
Apple has very clearly focused on healthcare, steadily building an in-house team of experts, most notably around medical devices who know how to work with regulators, researchers and IT. With the introduction of HealthKit, ResearchKit and CareKit, Apple has been at the forefront of unlocking personal health data and allowing users to share it with care teams, researchers and even first responders. Some of the broadest health studies ever conducted have relied on ResearchKit. iPhones and Apple Watches make it possible to contact emergency services and care-givers in seconds, and they provide key information about us using the emergency medical information card that can be accessed on an iPhone – even when the phone is locked. And increasingly, they alert us to signs of danger and disease that might otherwise go unnoticed. Apple is not slowing its efforts; in fact, it’s just getting started. The announcement this week of fall detection, complete with an understanding of different types of falls, is a major improvement aimed directly at older users.
Is Pattern Recognition Killing Innovation?
Underrepresented founders face greater challenges in convincing a fairly homogeneous industry that issues they are solving are significant enough, that the services they provide are widely needed and that they are the ones to take this vision into a multibillion dollar company. Katrina Lake, founder of Stitch Fix, and Shan Lynn Ma, founder of Zola (both multibillion dollar companies) have spoken out about their struggle to raise funding and felt it was due to the lack of diversity in the VC industry. "You can't blame the kind of individual for having that preference, but then you step back and realize 94% of venture investors are male and have similar preferences. And so, I think that it unquestionably made it harder," says Lake. In a sector that is driven by business ‘intuition’ and ‘gut feeling’ based on past patterns, female founders and other underrepresented founders, lose out. This is, to some extent, due to what experts call “homophily” in which similarity breeds connection, which means VCs prefer to hire, invest in, or co-invest with those that are similar to themselves.
Outcomes-based security is the way forward

“We are still finding the same problems every year that we have found in previous years, with things like credential theft and abuse still common, and multifactor authentication – especially for privileged accounts – still rare, even though this would reduce the attack surface massively,” he says. The only real change, he adds, is that there is now a lot more on the corporate IT network, with “almost everything” connected and online as business processes become increasingly digital and the dependency on IT is greater than ever before. “But businesses still assume that if they have spent millions on security products everything is fine, but bad guys usually work out what has been done to make something more secure and will find a way around it, so it is a continual arms race,” he says. As a result, Raeburn believes most cyber security technology innovations tend to provide a false sense of security for organisations because they will be effective only for a limited period of time.
Fighting the fear of new tech with the chief technology evangelist
Training is also paramount, and should be conducted in virtual or test environments as much as possible, long before the new technology goes live. It’s also important to remember that every employee will need to transition to a new technology at a pace that works for them which won’t interfere with their primary objectives. This can be especially important in organizations like healthcare, where doctors and other clinicians can’t be pulled away from their patients, or afford to slow down the treatment process due to the implementation of a new technology. Getting buy-in and acceptance from the workforce that will be using any new system is critical, since they will ultimately make or break the project. And for that to happen, the new technology needs an advocate, someone who can rally the troops and make people actively excited about the pending change long before the wheels start to turn on a new project.
Mobile fraud is increasing, attack rates rising 24% year-over-year

Financial institutions were besieged with 81 million cybercrime attacks in the first half of 2018 on the ThreatMetrix global network. Of these, 27 million were targeting the mobile channel as fraudsters turn their attention to the success story that is mobile banking adoption. Financial services mobile transactions are growing globally, with China, South East Asia and India showing the strongest regional growth. This indicates that the mobile channel is a key enabler for financial inclusion in emerging economies. Overall, the biggest threat in financial services comes from device spoofing, as fraudsters attempt to trick banks into thinking multiple fraudulent log in attempts are coming from new customer devices, perhaps by repeatedly wiping cookies or using virtual machines. Mule networks also continue to negatively impact the global banking ecosystem, particularly as financial crime becomes an ever-more sophisticated and hyper-connected beast. The challenge for financial institutions is detecting mule activity even when individual account behavior may not trigger red flags.
Smartwatches finally evolve into a viable platform

The Qualcomm Snapdragon Wear 3100 platform allows for a pervasive display, and the watches have battery life measured in days, not hours. This means that a watch maker can create a watch with a pervasive, attractive face designed to work with the watch case and look good to others, not just the watch user. Therefore, companies like TAG Heuer and Louis Vuitton (who owns TAG Heuer and Hublot) are now planning on releasing smartwatches by year’s end. Finally, we have smartwatches that embrace the idea of a watch being a showcase of wealth and status. The part the watchmakers need to address is collectability…and that suggests a modular approach, where the movements and the cases are separate. That way you can buy and collect cases and then insert your up-to-date smartwatch component (which will then morph its display to match the case it’s placed in). I’m aware that TAG Heuer was working on a project like this about a decade ago, so my money is on them getting this right first.
Supermicro unveils an insanely fast, insanely thin storage server
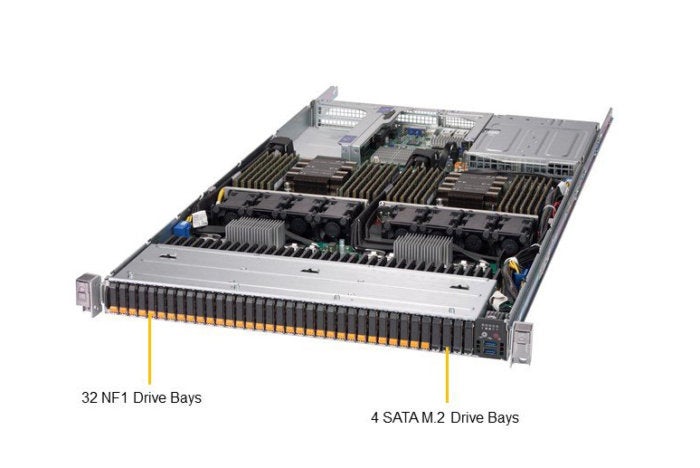
The new Supermicro product, the SSG-1029P-NMR36L, has 36 18TB NF1 drives in its 1U chassis, doubling the capacity of a model introduced in January with 288TB. The server also comes with two 28-core Xeon SP processors and holds up to 3TB of memory in 24 DIMM slots and dual 16-lane PCIe network cards. The NF1 drives are all front-loaded and hot-swappable using the NVMe protocol for high-capacity network storage and very low latency performance. The optimized power profile of the fully hot-swap-capable NF1 devices means more processing power can be reserved to drive IO with the fastest CPU and memory available. "At Supermicro, we consistently offer our customers early access to the very latest and best technologies," said Charles Liang, president and CEO of Supermicro, in a statement. "Our 1U NF1 storage server features the most power-efficient, next-generation flash technology with the highest storage density and best IOPS performance. This provides a real time-to-value competitive advantage for users with data-intensive workloads like big data, autonomous driving, AI, and HPC applications."
When to use a CRDT-based database
Everything looks good with the eventual consistency model until there are data conflicts. A few eventual consistency models promise best effort to fix the conflicts, but fall short of guaranteeing strong consistency. The good news is, the models built around conflict-free replicated data types (CRDTs) deliver strong eventual consistency. CRDTs achieve strong eventual consistency through a predetermined set of conflict resolution rules and semantics. Applications built on top of CRDT-based databases must be designed to accommodate the conflict resolution semantics. In this article we will explore how to design, develop, and test geo-distributed applications using a CRDT-based database. We will also examine four sample use cases: counters, distributed caching, shared sessions, and multi-region data ingest. My employer, Redis Labs, recently announced CRDT support in Redis Enterprise, with conflict-free replicated data types joining the rich portfolio of data structures—Strings, Hashes, Lists, Sets, Sorted Sets, Bitfields, Geo, Hyperloglog, and Streams—in our database product.
14 Things I Wish I’d Known When Starting with MongoDB

MongoDB’s security checklist gives good advice on reducing the risk of penetration of the network and of a data breach. It is easy to shrug and assume that a development server doesn’t need a high level of security. Not so: It is relevant to all MongoDB servers. In particular, unless there is a very good reason to use mapReduce, group, or $where, you should disable the use of arbitrary JavaScript by setting javascriptEnabled:false in the config file. Because the data files of standard MongoDB is not encrypted, It is also wise to Run MongoDB with a Dedicated User with full access to the data files restricted to that user so as to use the operating systems own file-access controls. MongoDB doesn’t enforce a schema. This is not the same thing as saying that it doesn’t need one. If you really want to save documents with no consistent schema, you can store them very quickly and easily but retrieval can be the very devil.
Four key considerations for evaluating graph warehouses
Organizations should also evaluate graph databases in terms of how much reading and writing they’ll require. GOLAP systems mostly read data for query purposes. Since data warehouses are usually batch jobs, their writing capabilities aren’t as important as their ability to swiftly query data for answers. However, the performance of batch loading is crucial. OLTP systems are constantly updating small portions of their transactional data via their writing capacity. For example, tollbooths are continually reading the license plates of vehicles and updating transactional data for passing motorists. Other examples include point-of-sale (POS) checkout systems, either for e-commerce or physical shopping locations. The same data from the tollbooths or consumer checkout is subsequently used by OLAP systems for establishing highway systems improvements, or pricing and marketing options for POS. Another defining attribute of OLTP and OLAP systems is the type of query required. In general, OLTP systems are primed for answering narrow, well-defined questions.
Quote for the day:
"It's very important in a leadership role not to place your ego at the foreground and not to judge everything in relationship to how your ego is fed." -- Ruth J. Simmons
No comments:
Post a Comment