4 factors to rethink when leading innovation
You may have been quite good at planning. Perhaps it helped you achieve your current leadership role. However, the age of planning is over, Whitehurst says. Processes such as performance management need to be dramatically shortened and focus more on experimentation. Innovation, he says “requires greater comfort with ambiguity all the way through your organization.” A prerequisite for that comfort is an understanding of corporate strategy. “Most leaders are saying, ‘My people really need to know the details of their job function. They don’t necessarily need to know the strategy of the whole company,’” Whitehurst says. “But to be more innovative, you have to flip that around. Everybody needs to know the strategy of the company and how they fit into it.” ... And you frankly want to be kind of ambiguous down to what the organization and the individual needs to do – because that’s where you’re giving people latitude to try.
The way companies look to fend off cyberattacks needs a rethink
When it comes to password protection, the only game-changer from the hacker’s perspective is in its length and uniqueness. Passwords with more than 25 characters that are unique rarely get reused and they also demand that users be innovative when creating them. When they are encrypted inside the solution, software or service, they will be the last ones to be cracked. Password manager applications are a good solution too. But if you are concerned about their level of security, given that nearly all of them have been hacked, a poem or a shopping list would serve well as a password. It would do a better job in minimising the chances of being hacked than the typically-advised uppercase and special character tweaks. We have discovered from our research that more than 4.3 billion passwords to different online accounts worldwide have been breached over the past three years. That is one in every three accounts. So it is increasingly likely that your organisation’s information is also vulnerable.
Data center admins gain the benefits of microservices
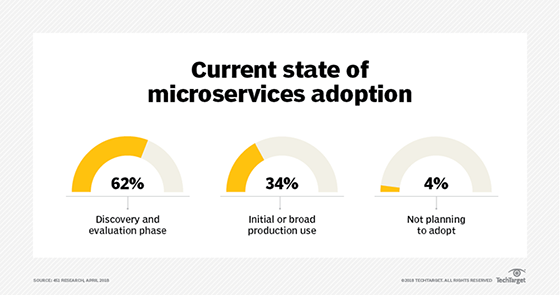
Microservices are applications coupled into a collection of services that implement business functionalities. To maintain certain software functions on a more regular basis, developers can break out software components -- or services -- to form a distributed system. This makes the technology a good fit for cloud-based or on-premises data center deployments because it is an architectural pattern that can be tailored to developers' needs. Docker and automation software, which many data center admins are already familiar with, are key enablers of microservices. "Microservices do not require gold-plated, expensive, dedicated hardware," said Ian McCarty, president and CEO of PhoenixNAP Global IT Solutions. "They can run on shared clusters on top of commodity [data center] hardware, which is easier to scale and replace." To get a microservices application up and running, admins must use an infrastructure with a low-latency connection. Admins can turn to automation software to ease deployment, because they must deploy each application component separately -- often within containers.
An interview with Robert Fink, Architect of Foundry, Palantir’s open data platform
The notions of open platforms and open architectures originate in hardware design and describe systems in which different components can be added, replaced, or upgraded independently. Buyers like this idea, because it reduces vendor lock-in and increases flexibility and negotiating power. This translates more or less directly to software platforms: they are considered open if their inter-component APIs follow open standards, are well documented, and can be accessed by any party through readily available tools and libraries. This is in contrast to closed APIs whose internals are undocumented and often intentionally cryptic. Moreover, use of closed APIs is typically governed by license agreements that prohibit third-party tools, or even outright ban any external use of its data. At Palantir, we lean on open standards like JSON and HTTP for APIs, and open-source technologies for data storage and transformations. In the early days of computing, the majority of commercial platforms were closed (because, hey, who doesn’t like a good monopoly?) and this led to the siloed compute and data infrastructures that most IT organizations on this planet are still trying to unwind today.
What the device-as-a-service (DaaS) trend is all about

Initially, major OEMs (original equipment manufacturers), like Dell, Hewlett-Packard and Lenovo. That made sense, since a big part of PCaaS was the faster hardware replacement cycle inherent to subscriptions; computer makers were the most motivated to pitch such plans, especially when shipments stalled, then sank, in large part because consumers abandoned PCs. Although vendors like those named above remain major players, others are eager to get in on the action. Microsoft, for one. Its "Microsoft Managed Desktop," or MMD, will include the usual bits and pieces - although restricted to Microsoft's own hardware for now - but because Microsoft makes the operating system, it has some unique strengths: It runs Windows 10's update/upgrade servicing and it pulls a wealth of data from devices running the OS through its mandatory telemetry. Microsoft has the edge over computer makers in the device management parts of PCaaS. Telemetry is key, Gartner analyst Stephen Kleynhans agreed in an interview last week.
Manage Insider Threat Risk and Prevent ‘Big Brother’ Perception

Introducing the idea of insider threat risk management to your workforce and enterprise risk planning agenda can be challenging. Your insider risk management plan may be met with a lack of workforce understanding of proposed policy changes, concern that it is going to set up ‘security speed bumps’ that impede workflows, or fear that it will invade their privacy. This means that the onus is on you to determine how to get your organization’s risk management naysayers onboard your well-intentioned security vessel. How can your organization introduce the idea of insider risk management to the workforce with as much transparency and inclusivity as possible? I learned the importance of bringing the workforce onboard through years of counterintelligence and insider threat mitigation in government and industry. ... Remind them that the impacts of an insider incident transcend stock price and shareholder value and could put the physical safety of staff and personnel at risk.
Grasp container basics to plan enterprise adoption

Before container basics comes container history. Physical hardware systems have an inherent risk of inefficient use and the inherent benefit of application isolation. To address inefficiency, the IT industry adopted multitasking systems, which run several applications at once, but that simple form of resource sharing doesn't separate the applications enough. One app can contaminate the performance of other apps if it behaves badly, and attackers may even be able to breach security from one app to another. This tradeoff between isolation and efficiency is inherent in virtualization because of shared resources. Perfect security and performance management requires physical isolation in bare metal. Highest efficiency calls for multitasking OSes. Virtualization options fall between these extremes. Virtual machines (VMs) replicate the server, with a full OS and middleware. Hypervisor software manages and runs these VMs on physical resources.
A cybercrime epidemic drives business–and funding–to cybersecurity
The artificial intelligence company’s growth highlights the demand for sophisticated defenses against hackers as well as Europe’s increasing capacity to spin up top-tier tech companies. “What drives the valuation is our response to the things covered in the media,” said Darktrace CEO Poppy Gustafsson in an interview. The five-year-old tech company was created by University of Cambridge mathematicians, and its software is designed to monitor everything from cloud networks and internet-of-things devices to industrial control systems. Cyber security is in demand for good reasons. As more data is kept online, the potential for breaches is increasing. At the same time, more of our devices are connected to the internet, giving hackers new ways to snoop on corporate board meetings, spy on political activists, or even damage important utilities. Data theft costs companies an average of $3.9 million, while “mega breaches” of more than 1 million compromised records can cost businesses as much as $350 million, according to a study sponsored by IBM Security and conducted by the Ponemon Institute.
Scrum The Toyota Way

We have learned that agility is hard, really hard. There is also no such thing as an agile transformation. You fundamentally have to change your operating model, and undertake an organizational transformation to achieve the agility you desire. Scrum is but one item in the toolbox to help you do this. You also need a sense of urgency. If the C Suite don’t see a compelling reason to change, chances are you’ll actually make things worse by messing with the current condition, and the resistance to change will be overwhelming, with no mandate to actually achieve that change. I’ve also realized that not everyone needs to be agile! If you’re shipping concrete slabs you probably don’t need to do that in two-week sprints, as the need to change rapidly is not there. Sure, Scrum will give you a planning cadence, but Scrum was intended to work in complex domains and with complex systems. These are areas where a linear approach and fixed thinking are not effective.
5 Competencies You Need to Succeed in DevOps and Beyond
Culture is a set of shared organizational assumptions that are learned by teams as they resolve problems. Integrated into day-to-day norms, culture is considered the correct way to perceive, think, and feel in relation to problems. Within DevOps, culture evolves to include implementation of continuous improvement, the building of collective intelligence, and continuously react to feedback—all based on trust. Transformational change requires strong leaders at all levels with core competencies in visioning, strategic management, flexibility, and the ability to inspire others to innovate and perform. Learning a set of skills does not make you a leader; instead leadership embodies an innate passion, integrity, authenticity, and courage. DevOps, like any other environment, requires leaders who are champions – individuals with advanced communications skills, the knowledge of diverse cultures, and people who behave collaboratively when working in teams. DevOps leadership is not something you learn and just do.
Quote for the day:
"Create A Fun And Happy Environment And Success Will Soon Be A Guest." -- Gordon TredGold

No comments:
Post a Comment