Building Trust with Centralized Data Access

As businesses continue to find ways to use, monetize, and aggregate data, they
need to effectively share their data in a way that’s more secure than an email
and more scalable than sending a thumb drive by courier. They also need
methods to use data more efficiently. In particular, businesses that are
exploring ML and AI solutions need to look to data trusts to provide these
solutions at scale, because the tedious overhead of data prep required to fuel
these solutions can derail projects entirely. Data trusts are also a logical
next step for any government or government institution looking to achieve
greater transparency and drive innovation. After all, a data trust is
primarily a vehicle for securely collecting and disseminating public, private,
and proprietary information. Government data systems are complex; data trusts
are a useful tool that can be used to synthesize, standardize, and audit data
that is generated or used internally. The key difference between the value
that data trusts bring for businesses is to increase data use within the
organization, whereas for governments it is primarily used to audit data
assets and better understand internal data environments.
Five ways COVID-19 will change cybersecurity

Next year, CISOs will have to grapple with the consequences of the decisions
they made (or were forced to make) in 2020. One of their first orders of
business will be to “un-cut” the corners they took in the spring to stand up
remote work capabilities. We’re already starting to see this trend play
out, with zero trust – an emerging security mindset that treats everything
as hostile, including the network, host, applications, and services –
gaining in traction: in November, 60 percent of organizations
reported that they were accelerating zero trust projects. That’s due in no
small part to CISOs and CSOs retrenching and taking a more deliberate
approach to ensuring operational security. The security leaders who
help their organizations successfully navigate the zero trust journey will
recognize that a zero trust mindset has to incorporate a holistic suite of
capabilities including, but not limited to: strong multifactor
authentication, comprehensive identity governance and lifecycle, and
effective threat detection and response fueled through comprehensive
visibility across all key digital assets. To address the increasing
digital complexity induced by digital transformation, effective security
leaders will embrace the notion of extended detection and response (XDR),
striving for unified visibility across their networks, endpoints, cloud
assets, and digital identities.
Stop the Insanity: Eliminating Data Infrastructure Sprawl
There are so many projects going on that navigating the tangle is pretty
difficult. In the past, you generally had a few commercial options. Now, there
might be tens or hundreds of options to choose from. You end up having to
narrow it down to a few choices based on limited time and information.
Database technology in particular has seen this problem mushroom in recent
years. It used to be you had a small number of choices: Oracle, Microsoft SQL
Server, and IBM DB2 as the proprietary choices, or MySQL if you wanted a free
and open source choice. Then, two trends matured: NoSQL, and the rise of open
source as a model. The number of choices grew tremendously. In addition, as
cloud vendors are trying to differentiate, they have each added both NoSQL
databases and their own flavors of relational (or SQL) databases. AWS has more
than 10 database offerings; Azure and GCP each have more than five flavors.
... If you’re building a new solution, you have to decide what data
architecture you need. Even if you assume the requirements are clear and fixed
– which is almost never the case – navigating the bewildering set of choices
as to which database to use is pretty hard. You need to assess requirements
across a broad set of dimensions – such as functionality, performance,
security, and support options – to determine which ones meet your needs.
Agility for business — championing customer expectations in 2021

2020 has shown that remote working isn’t just possible for many traditionally
office-based industries such as customer service, but also sometimes
preferable. It has given many employees a better way to structure their
workday and work/life balance while ensuring they stay protected. In 2021,
flexible working models will continue to become more prominent. Businesses and
their customer experience teams will therefore need to dynamically manage
employees and anticipate different working scenarios — remote work, in the
office, off-shore, on-shore, in-house or outsourced — and enable them to
deliver service across multiple channels. This means managers must be equipped
with the tools to address an agile workforce divergence. The workforce must be
effectively and efficiently managed as agents work across any channel and from
any location. Also, as digital tools continue to increase in prominence, a
robotic workforce will need to be managed together with customer service
employees as one integrated workforce. By embracing and adapting to these new
working conditions, businesses will be better placed to maintain customer
service levels whatever the circumstance.
FireEye: SolarWinds Hack 'Genuinely Impacted' 50 Victims
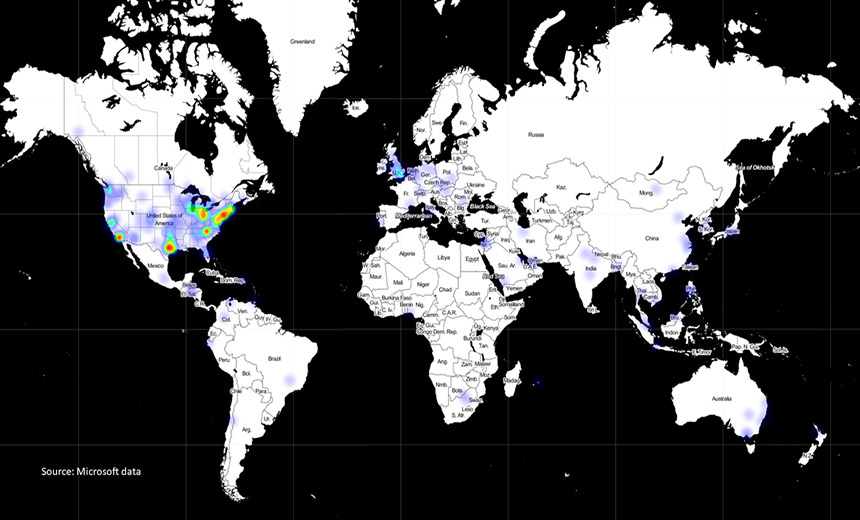
Microsoft on Thursday disclosed that it too was hacked, but says there are no
signs that its software was either Trojanized or used to infect anyone else.
On Friday, Palo Alto, California-based VMware said it was also a victim of the
supply chain attack. "While we have identified limited instances of the
vulnerable SolarWinds Orion software in our own internal environment, our own
internal investigation has not revealed any indication of exploitation,"
VMware said in a statement. FireEye's Mandia said in his Sunday interview that
the SolarWinds Orion code was altered in October 2019, but that the backdoor
wasn't added until March. An unnamed source with knowledge of the
investigation told Yahoo News that last October's effort appeared to be a "dry
run," adding that the attackers' caution suggested that they were "a little
bit more disciplined and deliberate" than the average attacker. Investigators
say the attack appears to have been launched by Russia as part of a cyber
espionage operation, and potentially by Moscow's SVR foreign intelligence
service. U.S. Secretary of State Mike Pompeo on Friday said in a radio
interview that "we can say pretty clearly that it was the Russians." On
Saturday, President Donald Trump attempted to downplay Pompeo's remarks.
Why Quantum Computing's Future Lies in the Cloud
The current generation of Noisy Intermediate-Scale Quantum (NISQ) computers
are large, temperamental, and complicated to maintain, said Konstantinos
Karagiannis, an associate director at business, finance, and technology
consulting firm Protiviti. They are also very expensive and likely to be
rapidly outdated, he added. Karagiannis, like most other sector experts,
believes that the enterprise path to quantum computing access is more likely
to go through the cloud than the data center. "Providing cloud access to
quantum computers ... allows researchers and companies worldwide to share
these systems and contribute to both academia and industry," he said. "As more
powerful systems come online, the cloud approach is likely to become a
significant revenue source [for service providers], with users paying for
access to NISQ systems that can solve real-world problems." The limited
lifespans of rapidly advancing quantum computing systems also favors cloud
providers. "Developers are still early along in hardware development, so
there's little incentive for a user to buy hardware that will soon be made
obsolete," explained Lewie Roberts, a senior researcher at Lux Research. "This
is also part of why so many large cloud players ... are researching quantum
computing," Roberts noted. "It would nicely augment their existing cloud
services," he added.
Microsoft Finds Backdoor; CISA Warns of New Attack Vectors

The hacking campaign involved slipping malicious backdoors into software
updates for SolarWinds' popular network management software called Orion. Once
those updates were installed by organizations, the attackers had free-ranging
access to networks and could install other malware and access data, such as
email accounts. Orion has powerful, administrative access, says John Bambenek,
chief forensic examiner and president of Bambenek Consulting and an incident
handler at the SANS Institute."Owning SolarWinds is effectively owning the
CIO," Bambenek says. "You've got the infrastructure. You don't need a special
tool to sit there and change passwords or create accounts or spin up new VMs
[virtual machines]. It's all built in, and you've got full access." As many as
18,000 organizations downloaded the infected updates, SolarWinds has said. But
experts believe the hacking group likely only deeply penetrated a few dozen
organizations, with many in the U.S. government sphere. The U.S. Cybersecurity
and Infrastructure Security Agency warned Thursday, however, that the
SolarWinds compromise "is not the only initial infection vector this actor
leveraged."
Demystifying Master Data Management

For master data to fuel MDM, it must be organized into relevant business
schemas. Reference data, imported from multiple customers, needs to be made
relevant to work activities, (e.g. automate account processing, from the example
above). Humans intervene with this reference data and add new data or transform
it into an information product (e.g. adding transactions to invoices, matching
bills). The data transformation throughout the company needs to work within the
larger business context, including enhancing the reference data. When customers
view the final information (e.g. that bills have been paid), the reference data
used throughout the production process needs to be made available. MDM provides
the framework needed to move and use raw master data. Since MDM involves a
complete 360-degree business view, all company departments contribute to
conception of the master data context. What may be relevant information to one
business department may not be to another and may not relate to the master data
context. Listing what comprises master data, including reference data, and the
systems that generate master data, gives a picture toward integrating master
data between other systems, throughout the entire business. But this is only a
start. Providing cross-organizational commitment to the master data’s relevancy
and guidance to its contextual structure becomes critical. A Data Governance
program fills this need.
Hackers Use Mobile Emulators to Steal Millions

"This mobile fraud operation managed to automate the process of accessing
accounts, initiating a transaction, receiving and stealing a second factor -
SMS in this case - and in many cases using those codes to complete illicit
transactions," according to IBM. "The data sources, scripts and customized
applications the gang created flowed in one automated process, which
provided speed that allowed them to rob millions of dollars from each
victimized bank within a matter of days." ... They then connected to the
account through a matching VPN service, according to the report. The
attackers also could bypass protections, such as multifactor authentication,
because they already had access to the victims' SMS messages. "A key
takeaway here is that mobile malware has graduated to a fully automated
process that should raise concern across the global financial services
sector," Kesem says. "We have never seen a comparable operation in the past,
and the same gang is likely bound to repeat these attacks. But they are also
already being offered 'as-a-service' via underground venues to other
cybercriminals. We also suspect that these scaled, sporadic attacks are
going to become a more common way cybercriminals target banks and their
customers through the mobile banking channel in 2021."
How artificial intelligence can drive your climate change strategy

From a business perspective, there is a strong connection between
sustainability and business benefits, with nearly 80% of executives pointing
to an increase in customer loyalty as a key benefit from sustainability
initiatives. Over two thirds (69%) pointed to an increase in brand value.
The impact of sustainability credentials on brand value and sales is
supported by our consumer research: if consumers perceive that the brands
they are buying from are not environmentally sustainable or socially
responsible, 70% tell their friends and family about the experience and urge
them not to interact with the organisation. The research found that 68% of
the organisations also cited improvement in environmental, social and
governance (ESG) ratings of their organisation driven by sustainability
initiatives, with nearly 63% of organisations saying that sustainability
initiatives have helped boost revenues. Another high-impact industry which
we are seeing adapt to the new world order is the automotive sector.
Automotive and mobility companies worldwide are facing increasing pressure
from both consumers and government regulators to prioritise their
sustainability efforts. We’re seeing a fundamental potential for a shift in
approach as consumers adopt new, greener and more flexible approaches to
getting from A to B.
Quote for the day:
"I say luck is when an opportunity comes along and you're prepared for it." -- Denzel Washington
No comments:
Post a Comment