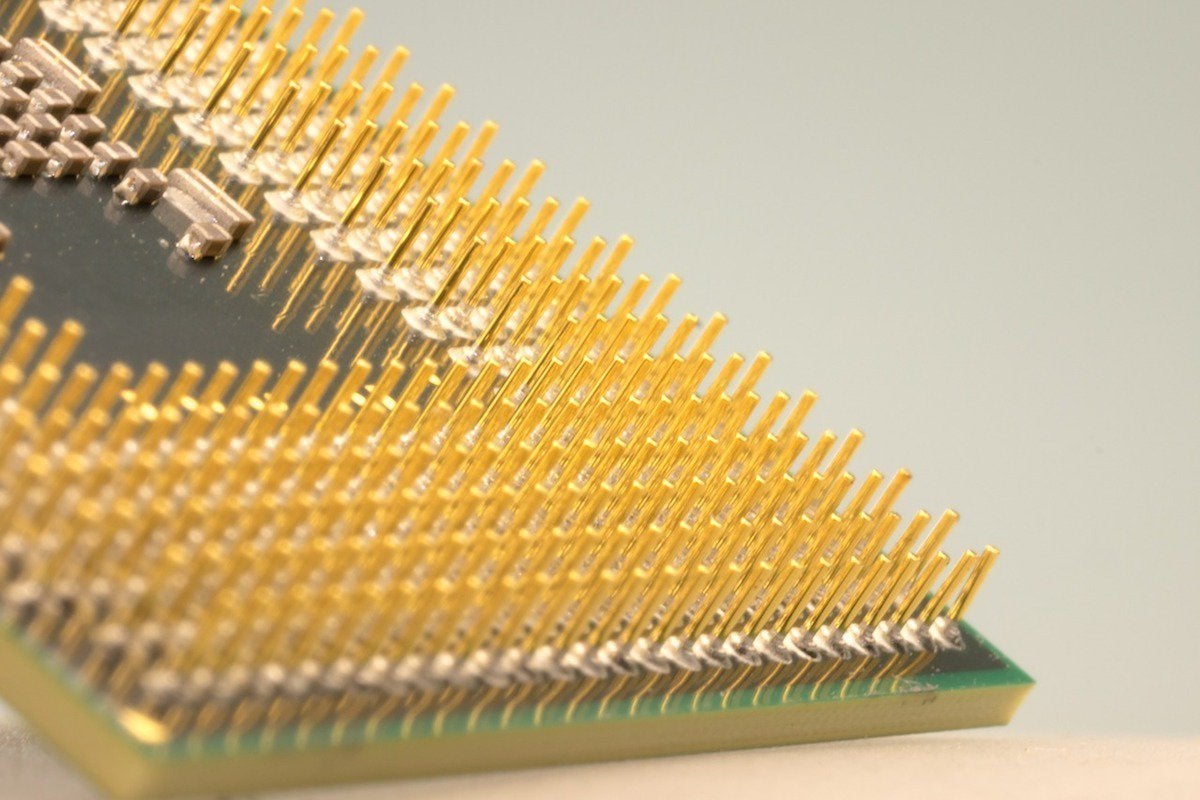
“The vast majority of today’s fabless customers are looking to get more value out of each technology generation to leverage the substantial investments required to design into each technology node. Essentially, these nodes are transitioning to design platforms serving multiple waves of applications, giving each node greater longevity. This industry dynamic has resulted in fewer fabless clients designing into the outer limits of Moore’s Law,” said Thomas Caulfield, who was named CEO of GlobalFoundries last March, in a statement. Making the move to a new process node is no trivial matter. It takes billions to drop one size in process technology. What Caulfield is saying is there are fewer customers for such bleeding-edge manufacturing processes, so the return on investment isn’t there. “I think we’ve reached a change in Moore’s Law. Moore’s Law is an economic law: that we reduce the cost of transistors with each generation. We will still reduce the size of the transistor but at a slower rate,” said Jim McGregor, president of Tirias Research, who follows the semiconductor industry.
No-code and low-code tools seek ways to stand out in a crowd

A suite of prebuilt application templates aim to help users build and customize a bespoke application, such as salesforce automation, recruitment and applicant tracking, HR management and online learning. And a native mobile capability enables developers to take the apps they've built with Skuid and deploy them on mobile devices with native functionality for iOS and Android. "We're seeing a lot of folks who started in other low-code/no-code platforms move toward Skuid because of the flexibility and the ability to use it in more than one type of platform," said Ray Wang, an analyst at Constellation Research in San Francisco. "People want to be able to get to templates, reuse templates and modify templates to enable them to move very quickly." Skuid -- named for an acronym, Scalable Kit for User Interface Design -- was originally an education software provider, but users' requests to customize the software for individual workflows led to a drag-and-drop interface to configure applications.
Will Google's Titan security keys revolutionize account security?

Titan security keys use the FIDO Universal Second Factor (U2F) protocol, which relies on public key cryptography. Adding a Titan device to an account ties a public encryption key to that account, which is verified against a private key using a cryptographic signature supplied by the Titan device during login. Titan keys also protect against phishing attacks from fake login portals—even with a compromised password a Titan-enabled account is still protected. When a user logs in to a fake portal, Google said, the key will know that it isn't a legitimate website and will stop the login process immediately. Don't assume that Titan keys are only usable with Google accounts—the FIDO protocol is a popular one that works with a multitude of websites and applications. Any website that supports U2F will work with a Titan key. Titan hardware is also built to be secure—Google designed the devices around a secure element hardware chip that contains all the necessary firmware for it to function, and all of that information is sealed in during the manufacturing process, as opposed to being installed afterward.
DDD With TLC

When introducing DDD to a new team, start with bounded contexts – breaking down big problems into small, manageable, solvable problems. But leave out the terminology and just start doing it. Understanding the dynamics of a team in order to successfully coach them has a lot to do with instinct and empathy. It’s so important to listen carefully, be respectful, non-judgmental and to be kind. People resist DDD because they believe it is too much to learn or is too disruptive to their current process. Solving small problems is a good approach that can gain trust in adopting DDD. Domain modeling is an art, not a science, so it’s not uncommon to run into a wall and circle back or even have a revelation that makes you change direction. Teams benefit from encountering that with a coach who is familiar with modeling and is not worried about the perspective changing while you are going through the process.
Quote for the day:
"A company is like a ship. Everyone ought to be prepared to take the helm." -- Morris Wilks