Preventing data loss and mitigating risk in today’s remote work environment

Regulations, particularly in the financial services sector, often contain specialized requirements for certain data, which specifies that an organization must control their encryption key. Typically, a very small percentage of a customer’s data falls into this category, but it is important for our customers to care for that specific data correctly. To address that regulatory and unique need for some organizations, today we are pleased to announce the public preview of Double Key Encryption for Microsoft 365, which allows you to protect your most confidential data while maintaining full control of your encryption key. Double Key Encryption for Microsoft 365 uses two keys to protect your data, with one key in your control and the second in Microsoft’s control. To view the data, one must have access to both keys. Since Microsoft can access only one key, your data and key are unavailable to Microsoft, helping to ensure the privacy and security of your data. With Double Key Encryption for Microsoft 365, you not only hold your own key, but this capability also helps you to address many regulatory compliance requirements, easily deploy the reference implementation, and enjoy a consistent labeling experience across your data estate. For more information, check out the Tech Community blog.
Twitter hack raises alarm among government officials, security experts

It's still not known whether a nation-state actor was involved, although
Kennedy, like many security experts, notes that “it sure is interesting timing
with the election coming up.” However, because President Trump relies so
heavily on Twitter to communicate his messages, Kennedy doesn’t believe that
Russia would be the culprit this go-around. “If you think Trump and Russia are
in cahoots, it would not be in the Russians’ best interest to make Twitter
look like an untrusted source of information.” The distinction between Twitter
and other critical services is that Twitter doesn’t maintain a unique
infrastructure for which the marketplace cannot quickly and easily provide a
substitute. It is, in essence, just a form of speech, which is backed by
sophisticated infrastructure, to be sure. It is fundamentally a communications
platform protected by the First Amendment right to free speech, some experts
say. “Regardless of the ubiquity of platforms like Twitter, they are not
'critical infrastructure' like the telephone system or the electric grid that
are necessary to the operation of vital functions,” Robert Corn-Revere, First
Amendment law expert and partner at Davis, Wright, Tremaine LLP tells CSO. “It
is not as if news or political dialog would stop if Twitter were disrupted,”
he adds.
Cybersecurity Lessons from the Pandemic
When a crisis hits, it's usually late in the investigation that we discover
the unknowns that we didn't know about. For example, when COVID-19 initially
became known, experts assumed it had spread to only a few Asian countries. As
a result, many countries outside of Asia immediately set in motion preventive
measures and travel bans for people traveling from those countries, while
still keeping open borders for other nations. It was discovered later how
coronavirus spread to rest of the world and that cases in Italy had escalated
drastically in just a few days, thereby revealing the true extent of spread
and risk exposure. Similarly, when a cyberattack happens, it is mostly during
the ongoing investigation, and often later rather than earlier, that one finds
out about the true extent of infiltration, risk exposure, and the effects on
an organization's infrastructure and business. It's this meta-ignorance that
poses a challenge and prevents us from being immune to these unknown threats
that we don't know. The other aspect that connects the challenges of a
pandemic to the challenges we face today in cybersecurity is the extensive
globalization, digitalization, and interconnections.
COVID-19 fuels cyber attacks, exposes gaps in business recovery

With added risks from third-party applications and the supply chain, these
findings revealed that the extended enterprise was under pressure, according
to Rick McElroy, VMware Carbon Black's cyber security strategist. The
COVID-19 outbreak also unveiled gaps in business recovery planning of 89% in
the country, who described such holes as slight to severe. Another 86%
uncovered gaps in their IT operations as a result of the pandemic, while 85%
identified problems due to a remote workforce and 73.5% had issues related to
visibility of cybersecurity threats. McElroy said: "The global situation with
COVID-19 has put the spotlight on business resilience and disaster recovery
planning. Those organisations that have delayed implementing multi-factor
authentication (MFA) appear to be facing challenges, as 32% of Singaporean
respondents say the inability to implement MFA is the biggest threat to
business resilience they are facing right now. "These figures indicate that
the surveyed CISOs (chief information security officers) may be facing
difficulty in a number of areas when answering the demands placed on them by
the COVID-19 situation," he said.
AI Adoption – Data governance must take precedence

Unsurprisingly, across the board research and development dominate in current
AI adoption trends, followed closely by applications in IT and customer
service. That being said, respondents cited a widening range of industry areas
in which functional parts of a company use AI. As a whole, this indicates that
companies are increasingly turning to AI and machine learning as a business
tool. Obstacles are to be expected on the path to digital transformation,
particularly with unfamiliar entities in the mix. For AI adoption, the most
prevalent obstructions are: a company culture that doesn’t recognise a need
for AI, difficulties in identifying business use cases, a skills gap or
difficulty hiring and retaining staff and a lack of data or data quality
issues. With this broad spectrum of challenges, it is worth delving into a
couple of them. Firstly, it is interesting to note that an incompatible
company culture mostly affects those companies that are in the evaluation
stage with AI. When rephrased, perhaps it is obvious – a company with “mature”
AI practices is 50 percent less likely to see no use for AI. By contrast, in a
company where AI is not yet an integrated business function, resistance is
more likely.
Remote working: We're stressed and distracted and making these security errors

"Working in unusual environments can be stressful and distracting," said
Hancock. "Prior to the pandemic, people were used to operating in distinct
spaces - home, work, social - and we had different ways of understanding the
world in each space. The events of 2020 mean these spaces have blurred, and
we've had to quickly learn new ways of operating and this has its
challenges." Other reasons for people clicking on phishing emails
included the fact that they looked legitimate (43%) and the fact that they
appeared to have come from a senior executive (41%) or a well-known brand
(also 41%). Men were twice as likely as women to fall for phishing scams, with
34% of male respondents saying they have clicked on a link in a spoof email
compared to just 17% of women. Those working in the tech industry were the
most likely to click on phishing emails, with nearly half of respondents in
this sector (47%) admitting having done so. This was closely followed by
employees in banking and finance, with 45% of workers admitting to have
clicked on phishing links in emails. Fatigue was another factor in
causing workers to click on malicious links, and was also cited as a top
reason for sending an email to the wrong person by 44% of respondents. Nearly
half (46%) of respondents said they had experienced burnout in their career.
4 Steps to Help You Plan a Cyber Resilience Roadmap
Keep in mind resources are not purely technological. Your resource mix is made
of up technological and human capital, including how they operate and interact
with each other. You can have the latest-and-greatest tools all properly
configured, but, if you do not have an experienced and properly-trained team
managing and maintaining these tools, these tools may never see the light of
day. You also need to be cognizant that all current and future
information security tools could lead you into a privacy jam if use is not
thought through. Anything from real-monitoring issues to holding too much (or
unnecessary) amounts of personally identifiable information (PII) increases
the liability side of your balance sheet. Therefore, it’s the totality of your
resource mix that will help determine your current position. So how do you
determine your current position? It all begins with risk management. Risk
management is by no means a science, even though a lot of science goes into
it. As some environments become more complex, their likelihood for fragility
increases, notes risk management expert Nassim Nicholas Taleb in his book
“Antifragile: Things That Gain from Disorder.”
Engineering Successful Cloud Migrations
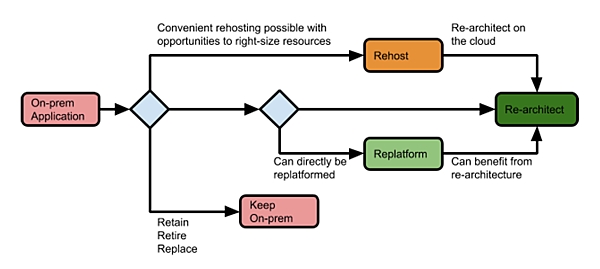
The perception of agility on the cloud is largely from the lens of
provisioning. Unlike the infrastructure on premises, provisioning necessary
infrastructure and platform resources is far more convenient on the cloud,
albeit at a cost. But this is only a small component in the overall process of
launching a change into production. Achieving agility on the cloud involves
relentless automation and optimisation of not just the delivery pipeline but
also the business. When combined with lean practices and evolutionary
architectural principles, businesses rapidly adjust to capitalise on
opportunities and reduce risks. The emergence of digital technologies on cloud
platforms, in combination with agile practices, promises faster innovation.
Most cloud vendors are offering technologies that are building blocks for IoT
sub-systems, data science applications, big data pipelines, and AI/ML
services. This allows cloud consumers to build and evolve digital applications
on the cloud fairly quickly. This convenience comes with its own challenges.
Vendor lock-in is a big risk as these technologies offered by different cloud
vendors may not be compatible. Applications built using Domain Driven Design
techniques can be migrated between different cloud offerings if they have
interfaces to these technologies on the host cloud offering.
Dell XPS 15 9500 (2020) review: Still the 15-inch laptop to beat

Cramming a 15.6-inch screen into a chassis with a 344mm by 230mm footprint is
quite a feat. This year's model comes in at 18mm thick (1mm more than the 2019
XPS 15), and has a starting weight of 1.8Kg, which you'll certainly feel in a
backpack. The trade-off is a very robust build utilising carbon fibre to add a
real solidity to the chassis. There's no give in the thin lid section, nor in
the base, wrist rest or keyboard. A sleeve probably isn't necessary to provide
in-bag protection, unless you want to preserve a scratch-free finish to the
outer chassis. There are two other notable design changes compared to last
year's model. One of these is the touchpad, which has increased significantly
in size. It now looks almost comically huge, but in fact the size makes
navigation around the screen easier: there's no need to feel for one edge if
you want to drag the cursor from one side of the screen to the other. After
writing this review, going back to my regular laptop's smaller touchpad felt
positively constraining. ... The XPS 15 9500 really stands out for the quality
of its 15.6-inch display. My review unit had the top-end 4K+ touch screen with
3,840 by 2,400 resolution (290ppi).
The State of Hacktivism in 2020
While the days of high-risk technical hacks dominating headlines may be gone,
the Twitter hijack and BlueLeaks show there are still hackers looking to access
secure data — and their reasons remain varied. One thing that might temper
planned hacktivist actions could be "the hammer of the state" in the form of
aggressive law enforcement, says Coleman, author of "Hacker, Hoaxer,
Whistleblower, Spy: The Many Faces of Anonymous." DDoSecrets has said they're
prepared for the US government to come after them, but Coleman isn't so sure.
"The question is whether BlueLeaks will be stamped out in the next few months.
But the blocking and censorship makes them more visible," she says. Organizing
groups to participate in social media actions is not prevented under the
Computer Fraud and Abuse Act (CFAA), the broad antihacking law that has been
amended several times but not dramatically changed since it was passed in 1986.
But more technical hacks of networks remain illegal, and prosecutors still have
broad leeway in pursuing computer crimes, seven years after the prosecution and
subsequent suicide of Internet hacktivist Aaron Swartz under the CFAA.
Quote for the day:
No comments:
Post a Comment