
Everyone in an organisation who is connected to the internet should be given general cyber security training. This is “definitely lacking,” says Wool. As phishing scams – among others – surge, the untrained employee remains a constant risk to the security of their company. The level of training needs to be improved, because currently “there is a poor understanding of the basics of the threat landscape,” according to Wool. “This is something that should be taught in elementary schools. When children learn how to use Excel, PowerPoint and Google, it makes sense for them also to be trained on basic safety rules, just like crossing the street.” ... “A lot can be done and it can be effective, but it takes a very long time to put together,” explains Wool. “Think: how long did it take the human race to figure out what needs to be done to make vehicle transportation reasonably safe. Think about sidewalks, zebra crossings, highway exit and entry ramps and so on. It took 100 years from the invention of the automobile to where we are now. When it comes to safety, we can always do better.”
Multi-Clouds And Composable Infrastructure At VM World
One important trend at VM World and leading up to the show was a focus on software defined infrastructure, including what is called composable infrastructure, that allows virtualizing and addressing individual components, such as storage devices. Before VM World, Dell EMC announced their PowerEdge MX, a high performance, modular infrastructure solution that the company said will easily adapt to future technologies and server disaggregation (a term often used in composable infrastructure). Dell EMC says that the system’s kinetic infrastructure is “uniquely designed without a mid-plane, enabling support for multiple generations of technology releases—processor technologies, new storage types and new connectivity innovations—well into the future. Specifically, the absence of a mid-plane enables direct compute to I/O module connections, allowing for future technology upgrades without disrupting customer operations and without a mid-plane upgrade.
To build a roadmap to digital transformation, more often than not companies are looking into the future, attempting to visualize where they want or need to be in twenty years, and planning backwards. For many however, a more proactive approach to planning would be to accept that “You can't know where you're going without knowing where you are now." We often talk to companies who have predictive and preventative aspirations but who still don’t have machines networked, the necessary IT infrastructure to capture and aggregate machine data, or the internal organizational resources required to decipher the data and implement continuous process changes. This roadmap should actually be quite logical at its core: let’s become as capable as we can and have all our ducks in a row to ready ourselves for the greater journey ahead. Once we’ve optimized capability, it’s time to digitize our assets, visualize our manufacturing data in real-time, and measure the success of our KPI’s using our tools.
Fintech companies: The ideal talent pool for banks?
Partner up with fintech companies so you can leverage their talent pool. Thailand’s Bank of Ayudhya (BAY), for example, has forged relationships with 25 fintech companies so far, and expects that number to rise to 40 by the end of the year. Other banking giants in Thailand are using the same strategy. Bangkok Bank’s Executive VP Kukkong Ruckphaopunt told local media that the partnership model is a key strategy for acquiring tech talent. Wirawat Panthawangkun, Senior Executive VP of Kasikornbank, said KBank too is using a similar strategy to invest in tech firms to scout out tech talent from around the world. Banks and financial services institutions in other parts of Asia are following suit — except China who produces eight million computer science graduates every year and only needs the occasional innovator or thought leader to accelerate its tech growth.
What hiring managers want to see in data scientists’ CVs

Some candidates focus on who they reported to, others focus on the accuracy and/or complexity of the models they built, while others only mention the types of projects they worked on. ... My ethos, which is essential in a commercial environment, is to always start with the simplest possible model and only optimise and/or add complexity if/as required. This is precisely what the Lean Startup framework mandates and is precisely what we do in my Data Science team at Royal Mail. This is because you would usually hit diminishing returns as you continue to optimise and/or add complexity to a model, and the key is to know when your model is good enough to have a tangible business impact, and then deliver it, realise the value and move on to the next most crucial problem. So ideally, in the work experience section of the CV, I would like to see multiple impact statements, at least one for each Data Science role the candidate has held. This would give me confidence that the candidate has good commercial awareness and is worth investing in, as I can expect a good ROI.
Microservices in a Post-Kubernetes Era

On cloud native platforms, observability is not enough. A more fundamental prerequisite is to make microservices automatable, by implementing health checks, reacting to signals, declaring resource consumption, etc. It is possible to put almost any application in a container and run it. But to create a containerized application that can be automated and orchestrated effectively by a cloud-native platform requires following certain rules. Following these principles and patterns, will ensure that the resulting containers behave like a good cloud-native citizen in most container orchestration engines, allowing them to be scheduled, scaled, and monitored in an automated fashion. Rather than observing what is happening in a service, we want the platform to detect anomalies and reconcile them as declared. Whether that is by stopping the directing of traffic to a service instance, restarting, scaling up and down, or moving a service to another healthy host, retrying a failing request, or something else, this doesn’t matter.
Card-Skimming Malware Campaign Hits Dozens of Sites Daily
Websites don't necessarily catch on quickly after an infection. "The average recovery time is a few weeks, but at least 1,450 stores have hosted the magentocore[dot]net parasite during the full past six months," de Groot writes. Attackers often execute a brute-force attack against a Magento control panel, de Groot says. And attackers are clever: Their code can remove other malicious code that's already in a Magento installation and is also designed to hide its tracks. The malicious code does that via a backdoor included in a cron.php file placed by attackers periodically downloads "malicious code, and, after running, delete itself, so no traces are left," he writes. The code also changes the password for registered Magento users to "how1are2you3," de Groot writes. ... It's best to nuke infected installations and restart, he says. "Revert to a certified-safe copy of the codebase, if possible," de Groot writes. "Malware is often hidden in default HTML header/footers, but also in minimized, static JavaScript files, hidden in deep in the codebase."
A glimpse into the dark underbelly of cryptocurrency markets
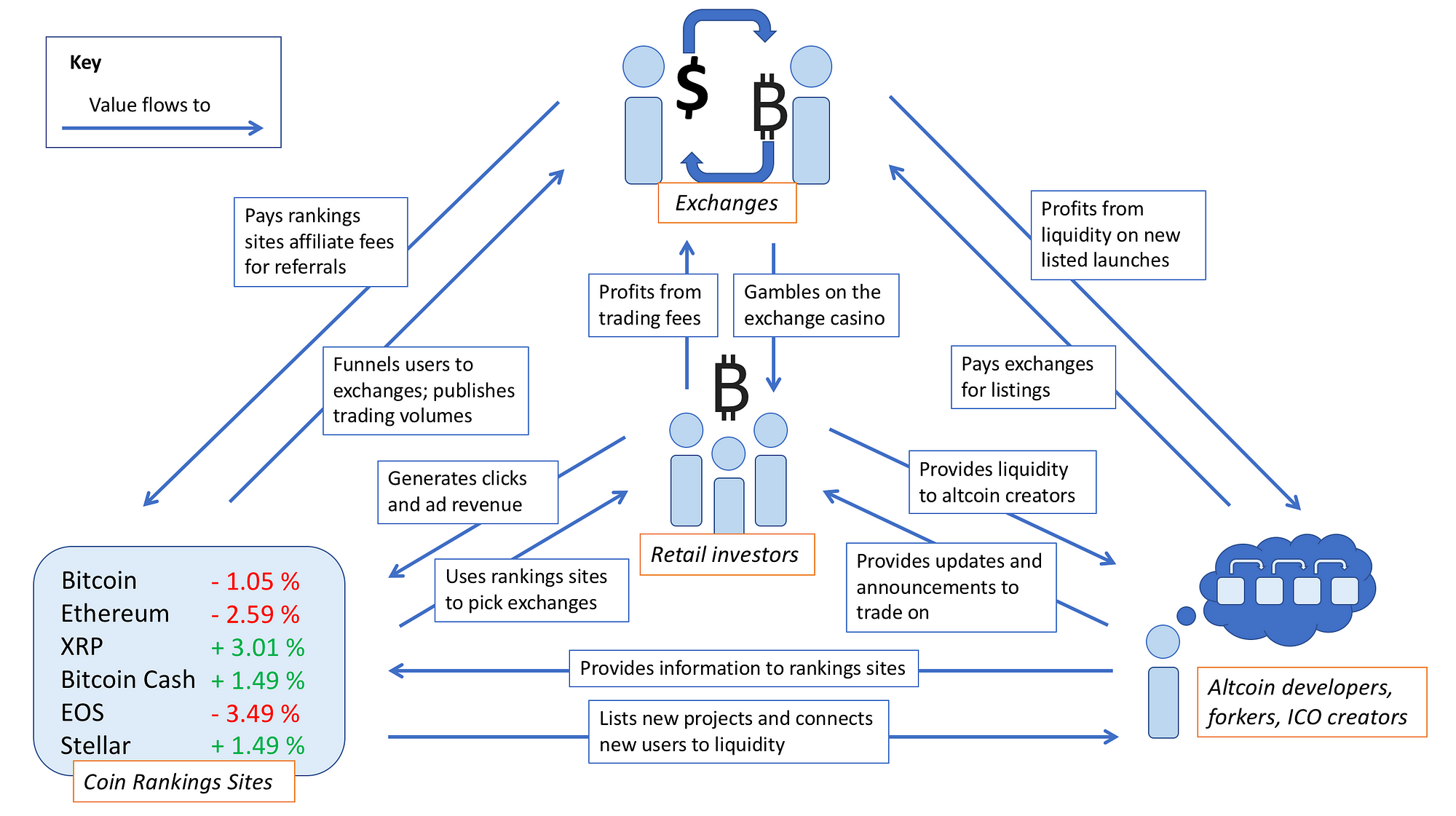
What is the business model of the coin rankings sites? Sites like CoinMarketCap, CoinGecko, CoinRanking, Cryptoslate, CryptoCoinRankings, CoinCodex, CryptoCoinCharts, (et al.) sell ads, and in some cases, insert affiliate links to the exchanges. Some of them will sell blended pricing APIs to more sophisticated traders who want a reliable price feed. Many if not most exchanges have affiliate schemes, and referral links (“reflinks”) can be a lucrative source of revenue if you are the intermediary between active traders and exchanges. Sometimes rankings sites win doubly by accepting payment for banner ads for exchanges or trading venues, and then including their own affiliate links in the ad itself. It’s good money if you can get it. Investors go to these sites to find links to exchanges where they can trade their coins of choice, especially if they are smaller projects and do not have many points of liquidity. Since the rankings sites are the ports of call for investors, they have an almost captive audience and can easily monetize with an affiliate link.
Bitcoin Gold delisted from major cryptocurrency exchange after refusing to pay hack damages

The hack at the center of this dispute took place between May 18 and 22, according to an incident response report published this May. The BTG team says the hack was a combination between a 51% attack and a double-spend attack. BTG experts said hackers rented servers through the NiceHash cryptocurrency mining market to overwhelm the Bitcoin Gold network and take control of more than half the BTG network computational hashrate. This is what cryptocurrency experts call a "51% attack," a dangerous scenario that grants attackers the ability to modify transaction details on the entire Bitcoin Gold network. The BTG team says that during the 3.5 days attackers overwhelmed the Bitcoin Gold network, hackers deposited large quantities of Bitcoin Gold funds at cryptocurrency trading platforms. Seconds after these deposits, hackers would convert the funds into another cryptocurrency and transfer the money to new accounts at other exchanges.
Google and Mastercard cut a secret deal to track retail sales data
A Google spokeswoman declined to comment on the partnership with Mastercard, but addressed the ads tool. "Before we launched this beta product last year, we built a new, double-blind encryption technology that prevents both Google and our partners from viewing our respective users’ personally identifiable information,” the company said in a statement. “We do not have access to any personal information from our partners’ credit and debit cards, nor do we share any personal information with our partners.” The company said people can opt out of ad tracking using Google’s “Web and App Activity” online console. Inside Google, multiple people raised objections that the service did not have a more obvious way for cardholders to opt out of the tracking, one of the people said. Seth Eisen, a Mastercard spokesman, also declined to comment specifically on Google. But he said Mastercard shares transaction trends with merchants and their service providers to help them measure "the effectiveness of their advertising campaigns.”
Quote for the day:
"Stressing output is the key to improving productivity, while looking to increase activity can result in just the opposite.” -- Paul Gauguin

No comments:
Post a Comment