How we protect our users against the Sunburst backdoor

SolarWinds, a well-known IT managed services provider, has recently become a
victim of a cyberattack. Their product Orion Platform, a solution for
monitoring and managing their customers’ IT infrastructure, was compromised by
threat actors. This resulted in the deployment of a custom Sunburst backdoor
on the networks of more than 18,000 SolarWinds customers, with many large
corporations and government entities among the victims. According to our
Threat Intelligence data, the victims of this sophisticated supply-chain
attack were located all around the globe: the Americas, Europe, Middle East,
Africa and Asia. After the initial compromise, the attackers appear to have
chosen the most valuable targets among their victims. The companies that
appeared to be of special interest to the malicious actors may have been
subjected to deployment of additional persistent malware. Overall, the
evidence available to date suggests that the SolarWinds supply-chain attack
was designed in a professional manner. The perpetrators behind the attack made
it a priority to stay undetected for as long as possible: after the
installation, the Sunburst malware lies dormant for an extended period of
time, keeping a low profile and thwarting automated sandbox-type analysis and
detection.
Why I've Been Merging Microservices Back Into The Monolith At InVision
One of the arguments in favor of creating independent services is the idea that
those services can then "scale independently". Meaning, you can be more targeted
in how you provision servers and databases to meet service demands. So, rather
than creating massive services to scale only a portion of the functionality, you
can leave some services small while independently scaling-up other services. Of
all the reasons as to why independent services are a "Good Thing", this one gets
used very often but is, in my (very limited) opinion, usually irrelevant. Unless
a piece of functionality is CPU bound or IO bound or Memory bound, independent
scalability is probably not the "ility" you have to worry about. ... If I could
go back and redo our early microservice attempts, I would 100% start by focusing
on all the "CPU bound" functionality first: image processing and resizing,
thumbnail generation, PDF exporting, PDF importing, file versioning with rdiff,
ZIP archive generation. I would have broken teams out along those boundaries,
and have them create "pure" services that dealt with nothing but Inputs and
Outputs (ie, no "integration databases", no "shared file systems") such that
every other service could consume them while maintaining loose-coupling.
CIOs see cloud computing as the bedrock of digital transformation
The CIOs also shared their challenges and experiences during the pandemic.
Responding to the big business focus area that tech and cloud will enable or
drive in 2021, Chatterjee shared, “For us, it’s very clear the data and
analytics piece, and all the modeling that we are doing around fraud,
retention propensity, the entire claims experience, I think, across the
value chain, anything that is data and insights. And I will be careful in
using the term ‘analytics’, because in a lot of areas we use analysis and we
incorrectly call it analytics, but the idea is, cloud will enable the entire
data and insights as a capability within the organisation. This is something
big for us and will be driven by the cloud.” For SonyLiv, the focus is on
harnessing the use of data. “We as an organisation, are digital and are
using data in each and every decision that we make, whether it is on the
infrastructure side, content programming, content production, churn
analysis, retention – everywhere. I think it is all about data and
democratisation of the data. We are working big time on introducing some of
the prediction models, machine learning models, which can help us to retain
users. So, I think data is going to play a critical role. The other area
which I feel we as a business, is on the OTT side.
Why Boring Tech is Best to Avoid a Microservices Mess

You need to go back to the fundamentals. One way to look at it is
understanding that microservices are distributed systems, something many
people will have experience with. They should also be familiar with what
another panelist, Oswaldo Hernandez Perez, engineering manager at
Improbable, called the first law of distribution: “If you don’t need to do
it, don’t do it.” So that means focusing on why you are building what you
are building. What are you trying to achieve? This is a fundamental question
that’s applicable to businesses of all sizes. What problem are you trying to
solve, and how will your solution remove friction from its users’ lives?
That’s what people care about. Even if you’re developing a niche app for a
highly technical audience, they are unlikely to care too much about how it
got to them, only that it did and it is fixing a problem for them. If the
only way to achieve that is with microservices, then yes, you should
definitely use them. If there is an alternative, then consider using that.
Do not simply start breaking everything up into microservices just because
that is what everyone is currently talking about. Ultimately, microservices
are an architectural pattern to reduce complexity. It does this, but it also
adds complexity elsewhere. If used in isolation, then you’ll fix your
complexity in one dimension and have it proliferate elsewhere.
The power of value 4.0 for industrial internet of things
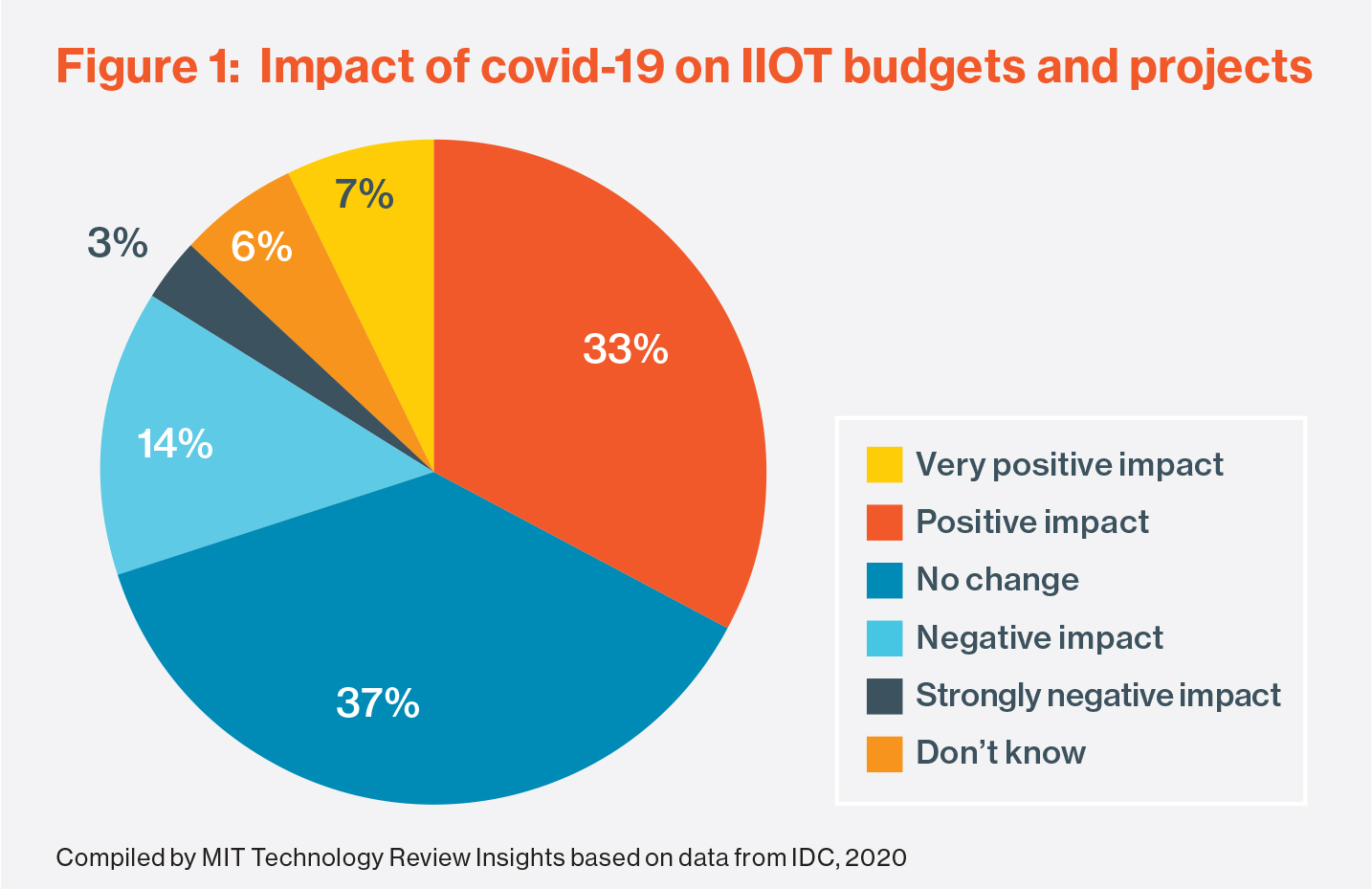
Technological discussions are essential to provide a solution to a defined
improvement area or challenge, but they are meaningful only after there has
been a clearly defined use case with concrete and measurable value
identified and captured within financial reporting systems. This means that
each effort should start with an integrated value design, rather than
technology. It needs to be integrated in the sense that the designed target
value can be directly linked to an outcome —for example, process
improvements enabled by the digital solution that generated a measurable
value impact. Value and solution design need to be one integrated effort. In
consequence, this also implies that use cases need to be defined bottom-up,
by the operators and resources that operate production and thus realize
value add, rather than top-down. Within industrial settings, implementing
industry 4.0 technologies takes more time and effort, compared to
applications in the consumer space, for a variety of reasons. Any industrial
customer today depends on existing brownfield installations to run and
operate their business—these are mostly highly complex and tailored to the
targeted product. Managing this complexity manually would be a Sisyphean
struggle. When industrial companies are integrating digital manufacturing
and supply chain solutions with their customers, they need to continually
adapt the solution stack to customer requirements.
5 Robotic Process Automation (RPA) trends to watch in 2021

Expect a sharper focus on understanding and optimizing processes as a direct
result of the shift from RPA adoption to evaluation and optimization. Plenty
of organizations will realize their initial efforts were stymied by processes
that they didn’t fully understand or that simply weren’t good fits for RPA.
Day predicts that process-focused technologies and practices – such as process
mining – will gain a greater share of attention in the new year. Related terms
and technologies such as process discovery, process intelligence, process
optimization, and process orchestration will similarly become a bigger part of
the RPA vocabulary and toolkit. And as we wrote about recently, we could see a
closer relationship between business process management (BPM) and RPA going
forward. “Most companies are jumping straight into RPA or trying to automate
processes without first adopting process mining, which leads to more strategic
deployment of RPA and a more efficient automation framework overall,” Day
says. “By more closely associating RPA with process mining and process
management, RPA will stand a better chance for success – and organizations
will not adopt automation for automation’s sake, and instead focus on ROI and
higher success rates.”
Enterprise IT Leaders Face Two Paths to AI

There will be two pathways for companies to get AI software," said Andrew
Bartels, VP and principal analyst serving CIO professionals at Forrester
Research. The first movers will continue to build their own for speed to
market and differentiation. It's a more expensive path, but some organizations
will find value in pursuing it. Meanwhile, other organizations in the future
will take another pathway. "The second pathway will be to wait for existing
vendors to add the relevant functionality into existing products," Bartels
said. "We think over time that will be the more dominant pathway." ... Bartels
offers a simple model for assessing the maturity of your vendor's AI and
whether it is the right fit for the task you have. He uses the metaphor of
K-12 grade school students. If a vendor says they are adding AI functionality
to their roadmap, that is a pre-kindergarten level. If they are actually
developing the technology, they are in kindergarten. If they have it in beta
with clients, they are a third grader. If they are in production with multiple
clients for a few years then they are an eighth grader. The scale continues
along the same lines with more advanced work. Bartels said enterprise IT
leaders need to ask themselves: "Is this a task that an eighth grader could
do? Then trust an AI engine to do it. Or, is this a task we would not give to
a human who did not have an equivalent of an 11th grade education?"
Responsible Innovation Starts With Cybersecurity

Recent events heightened the need to instill the cybersecurity culture and
mindset into businesses and local governments. When employees understand how
to monitor, spot, and recover from threats, systems can become more resilient.
Murphy says, "When I talk with folks about cybersecurity, I tell them the most
important thing is to educate your employees or citizens on how they should
behave and the things to watch out for. The second component is to know what's
going on in your world and then be able to respond or recover your
environment. Educating your employees while using AI is key." At this point,
even if companies and local governments have limited resources, there are
still strategies they can take to secure their environment. Murphy says, "If
you don't have the money, at least do things like segment your network. There
are certain design criteria that you can build for a safer environment. There
are best practices that don't require capital investment. At a minimum,
there's good change control and configuration management practices that must
be implemented." Without a foundation of cybersecurity, innovation cannot
progress.
What AI investments should businesses prioritise for Covid-19 recovery?

While there will be a whole host of systems that businesses and individuals
will interact with in the future, they must be intelligent, they need to
involve us, they need to sense and be able take decisions, some on their own.
What this means for businesses is that while the digital presence of systems
and processes will only increase, increasing their intelligence and
continually enhancing them will be crucial. Therefore, we can expect the role
of AI to be far more strategic than ever before, particularly as we think
about emotional intelligence in the future. The beauty of this change will be
greater demand for people and skills. While AI will start making systems
intelligent and reduce demand on maintenance and smaller operations, the next
innovations, the roadmap development, the enhancements, and emotional
intelligence will require more man=power. Up to now AI investment in industry
has been aimed at solving specific business challenges and driving cost
reduction, now businesses really need to invest in creating an enterprise
grade AI stack to responsibly scale AI across the enterprise. Ultimately,
organisations need to focus on improving the end user and customer experience,
using AI to drive hyper-personalisation such as conversational commerce tools.
Enterprise IoT Security Is a Supply Chain Problem
IoT devices and systems represent additional enterprise attack surface — the
same as allowing users to "bring your own device" for mobile devices. These
devices expose the organization to the same types of risk as other devices
deployed on the corporate network. Security flaws in IoT devices can lead to
device takeover and the exposure of sensitive data, and they provide attackers a
foothold in the corporate network that can be used to launch additional attacks.
Additionally, these IoT systems tend to traffic in a lot of sensitive data,
including confidential and proprietary information, and information that has
privacy implications. This data will leave the corporate firewall and be
processed by services hosted by the IoT system provider and places the burden on
the enterprise to understand how these IoT systems affect their risk posture.
Third-party risk must be approached in a structured manner as part of an overall
vendor risk management program. New IoT systems that are going to be deployed on
enterprise networks and process sensitive enterprise information need to be run
through a vetting process, so the organizations understand the change in risk
exposure. This process can share many of the same characteristics of a standard
vendor risk management program but may need to be augmented to address some of
the specific concerns that IoT systems raise.
Quote for the day:
"Appreciation is a wonderful thing: It makes what is excellent in others belong to us as well." -- Voltaire
No comments:
Post a Comment