
Mobile communications are exponentially vital to individuals, to communities, to businesses, and to the wider economy. Research analysis shows that there are more than 2,500 telecom operators across the globe eliminating distances between people through data or voice connectivity. More and more, and for good reasons, the industry is adopting the blockchain technology to take advantage of fascinating applications, new features and capabilities. It is paving a concrete leap in the way to manage transactions compared to the old-fashioned traditional systems. In addition to other carrier members of the ITW Global Leaders’ Forum (GLF) that are involved in blockchain initiatives, blockchain trials (POCS) are successfully carried out by companies such as BT, Telefónica, PCCW, Colt in, Telstra, HGC Global Communications, just to name few of them. Other operators, such as South Korean Telecoms Giant KT, have built their own blockchain. The PoCs (with extensive features) demonstrated that the blockchain technology is reducing drastically the operational costs and eliminating many unnecessary outdated systems while uncovering new business streams with an unprecedented quality in monitoring transactions in real-time.
Education in the Age of Automation

Human-to-human interaction as a basis for a meaningful educational experience becomes optional. Today, it’s entirely possible to learn all you need to know to make a good living in the modern world without ever needing to sit in a classroom or interact with a human directly. Let’s face it: You can do a lot of learning from YouTube. As a result, more people are beginning to question the conventional wisdom of spending four years and thousands of dollars to get a bachelor’s degree—particularly now that companies including IBM, Google and Apple no longer require one to get hired. Coincidentally, as companies eliminate the college degree requirement for new hires, we’re seeing significant growth in technical bootcamps. One study reports that this year, 20,000 students will complete a course of study at a coding boot camp and be “job ready.” Considering that the number of students who graduated with a computer science degree from a typical college in 2017 numbered about 93,000, there’s a good case to be made that boot camps are siphoning off a number of students that otherwise would be headed to academia.
5 Artificial Intelligence and Machine Learning Use-Cases for Cybersecurity

Building resiliency in a growing digital environment complicates the development and advancement of strategic initiatives, given the propensity of underestimating the external abilities of hackers, viruses and weak structural configuration by many enterprises. Reducing the occurrence of incidents and breaches in a technological environment requires strong organizational design, which includes the necessary capabilities and precautions within the infrastructure build. Where risk is prevalent, extrapolation into the potential positive and negative opportunities that effect cross-functional departments can only be properly assessed by running many different scenarios with the data an organization already has. This is where AI can play a critical role augmenting and empowering the existing security resources. Implementing ML to actively monitor and review API calls, external access points and other logs within enterprise systems enables advanced data monitoring and filtering that can be performed around the clock, thereby eliminating some of the human resourcing and security issues.
How to match microservices middleware to your mission

It's also possible to build state-controlled microservices applications by using specific state control tools. Cloud tools, like AWS Step Functions and Azure Logic Apps, provide sequencing and state control within their respective clouds. Middleware tools, like the Redis data/state caching tool, provide similar capabilities for on-premises applications and general cloud applications. Any of these options provide an assembly framework for step-wise microservices processes and maintain the data and state context of transactions through locally stateless processes. Microservices scaling is related to state control. When multiple instances of a microservice might be used, it's necessary to distribute the work first. It's also important to maintain the transaction context over multiple messages in some way. If your business applies state control logic to its overall application, it's not difficult to extend that to multiple instances of the same microservice, but you'll still have to provide load-balancing capabilities.
Human brain stimulated by artificial synaptic device
This electrical synaptic device stimulates the function of synapses in the brain, as the resistance of the tantalum oxide gradually increases or decreases depending on the strength of the electric signals. It has succeeded in overcoming durability limitations of current devices by allowing current control only on one layer of Ta2O5-x. Synapses are areas where axons and dendrites meet. There are hundreds of trillions of synapses in one individual human brain, and these areas are where signals are sent and received. The chemical synapse information transfer system transfers data from the brain, and can handle high-level parallel arithmetic with very little energy. Worldwide research on artificial synaptic devices, which mimic the biological functioning of a synapse, is already underway. The research team also successfully implemented an experiment that identified synapse plasticity; the process of creating, storing and deleting memories, by adjusting the strength of the synapse connection between two neurons.
How to make an old Android phone feel new again

Old Android phones are everywhere. They're in closets, kitchens, desk drawers — and, yes, even in the pockets of productive business people who (gasp!) haven't bothered to upgrade in a while. Despite the constant marketing to the contrary, mobile devices can remain perfectly capable long after their launch dates. They can, however, start to seem a little slow or behind the curve after a few years of use — and the older and more resource-limited a device is, the more pronounced that effect is likely to be. But wait! Don't abandon hope just yet: A handful of simple steps can make your old Android phone feel new (or at least newer) again. And whether you're still carrying the device around as a daily driver or using it for more creative purposes, every little improvement counts. So summon your inner mechanic and get ready: It's time to give that old Android phone a much-needed tune-up — and a fresh lease on life.
Small business servers: Why and how you can say 'no' to the cloud

If your plan is to configure a server on-premises in your office or home, how you connect to the internet may be an issue. If you're just accessing some shared files on an internal network, you won't have any special complications. But if you want to use your on-premises server to serve web pages or email (or any other application) to users on the internet, you're going to have to consider the transition of data requests from the internet, through your firewall, and to your on-premise server. You should plan on having a discussion with your ISP. If you're using a consumer ISP, you may not be allowed to send data out via certain ports. At one time, when I was first setting up my web server in my apartment, I found that the local cable company wouldn't let me serve any traffic out of port 80 (the standard port for web pages). That effectively squelched my ability to run a web site, and I wound up having to buy a dedicated line. You'll also need to consider whether you can get a fixed IP address from your ISP, or whether you need to set up some sort of dynamic DNS routing. Additionally, you may have to set up port forwarding and routing on your router to send data to the right machine on your network, particularly if you're serving web pages or email.
Nagios Core monitoring software: lots of plugins, steep learning curve

The Nagios Exchange website offers a large selection of plugins for various monitoring/management scenarios. In fact, one of the strengths of Nagios is the availability of an impressive number of plugins which are compiled executables or scripts that check the status of a host or service. Nagios uses the information from plugins to determine the current status of hosts and services on your network. The plugins act as an abstraction layer between the monitoring logic present in the Nagios daemon and the actual services and hosts that are being monitored. The upside of this architecture is that you can monitor just about anything you can think of. The downside is that Nagios has no idea what is being monitored. Its job is to track changes in the state of what is being monitored. Only the plugins themselves know exactly what they're monitoring and how to perform the actual checks. The Nagios Exchange currently has almost 6,000 projects in over 400 different categories.
These 5 “clean code” tips will dramatically improve your productivity
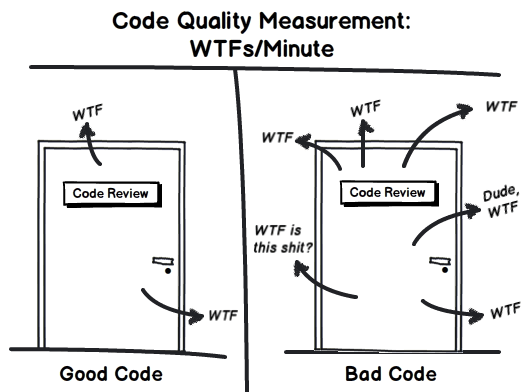
Test, test, test. We know we should always do it, but sometimes we cut corners so we can push the project out faster. But without thorough testing, how will you 100% fully know that the code works? Yes there are very simple pieces of code, but one is always surprised when that crazy edge case comes up that you thought you didn’t need to test for! Do yourself and everyone on your team a favour and regularly test the code you write. You’ll want to test in a coarse to fine style. Start small with unit tests to make sure every small part works on its own. Then slowly start testing the different subsystems together working your way up towards testing the whole new system end to end. Testing in this way allows you to easily track where the system breaks, since you can easily verify each individual component or the small subsystems as the source of any issues. Choose meaningful names. This is what makes code self-documenting. When you read over your old code, you shouldn’t have to look over every little comment and run every small piece of code to figure out what it all does!
These are the warning signs of a fraudulent ICO
If a company website, whitepaper, or project descriptions are also full of nothing more than fluff, buzzwords, and portray a lack of substance, this is a clear warning sign that all may not be as it seems. Another classic warning sign that an ICO may not be everything it promises is also a return on investment (ROI) which seems too good to be true. In the case of Bitconnect, investors were offered a 120 percent return on their investment annually, but the company performed an exit scam and rendered its tokens useless, leaving investors heavily out of pocket. LoopX went dark and vanished with $4.5 million after pulling an exit scam in February, three ventures -- ACChain, Puyin, and BioLifeChain -- launched by Shenzhen Puyin Blockchain have stolen close to $60 million, and CryptoKami, ran by anonymous parties, also ran a fraudulent ICO and closed after raising $12 million. According to Diar, from 2016 to August this year, fraudulent ICOs have been responsible for the theft of close to $100 million.
Quote for the day:
"Blessed are the people whose leaders can look destiny in the eye without flinching but also without attempting to play God" -- Henry Kissinger
No comments:
Post a Comment