How to write a cyberthreat report executives can really use

Although there’s no single template for crafting a threat report, “it should
look like whatever you think people will read," says deGrazia. "Senior managers
get hit with lots and lots of paper, so whatever format it’s in, it has to get
their attention.” CISOs also need to consider how often they want to generate
these reports. Security leaders say the reports should come out on a regular
schedule, whether they’re passed out weekly as Stebila did, monthly, or
quarterly. The best schedule is one that matches the organization’s own cultural
tempo, Rawlins says, adding that CISOs could also create and distribute
customized reports to different recipients on different schedules based on the
varying levels of threats and interest levels each party has. CISOs could, for
example, share reports weekly with their CIOs but distribute them to the board
only semi-annually. That regular schedule should not preclude sending out threat
reports in response to urgent issues, security experts say. “You can’t ignore
the fact that things come up, and come up quickly, and those things need to be
communicated up the chain as quickly as possible,” deGrazia adds.
Consumer data protection is a high priority, but there’s still work to be done
“Most pertinently, it’s encouraging that consumer data protection is such a high
priority for organizations, but there is clearly some work to be done in turning
that priority into a reality in terms of what data is actually encrypted and at
what points in the data lifecycle. It’s also apparent that organizations of all
shapes and sizes are looking to adopt encryption for a range of new and
cutting-edge use cases, which will no doubt continue to drive innovation in the
industry.” “IT is tasked with deploying, tracking and managing encryption and
security policy across on-premise, cloud, multi-cloud and hybrid environments,
for an expanding array of uses cases, and amidst widening threats. Encryption is
essential for protecting company and customer data, but managing encryption and
protecting the associated secret keys are rising pain points as organizations
engage multiple cloud services for critical functions,” added Grimm. “Rising use
of HSMs for encryption and key management shows that IT is starting the meet
these challenges. Organizations will benefit from a growing and ecosystem of
integrated solutions for cloud security policy management ...”
The security impact of shadow IT

Shadow IT is also one of the reasons why strict compliance-based approaches to
cyber security can only help you so far. If you are measuring patching of your
internal systems as a security key performance indicator (KPI), for example,
then you need to be conscious that if you have a 99% success rate at patching
servers, an adversary will probably find that 1% of servers you have not
patched. And if you have a 100% success rate at patching servers, you absolutely
have to make sure that every server that exists is part of that measurement – if
you have a server which is not enrolled in asset management and therefore not
monitored in patch management processes, you could still be exposed and not be
aware of it. We talk about the “advanced persistent threat” a lot in security,
and it is easy to get hung up on the “advanced” part of that epithet. Although
“advanced” is dangerous, what we should be most concerned about is “persistent”.
You may have thousands of servers properly enrolled in your technical controls,
fully-monitored and fully-patched – and one undocumented server which is not
patched and not monitored.
Business Process Automation at Scale Is Key to Customer and Employee Experience

“The electronic signature is often where folks start,” asserted Casey of
DocuSign. “I think that’s wonderful, obviously. But we have also started to
step back and think about the systems of agreement that businesses have as a
whole.” ... “Sure, automation will always cut costs—but we want to consider
the experience. That’s what’s durable,” said Casey. During COVID, short-term
fixes on the ground were prioritized over long-term solutions with high-level,
lasting impacts. Now, the tide is beginning to shift. The benefits of
full-scale automation—like better customer experiences, business agility,
increased productivity, and greater security—are clearer than ever before. But
what does strategic end-to-end automation look like in practice? ...
Automating at scale is both technical science and change management art. For
instance, close to 50% of businesses today claim that they are prepared to
invest in an automated, end-to-end contract management solution, but simply
don’t have the tools or know-how to do it effectively. “The problem is that
end-to-end automation requires a lot of technology,” said Koplowitz.
The clash over the hybrid workplace experience

To optimize the employee experience of their hybrid workforce, employers
should focus on "digital parity" as well as employee "experience parity,"
according to IDC. Digital parity refers to the requirement that all workers
have secure access to the resources required to do their jobs, no matter their
preferred device or location (office/remote/in the field). Experience parity
means a democratized workplace, where all employees have the opportunity to
collaborate, learn, develop, innovate and succeed, the report said.
... "Businesses everywhere must place a greater priority on enhancing
employee experiences, which in turn will drive higher productivity,
collaboration and better customer outcomes," said Leon Gilbert, senior vice
president and general manager, Digital Workplace Services, Unisys, in a
statement. "Organizations that adapt to provide digital and experience parity
will not only retain employees in a competitive marketplace but will also
empower those employees to provide the best service possible to their
organization's customers. Do it well and you drive engagement, productivity
and adaptability as new workforce demands emerge."
TCP/IP stack vulnerabilities threaten IoT devices

The actual danger to which an organization is exposed differs based on which
of the vulnerable stacks it’s using. The FreeBSD vulnerability is likely more
widespread – it affects millions of IT networks, including Netflix and Yahoo,
as well as traditional networking devices like firewalls and routers,
according to the report, but is likely easier to fix. “Those are manageable
systems – we should be able to update them,” said Forrester senior analyst
Brian Kime. “[And] they should be prioritized for remediation, because they’re
part of your network stack.” The same cannot be said, in many cases, of the
real-time operating systems affected by Name:Wreck, since the standard issues
that make securing IoT devices remain in play here. The ability to patch and
update firmware is still not a standard feature, and the OEMs of connected
devices – which may be quite old, and may not have been designed to be
Internet-facing in the first place – might not even be operating any more. In
cases where those IoT devices are vulnerable, strong security has to start at
the network layer, according to Hanselman. Monitoring the network directly for
anomalous activity – which, again, can sometimes be difficult to detect in the
case of a TCP/IP vulnerability – is a good start, but what’s really needed is
techniques like DNS query protection.
The Four Fs of employee experience
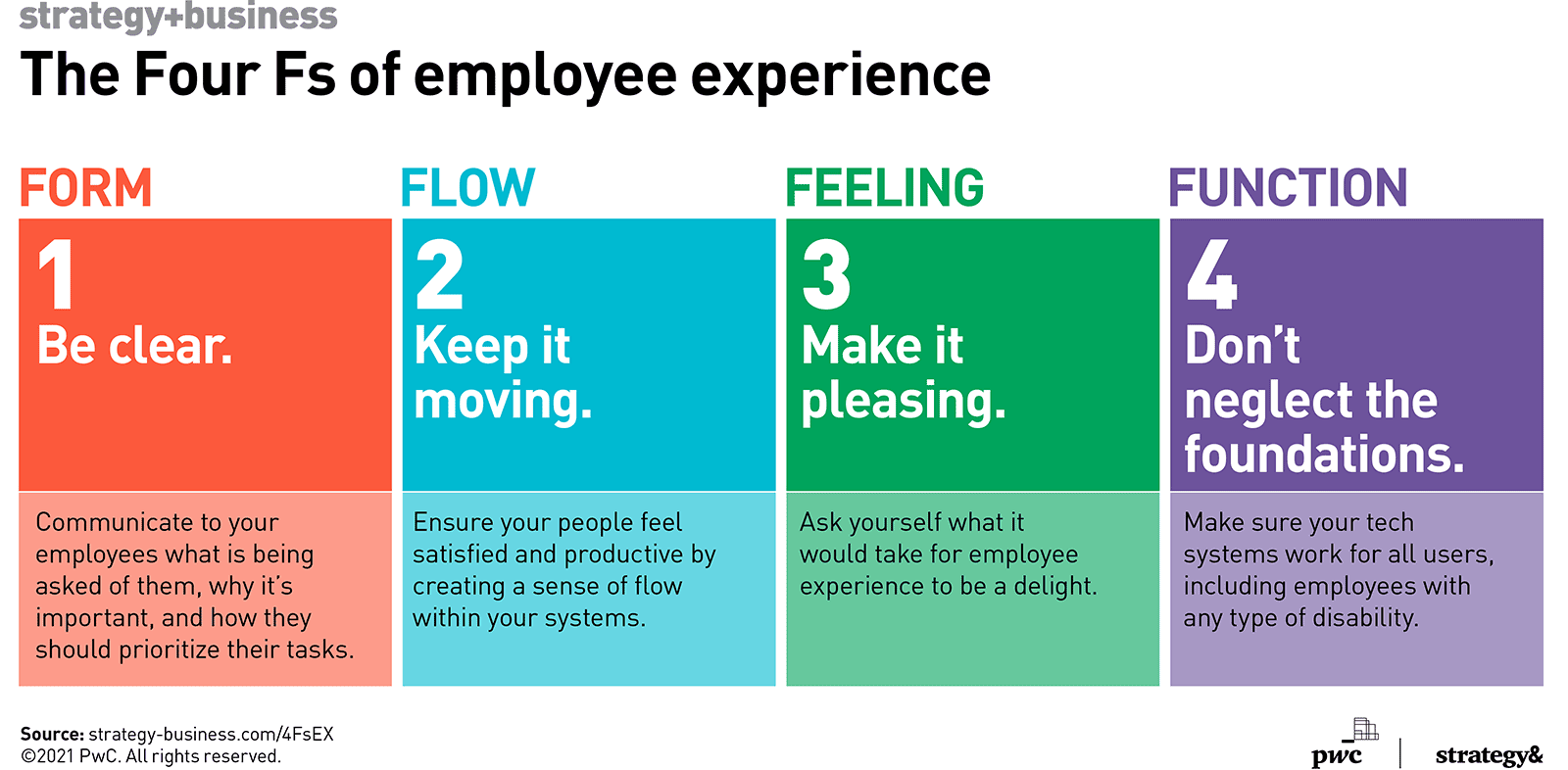
To deliver an optimal employee experience (EX), we recommend focusing on four
principles that we call the Four Fs. They are a set of heuristics inspired by
the user-centric, iterative practice of design thinking, and they rest on the
idea that your business goals, experiences, and technology are inseparable
from one another and must be addressed in a unified, cross-company way. We
refer to this approach as BXT (for business, experience, and technology). When
applied to EX, the Four Fs unlock productivity and cut down on energy-sapping
frustration stemming from internal systems and tools. They are the form, flow,
feeling, and function of an employee’s work life. ... Employees can’t do their
jobs well if they don’t understand what is being asked of them, the purpose of
the work, or how they should prioritize their tasks. A firm we advised
recently had received feedback from staff that the online training module for
a new marketing curriculum it had developed was hard to follow and a bad
experience overall. To address the problem, the company’s user experience team
worked with PwC and a leading software firm to reimagine the employee learning
interface.
Building a learning culture that drives business forward

We all think we have it. So we might say, “I’m a fast learner” or “I’m a slow
learner” or “I learn in this way or that way.” But, actually, a lot of the
underlying research—there are several strands of research—shows that people
can actually build skills to learn new skills. We think of this as one of the
most fundamental capabilities that a person can develop for themselves. It
makes you better at getting better at things. It makes you better able to
adapt to the changing environment that we all face these days. This idea of
learning as a skill, in and of itself, is a fundamental one, and one that we
talk to a lot of our clients about and, frankly, a lot of our colleagues as
well. Because they’re also curious. They want to learn. But they need to be
taught. Back in school, you might have thought about this as study skills. How
do I organize myself in order to get my schoolwork done? But there’s a much
more sophisticated version of that when you think about adult learners that I
think we all need to invest in more. ... Learning to follow is listening
before talking and learning how to be a contributor so that you can then lead.
There are a few ways you can learn how to follow.
Concerns grow over digital threats faced from former employees

"A lot of companies fail to have clear policies or a checklist that employers
use for post-employee separation. This is extremely important because failing
to do so is going to involve a lot of things but the most important thing is
that you want to make sure that the former employee or even a subcontractor
that previously had access to the organization's technologies and systems is
completely locked out," Guccione said in an interview. "It's going to avoid
the risk of business disruption. It's going to avoid the risk of the leakage
of intellectual property or trade secrets. It also mitigates legal risk
because what you don't want is any exposure of or unauthorized access to
sensitive data about the organization or its stakeholders. If a door is left
open to a former member of the team and that person is disgruntled, you could
have a real problem on your hands." ... In December, the Justice Department
announced that a former Cisco worker was sentenced to two years in prison
after he accessed the Cisco Systems cloud infrastructure that was hosted by
Amazon Web Services and deleted 456 virtual machines for Cisco's Webex Teams
application.
MLOps, An Insider’s Perspective: Interview With Nikhil Dhawan
Large tech firms have used data science and its various techniques to learn
about consumer behaviour for a long time. They have optimised their
recommendation engines, have bundled products together, improved targeting for
the right customers, increased the basket size and so on. They had the budget
to dedicate resources for research, partnership with academic institutes that
focused highly on statistical knowledge and theory. They also had a
significant engineering function to build infrastructure and tooling required
to build on research outcomes. Smaller or business-focused firms don’t have
this luxury. There is a big task list on any data science project that ranges
from data acquisition, data ingestion, determining or starting with initial
algorithms, testing multiple variants including tuning the model and
hyperparameters, preparation of the datasets for each experiment, validating
and comparing the outputs etc. Finally, once we get the best possible trained
model, the engineering task is to deploy the model to score or predict on live
data to improve business functions.
Quote for the day:
"A leader does not deserve the name
unless he is willing occasionally to stand alone." --
Henry A. Kissinger
No comments:
Post a Comment