
Edge networking was only one of the areas of growing interest revealed in the study. Another hot technology is Intent-Based Networking (IBN) which basically employs automation, analytics, intelligent software and policies that let network administrators define what they want the network to do. Cisco, Juniper along with startups such as Apstra have made IBN technology a relatively new industry buzzword and the study proves that out: More than half of network professionals that we surveyed are familiar with intent-based networking (54%), and one-third of them work at companies with IT budgets of more than $1 billion. “It’s not surprising then that only 3% report adoption of an intent-based network and 8% are beginning to execute an intent-based networking strategy, including investing in SDN [software-defined networking], virtualization, machine learning, model-based APIs and security tools. A larger pool (38%) have not yet considered this strategy but plan to begin research in the next 12 months,” Network Worldwrote.
Ending the estrangement: Why the CIO and the CMO need to collaborate

Breaking down data silos and supporting a compelling customer experience are at the top of the list. Creating a single view of the customer and personalizing communications involves more than building out APIs to connect internal and external data sets. Customer identity management needs to be centralized, so that updates to one part of a profile are instantly and automatically reflected in all the databases in which that customer’s data is held. This is a major marketing requirement, but the execution is up to IT. Marketing also needs IT’s help to navigate new data privacy standards such as the EU’s General Data Protection Regulation (GDPR). ... It is up to IT to determine the right balance between personalization and privacy without compromising marketing’s effectiveness or breaking the law. Good models for this are the IT departments in highly regulated industries, such as financial services and healthcare, that have already succeeded at putting terabytes of customer data in the hands of their marketers, while remaining complaint with myriad regulations. In sum, marketing can no longer go it alone with its digital agenda.
Unit Testing With Mockito
TDD (Test Driven Development) is an effective way of developing the system by incrementally adding the code and writing tests. Unit tests can be written using the Mockito framework. In this article, we explore a few areas of writing unit tests using the Mockito framework. We use Java for the code snippets here. Mocking is a way of producing dummy objects, operations, and results as if they were real scenarios. This means that it deals with no real database connections and no real server up and running. However, it mimics them so that the lines are also covered and expect the actual result. Thus, it can be compared with the expected result and asserted. Mockito is a framework that facilitates mocking in the tests. Mockito objects are kind of proxy objects that work on operations, servers, and database connections. We would be using dummy, fake, and stub wherever applicable for mocking. We will use JUnit with the Mockito framework for our unit tests.
Audi to test 5G use cases in car production

Audi and Ericsson believe that many potential characteristics of the emerging 5G standard – notably its ability to run faster, low-latency, high-capacity, highly secure mobile networks – lend themselves to complex, automated production environments such as a car factory. In Germany, the trend towards digitisation of industrial production is known as Industry 4.0, and it is a key government initiative spearheaded by the German Ministry of Education and Research (BMBF) and the Ministry for Economic Affairs and Energy (BMWI) under chancellor Merkel. The first phase of the collaboration will see Audi and Ericsson working together on a latency-critical application using wireless production robots equipped with a gluing application for bodywork construction. Eventually, the Audi lab – which, in recent years, has explored big data in supply chain logistics and augmented reality in engine assembly, among other things – will be equipped with a 5G-enabled, simulated production environment that mirrors Audi’s real-life production line in nearby Ingolstadt.
5 Google Assistant tasks that will make your work life easier
Google Assistant is, without question, the most powerful and user-friendly virtual assistant on the market. Powered by AI, Assistant can help you with so many things: from answering questions to scheduling to making reservations to getting the latest weather from Mars—and even helping you with your bedtime routine. Yet for most users, the depth and breadth of what Assistant can do goes largely untapped. Why? Because it can do so much. With that in mind, I thought I'd share with you five tasks that can make your busy life a bit easier. Of course everyone's idea of "easier" varies, so I'm going to attempt to make these as broad and universal as possible ... at least within the realm of IT. Keep in mind, this is about making your life a bit easier, not more productive. Whether you're shopping for a family, your department, a client, a job, or yourself, it can be a daunting task to keep track of what you need to purchase ... especially when you're on the go. Driving to a client? The last thing you need is to pull out that phone to remind yourself to pick up Cat5 cable. Instead, use Google Assistant.
PSD2: Blessing or Curse for Banks?
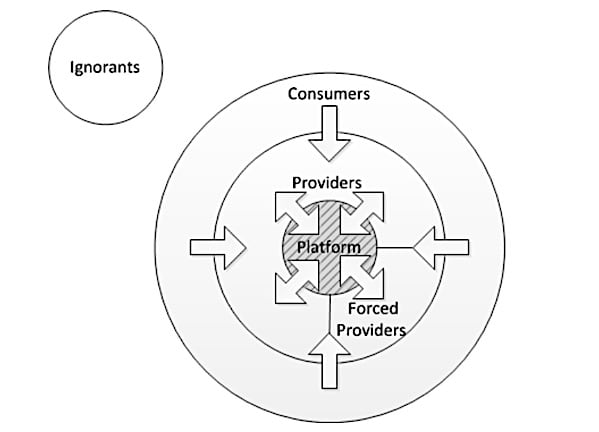
PSD2 is a new European regulation that forces all banks in the European Union to open up their systems to outside players. Banks have to offer 3 APIs free of charges to all 3rd parties approved by the ECB: Accounts, Transactions and Payments. By forcing banks to open up a number of their core systems, the ECB hopes to stimulate innovation into the financial industry through an open API ecosystem. PSD2 brings a lot of challenges and investments for banks without any financial compensation in return: they have to invest in an API gateway, API security, modernizing some of their core systems to expose APIs, etc. and they have to offer the same performance for their APIs as for their existing banking app and website. So, as bank, you can definitely consider PSD2 as a legal obligation similar to GDPR. On the other hand you can also see it as a first step in opening up your core systems and becoming a digital player. If you were planning to strive for an Open API business strategy, than the PSD2 investments are anyway necessary. PSD2 forces you to offer the 3 APIs for free, but PSD2 also doesn’t prevent you from monetizing other APIs
Your hacked devices are being used for cyber crime says FBI
"Devices in developed nations are particularly attractive targets because they allow access to many business websites that block traffic from suspicious or foreign IP addresses. Cyber actors use the compromised device's IP address to engage in intrusion activities, making it difficult to filter regular traffic from malicious traffic," said the alert. IoT devices make easy targets for attackers because many are still shipped with poor security, often enabling attackers to gain access with the use of default username and passwords, or by using brute force attacks to guess passwords - and that's if the devices even have authentication processes in the first place. When security loopholes are uncovered in IoT devices, some vendors will push out firmware and software updates in order to prevent vulnerabilities being exploited - but given how large numbers of smart devices are connected to the internet then forgotten about, it's not guaranteed that users will apply the patches required to protect them from attacks.
How to identify a high-performing tech job candidate: 5 traits
If companies want high-performance employees, they must foster an environment where those individuals can flourish. "Regardless of what business you're in, if you want to improve a team it's critical that employees are engaged," said Cameron Smith, senior global director at Genesys. "Gallup's 2017 State of the American Workplace report found, 'Business or work units that score in the top quartile of their organization in employee engagement have nearly double the odds of success when compared with those in the bottom quartile.'" To fundamentally improve a team, supervisors and business executives need to step up. Employees can't be engaged in a company that isn't worth engaging in. "Instead, it's more of a two-way street, with companies playing a large role in fostering talent," said Smith. "The competence of an employee's supervisor, making sure appropriate workloads are assigned, and company culture all play a role in keeping staff performing at a high-level."
Manage APIs with connectivity-led strategy to cure data access woes

Once DevOps teams deliver microservices and APIs, they see the value of breaking down other IT problems into smaller, bite-size chunks. For example, they get a lot of help with change management, because one code change does not impact a massive, monolithic application. The code change just impacts, say, a few services that rely on a piece of data or a capability in a system. APIs make applications more composable. If I have an application that's broken down into 20 APIs, for example, I can use any one of those APIs to fill a feature or a need in any other application without impacting each other. You remove the dependencies between other applications that talk to these APIs. Overall, a strong API strategy allows software development to move faster, because you don't build from the ground up each time. Also, when developers publish APIs, they create an interesting culture dynamic of self-service.
Apache OpenWhisk vulnerability targets IBM Cloud Functions
According to PureSec's tests, an intruder could exploit the vulnerability to insert malicious code with the same permissions as the serverless function it replaced. Specifically, a remote attacker could overwrite the source code of a vulnerable function executed in a runtime container and influence subsequent executions of the same function in the same container. The attacker could then extract confidential customer data, such as passwords or credit card numbers; modify or delete data; mine cryptocurrencies; and more, Segal said. Other OpenWhisk-based serverless platforms, such as Adobe I/O, were not impacted by the vulnerability because a provider may opt not to use the runtime images provided by Apache OpenWhisk, said Rodric Rabbah, co-creator of OpenWhisk and recent co-founder of CASM, a stealth startup focused on serverless computing. OpenWhisk accepts user functions and then dynamically injects that code into Docker container images; a vendor can provide its own images, for example to provide a runtime that contains libraries that are important for their organization.
Quote for the day:
"Without deviation from the norm, progress is not possible." -- Frank Zappa
No comments:
Post a Comment