Why the Age of IIoT Demands a New Security Paradigm
 Perhaps the most dangerous and potentially prolific security threats are
employees, experts contend. “We fear Russia in terms of cybersecurity breaches,
but the good-hearted employee is the most dangerous,” says Greg Baker, vice
president and general manager for the Cyber Digital Transformation organization
at Optiv, a security systems integrator. “The employee that tries to stretch
their responsibilities by updating a Windows XP workstation to Windows 10 and
shuts the factory down—they’re the most dangerous threat actor.” Historically,
security of OT environments has been addressed by preventing connectivity to
outside sources or walling off as much as possible from the internet using a
strategy many refer to as an “air gap.” With the latter approach, firewalls are
the focal point of the security architecture, locking down an automation
environment, perhaps in a specific building, to prevent external access as
opposed to a strategy predicated on securing individual endpoints on the
industrial network such as HMIs or PLCs. “We used to live in a world that was
protected—you didn’t need to put a lock on your jewelry drawer because you had a
huge fence around the property and no one was getting in,” explains John
Livingston
Perhaps the most dangerous and potentially prolific security threats are
employees, experts contend. “We fear Russia in terms of cybersecurity breaches,
but the good-hearted employee is the most dangerous,” says Greg Baker, vice
president and general manager for the Cyber Digital Transformation organization
at Optiv, a security systems integrator. “The employee that tries to stretch
their responsibilities by updating a Windows XP workstation to Windows 10 and
shuts the factory down—they’re the most dangerous threat actor.” Historically,
security of OT environments has been addressed by preventing connectivity to
outside sources or walling off as much as possible from the internet using a
strategy many refer to as an “air gap.” With the latter approach, firewalls are
the focal point of the security architecture, locking down an automation
environment, perhaps in a specific building, to prevent external access as
opposed to a strategy predicated on securing individual endpoints on the
industrial network such as HMIs or PLCs. “We used to live in a world that was
protected—you didn’t need to put a lock on your jewelry drawer because you had a
huge fence around the property and no one was getting in,” explains John
Livingston9 unexpected skills you need for today's tech team
 Pekelman said that being adaptable is also crucial. "More than ever, teams need
to be agile and flexible—as we've learned, things can truly change in a very
short period of time," he said. Nathalie Carruthers, executive vice president
and chief HR officer at Blue Yonder, agreed that change, innovation and
transformation are the only constants in the tech world. "We look for candidates
who can adapt to this constant change and who have a passion for learning," she
said. In addition to working well with others, IT professionals have to be able
to set priorities for their daily and weekly to-do lists without extensive
guidance from the boss. Jon Knisley, principal of automation and process
excellence at FortressIQ, said employees also should be able to think critically
and act. "With more agile and collaborative work styles, employees need to
execute with less guidance from management," he said. "The ability to conduct
objective analysis and evaluate an issue in order to form a judgement is
paramount in today's environment." Carruthers said technical skills and prior
experience are good, but transferable skills are ideal. "Transferable skills
showcase problem-solving ability, versatility and adaptability—common traits in
successful leaders and essential elements for career development," she said.
Pekelman said that being adaptable is also crucial. "More than ever, teams need
to be agile and flexible—as we've learned, things can truly change in a very
short period of time," he said. Nathalie Carruthers, executive vice president
and chief HR officer at Blue Yonder, agreed that change, innovation and
transformation are the only constants in the tech world. "We look for candidates
who can adapt to this constant change and who have a passion for learning," she
said. In addition to working well with others, IT professionals have to be able
to set priorities for their daily and weekly to-do lists without extensive
guidance from the boss. Jon Knisley, principal of automation and process
excellence at FortressIQ, said employees also should be able to think critically
and act. "With more agile and collaborative work styles, employees need to
execute with less guidance from management," he said. "The ability to conduct
objective analysis and evaluate an issue in order to form a judgement is
paramount in today's environment." Carruthers said technical skills and prior
experience are good, but transferable skills are ideal. "Transferable skills
showcase problem-solving ability, versatility and adaptability—common traits in
successful leaders and essential elements for career development," she said.4 Innovative Ways Cyberattackers Hunt for Security Bugs
 A more time-consuming and less satisfying tactic to find bugs is fuzzing. I was
once tasked with breaking into a company, so I started at a relatively simple
place — its employee login page. I began blindly prodding, entering ‘a’ as the
username, and getting my access denied. I typed two a’s… access denied again.
Then I tried typing 1000 a’s, and the portal stopped talking to me. A minute
later, the system came back online and I immediately tried again. As soon as the
login portal went offline, I knew I found a bug. Fuzzing may seem like an easy
path to finding every exploit on a network, but for attackers, it’s a tactic
that rarely works on its own. And if an attacker fuzzes against a live system,
they’ll almost certainly tip off a system admin. I prefer what I call
spear-fuzzing: Supplementing the process with a human research element. Using
real-world knowledge to narrow the attack surface and identify where to dig
saves a good deal of time. Defenders are constantly focused on making intrusion
more difficult for attackers, but hackers simply don’t think like defenders.
Hackers are bound to the personal cost of time and effort, but not to corporate
policy or tooling.
A more time-consuming and less satisfying tactic to find bugs is fuzzing. I was
once tasked with breaking into a company, so I started at a relatively simple
place — its employee login page. I began blindly prodding, entering ‘a’ as the
username, and getting my access denied. I typed two a’s… access denied again.
Then I tried typing 1000 a’s, and the portal stopped talking to me. A minute
later, the system came back online and I immediately tried again. As soon as the
login portal went offline, I knew I found a bug. Fuzzing may seem like an easy
path to finding every exploit on a network, but for attackers, it’s a tactic
that rarely works on its own. And if an attacker fuzzes against a live system,
they’ll almost certainly tip off a system admin. I prefer what I call
spear-fuzzing: Supplementing the process with a human research element. Using
real-world knowledge to narrow the attack surface and identify where to dig
saves a good deal of time. Defenders are constantly focused on making intrusion
more difficult for attackers, but hackers simply don’t think like defenders.
Hackers are bound to the personal cost of time and effort, but not to corporate
policy or tooling.7 Things Great Leaders Do Every Day
 A leader needs to inspire takeaways, which will bring value to-and-for the team.
Consistency in success relies on having all able hands on deck, working together
and with mutual understanding, to make for the steadiest ship. If you're trying
to build better structure within mid-sized or larger organizations, the Leader
should consider delegating the sharing of information amongst
department/division heads and allow for them to disseminate the state of things
to their reports. Choosing one-on-ones, senior staff huddles, and/or both
(depending on what needs to be accomplished) are good ways to ensure this
process smoothly moves forward. These should not substitute for any regularly
scheduled staff meetings, which should be conducted at the frequency and manner
that most makes sense for your organizational environment, sector, and company
size. In turn, communicating the state of things to your department/division
heads will task and empower them to take progressive roles in having ownership
of communications relevant to their department/division while being “in the
know” on the overall macro level.
A leader needs to inspire takeaways, which will bring value to-and-for the team.
Consistency in success relies on having all able hands on deck, working together
and with mutual understanding, to make for the steadiest ship. If you're trying
to build better structure within mid-sized or larger organizations, the Leader
should consider delegating the sharing of information amongst
department/division heads and allow for them to disseminate the state of things
to their reports. Choosing one-on-ones, senior staff huddles, and/or both
(depending on what needs to be accomplished) are good ways to ensure this
process smoothly moves forward. These should not substitute for any regularly
scheduled staff meetings, which should be conducted at the frequency and manner
that most makes sense for your organizational environment, sector, and company
size. In turn, communicating the state of things to your department/division
heads will task and empower them to take progressive roles in having ownership
of communications relevant to their department/division while being “in the
know” on the overall macro level.Rearchitecting for MicroServices: Featuring Windows & Linux Containers
 First, let’s recap the definition of what a container is – a container is not a
real thing. It’s not. It’s an application delivery mechanism with process
isolation. In fact, in other videos I have made on YouTube, I compare how a
container is similar to a waffle, or even a glass of whiskey. If you’re new to
containers, I highly recommend checking out my “Getting Started with Docker”
video series available here. Second, let’s simplify what a Dockerfile actually
is – the TL;DR is it’s an instruction manual for the steps you need to either
simply run, or build and run your application. That’s it. At its most basic
level, it’s just a set of instructions for your app to run, which can include
the ports it needs, the environment variables it can consume, the build
arguments you can pass, and the working directories you will need. Now, since a
container’s sole goal is to deliver your application with only the processes
your application needs to run, we can take that information and begin to think
about our existing application architecture. In the case of Mercury Health, and
many similar customers who are planning their migration path from on-prem to the
cloud, we have a legacy application that is not currently architected for cross
platform support – I.E. it only runs on Windows.
First, let’s recap the definition of what a container is – a container is not a
real thing. It’s not. It’s an application delivery mechanism with process
isolation. In fact, in other videos I have made on YouTube, I compare how a
container is similar to a waffle, or even a glass of whiskey. If you’re new to
containers, I highly recommend checking out my “Getting Started with Docker”
video series available here. Second, let’s simplify what a Dockerfile actually
is – the TL;DR is it’s an instruction manual for the steps you need to either
simply run, or build and run your application. That’s it. At its most basic
level, it’s just a set of instructions for your app to run, which can include
the ports it needs, the environment variables it can consume, the build
arguments you can pass, and the working directories you will need. Now, since a
container’s sole goal is to deliver your application with only the processes
your application needs to run, we can take that information and begin to think
about our existing application architecture. In the case of Mercury Health, and
many similar customers who are planning their migration path from on-prem to the
cloud, we have a legacy application that is not currently architected for cross
platform support – I.E. it only runs on Windows.How to Change Gender Disparity Among Data Science Roles
 There are times that I see job reqs and I’ll see recruiters come back saying
they’re not finding that type of candidate -- that it doesn’t exist. I’m pretty
convinced that the way the job requisitions are written they are inherently
attracting individuals that may feel more confident. There’s a ton of data
around the idea that individuals that identify as female are far less likely to
apply to a role if they don’t tick every single box whereas their male
counterparts, if they check a third or less, will be bold and apply. I think we
need to do a better job at writing job descriptions that are inclusive. If
there’s roles that you foresee your organization is going to need filled in AI,
robotics, or edge computing -- some of the things that are tip of the spear --
the whole market is stripped out irrespective of what gender or background you
may have. That is a leading indicator that an investment needs to be made.
Whether that’s investing in junior practitioners, or creating alliances and
relationships with local colleges and universities, or being more creative about
how you curate your class of interns so they have time to ramp up, you’ve got to
handle both sides of it.
There are times that I see job reqs and I’ll see recruiters come back saying
they’re not finding that type of candidate -- that it doesn’t exist. I’m pretty
convinced that the way the job requisitions are written they are inherently
attracting individuals that may feel more confident. There’s a ton of data
around the idea that individuals that identify as female are far less likely to
apply to a role if they don’t tick every single box whereas their male
counterparts, if they check a third or less, will be bold and apply. I think we
need to do a better job at writing job descriptions that are inclusive. If
there’s roles that you foresee your organization is going to need filled in AI,
robotics, or edge computing -- some of the things that are tip of the spear --
the whole market is stripped out irrespective of what gender or background you
may have. That is a leading indicator that an investment needs to be made.
Whether that’s investing in junior practitioners, or creating alliances and
relationships with local colleges and universities, or being more creative about
how you curate your class of interns so they have time to ramp up, you’ve got to
handle both sides of it.Cyber attackers rarely get caught – businesses must be resilient
 Hackers are increasingly targeting SMBs as, to them, it’s easy money: the
smaller the business is, the less likely it is to have adequate cyber defences.
Even larger SMBs typically don’t have the budgets or resources for dedicated
security teams or state-of-the-art threat prevention or protection. Ransomware,
for instance, is one of the biggest threats companies are facing today. While we
saw the volume of ransomware attacks decline last year, this was only because
ransomware has become more targeted, better implemented, and much more ruthless,
with criminals specifically targeting higher value and weaker targets. One of
the most interesting – and concerning – findings from our report, “The Hidden
Cost of Malware”, was that the businesses had become preferred targets because
they can and will pay more to get their data back. About of quarter of companies
in our survey were asked to pay between $11,000 and $50,000, and almost 35% were
asked to pay between $51,000 and $100,000. In fact, ransomware has become so
lucrative and popular that it’s now available as a “starter kit” on the dark
web. This now means that novice cyber criminals can build automated campaigns to
target businesses of any size.
Hackers are increasingly targeting SMBs as, to them, it’s easy money: the
smaller the business is, the less likely it is to have adequate cyber defences.
Even larger SMBs typically don’t have the budgets or resources for dedicated
security teams or state-of-the-art threat prevention or protection. Ransomware,
for instance, is one of the biggest threats companies are facing today. While we
saw the volume of ransomware attacks decline last year, this was only because
ransomware has become more targeted, better implemented, and much more ruthless,
with criminals specifically targeting higher value and weaker targets. One of
the most interesting – and concerning – findings from our report, “The Hidden
Cost of Malware”, was that the businesses had become preferred targets because
they can and will pay more to get their data back. About of quarter of companies
in our survey were asked to pay between $11,000 and $50,000, and almost 35% were
asked to pay between $51,000 and $100,000. In fact, ransomware has become so
lucrative and popular that it’s now available as a “starter kit” on the dark
web. This now means that novice cyber criminals can build automated campaigns to
target businesses of any size.How to Secure Employees' Home Wi-Fi Networks
A major security risk associated with remote work is wardriving: stealing Wi-Fi credentials from unsecured networks while driving past people's homes and offices. Once the hacker steals the Wi-Fi password, they move on to spoofing the network's Address Resolution Protocol (ARP). Next, the network's traffic is sent to the hacker, and that person is fully equipped to access corporate data and wreak havoc. A typical home-office router is set up with WPA2-PSK (Wi-Fi Protected Access 2 Pre-Shared Key), a type of network protected with a single password shared between all users and devices. Unfortunately, WPA2-PSK is by far the most common authentication mechanism used in homes, which puts employees at risk for over-the-air credential theft. WPA2-PSK does have a saving grace, which is that the passwords must be decrypted once stolen. Password encryption can prevent hackers from stealing passwords once they have them, but only if they are unique, complex, and of adequate length. Avast conducted a study of 2,000 households that found 79% of homes employed weak Wi-Fi passwords.Solve evolving enterprise issues with GRC technology
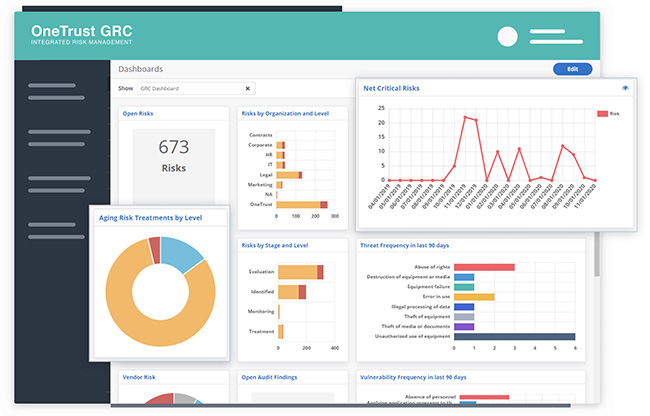 The key challenges organizations face in fulfilling regulator requests is
keeping business data up to date. Organizations of all sizes are working to
reduce the delay between distributing a risk assessment, receiving responses,
understanding their risk insights, and making risk-based decisions. The insights
an organization receives from this work can lose value over time if the data
isn’t kept up-to-date and monitored for compliance. By leveraging data
classification methods and risk formulas, organizations can reduce lag time,
gain real time risk insights and standardize risk at scale. OneTrust GRC
provides workflows to find, collect, document and classify data in real-time to
gain meaningful risk insights and support compliance. ... What sets our GRC
solution apart is that it is integrated into the entire OneTrust platform of
trust. Trust differentiates as a business outcome, not simply a compliance
exercise. Companies nowneed to mature beyond the tactical governance tools of
the past and into a modern platform with centralized workflows that bring
together all the elements of trust: privacy, data governance, ethics and
compliance, GRC, third-party risk, and ESG. OneTrust does just that.
The key challenges organizations face in fulfilling regulator requests is
keeping business data up to date. Organizations of all sizes are working to
reduce the delay between distributing a risk assessment, receiving responses,
understanding their risk insights, and making risk-based decisions. The insights
an organization receives from this work can lose value over time if the data
isn’t kept up-to-date and monitored for compliance. By leveraging data
classification methods and risk formulas, organizations can reduce lag time,
gain real time risk insights and standardize risk at scale. OneTrust GRC
provides workflows to find, collect, document and classify data in real-time to
gain meaningful risk insights and support compliance. ... What sets our GRC
solution apart is that it is integrated into the entire OneTrust platform of
trust. Trust differentiates as a business outcome, not simply a compliance
exercise. Companies nowneed to mature beyond the tactical governance tools of
the past and into a modern platform with centralized workflows that bring
together all the elements of trust: privacy, data governance, ethics and
compliance, GRC, third-party risk, and ESG. OneTrust does just that.Indestructible Storage in the Cloud with Apache Bookkeeper
After researching what open source had to offer, we settled upon two finalists: Ceph and Apache BookKeeper. With the requirement that the system be available to our customers, scale to massive levels and also be consistent as a source of truth, we needed to ensure that the system can satisfy aspects of the CAP Theorem for our use case. Let’s take a bird’s-eye view of where BookKeeper and Ceph stand in regard to the CAP Theorem (Consistency, Availability and Partition Tolerance) and our unique requirements. While Ceph provided Consistency and Partition Tolerance, the read path can provide Availability and Partition Tolerance with unreliable reads. There’s still a lot of work required to make the write path provide Availability and Partition Tolerance. We also had to keep in mind the immutable data requirement for our deployments. We determined Apache BookKeeper to be the clear choice for our use case. It’s close to being the CAP system we require because of its append only/immutable data store design and a highly replicated distributed log.Quote for the day:
"Ninety percent of leadership is the ability to communicate something people want." -- Dianne Feinstein
No comments:
Post a Comment