5G and the sustainable future: a look to 2025
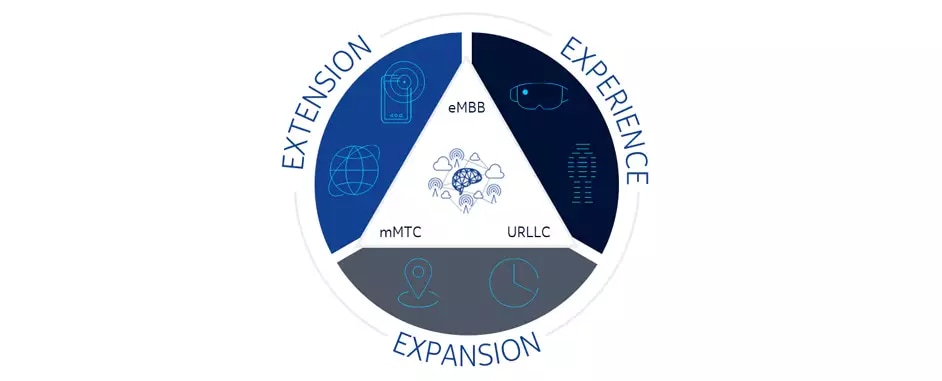
5G could boost economic resilience by providing a reliable second source of
precise location and timing information, not only assisting global navigation
satellite systems (GNSS) but complementing them. GNSS only work in “open sky”
environments — they can’t provide information in “sheltered” settings such as
tunnels or buildings. 5G delivers position and timing information that is just
as accurate as GNSS but can do so while providing unbroken indoor and outdoor
coverage. Broadband has become essential to our social lives and the world’s
economies (both national and local), but there are still many “white spots”
where no coverage exists. This digital divide must be addressed if more people
are to access the economic opportunities and benefits that mobile connectivity
provides. As future economic growth will depend less on basic connectivity and
more on advanced service profiles, the harmful effects of these white spots
will only become more acute. White spots in farmland hinder modern
agricultural water management. An estimated 42 percent of the world’s
accessible fresh water is lost through leaky irrigation systems, inefficient
application methods and growing crops that are too “thirsty” for their
environment.
SSO and MFA Are Only Half Your Identity Governance Strategy
The time employees spend waiting for access approval is paid time when they are
not working. As mentioned, the time spent by IT staff entering or resetting
passwords adds up. It's an unnecessary and costly allocation of resources. The
crux of the problem is not only understanding which roles need access to which
application assets but determining what is the right level of access. The faster
this can be achieved with less human intervention, the greater the efficiency
and cost-saving. New automated solutions that harness machine learning hold
promise to help IT and security teams with smart recommendations about where to
direct their efforts. Prioritization is essential when managing thousands or
tens of thousands of identities. Lost in the sea of identities, it is easy for
organizations to lose track of which permissions they have granted. This can
lead to permission sprawl and unnecessary exposure. However, automated tracking
of users, their roles, and the permissions granted to them can dramatically
reduce the risk of unused entitlements that attackers can exploit to gain access
to valuable assets. Permission management has a lot of catching up to reach the
robustness and adoption of SSO-related tools.
Microservice Architecture and its 10 Most Important Design Patterns
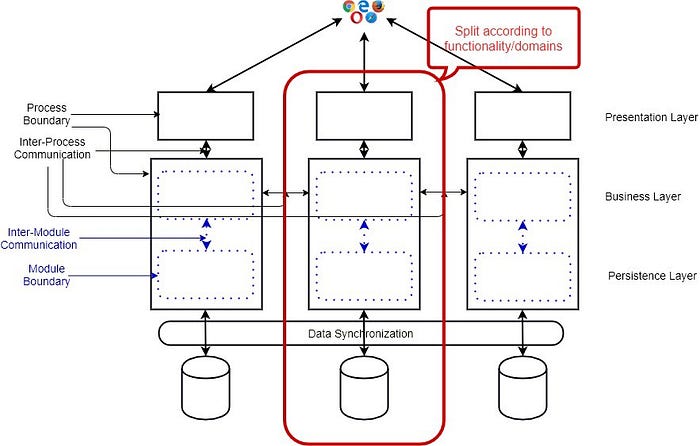
Microservice Architecture is about splitting a large, complex systems
vertically (per functional or business requirements) into smaller sub-systems
which are processes (hence independently deployable) and these sub-systems
communicates with each other via lightweight, language-agnostic network calls
either synchronous (e.g. REST, gRPC) or asynchronous (via Messaging) way. ...
In a Microservice Architecture, especially with Database per Microservice, the
Microservices need to exchange data. For resilient, highly scalable, and
fault-tolerant systems, they should communicate asynchronously by exchanging
Events. In such a case, you may want to have Atomic operations, e.g., update
the Database and send the message. If you have SQL databases and want to have
distributed transactions for a high volume of data, you cannot use the
two-phase locking (2PL) as it does not scale. If you use NoSQL Databases and
want to have a distributed transaction, you cannot use 2PL as many NoSQL
databases do not support two-phase locking. In such scenarios, use Event based
Architecture with Event Sourcing. In traditional databases, the Business
Entity with the current “state” is directly stored. In Event Sourcing, any
state-changing event or other significant events are stored instead of the
entities.
Researchers develop tool that automates device programming in the IoT
A new solution is now on the table, seeking to standardize the programming of
event-driven architectures: the AsyncAPI specification. This specification
allows users to define all the relevant information needed to design and run IoT
devices in these environments. However, AsyncAPI is still in the early stages of
development and therefore the tools that support it remain in short supply.
Despite this, the researchers have developed a tool based on this new proposal
that allows users to automate the creation of messages in the appropriate
format, as well as the sending and receiving of these messages. Abel Gómez said:
“Much of the work that goes into implementing a program for an IoT device
involves creating messages in the format that subscribers to the channel expect
and also “translating” messages from other devices in order to process the
information. A large amount of code must therefore be programmed and, when done
manually, this can be a source of errors.” The researcher continued: “By
adopting this new tool, we can significantly shorten the amount of time needed
to develop and launch programs, which favours interoperability, improves code
quality and in turn limits the number of errors in the software development life
cycle.
Covid-19 sparks boom in Middle East digital payments sector

“The biggest opportunities lie in getting everyone in the region into the
financial system,” said Dannish, adding that the advent of open banking will
allow application programming interfaces (APIs) to transform regional payment
systems. “APIs enable innovation and allow businesses to perform in a better
way,” he said. “There is so much growth still to be had in this market. The
barriers to entry have been lowered since the pandemic.” However, Yusuf noted
that fragmentation remains a major barrier to growth for the digital payments
sector. “The region is split in terms of payment methods, policy and
regulation, infrastructure and consumer preference,” he said. “There is also a
generally fragmented landscape in terms of payments partners. Merchants often
have to operate payments strategy at a granular level.” Yusuf added that cash
as payment remains stubbornly popular in the Middle East. “Despite the
momentum away from cash, if we look at the region compared to the rest of the
world, it is still cash-centric and digital payments are only on the way to
fulfilling their potential,” he said. “While Covid-19 and deep digital
penetration are fostering change, our report showed that cash has deep-rooted
social and cultural significance in the region, and that won’t be transformed
overnight.”
Building stronger multicloud security: 3 key elements

The typical enterprise IT infrastructure and solutions stack today includes
not only public and private cloud deployments but also an average of 288
different SaaS offerings, according to the 2020 SaaS Trends report from tech
vendor Blissfully. (That’s in addition to legacy technologies in many cases,
too.) These various elements have different security requirements as well as
different levels and types of built-in security capabilities. Different cloud
providers have different tools, they often use different terms for the same
class of tools, and they have differing positions on their security
responsibilities. All this leaves CISOs having to stitch together a cohesive
whole that documents whether the cloud-provided security features are
adequate, whether more security is needed, and where and what additional
security measures are warranted. “Cloud was supposed to make our lives
simpler, and it a lot of ways it does; it provides a lot of benefits. But from
a security perspective it adds a lot of complexity because there’s so much to
do,” says Garrett Bekker... Respondents to the 2020 Cloud Threat Report survey
from Oracle and KPMG cited complexity as significant challenge, with 70% of
respondents saying that too many specialized tools are required to secure
their public cloud footprints and 78% highlighting the need for varying
security policies and procedures between their cloud-resident and on-premises
applications.
6 container concepts you need to understand

This architecture provides agility that is not feasible with VMs. Furthermore,
containers support a more flexible model when it comes to compute and memory
resources, and they allow resource-burst modes so that applications can
consume more resources, when required, within the defined boundaries. In other
words, containers provide scalability and flexibility that you cannot get from
running an application on top of a VM. Containers make it easy to share and
deploy applications on public or private clouds. More importantly, they
provide consistency that helps operations and development teams reduce the
complexity that comes with multi-platform deployment. Containers also enable a
common set of building blocks that can be reused in any stage of development
to recreate identical environments for development, testing, staging, and
production, extending the concept of "write-once, deploy anywhere." Compared
to virtualization, containers make it simpler to achieve flexibility,
consistency, and the ability to deploy applications faster—the main principles
of DevOps. Docker has become synonymous with containers. Docker
revolutionized and popularized containers, even though the technology existed
before Docker.
Concerns Run High as More Details of SolarWinds Hack Emerge
The security vendor has described UNC2452 as a threat actor that it has not
encountered previously. FireEye has released indicators of compromise (IoCs) and
signatures so organizations can detect the threat. But so far it has not
publicly, at least, attributed the attack to any specific nation-state sponsor.
Numerous media reports, however, have pinned the campaign on APT29, or Cozy
Bear, a group thought to be associated with Russia's intelligence apparatus.
Paul Prudhomme, cyber-threat intelligence analyst at IntSights, says his firm
has so far not been able to corroborate or independently verify the claimed
attribution to state-sponsored Russian cyber-espionage groups. "But we do
nonetheless find the claim credible and worthy of further consideration," he
says. The campaign is consistent with what IntSights has observed with
state-sponsored Russian actors, including the targeting of the US government,
the tight operational security, and the generally high level of sophistication
and tradecraft involved. At the same time, "technology supply chain compromises
of this kind are more typical of Chinese cyber-espionage groups than their
Russian counterparts," Prudhomme says.
The state of AI in 2020: Biology and healthcare's AI moment
There's a ton of topics we could pick to dissect from Benaich and Hogarth's
work, such as the use of PyTorch overtaking TensorFlow in research, the boom
in federated learning, the analysis on talent and retainment per geography,
progress (or lack thereof) in autonomous vehicles, AI chips, and AutoML. We
encourage readers to dive into the report to learn more. But we wrap up with
something different. Hogarth mentioned that the speculation phase in AI for
biology and healthcare is starting, with lots of capital flowing. There are
going to be some really amazing companies that come out of it, and we will
start to see a real deployment phase kick in. But it's equally certain, he
went on to add, there are going to be instances that will be revealed to be
total frauds. So, what about AI ethics? Benaich and Hogarth cite work by
pioneers in the field, touching upon issues such as commercial gender
classification, unregulated police facial recognition, the ethics of
algorithms, and regulating robots. For the most part, the report focuses on
facial recognition. Facial recognition is widespread the world over and has
lead to controversy, as well as wrongful arrests. More thoughtful approaches
seem to gather steam, Benaich and Hogarth note.
Security automation: Time for a new playbook
Start by examining the processes and procedures your organization’s security
team already has in place and identify the tasks that consume the majority of
team member’s time. These will be the key use cases where SOAR can provide the
most benefit by applying efficiency, speed and consistency. For example, in many
organizations this might include processes such as looking up asset information
or reviewing additional data points related to a security alert or a reported
phishing email. It could be the process of pulling data on what’s running in
memory on a device and adding that detail to an existing incident management
ticket to assist in an investigative decision. Or it could be isolating hosts or
blocking an IP range on the network in order to stop a threat from spreading.
These are all common use cases that can be effectively automated, but only if
the underlying processes and procedures are mature and well-defined. Different
categories of automation require different levels of maturity in the underlying
processes. If you plan to introduce any type of automated response – such as
automated threat containment – you must be absolutely certain that the
underlying processes are mature, or it could have a greater than intended impact
the availability of systems and people.
Quote for the day:
"People with good intentions make promises, but people with good character keep them." -- Joubert Botha
No comments:
Post a Comment