Hackers hide web skimmer inside a website's CSS files

Places where web skimmers have been found in the past include inside images
such as those used for site logos, favicons, and social media networks;
appended to popular JavaScript libraries like jQuery, Modernizr, and Google
Tag Manager; or hidden inside site widgets like live chat windows. The latest
of these odd places is, believe it or not, CSS files. Standing for cascading
style sheets, CSS files are used inside browsers to load rules for stylizing a
web page's elements with the help of the CSS language. These files usually
contain code describing the colors of various page elements, the size of the
text, padding between various elements, font settings, and more. However, CSS
is not what it was in the early 2000s. Over the past decade, the CSS language
has grown into an incredibly powerful utility that web developers are now
using to create powerful animations with little to no JavaScript. One of the
recent additions to the CSS language was a feature that would allow it to load
and run JavaScript code from within a CSS rule. Willem de Groot, the
founder of Dutch security firm Sanguine Security (SanSec), told ZDNet today
that this CSS feature is now being abused by web skimmer gangs.
The Line Between Physical Security & Cybersecurity Blurs as World Gets More Digital
For manufacturers, the importance of forcing users to change default credentials
before first use has never been higher. The Mirai botnet, one of the most
well-known and successful pieces of malware in history, infected millions of
connected devices across the globe by exploiting common default
username/password combinations. While manufacturers have been aware of the
importance of changing default passwords, we are now seeing mechanisms being put
in place to ensure a device doesn't function until the password is changed.
Going even further, some states, including California, have reinforced that
knowledge with legislation mandating their use. Similarly, integrators must be
able to keep devices protected during and after the installation process,
avoiding the sort of misconfigurations that cyberattackers are known to exploit.
IT departments and users themselves also bear a degree of responsibility when it
comes to securing their devices by installing product updates and patches in a
timely manner. Organizations must ensure that their employees understand the
importance of protecting every device on the network, while also effectively
vetting the security knowledge and capabilities of both their manufacturer and
integrator partners.
5 big and powerful Python web frameworks

At its core, CubicWeb provides basic scaffolding used by every web app: a
“repository” for data connections and storage; a “web engine” for basic HTTP
request/response and CRUD actions; and a schema for modeling data. All of this
is described in Python class definitions. To set up and manage instances of
CubicWeb, you work with a command-line tool similar to the one used for
Django. A built-in templating system lets you programmatically generate HTML
output. You can also use a cube that provides tools for web UIs, such as that
for the Bootstrap HTML framework. Although CubicWeb supports Python 3 (since
version 3.23), it does not appear to use Python 3’s native async
functionality. ... Django has sane and safe defaults that help shield your web
application from attack. When you place a variable in a page template, such as
a string with HTML or JavaScript, the contents are not rendered literally
unless you explicitly designate the instance of the variable as safe. This by
itself eliminates many common cross-site scripting issues. If you want to
perform form validation, you can use everything from simple CSRF protection to
full-blown field-by-field validation mechanisms that return detailed error
feedback.
Myth vs. reality: a practical perspective on quantum computing

Developers and researchers want to ensure they invest in languages and tools
that will adapt to the capabilities of more powerful quantum systems in the
future. Microsoft’s open-source Quantum Intermediate Representation (QIR) and
the Q# programming language provide developers with a flexible foundation that
protects their development investments. QIR is a new Microsoft-developed
intermediate representation for quantum programs that is hardware and language
agnostic, so it can be a common interface between many languages and target
quantum computation platforms. Based on the popular open-source LLVM
intermediate language, QIR is designed to enable the development of a broad
and flexible ecosystem of software tools for quantum development. As quantum
computing capabilities evolve, we expect large-scale quantum applications will
take full advantage of both classical and quantum computing resources working
together. QIR provides full capabilities for describing rich classical
computation fully integrated with quantum computation. It’s a key layer in
achieving a scaled quantum system that can be programmed and controlled for
general algorithms.
A newly-described 'blockchain denial of service' attack could convince miners to stop minin

The attack works by targeting the system’s reward system in a way that
discourages miner participation. Specifically, the attacker publishes a proof
to the blockchain that signals to other miners that the attacker holds a
mining advantage. The researchers found that what they define as “rational”
miners will stop mining if they detect that they are at a disadvantage. “If
the profitability decrease is significant enough so that all miners stop
mining, the attacker can stop mining too,” they write. “The blockchain thus
grinds to a complete halt.” The study authors add: “We find that Bitcoin’s
vulnerability to BDoS increases rapidly as the mining industry matures and
profitability drops.” According to Ittay Eyal, a senior lecturer at
Technion who co-authored the study, BDoS attacks are different from a type of
attack called selfish mining, in which the attacker manipulates the system to
get more than their fair share of rewards. In a BDoS attack, the attacker’s
aim is to take down a proof-of-work cryptocurrency rather than reap
rewards. Eyal said the findings of the study pertain specifically to
Bitcoin, but that’ it’s likely there are similar attacks against Ethereum. The
researchers have not gathered any concrete results on this yet, he said.
Zscaler CEO: Network Security Is Dead. Long Live SASE

The security vendor started as a secure web gateway provider before adding
firewall and zero-trust network access. It then it added out-of-band cloud
access security broker (CASB) capabilities to its platform, all of which
positioned it perfectly to dive into SASE when Garter coined the term last
year. Earlier this year, Zscaler also acquired Edgewise Networks to add that
company’s zero-trust networking and application microsegmentation technologies
to its platform, which also give it a SASE boost. SASE, according to Gartner,
consolidates networking and security capabilities into an edge cloud-delivered
service. While Zscaler arguably provides a best-of-breed SASE security stack,
it doesn’t own a networking piece. Instead, Zscaler partners with all of the
SD-WAN vendors including VMware, and, in fact, VMware CEO Pat Gelsinger joined
Chaudhry for a video appearance during the virtual keynote to tout the two
companies’ SASE partnership. When asked if Zscaler plans to continue
partnering with SD-WAN vendors to provide a full SASE architecture or acquire
SD-WAN to provide its own networking capabilities, Chaudhry said there’s no
reason for Zscaler to provide SD-WAN. “We believe that the notion that SASE
means networking and security coming together is a misinterpretation of it,”
the exec said.
Soft PLCs: The industrial innovator’s dilemma
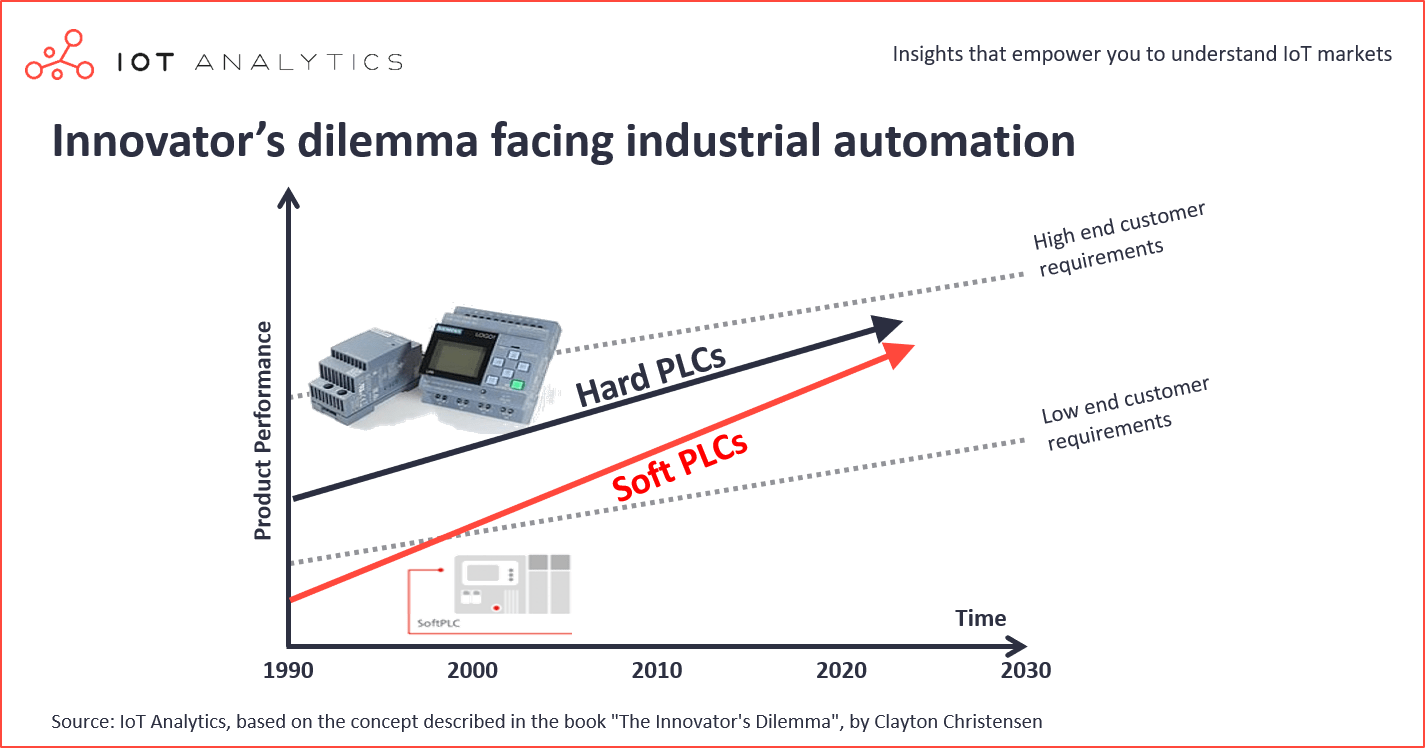
Industrial control has come a long way from being bulky, maintenance heavy
relay-based systems in the 1960s to today’s high-speed processor-based
programmable logic controllers (PLCs). What began as a basic attempt to
replace relay control quickly transformed as the foundation of modern
industrial control and automation. The introduction of Windows in 1985
spawned the first wave of soft PLCs which manifested themselves in PC-based
control systems. The engineering community quickly saw the benefits of
combining PLC control and HMI in one box – the PC. Several Windows-based
control systems emerged in the 1990’s (e.g. ASAP, Think and Do, Steeplechase
Software and Wonderware), but none managed to gain sustained traction in the
marketplace. “Blue screens of death” raised questions about the reliability of
these systems, and the lack of virtualization / containerization technologies
made it difficult to efficiently run multiple workloads (e.g. HMI and control)
on a single box. Fast forward to 2020, and the value proposition of PC-based
control is much stronger than it was in the 90’s as the maturation of Linux
operating systems, virtualization technologies and low-cost edge computing
hardware have addressed many of the early issues that plagued the first wave
of PC-based control systems.
As Ransomware Booms, Are Cyber Insurers Getting Cold Feet?

Constant innovation is one factor, as ransomware operations have continued to
refine their business strategies, including exfiltrating and leaking stolen
data, using affiliate programs to boost their reach, and even hiring call
centers to run boiler-room operations to pressure victims to pay. In Q3, the
average ransom payment - when a victim paid - was $233,817, which was an
increase of 31% from the previous quarter, reports ransomware incident
response firm Coveware. Gangs' successes carry an obvious cost for victims who
pay; their criminal profits put a drain on someone else's budget. When victims
do pay a ransom, some will remit it entirely from their own coffers. But many
organizations now carry cyber insurance with ransomware or extortion
protection. As ransomware payouts have risen, however, insurance providers'
profits have been taking a dive. Accordingly, some insurers now appear to be
"attempting to shelter themselves from these losses, either by excluding
extortion events from standard cyber insurance coverage or by introducing
onerous new conditions on policyholders," the Seriously Risky Business
newsletter reported last week. Experts across the security and insurance
industries say that, with ransomware racking up record profits, there's little
chance of it abating anytime soon.
Agile is changing software development. Here's how one company made the switch

At Capital One, Soule has helped the bank move away from legacy ways of
working and towards an investment in software engineering capability and Agile
methodologies. It's a long-term rebalancing act that has seen the company
adopt close-knit development teams with clear and concise deliverables.
"Changing little and often is now a reality for this organisation," he says.
"That change is the mark of the difference between large, monolithic Waterfall
delivery of implementations to open-source software, delivered incrementally
in feature form on existing products. We've converted most of our IT spending
on assets into people. That's been a stellar story." Back in 2014, there were
30 engineers – most of them infrastructure engineers – working for Capital One
Europe. Today, there's as many as 300 engineers in the UK business alone. The
vast majority are software engineers, compared to just a few six years ago.
Soule says this transformation to Agile working has had a "game-changing"
impact on the delivery of applications to customers. In the old
Waterfall-based way of working, systems and services would take years of
effort and millions of pounds to create. These big projects, says Soule,
consumed resources and meant other interesting innovations fell by the
wayside: "Often other things didn't get done because all the focus of the
development engine was on that one big thing."
Why DSLs? A Collection of Anecdotes
Domain-specific languages rely on a different approach. They allow the domain
expert to specify the behavior of the software directly. The transformation
from unstructured thought to executable specification happens in their brains.
The executable specifications - or models - created this way are then
automatically transformed into "real" source code by machinery developed by
software engineers. Does this really work? It does under certain conditions.
In particular, the language must be suitable for use by non-programmers. The
primitives in the language should not be generic to "computation" - such as
variables, conditions, loops, functions, monads or classes - but instead be
specific to the domain, and therefore meaningful to the user: decision table,
treatment step, tax rule or satellite telemetry message definition. The syntax
should build on existing notations and conventions used in the domain -
tables, symbols, diagrams and text - and not just consist of magenta-colored
keywords and curly braces. DSLs are also usually less flexible in the sense
that users can only compose new abstractions in very limited ways; while this
would be a problem for general-purpose languages, it is a plus for DSLs
because it ensures that programs are less complicated and easier for tools to
analyze and provide IDE support for.
Quote for the day:
"Successful leadership requires positive self-regard fused with optimism about a desired outcome." -- Warren Bennis
No comments:
Post a Comment