Software as a Service (SaaS): A cheat sheet

Beyond reliability, and depending on the nature of your business applications,
it is also vitally important to evaluate the capacity provided by your chosen
ISP. Querying large databases or moving large media files will require more
bandwidth than is typical for less-intense applications like email; however,
even extremely large bandwidth may not be enough, if there are also latency
issues. There are similar reliability concerns when choosing the service
provider for the SaaS applications themselves. Business organizations have to
think about the longevity of their provider, their commitment to security,
their willingness to customize applications, and their plans for feature
upgrades. SaaS requires a business to relinquish some control in order to reap
the benefits of the distribution system. Relinquishing control may also cause
problems when the SaaS provider updates certain application features that the
business does not want changed. Some feature upgrades will break existing use
cases, especially if the business is using a customized version of the
software. Some SaaS vendors have been known to eliminate aggregately under
used features from their software, which causes problems for businesses that
choose to adopt those features.
APT Group Targets Fintech Companies
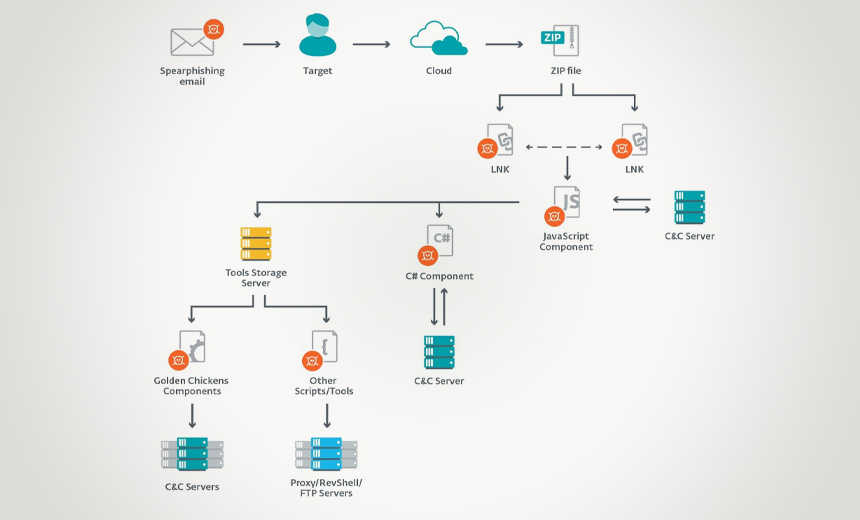
Once the targeted victim clicks on the LNK file to view one of the documents,
the malware begins to load in the background and infect their device,
according to the report. Once the attackers successfully infect devices and a
network, the malware steals sensitive corporate data, such as customer lists,
credit card information and other personally identifiable data, along with the
firm's investments and trading operations data, the ESET researchers report.
In the next phase of the attack, the JavaScript components deploy other
malware the Evilnum operators purchased from other hackers, including code
written in C# from the malware-as-a-service provider Golden Chickens, the
report notes. The attackers also use Python-based tools in their toolkits, the
researchers add. While the JavaScript component acts as a backdoor and handles
communications with the command-and-control server, the C# code takes on other
tasks, including grabbing a screenshot whenever the mouse is moved over a
certain length of time, sending system information back to the operators as
well as stealing cookies and credentials. Eventually, this process will kill
the malware when the campaign is complete, according to the report.
Why Segmentation is More Effective Than Firewalls For Securing Industrial IoT

As we’re so accustomed to using firewalls in our everyday lives (particularly
on our own private computers, tablets, and smartphones) it might seem
intuitive to use a firewall as a safeguard for IIoT-connected devices as well.
However, the choice isn’t quite so straightforward as it might at first seem.
Internal firewalls are expensive and complex to implement. It could be that
for genuinely reliable protection, you need to install a firewall at every
IIoT connection point. This could mean that hundreds (perhaps even thousands)
of firewalls are required. We’ve already discussed how businesses’ technology
security budgets are often overstretched. Taking this into account, security
spend needs to be very carefully calculated and targeted. Segmentation, on the
other hand, makes it possible to keep particular types of devices siloed off
in a certain segment, thereby enhancing security. It also helps to enhance
visibility and simplify classification of different device types.
Organisations can then create risk profiles and relevant security policies for
device groups.
How data and AI will shape the post-pandemic future

The general public are particularly becoming used to AI playing a huge role.
The mystery around it is beginning to fade, and it is becoming far more
accepted that AI is something that can be trusted. It does have its
limitations. It's not going to turn into the Terminator and take over the
world. The fact that we are seeing AI more in our day-to-day lives means
people are beginning to depend on the results of AI, at least from the
understanding of the pandemic, but that drives that exception. When you start
looking at how it will enable people to get back to somewhat of a normal
existence―to go to the store more often, to be able to start traveling again,
and to be able to return to the office―there is that dependency that Arti
mentioned around video analytics to ensure social distancing or temperatures
of people using thermal detection. All of that will allow people to move on
with their lives and so AI will become more accepted. I think AI softens the
blow of what some people might see as a civil liberty being eroded. It softens
the blow of that in ways and says, "This is the benefit already and this is as
far as it goes." So it at least forms discussions whenever it was formed
before.
IoT: device management and security are crucial

Operational challenges abound from the beginning of the IoT journey to its
end. For example, how do you efficiently roll out hundreds of thousands or
even a million devices in a timely manner? Once up and running, device
firmware and IoT application software will need to be updated – possibly
multiple times – during the course of the device’s life. Additionally, the
device should be monitored against established baselines. This creates
the environment for an early warning system that can highlight possible
software bugs or security exploits. Devices also may experience an “upgrade”
during their life cycles, as new capabilities may be activated and enabled
over-the-air, based on needs and business cases. Ownership changes require
re-assignment of control, and at the end, devices need to be decommissioned
and brought to end-of-life in an efficient manner. These development and
deployment challenges are prompting companies to re-examine how they allocate
resources more efficiently. For example, only 15% of overall IoT systems
development time is IoT application development. But a full 30% is
device-management issues (provisioning, onboarding, and updating devices and
systems), while 40% is taken up by developing the device stacks.
More pre-installed malware has been found in budget US smartphones

While the app does function as an over-the-air updater for security fixes and
as an updater to the operating system itself, the software also installs four
variants of HiddenAds, a Trojan family found on Android
handsets. HiddenAds is a strain of adware that bombards users with
adverts. In order to verify where the malware originated from, Malwarebytes
disabled WirelessUpdate and then re-enabled the app. Within 24 hours, four
adware strains were covertly installed. As the malware on the UMX and ANS
differ, the team wanted to see if there were any ties linking the brands. A
common thread was the use of a digital certificate used to sign the ANS
Settings app under the name teleepoch. Upon further investigation, the
certificate was traced back to TeleEpoch Ltd, which is registered as UMX in
the United States. "We have a Settings app found on an ANS UL40 with a
digital certificate signed by a company that is a registered brand of UMX,"
Collier says. "That's two different Settings apps with two different malware
variants on two different phone manufactures & models that appear to all
tie back to TeleEpoch Ltd. ..."
Increasing demand for RegTech to Meet Regulatory Burden

The demand has grown exponentially high since the Global Financial Crisis of
2008, businesses need to comply with regulatory reforms related to Anti-Money
Laundering (AML) and due diligence (KYC) requirements. The cost to comply with
regulations was staggering, but the non-compliance costs more due to hefty
amounts of fines. Digitization of regulatory compliance assists businesses in
meeting the needs of regulation, that too, by cutting the cost. According to
the study, the cost of compliance across all banks from 2014 to 2016 averaged
approximately 7.0% of their noninterest expenses. RegTech startups are
experiencing growth and investment as firms are realizing the need to
capitalize on compliance efficiency. Businesses can use it for a competitive
edge in the industry. There is great potential for powering the future of
financial regulation by integrating RegTech. It has major implications as it
provides reduced regulatory costs and improved operational efficiency. The
main target of RegTech was the finance industry.
Why businesses are adopting AI to improve operations

AI has improved productivity in an array of sectors. AI-powered contact center
software has allowed companies to become incredibly efficient. In a shop, a
digital SKU system is far more efficient at keeping tabs on stock levels than
a manual one. It can record and analyze the demand for certain articles. More
will automatically get ordered. A fashion store can see when a garment is
selling like hot cakes and get more before the trend runs its course. This
maximizes profit on the item. For teleconferencing solutions or other software
providers, one of the biggest problems faced is customer churn. Retention
schemes try to contact as many customers as possible whose contract is due to
run out. Discounts and other enticements are offered to remain. But some of
those customers would have stayed anyway. Others, who were more likely to
leave, may not have been contacted. Customer services can't get in touch with
every single person whose contract is due to be up. What the firm needs to
understand are the factors influencing people to stay or go. An AI program is
able to analyze the data from thousands of customers. It works out the risk
factors and pulls out a list of people most likely to leave.
10 Ways AI Is Improving New Product Development

From startups to enterprises racing to get new products launched, AI and
machine learning (ML) are making solid contributions to accelerating new
product development. There are 15,400 job positions for DevOps and product
development engineers with AI and machine learning today on Indeed, LinkedIn
and Monster combined. Capgemini predicts the size of the connected products
market will range between $519B to $685B this year with AI and ML-enabled
services revenue models becoming commonplace. Rapid advances in AI-based apps,
products and services will also force the consolidation of the IoT platform
market. The IoT platform providers concentrating on business challenges in
vertical markets stand the best chance of surviving the coming IoT platform
shakeout. As AI and ML get more ingrained in new product development, the IoT
platforms and ecosystems supporting smarter, more connected products need to
make plans now how they're going to keep up. Relying on technology alone, like
many IoT platforms are today, isn't going to be enough to keep up with the
pace of change coming.
CDO Leadership Skills That Matter
Persistence is a key trait of successful leaders—they don’t get demotivated too
easily. Whereas some people retreat back to their caves after failed attempts to
collaborate with the organization, choosing to focus only on internal marketing
or just a few pilots, I find that leaders who are persistent have a seat at the
strategic table with their peers, have a strategy, and have a roadmap. They’re
constantly thinking through how their capabilities could be used across the
organization. They’re not easily defeated when something doesn’t go right.
Persistence is important because the failure rate of data strategies and data
governance teams is high; you’re building in a function that you’re not
consolidating under one person, one business function. You’re often using a
distributed leadership and organization model, which takes hard work to set the
right expectations and have ongoing communications. On a regular basis, you have
to give different people the WIIFM, the goals and objectives, that apply to
their particular situation, and try to drive adoption and change in a way that
fits with how each team works.
Quote for the day:
No comments:
Post a Comment