
Oval shaped and available in black or white, the Link 300 has a wrap-around textured mesh grill masking a front-mounted 0.8 inch tweeter and a 3.5-inch woofer, with a large passive radiator in back that’s crucial to that JBL sound signature. The ever-ready Google Assistant wants users to control almost everything by voice. Still, this speaker’s hard plastic and rubbery-surfaced top offers press-deep (not thermal contact) volume and pause/play buttons, as well as the obligatory microphone mute button to tap if you fear Big Brother is listening. Also note the Bluetooth pairing button and a centered home button. Pressing the latter lets you abbreviate a voice command to eliminate the tedium of saying “Hey Google” before calling out a radio station, artist, or action request for news, weather, jokes, movie times, recipes, light switching, door locking, and hundreds of other commands. Although there are just two far-field microphones fitted on the top of the Link 300, they did a good job of hearing my requests, even from across the room.
Cutting through the blockchain hype

“Now, that is very attractive to smaller firms because they have a chance to come together to beat the bigger companies,” he said. “But not so much for the market leaders, without which the blockchain ecosystem won’t spin up fast enough.” Sprenger also touched on the security of blockchain systems that are deemed secure as far as the immutability of information is concerned. However, he said that notion would not apply to data privacy and access management. Citing AdNovum’s Car Dossier project, which uses blockchain as a technological basis to create trust and drive value within the used and second-hand car industry in Switzerland, Sprenger said details such as the location of a car that had been involved in an accident could be captured on a blockchain. “So you have location information and you know who owns the car at a certain point in time – that’s very sensitive information, at least in Switzerland,” he said.
Cloud complexity management is the next big thing

The growing cloud computing complexity was recently documented by the Wall Street Journal that cites a survey of 46 CIOs by KeyBanc Capital Markets. It found that 32 percent said they plan to use multiple vendors to create internal private cloud systems, while 27 percent planned hybrid cloud arrangements. ... Traditional thinking is that cloud computing will replace hardware and software systems, so things will be simpler. You’ll just have to spend a few days moving workloads and data using processes so easy that the applications and data almost migrate themselves. But it turns out to be a complex migration process with many new choices to make and new technology to use. Where you once had five security systems, you now have 20. Where you had three directories, you now have seven. Why? It turns out you cannot just shut down the old stuff, so the hardware, software, and supporting systems remain. At the same time, you are standing up cloud-based systems that used a whole new set of skills and technology. Thus the complexity.
Smart building and IoT technology are highly fragmented

One vendor of automation software for, say, elevators might use a much different data format than the manufacturer of a given building’s HVAC systems, making it difficult to integrate these two critical systems into the same framework. Part of what makes the problem of standardization at the building level so difficult is that most systems currently being used for digital facilities administration were originally designed to perform a wide range of functions. For example, the Green Building XML schema, or gbXML, was created to be a standard format for sharing CAD-based information between different building blueprints, but it’s now in use as a tool for live analysis of energy usage in smart buildings, for example. The centralization of these myriad systems is, nevertheless, underway at the National Institute of Standards and Technology. The “IoT-Enabled Smart City Framework,” or IES-City Framework, that NIST is working on with groups in other countries, is largely a conceptual one at this point, but highlights several potential concrete use cases for more unified standards down the line.
Google remotely alters battery settings on some Android 9 Pie devices
If you are using a beta version of Android, the user license agreement gives Google the right to modify system settings for testing purposes, by way of an update sent "over the air" to your device. However, remotely modifying the system settings of devices running the retail version of Android, without informing the user about what's going on, is a new precedent. Under ordinary circumstances, a user can instruct their Android Pie device to start saving battery juice when it reaches 75 percent capacity. This is supposed to be the highest threshold at which power saving can be enabled. Google's unexpected experiment, however, raised this to 99 percent and turned the feature on without notifying the user. When Android Pie's Battery Saver function gets triggered, several strong measures are enforced to reduce drain: Location Services are disabled if the device is locked, apps no longer refresh with new data in the background, and some notifications won't even show up.
Key steps to ensure data protection amidst the growth of mobile apps

It's likely you already have conventional security measures in place to monitor your organization's network, devices and users. That may or may not extend to mobile users entering your system, and if it doesn't, you'll need to look for mobile solutions specifically. This is where a diagnosis of your mobile framework will come in handy. What kind of policies do you have in place to protect your network and users? Are employees forbidden to download and install applications from third-party mobile app stores, for example? Have you instead decided to issue enterprise-exclusive devices and restrict business-related activities to said platforms only? Additionally, consider what can be done to protect the network from users tapping in. For instance, you might look at separate network access between customers and employees. You might also deploy a joint security monitoring and firewall system that can be used to identify, track and block access to various users based on activity.
Cyber security: A work in progress

Whether it is the lack of skills to deal with increasing threats or the fact that many users still fall for scams and click on malicious links or open suspicious documents, one thing has been constant over the past three years. When asked what the biggest problem is – people, process or technology – the results leave little room for ambiguity as to where the challenge lies, with 82% saying that cyber security is a people problem – consistent with the responses of the previous two years. So, what can we conclude from three years of IISP surveys? The ongoing problem that security teams are trying to solve is clear. New attacks continue to emerge and new vulnerabilities are discovered and patched. Data volumes and technology reliance continue to increase and the burden often falls to a team with roughly the same headcount and budget as the year before.
Europe Catches GDPR Breach Notification Fever

After notifying authorities, many organizations that have suffered a data breach will be instructed to notify victims, or else choose to do so on their own. Because consumers are already seeing a sharp rise in breach notifications, some have voiced concern that it could lead to "breach fatigue" and perhaps a sense of helplessness at their lack of power to control the fate of their data. "There is an argument that we risk people suffering data breach notification fatigue," says Honan, who is also a cybersecurity adviser to Europol, the EU's law enforcement intelligence agency. "However, I would argue that people are better off knowing that their data is at risk so they can take appropriate action to protect themselves. We should also be aware that breach notifications serve to provide not just the individuals affected by the breach details of what happened but also should be used by other organizations to learn from. If we are more aware of the root causes of breaches in other organizations, we can use that information to better secure our own systems."
What is multi-access edge computing, and how has it evolved?
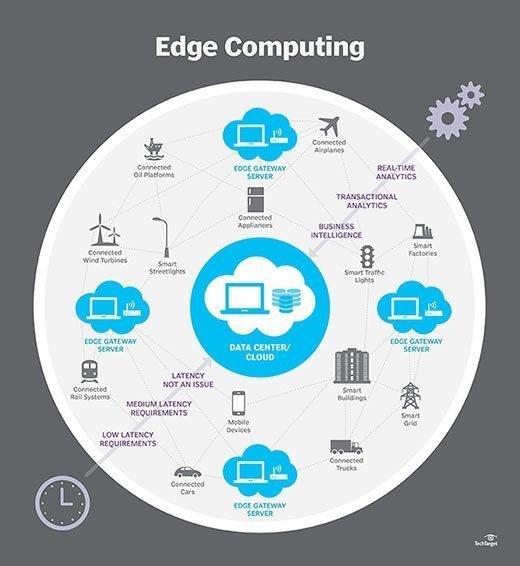
Multi-access edge computing (MEC) is a network architecture that supports compute and storage capacity at the network edge, rather than in a central data center or cloud location. MEC enables rapid and flexible deployment of new applications, and it offers significantly lower latency -- and better performance -- for local applications and data, compared with centralized data center resources. Prototypical MEC applications require ultrafast response times and high availability, and they derive security benefits from localized data flows. MEC provides the intelligence for taking real-time actions and the ability to perform complex data analytics. Applications suited to MEC capabilities include virtual reality, self-driving cars and business-critical IoT applications, all of which require real-time response. Any application that generates a large amount of data can benefit from MEC, as edge computing can make immediate decisions and only transmit aggregate data to central cloud infrastructure, thus significantly reducing network bandwidth requirements.
Hackers wage a new Cold War
The cyber Cold War isn’t just a matter for military and intelligence personnel to ponder. It can easily affect the life of any business. Personal financial information can be stolen and sold for profit by a crime ring, or used to finance a terrorist attack. A company’s intellectual property can be targeted by an industrial rival, or its systems sabotaged, or its stock price manipulated by a fake Twitter account, or its reputation and business relationships ruined through leaks and hoaxes. Citizens can be disenfranchised by hacked voting systems that render polling places inoperable or change recorded votes. Cities can be imperiled by attacks on the electrical power grid, or on the systems controlling large dams, or even on the connected cars and smart homes that fill their streets and neighborhoods. What can you do about it? In our interconnected world, the lines between espionage, war, and business can be all too blurry. If you run a business, work with sensitive data, or work in cybersecurity, you’re already considered fair game—and so are your customers.
Quote for the day:
"Management is efficiency in climbing the ladder of success; leadership determines whether the ladder is leaning against the right wall." -- Stephen Covey
No comments:
Post a Comment