Smart Cities: How They’ll Make Us Healthier
Pollution is inevitable in large cities. However, smart cities will be better equipped to detect pollution and enable experts to reduce it. Already, cities are installing air quality sensors to find out where air quality can be improved, enabling cities to detect sources of pollution that might have gone undetected in the past. Sensors have already revealed that pollution hot spots can occur in unexpected places, and steps taken to reduce air pollution will improve the health of all residents. Smart cities are also better able to tackle water pollution. Sensors can detect where water is being polluted, letting planners uncover where pollution is entering nearby bodies of water. Furthermore, sensors can be installed to detect lead and other pollutants in drinking water on a more fine-grained basis, enabling health officials to act more promptly and prevent infections and poisoning.... Television and radio are often used by cities to provide health information to residents. However, people are increasingly turning to the internet for information, and they might miss out on local health alerts.
RabbitMQ in Microservices
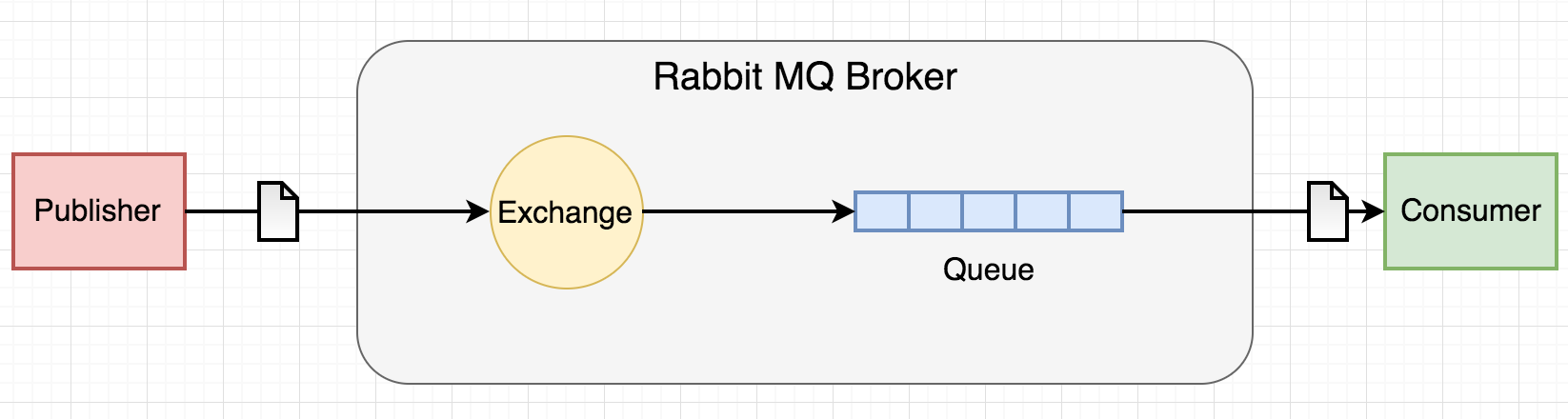
RabbitMQ is one of the simplest freely available options for implementing messaging queues in your microservices architecture. These queue patterns can help to scale your application by communicating between various microservices. We can use these queues for various purposes, like interaction between core microservices, decoupling of microservices, implementing failover mechanisms, and sending email notifications via message brokers. Wherever two or more core modules need communicate with each other, we should not make direct HTTP calls, as they can make the core layer tightly coupled and it will be difficult to manage when there are more instances of each core module. Also, whenever a service is down, the HTTP call pattern will fail, as after a restart, there is no way to track old HTTP request calls. This results in the need for RabbitMQ. In microservice architecture, for this demonstration, we will use an example pattern of sending email notifications via various core microservices. In this pattern, we will have a producer, any of the core microservices, which will generate the email content and pass it on to the queue.
Why Python is so popular with developers: 3 reasons the language has exploded

Python has the best claim to being the fastest-growing major programming language right now, said Stack Overflow data scientist Julia Silge. Developer Stack Overflow visits to Python have grown very quickly, she added: This year, it became the most visited programming language in the world on the site. The rate of growth is high across industries including academia, manufacturing, electronics, finance, energy, tech, and government, Silge said. It's not shrinking in any industry, she added. "The rise of Python is linked to businesses understanding that they are generating all this data all the time, and if they either train people internally or hire people who have these skills, they can use that data to make better decisions, and it can help their businesses thrive," Silge said. "It's a great first programming language to learn, and also it is a center of one of the most impactful trends driving how businesses are adding value to what they're doing right now."
Multi-cloud strategy: Determine the right cloud for your workloads
The skills revolve around managing, configuring and maintaining the different cloud service provider’s environments. So, for AWS it is being able to handle and manage all of the AWS configurations, deployment and features that are being brought in. Same thing for Azure and Google Cloud. It’s setting up the network infrastructure, setting up the firewall, setting up the virtual cloud environments. Each one of the vendors does that in a different way; there’s no one-size-fits-all that will work across all of the environments. My highest recommendation for anybody going into the cloud is automating their environment as much as possible, but the script automations are different in each one of those environments. I can automate building my workload in AWS, but I can’t take that same script and run it in Azure to build my workload environment there.
8 Cryptomining Malware Families to Keep on the Radar

Cryptojacking activities that bleed off victims' compute power to mine for cryptocurrency have skyrocketed, as cybercriminals find it to be one of the most profitable low-key attacks on the Web today. It has even pushed out ransomware as cybercriminals' favorite means of raking in cash. While cryptomining malware may not be calibrated specifically to steal data, it should remain on the radar of enterprise defenders. Campaigns carried out by these malicious tools do real damage to computing equipment and siphon off vast amounts of electricity, never mind the fact that their infections are the perfect foothold to carry out other kinds of devastating lateral attacks. Here are some of the most prevalent and powerful cryptomining malware families active today. Ericka Chickowski specializes in coverage of information technology and business innovation. She has focused on information security for the better part of a decade and regularly writes about the security industry as a contributor to Dark Reading.
Alternatives to Nmap: from simple to advanced network scanning

There are alternatives – not many – that range in technical sophistication from tools with GUIs that can ease you into performing the essentials of network maintenance to more advanced software that is similar to Nmap itself. ... You don't need to install either one on a computer. Each is an executable that you can launch right away, running from a USB flash drive, for example. Advanced IP Scanner is designed to scan LANs. Through its GUI, it shows you all the computers and other devices connected to your LAN. Scan results can be exported to a CSV file. You can also access shared folders on a computer or device, control them remotely (using RDP and Radmin), or shut down a computer or device. Advanced Port Scanner scans for open ports on network computers and other devices, and it shows any version information it finds for programs running on detected ports. Commands can be executed on remote computers or devices, and resources can be accessed from them via FTP, HTTP, HTTPS or shared folders. As with Advanced IP Scanner, you can remote-control a computer or device on the network using RDP and Radmin, or you can shut it down.
What is Microsoft’s Intune – and how well does the UEM tool really work?

Intune is designed to give IT admins an easy way to manage a variety of devices – whether corporate or personal – in a way that protects corporate data while still allowing employees to get their jobs done. It combines mobile device management (MDM) capabiltiies with mobile application management (MAM) features and puts them all in a single console. Though obviously tied to Windows 10 and other Microsoft products, it is designed to manage hardware running other operating systems. Intune's arrival seven years ago came as companies were being forced to manage a sudden onslaught of devices accessing corporate data and networks – fallout from the bring-your-own-device (BYOD) trend that took off after the release of Apple's iPhone in 2007. "Even if the workers are not mobile all the time, the way we do business today requires a different approach, and that's where Intune comes in," said Maura Hameroff, Microsoft's director of security product marketing. As a subscription service, Intune charges companies on a per user/per month basis. It can be purchased as a stand-alone product for $6 per seat or for $8.74 per seat as part of Microsoft's Enterprise Mobility Suite
Scaling Business Agility: Three Essential Pillars for Being Vs. Doing Agile
If each business unit within an organization operates as a separate function, this has to be the first candidate for transformation. Even before we align the cadence and processes, it’s important to ensure everyone understands the purpose of working together. System thinking evolves as we help the team understand the vision and purpose. Top management must be aligned before a team gets involved. Transparency and working agreements within and across teams are vital in building a healthy culture. It’s at all levels, not just top or middle management. This is about enabling and adding value at every level in the ecosystem. It starts with product management who plays a crucial role in identifying and communicating value to the entire stream. From Engineering and Support to Program Management and Sales, everyone has a role to play in the value ecosystem. Those leaders must be identified and nurtured by management and the leaders need to hone their skills, not just to show or lead, but to be part of the journey.
Are You the Barrier to Innovation?

Risk aversion gets embedded in a culture and often reflected in structure, unspoken values, and the architectures that support it. Such architectures are heavily redundant, often held in datacenters controlled by the organization, monitored to within an inch of life (which can also lead to the Sisyphean chore of wringing out every ounce of performance), and protected by layers of security and abstraction. The goal is stability, but its price is stagnation. The fear of additional complexity also leads to risk aversion in trying new technologies even for small, non-critical projects. All too often, these projects can grow into core pieces of functionality that other systems rely on. An organization with an agile mindset will isolate such systems and abstract their functionality behind an API, but traditional IT operations would prefer to avoid them completely as they require knowledge dependencies that complicate the hiring process and add to the list of expertise the team must gain.
7 Costly Mistakes Entrepreneurs Make in The Digital World

In theory, SEO is very simple. Find and use the right keywords and Google will rank it near the top of any searches--thus making your business easily found by potential customers. But like many things, while the theory is simple and straightforward, the practical implementation of it is anything but. The rules for SEO are constantly changing and the internal workings can often be complex enough to give even Einstein a headache trying to figure it out. And once you have figured it out, you need to get the balance right between not enough SEO and too much SEO. Unless your business is SEO, then you're not going to have the skills to keep up, nor the time to divert from your core business to deal with it. A bit like plumbing, it seems easy, but it's much easier to get an expert in than it is to clear up the potentially costly mess getting it wrong. If you want to get your website found, then you need to make sure that you have the right keywords. These are the words or phrases that people are searching for on Google. The better your SEO keywords, the higher your business will rank.
Quote for the day:
"You have to lead people gently toward what they already know is right." -- Phil Crosby

No comments:
Post a Comment