How quantum computers will destroy & save cryptography
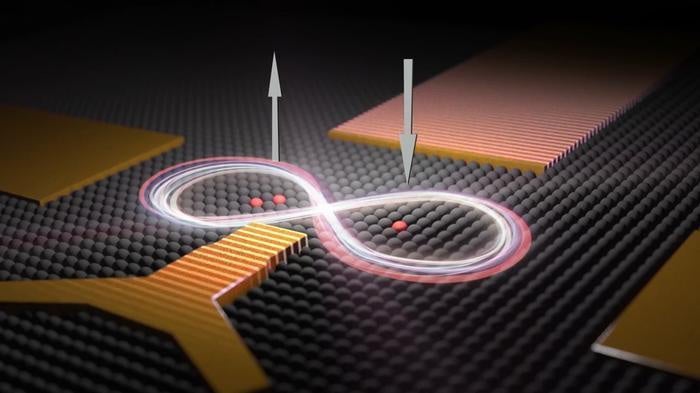
To crack most current public key encryption, it would take a quantum computer with at least 4,000 perfect qubits or many times that number if the qubits were imperfect. How close are we to a perfect 4,000 qubits? It depends on who you ask. Dr. Jackson is confident that we’ll have perfect 4,000-qubit quantum computers in the next five years. He has some evidence to support his claim, although we are nowhere near 4,000 perfect qubits. In March 2018, Google announced an imperfect 72-qubit computer. Google’s current (publicly known) implementation makes a mistake about once every 200 calculations. When you’re doing billions of calculations a second, that error rate is an unusable disaster. Tens if not hundreds of billions of dollars are being spent around the world trying to make more stable quantum computers. Some say that the jump needed to get to 4,000-qubits is not as daunting as it once was. Dr. Jackson, who is directly working with quantum computers says, “We have gone from nine to 72 qubits in just one year, so it’s not crazy at all that we could get 4,000 in another five [years]. Given that the US government finally got on board a few months ago, I think that’s now a conservative estimate.”
Evaluating Hyperledger Composer
Hyperledger Composer allows you to write smart contracts in server-side JavaScript. It makes available a native client library by which Node.js applications can access the ledger and submit transactions to these smart contracts. For the purposes of this experiment, I used an already developed Node.js microservice as the control. I copied the source code for that microservice to a new folder then I replaced all references to MySQL, Redis, and Cassandra with calls to the Hyperledger Composer client API. It is the feed7 project that serves as the test in this experiment. Both projects use Elasticsearch because one of the requirements of each news-feed service is a keyword-based search, and a blockchain is not appropriate for that. Like most of the other microservices in this repo, the feed7 microservice uses Swagger to define its REST API. The specification can be found in the server/swagger/news.yaml file. With Hyperledger Composer, you create a business network that consists of a data model, a set of transactions that manipulate the data model, and a set of queries by which those transactions can access data within the model.
Mastering MITRE's ATT&CK Matrix
Originally developed to support Mitre's cyberdefense work, ATT&CK is both an enormous knowledge base of cyberattack technology and tactics and a model for understanding how those elements are used together to penetrate a target's defenses. ATT&CK, which stands for Adversarial Tactics, Techniques, and Common Knowledge, continues to evolve as more data is added to the knowledge base and model. The model is presented as a matrix, with the stage of event across one axis and the mechanism for that stage across the other. By following the matrix, red team members can design an integrated campaign to probe any aspect of an organization's defense, and blue team members can analyze malicious behavior and technology to understand where it fits within an overall attack campaign. Mitre has defined five matrices under the ATT&CK model. The enterprise matrix, which this article will explore, includes techniques that span a variety of platforms. Four specific platforms — Windows, Mac, Linux, and mobile — each have their own matrix.
Intelligent transportation: The most important pillar of a smart city?

Intelligent transportation must be a first step in the smart city movement. This could include monitoring traffic patterns, highly trafficked pedestrian areas, metro stations, coordinating train times and much more. When cities host large events that increase traffic and security concerns, it becomes increasingly clear that any smart city initiative must begin with intelligent transportation. Intelligent transportation can improve overall situational awareness while enhancing interoperability and the ability to share information quickly. It provides a holistic approach to risk management as it fortifies emergency preparedness and response capabilities for cities, including fare evasion, vandalism or violence, medical emergencies, track obstructions and other similar types of disruptive events. ... Rather than focusing on the short-term fixes, cities and states can find holes where smart transportation solutions can resolve major issues. This leads to improved traffic flow, better roads, and can even help support law enforcement by identifying safety hazards and where cameras should be installed.
The biggest data breaches in the ASEAN region

When it comes to data breach control, the prospects are even gloomier. Whereas Philippines or Indonesia require that data controllers notify promptly affected users in the case of a data breach, Thailand, Brunei or Malaysia don’t have specific notification requirements in this particular scenario. This makes more difficult to know the real extent of actual data breaches in those countries as most of them would go unreported. Since the lack of sector-specific governance and policies is a problem around the whole region, ASEAN could benefit of a coordinated approach similar to the one implemented in the European Union (EU). In 2013 the EU developed a Cybersecurity Package, a region-wide cybersecurity strategy to “enhance the EU’s overall performance” and to “safeguard an online environment providing the highest possible freedom and security for the benefit of everyone.” The package was reviewed last year and marks a milestone in the fight against cybercrime in the union. Below we have compiled a list of the most serious data breach incidents in the ASEAN region during the past few years.
Lessons From The Amazon Ecosystem
The ARM Holdings design ecosystem is a set of relationships between major mobile device vendors, silicon manufacturers and chip designers, usually organised by Arm. It’s a highly specialised and effective ecosystem that can push chip design in novel directions and move designs to manufacture quickly because of the inclusion of silicon factories and smartphone makers. Very few ecosystems work this way. In fact the Amazon ecosystem in books is trying to optimise the Amazon platform rather than optimise or maximise market opportunity and customer success. Take the role of book arbitrage (mid-right in blue in the diagram above). In essence this means finding books deep in the Amazon catalogue, buying them cheaply, and then using more effective descriptions to sell them, also on Amazon, at a higher price. It makes up for Amazon’s indiscriminate search engine and the poor product descriptions of most booksellers. It pays the Amazon ecosystem to get any good enough product to market to tap into the long tail, at a very low price (99 cent novels). That is output rather than outcome; it is a product that does not necessarily please customers as much as might be possible at a lower volume of publishing.
By 2020, 1-in-5 healthcare orgs will adopt blockchain; here’s why

While there is some degree of network interoperability between healthcare providers, pharmacies and insurance companies through various frameworks like HIEs, they've had "varying degrees of success and penetration," IDC said. It cited innate shortcomings that include "limitations in the interoperability standard or protocol itself, workflow and policy differences between entities, information blocking, and technology requirements." Two leading HIEs – CommonWell Health Alliance, a trade association working toward healthcare record interoperability, and Carequality, a public-private collaborative created to establish a common interoperability framework – have had success in establishing a solid industry foundation for data exchange with the backing of EHR vendors. "And that's facilitating a somewhat limited form of query-based [data] exchange," said Mutaz Shegewi, IDC's research director for provider IT transformation strategies. Shegewi was referring to the ability to search for secured patient information online.
IT Managers: Are You Keeping Up with Social-Engineering Attacks?
Using both high-tech tools and low-tech strategies, today's social-engineering attacks are more convincing, more targeted, and more effective than before. They're also highly prevalent. Almost seven in 10 companies say they've experienced phishing and social engineering. For this reason, it's important to understand the changing nature of these threats and what you can do to help minimize them. Today's phishing emails often look like exact replicas of communications coming from the companies they're imitating. They can even contain personal details of targeted victims, making them even more convincing. In one incident, bad actors defrauded a U.S. company of nearly $100 millionby using an email address that resembled one of the company's vendors. And in the most recent presidential election, hackers used a phishing email that appeared to come from Google to access and release a top campaign manager's emails. Bad actors can get sensitive data in many other ways. In one case, they manipulated call-center workers to get a customer's banking password.
NVME SSDs, The Insanely Fast Storage You Want In Your PC
It’s possible to add an NVMe drive to any PC with an PCIe slot via a $25 adapter card. All recent versions of the major operating systems provide drivers, and regardless of the age of the system you will have a very fast drive on your hands. But there’s a catch. To benefit fully from an NVMe SSD, you must be able to boot the operating system from it. That requires BIOS support. Sigh. Most older mainstream BIOSes do not support booting from NVMe and most likely, never will. ... While just about any NVMe should make your system feel quicker, they are not all alike. Not even close. Where Samsung’s 970 Pro will read at over 3GBps and write at over 2.5GBps, Toshiba’s RC100 reads at 1.2GBps and writes at just under 900MBps. The difference can be even greater when the amount of data written exceeds the amount of cache on board. A number of factors that affect performance, including the controller, the amount of NAND on board, the number or PCIe lanes (see above), and the type of NAND.
Strong governance programs separate data lakes from swamps
A good data governance framework combined with a data catalog can keep a data lake pristine by cleaning up the disorderly swamp of data. A data catalog offers a single source of intelligence for data experts and other data users who need quick access to their data. Users can tag, document, and annotate data sets in the data catalog, continuously enriching the data and increasing the value of existing data assets while also eliminating data silos. A data catalog enables users to collaborate to understand the data’s meaning and use, to determine which data is fit for what purpose, and which is unusable, incomplete, or irrelevant. It provides a way for every user to find data, understand what it means, and trust that it’s correct. Businesses today are either building a brand new lake, or cleaning up an existing data lake. Whether you’ve inherited a swamp, or are just starting out and want to keep your data lake pristine, establishing a set of policy-driven processes can help you avoid these four common data lake problems
Quote for the day:
"Leadership in the past was a model of direction and control. Now it should help people set directions for the future and facilitate their delivery." -- John Bailey
No comments:
Post a Comment