Blockchain for Master Data Management

Blockchain allows visibility and traceability of the inventories of the needed
supplies. Enterprises can trace and track the documentation and financial
transaction. Compared to traditional manual and error-prone approaches, the
shared masted information becomes much more accessible. The digitally extended
enterprise can use all parts, products, suppliers, warehouses, inventory,
documentation, tracing, and financial transaction masters stored on the
Blockchain to function as an efficient and optimized pipeline. Supply Chains
leveraging Blockchain master data and information are applicable in all
industries, and there are various innovative initiatives, projects, and
solutions that have demonstrated the compelling value proposition for
Blockchain for Supply Chain. ... It gets even more exciting and compelling
when the supply chain crosses international borders and involves various
country-specific logistical regulatory and financial documents that need to be
processed. The IBM-Maersk cross-border shipping Blockchain solution is a
compelling text-book example of Blockchain for Supply Chain master data.
Maersk had done a study in 2014 tracing roses and avocadoes from Kenya to the
Netherlands. The study identified several inefficiencies.
Working Remotely: Good Practices and Useful Resources
While remote working may appear straightforward, there are common issues that
come up as you shift to this way of working that may not be apparent, even if
you’ve done regular remote days as part of your working week. For people
thrust into this suddenly, the impact of the change will be significant. This
is not “normal” remote working, in which people have time to plan how they
will set up their space, find equipment and furniture which suits their
location and lifestyle and make a considered transition to working remotely.
This is responding to change in the most immediate way, it probably involves
sharing the working space with a spouse, partner, parents or flatmate and
quite likely children who are simultaneously trying to figure out how
remote-schooling works. One of the most important pieces of advice which has
been repeated around the world as societies respond to the need for people to
be isolated is “be kind” - be kind to yourself, be kind to your colleagues, be
kind to your staff, be kind to your manager, be kind to the people sharing
your space.
Phishing attacks and ransomware are the most challenging threats for many organizations

Poor asset and inventory management can prove problematic if an organization
is hit by a cyberattack or learns of a serious vulnerability. Only 58% of
those surveyed said they can determine within 24 hours every vulnerable asset
in their organization following a critical exploit. More than 40% said it
would take them 24 hours or longer to identify each vulnerable system.
Granting access privileges to users is also a challenge. Too little, and
employees have difficulty doing their jobs. Too much, and you open the door to
security risks. In this case, though, IT teams tend to lean toward too much.
Almost half (48%) admitted to giving at least some users more access
privileges than required. Finally, trying to explain the need for certain
security methods and projects to the board or senior management can be an
onerous task faced by high-level IT personnel. In this case, 52% of the
respondents said they had a good discussion and got their point across, though
the outcome was not as expected. Only 13% said that these types of
presentations go over well and that the board members understand the security
situation.
New look for Microsoft Office and Microsoft 365 will tackle work-life distractions on desktop and mobile

In recent years, Microsoft has simplified the Office 'ribbon' — the strip at
the top of Office apps with tools, buttons and shortcuts — as well as
introduced dark mode and brought its Fluent Design scheme to bear on these
apps in mobile and desktop. "The next wave of Microsoft 365 UX changes
will go even further by fading brand colors from app headers and exploring
adaptive commanding. A flexible ribbon that progressively discloses
contextually relevant commands at the right time just where you need them,"
explains Friedman. By flexible, Friedman told The Verge that Microsoft
means Office will give users a simplified toolbar that moves around the screen
to where users find it most helpful, while commands are surfaced when
contextually relevant. Friedman notes that the ribbon interface
originated on the desktop but that Microsoft is trying to reimagine what
intent and context-aware commanding looks like when work is carried out across
multiple devices. "Having your ribbon commands follow your actions and
being context aware will reduce cognitive load and increase focus on the task
at hand, whether you're on your phone in the subway or your tablet on the sofa
or your desktop," he told The Verge.
AI is accelerating the move to a touchless world

"As a result of COVID-19, customers are increasingly looking for digital,
no-touch connections with organizations, given the constraints and concerns
about physical interactions in a new-normal, socially distanced world,"
Capgemini said. "Our research shows that even when lockdowns are lifted,
customers across the world say they will still be looking to make increased
use of touchless interfaces, such as voice interfaces, facial recognition, or
apps." Touchless interfaces are moving beyond improving the customer
experience in an increasingly health-and-safety conscious world into the
enterprise. Three-quarters of organizations believe that increasing customer
appetite for non-touch practices will persist even in the post-pandemic world.
This is helped by the fact that customers' trust in AI is on the rise, with
67% of customers reporting that they trust the personalized recommendations
and suggestions provided by AI-enabled interactions. "Trust is something very
difficult to gain and very easy to lose," the report quotes Luciano Floridi, a
philosophy and ethics information professor and director of the Digital Ethics
Lab at the University of Oxford, as saying.
Why Builder Is Often an Antipattern and How to Replace it With Fluent Builder
First of all, let's define the goal. The goal here is to return checks back to compile time. If code which does not build complete POJOs will not pass compilation, then there will be no need for dedicated tests, no need to perform checks in build() method. But, most importantly, we will remove a lot of mental overhead from developers. So, how this can be done? Probably, the most obvious way is to use the Fluent API pattern. The Fluent API has two parts (just like Builder, by the way): provide a convenient way to invoke methods in a chain (both, Fluent API and Builder are identical in this part) and restrict every subsequent call in the chain to only an allowed set of methods. The second part is what is most interesting for us. By limiting the set of methods that can be invoked at every step of building POJOs, we can enforce a particular sequence of calls and enable the call to the build() method only when all fields are set. This way, we shift all checks back to compile time. As a convenient side effect, we also make sure that all places where particular a POJO is built look identical.How neural network training methods are modeled after the human brain
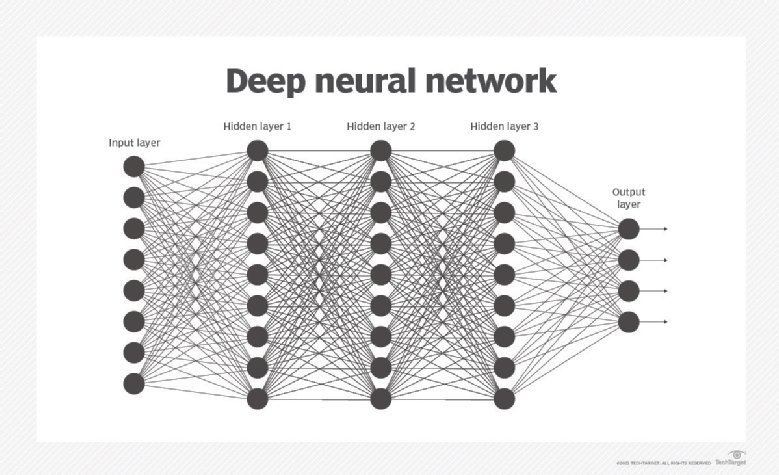
At a foundational level, neural nets start from some untrained or pretrained
state and the weights are then adjusted by training the network to make the
output more accurate. While this may sound simple, adjusting the weights can
take lots of time and compute power to get correct. Each hidden layer in the
neural net detects a specific class of features. If we take a neural net that
is built to detect cats, the first layer might detect some level of
abstraction in the image. The next layers then detect a further level of
abstraction. With enough training data, the neural net will adjust its weights
to be able to detect if the image presented is a cat or not a cat. Now, you've
built a model that identifies cats, a binary classifier that will give you a
probability of whether the image is a cat or not. However, since this model
was not trained on bird images, or car images, or flower images, the entire
process needs to start over to accurately detect each different object. While
there are approaches to take a neural network that has learned one thing and
apply it to another similar training task, called transfer learning, in
general, neural networks are narrow in what they have learned.
Chinese hackers blamed for the spread of MgBot Trojan across India, Hong Kong

It is believed that the RAT is being deployed via spear phishing emails and is
used in targeted attacks against political entities and individuals. "The
lures used in this campaign indicate that the threat actor may be targeting
the Indian government and individuals in Hong Kong, or at least those who are
against the new security law issued by China," the team says. If a victim
downloads the phishing document and enables macros, the payload is deployed
and executes, disguising itself as Realtek Audio Manager tool. The final
payload is dropped via the Application Management (AppMgmt) Service on
Windows. MgBot is able to link up to a command-and-control (C2) server to
transfer stolen device data, take screenshots, log keys, kill, disable, and
create processes, create Mutex resource restrictions, and uses persistence
mechanisms. The malware's authors have also attempted to stop the
malicious code from being analyzed through the implementation of anti-analysis
and anti-virtualization methods. These include the self-modification of code,
checks for existing antivirus products, and scans for virtualized environments
such as VirtualBox.
How COVID is Changing Technology Futures

In a normal economic downturn, you'd see companies getting conservative.
However, in this one, companies are realizing that they are behind in the
game, and they need to respond to a new situation. "This will turn into a real
innovation accelerator," Biltz said. First, it's changing where investments
are going. For instance, at grocery stores a percentage of the workforce will
be regularly spraying and sanitizing surfaces. There will be infrastructure
changes like the addition of plexiglass guards. Floor tape has been added to
show people where to stand. Plus, there have been so many changes to the
supply chain, Biltz said. He noted that over the last 4 months there's been a
60% increase in store pickups, and a lot of business moving forward will be
conducted digitally and via mobile devices. How does it look for Accenture's
clients? "We've got a bunch of companies that say the way they do business
needs to change," Biltz said. "They need to innovate to figure out how to
Rubik's Cube the new way to do it." Thankfully, over the last 10 years most
companies have already been heavily investing in their own digital
transformations. "This rapid change is almost a stress test for that," Biltz
said. "Companies had been trying to make themselves more agile."
Making Workplaces More Humanistic
eing able to become vulnerable will support you in building good business and
a more humanistic workplace. To develop the skills to do self-reflection is
one of the key activities that you are able to do for yourself and your
environment. As a leader, you keep a mirror for your team to see potentials,
opportunities, and obstacles. but if you can not see yourself clearly in it,
how are you able to reflect on your own behavior and share that with your
people, your team? ... I had team members of many ages, races, genders,
orientations, and preferences. I had multiple people with mental challenges
that could best be described as "neurodiversity". I never cared about how
people looked, where they came from, or what they did in their free time. The
only thing that mattered was: are they contributing to better products and a
better company? If yes, then they were welcome. A humanistic workplace
embraces humans of all stripes and colors. A humanistic workplace supports
professionals to perform better. In an earlier interview from StretchCon 2020,
InfoQ explored how leaders can foster high-performing teams.
Quote for the day:
No comments:
Post a Comment