Different Normalization Layers in Deep Learning
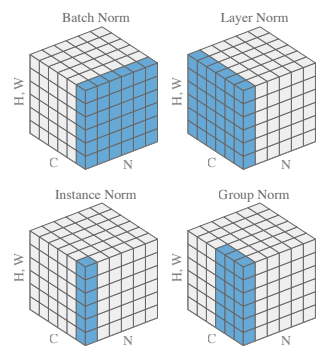
Deep learning certainly involves training carefully designed deep neural
networks and various design decisions impact the training regime of these deep
networks. Some of these design decisions include Type of network layer to use
such as convolution layer, linear layer, recurrent layer, etc. in the network,
and how many layers deep should our network be? What kind of normalization
layer we should use if at all? What should be the correct loss function
to optimize for? Majorly these design decisions depend upon the
underlying task we are trying to solve and require a deeper understanding of
the different options we have at hand. In this post, I will focus on the
second point “different Normalization Layers in Deep Learning”. Broadly I
would cover the following methods. ... One important thing to note is, in
practice the normalization layers are used in between the Linear/Conv/RNN
layer and the ReLU non-linearity(or hyperbolic tangent etc) so that when the
activations reach the Non-linear activation function, the activations are
equally centered around zero. This would potentially avoid the dead neurons
which never get activated due to wrong random initialization and hence can
improve training.
Financial Fraud Through the Lens of Cybersecurity
Certain web sites require the user to enter a security question and an answer
for it. The list of questions is standard, and one of them usually is – “What
is your mother’s maiden name?”. This form of knowledge-based authentication is
one of the most important aspects of conducting successful transactions online
for high-value products, as most banks ask this as a security question for
making any changes to the account. ... Credit card dumps are used by
fraudsters to capture valuable card data such as the card number and
expiration date. These can be obtained in a number of ways. The most popular
method nowadays is the “skimming”, a process in which an illegal card reader
is used to copy the data from a Credit Card. Other methods include hacking
into a retailer’s network or when unknown to the retailer, a malware-infected
point-of-sale device sends information to cybercriminals.... Bank
Identification Number is the first six numbers that appear on a Credit Card,
and it uniquely identifies the institution issuing the card. The BIN is key in
the process of matching transactions to the issuer of the charge card. This
numbering system also applies to charge cards, gift cards, prepaid cards and
even electronic benefit cards.
New ransomware campaign exploits weak MySQL credentials to lock thousands of databases

Interestingly, the operators do not appear to be utilizing any actual
ransomware payload in their attacks. It begins by brute forcing weak password
protocols for MySQL databases, followed by collection of data on existing
tables and users before installing a hidden backdoor on the way out to
facilitate future break-ins. “By the end of execution, the victim’s data is
gone – it’s archived in a zipped file which is sent to the attackers’ servers
and then deleted from the database,” write authors Ophir Harpaz and Omri
Marom. Guardicore Labs also spotted two distinct versions of this campaign.
The first, between January and November 2020, composed roughly two-thirds of
observed attacks and involved leaving a ransom note with a Bitcoin wallet
address, a ransom demand, an email address for technical support and a 10-day
deadline for payment. However, in leaving those breadcrumbs, the operators
made it possible for researchers to poke around their Bitcoin wallet and
examine how much money had been transferred to it. Ultimately, they traced
nearly $25,000 in payments from four separate IP addresses.
Using OPA for multicloud policy and process portability

Multicloud also presents a second alluring possibility, an extension of that
original cloud-native logic: the ability to abstract cloud computing
architectures so they can port automatically and seamlessly (if not just
quickly) between cloud providers to maximize performance, availability, and
cost savings—or at least maintain uptime if one cloud vendor happens to goes
down. Cloud-agnostic platforms like Kubernetes, which run the same in any
environment—whether that’s AWS, GCP, Azure, private cloud, or wherever—offer a
tantalizing glimpse of how companies could achieve this kind of multicloud
portability. But while elegant in theory, multicloud portability is
complicated in practice. Dependencies like vendor-specific features, APIs, and
difficult-to-port data lakes make true application and workload portability a
complicated journey. In practice, multicloud portability only really works—and
works well—when organizations achieve consistency across cloud environments.
For that, businesses need a level of policy abstraction that works across said
vendors, clouds, APIs, and so on—enabling them to easily port skills, people,
and processes across the cloud-native business. While individual applications
may not always port seamlessly between clouds, the organization’s overall
approach should.
How COVID-19 impacted the relationship between the enterprise and its employees

Most organizations understood the innate value of employee well-being, which
is defined in the report by a five-point system of indicators, all of these at
work: Feeling calm, feeling energized, rarely feeling overwhelmed by
responsibilities, feeling positive about yourself, and having trusting
relationships Employee well-being remains critical as organizations continue
to recover from this time of disruption, said Lauren Rice, XM scientist,
Qualtrics, also in the report. "Whether it's providing flexibility to
employees as they juggle work and personal responsibilities, supporting
employees as they attend to any family health concerns, or just taking the
time to listen to employees' concerns, it's a necessity at this time for
organizations to care and support employees' well-being. When organizations
care for their employees, the employees will in turn show care and dedication
to their work and the organization." ... There's a great disparity between
employers and their staff, according to the report, regarding acting on
feedback: 92% of employees believe it's important the company listen to
feedback, but admit that only 7% of employees say their company does so.
Big data is just a crutch for unimaginative marketers to lean on

The first problem seems to be the quality and the processes used in data
storage. We like to celebrate how much we have, but data normally comes from
separate systems, measured in different ways, stored in different places. Most
CTOs will embarrassingly admit they have too much data these days, not too
little. They find the data dirty, contradictory and in systems that won’t
mesh. If companies know that much about everything, why are we sent credit
card offers for credit cards we already have? Why is my bank offering me cheap
loans and pitching me funds to invest in at the same time? ... Big data has
the temptation of making the complex seem simple. It may think I like certain
movies, when in fact I like certain movies at certain times or in certain
situations. The crap I watch after a beer on a plane ruins any algorithm’s
chances, let alone an Airbnb guest using my TV. We endlessly refer to
“data-driven” insights when I’ve only ever seen facts, not insights, from
data. Insights are found by observation and, where needed, supported by data.
No spreadsheet ever revealed anything as beautiful and transformational as an
insight.
Remote working is starting to show tears. But going back to office isn’t only solution

The remote work experiment seemed to offer an initial boost in productivity.
But sustaining such productivity has been difficult, in part because the home
wasn’t designed for work and the consequences of “Zoom” fatigue are real.
Indeed, emerging evidence suggests burnout is plaguing remote workers across
the board. Yet managing employee burnout is particularly difficult during a
pandemic, when people are asked to mostly isolate at home, away from
colleagues whose mere presence can often ease work-related stress. ... What’s
worse, corporate policies meant to monitor and control employee behavior –
whether while they work remotely or as means to make the office safer – risk
eroding worker trust and undermining cultural norms. And the impact of these
policies will likely endure long after the crisis subsides ... A third major
cost of this sustained remote period of work is the lack of collaboration and
its disruptive impact on innovation. Sure, some collaborations and idea
generation can take place via Zoom meetings, but innovation still largely
happens in physical spaces: at lab benches, alongside a 3D printer or in
unintended office interactions that spark interdisciplinary collaborations.
Effective Use of Blockchain in the Legal Sector – A near future or a distant possibility?

Times changed and so did the use of technology in the legal sector. Although,
there is no doubt that technology in the legal sector has improved efficiency,
reduced errors and has further demystified the operations of the court system,
but the growth has been slow. Perhaps, because the traditional legal system is
a relic of the past, which while adjusting itself to the modern world
technology is still, metaphysically, attached to its ancient and archaic
roots. The present-day legal system, which has been slow in keeping up with
the changes in technology, has for the very first time attempted to digitise
itself overnight during these unprecedented pandemic times. Virtual court
hearings and paperless filings, even with certain limitations, has been
welcomed by the legal sector. The credit for the digitisation of courts should
be given to the Supreme Court’s e-committee headed by Hon’ble Justice DY
Chandrachud. The e-committee by swiftly implementing a contingency plan has
enabled our courts to continue operating even during this pandemic thus
helping thousands to get justice. However, the growth should not stop
here and this opportunity should also be fully utilised to explore other
technological innovations which can be imbibed and integrated into the
prevalent legal tech.
Researchers warn of security vulnerabilities in these widely used point-of-sale terminals

Attackers could gain access to the devices to manipulate them in one of two
ways. Either they're able to physically gain access to the PoS terminal, or
they're able to remotely gain access via the internet and then execute
arbitrary code, buffer overflows and other common techniques which can provide
attackers with an escalation of privileges and the ability to control the
device – and see and steal the data that goes through it. Remote access is
possible if an attacker to gains access to the network via phishing or another
attack and then move freely around the network to the PoS terminal.
Ultimately, the PoS machine is a computer and if it's connected to the network
and the internet, then attackers can attempt to gain access to and manipulate
it like any other insecure machine. The way the PoS terminal communicates with
the rest of the network means attackers could access unencrypted data card
data including Track2 and PIN information, providing all the necessary
information required to steal and clone payment cards. In order to
protect against attacks exploiting PoS vulnerabilities, it's recommended that
retailers using the devices ensure they're patched and up to date and they
should avoid using default passwords where possible.
The Right Data Governance for Your Organization’s Culture

The first step is to observe. Places to look for indications of core culture are
in the mission statement, in vision documents, and posters put up by the Human
Resources department. Since culture is driven at the leadership level, observe
what leadership values and rewards. In a more formal process, surveys of staff
and leadership, past and present, can provide knowledge useful for determining
the company culture. Recognize that culture clash is a possibility with mergers
and acquisitions. In those situations, “Make sure that you have those
conversations at your executive level because you can’t really drive that
through your Data Governance programs,” Levins said. ... Although most companies
have a predominant core culture, and there are often subcultures within that
culture, Levins said, but for the purpose of the presentation, they would be
focusing on the core culture for the organization as a whole. Each culture has
strengths and pitfalls. Elder noted, “The things that we love about our partner
also drive us crazy sometimes.” ... Cultivative culture is focused on people and
possibility, said Elder. “How can we make the future better? How can we make
people better?”
Quote for the day:
"Added pressure and responsibility should not change one's leadership style, it should merely expose that which already exists." -- Mark W. Boyer
No comments:
Post a Comment