Deep Neural Networks Help to Explain Living Brains
Artificial neural networks are built with interconnecting components called
perceptrons, which are simplified digital models of biological neurons. The
networks have at least two layers of perceptrons, one for the input layer and
one for the output. Sandwich one or more “hidden” layers between the input and
the output and you get a “deep” neural network; the greater the number of
hidden layers, the deeper the network. Deep nets can be trained to pick out
patterns in data, such as patterns representing the images of cats or dogs.
Training involves using an algorithm to iteratively adjust the strength of the
connections between the perceptrons, so that the network learns to associate a
given input (the pixels of an image) with the correct label (cat or dog). Once
trained, the deep net should ideally be able to classify an input it hasn’t
seen before. In their general structure and function, deep nets aspire loosely
to emulate brains, in which the adjusted strengths of connections between
neurons reflect learned associations. Neuroscientists have often pointed out
important limitations in that comparison: Individual neurons may process
information more extensively than “dumb” perceptrons do, for example, and deep
nets frequently depend on a kind of communication between perceptrons called
back-propagation that does not seem to occur in nervous systems.
Future of Corporate Governance Through Blockchain-powered Smart Companies
In essence, Smart Company is an entirely new form of business type (LTD., IBC)
except it rivals all traditional models by being fully automated by blockchain.
And certainly, it makes just that big of a difference. When you have the ability
to run your business in a structure that is legally compliant yet all its
transactions happen in real-time and are verified directly on the blockchain,
this changes the game. What this means for business owners is that managerial
ownership structures become more transparent. Corporate voting is easier, more
accurate and secret strategies such as ‘empty voting’ become more difficult to
execute. The ability to have corporate shares as ERC-20 tokens modified for
security laws offers the means to assert and transfer ownership and liabilities
of real-world assets with actual value. Just to give you a rough understanding
of the magnitude of this untapped potential, it has been estimated that the
total value of illiquid assets, including real estate, gold., is no less than
$11 Trillion . Roughly the nominal GDP of China, the world’s second largest
economy today. For shareholders, Smart Company model offers nearly free trading
and transparency in ownership records while simultaneously showing real-time
transfers of shares from one owner to another.
Agile development: How to tackle complexity and get stuff done

Holt believes his key role as CTO is to create a culture in the organisation
where his people feel comfortable and confident to try new things. Rather than
being scared of risk-taking, he says tech leaders should encourage their IT
professionals to innovate and develop customer-centred products and services
in an iterative manner. "Those are the kind of people who aren't afraid of the
complexity, who are able get in amongst it, and that's where you get really
good solutions," he says. Holt says engaging with a challenge involes great
teamwork. He says his organisation is always on the lookout for people who
have an ability to manage complexity and the solution often involves agility
in organisational culture as well as product development. ... Danny Attias,
chief digital and information officer at British charity Anthony Nolan, says
tech executives looking to deal with complexity must ensure they're working to
create a joined-up organisation. More often than not, that means using Agile
principles to break down problems into small parts that can be managed
effectively across the organisation. "My career has been about decoupling
dependencies wherever you possibly can," he says.
The world needs women who code
A lot of women are not aware of the power of IT. The industry’s reputation as
a boy’s club belies the fact that women are actually rising in many technology
fields, both in number and in title. They may think they have to already know
a bunch of code to get started. It's likely that many women simply don’t
realize how much opportunity there is for them, even as beginners. A slightly
different, yet related, reason is fear. Because of the percentage of men in
this field, some women may feel that there will be too much competition, that
they won’t be able to measure up against men with experience, or that they'll
be overlooked for men without experience. But nowadays, IT companies are
making strong efforts to welcome and support women, conducting various
programs to encourage women to learn about various tech disciplines, and
provide pathways for them to join the industry. And whenever a woman joins
this industry, it gives a boost of confidence to other women too. I constantly
get inspired by the many women I know that are doing amazing things in tech.
... Admittedly, coding can seem overwhelming in the beginning, but don’t
worry—it’s like that for almost everyone. Soon enough, what seems like
gibberish at first starts to come together, and you learn to harness it to
make things work and accomplish tasks.
Kafka at the Edge — Use Cases and Architectures
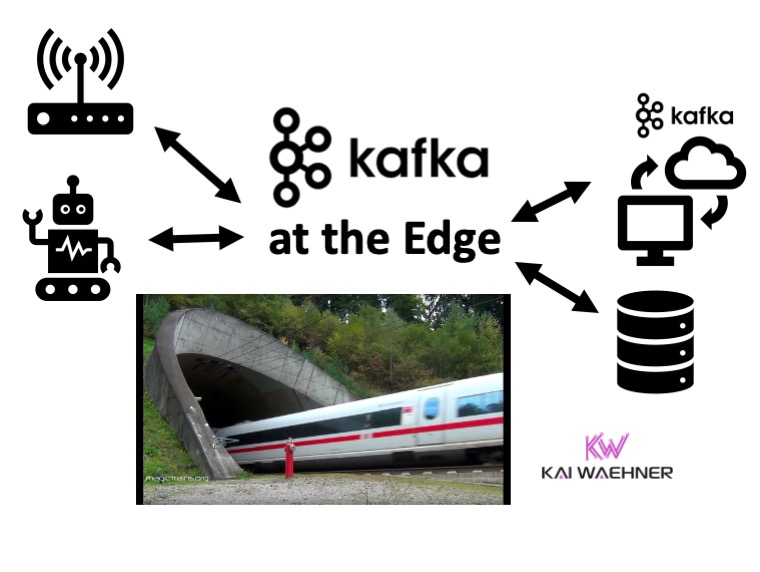
Event streaming with Apache Kafka at the edge is not cutting edge anymore. It
is a common approach to providing the same open, flexible, and scalable
architecture at the edge as in the cloud or data center. Possible locations
for a Kafka edge deployment include retail stores, cell towers, trains, small
factories, restaurants, etc. I already discussed the concepts and
architectures in detail in the past: "Apache Kafka is the New Black at the
Edge" and "Architecture patterns for distributed, hybrid, edge and global
Apache Kafka deployments". This blog post is an add-on focusing on use cases
across industries for Kafka at the edge. To be clear before you read on: Edge
is NOT a data center. And "Edge Kafka" is not simply yet another IoT project
using Kafka in a remote location. Edge Kafka is actually an essential
component of a streaming nervous system that spans IoT (or OT in Industrial
IoT) and non-IoT (traditional data-center/cloud infrastructures). The post's
focus is scenarios where the Kafka clients AND the Kafka brokers are running
on the edge. This enables edge processing, integration, decoupling, low
latency, and cost-efficient data processing. Some IoT projects are built like
“normal Kafka projects”, i.e., built in the (edge) data center or cloud.
How smartphones became IoT’s best friend and worst enemy

Relying on the ubiquity of smartphones and the rise of remote controls, users
and vendors alike have embraced the move away from physical device interfaces.
This evolution in the IoT ecosystem, however, brings major benefits AND
serious drawbacks. While users enjoy the remote capabilities of companion apps
and vendors bypass the need for hardware interfaces, studies show that they
present serious cybersecurity risks. For example, the communication between an
IoT device and its app is often not properly encrypted nor authenticated – and
these issues enable the construction of exploits to achieve remote control of
victim’s devices. It is important to explain that connected devices have not
always been this way. I’m sure others like myself do not need to cast their
minds far back to remember a time when smartphones did not even exist. User
input during these halcyon days relied on physical interfaces on the device
itself, interfaces that typically consisted of basic touch screens or two-line
LCD displays. Though functional, these physical interfaces were certainly
limited (and limiting) when compared to the applications that superseded them.
Devices without physical interfaces are smaller, consume less power, and look
better.
Singapore government rolls out digital signature service

Called Sign with SingPass, the service is being rolled out by Assurity, a
subsidiary of the Government Technology Agency (GovTech), together with
eight digital signing application providers, including DocuSign, Adobe and
Kofax. GovTech said each digital signature is identifiable and
cryptographically linked to the signer, while signed documents are platform
agnostic and can be viewed with the user’s preferred system. No document
data will be transferred during the digital signing process. Assurity will
also issue digital certificates for signatures created under the service.
Upon Assurity’s accreditation under Singapore’s Electronic Transactions Act,
signatures made with the service will be regarded as secure electronic
signatures. GovTech said the service will be useful for organisations and
their customers amid the growing number of online transactions and will test
the service with the Singapore Land Authority (SLA) for the digital signing
of property caveats in the coming weeks. Kok Ping Soon, chief executive of
GovTech, said the high security document signing service will help
businesses save cost and manpower by alleviating the need to manually verify
physical paperwork.
Is your approach to data protection more expensive than useful?

With the recent increase in cyberattacks and exponential data growth,
protecting data has become job one for many IT organizations. And in many
cases, their biggest hurdle is managing an aging backup infrastructure with
limited resources. Tight budgets should not discourage business leaders from
modernizing data protection. Organizations that hang on to older backup
technology don't have the tools they need to face today's threats. Rigid,
siloed infrastructures aren't agile or scalable enough to keep up with
fluctuations in data requirements, and they are based on an equally rigid
backup approach. Traditional backup systems behave like insurance policies,
locking data away until it's needed. That's like keeping an extra car
battery in the garage, waiting for a possible crisis. The backup battery
might seem like a reasonable preventive measure, but most of the time, it's
a waste of space. And if the crisis never arises, it's an unnecessary
upfront investment, making it more expensive than useful. In the age of
COVID-19, where cash is king and on-site resources are particularly limited,
some IT departments are postponing data protection modernization, looking to
simplify overall operations and lower infrastructure costs first. That plan
can block a company's progress.
Taking Control of Confusing Cloud Costs
It’s difficult to compare services across multiple clouds, because each
provider uses different terminology. What Azure calls a ‘virtual machine’ is
called a ‘virtual machine instance’ on GCP and just an ‘instance’ on AWS. A
group of these instances would be called ‘autoscaling groups’ on both Amazon
and GCP, but Scale Sets on Azure. It’s hard to even keep up with what it is
you’re purchasing and whether there is even an alternative cloud comparable
service, as the naming convention is different. As outlined above in regards
to the simple web application using Lambda, it would be very time consuming
for someone to compare what it would cost to host a web application in one
cloud versus another. It would take technical knowledge of each cloud
provider to be able to translate how you could comparably host it with one
set of services against another before you even got into prices. Cloud
pricing uses an on-demand model, which is a far cry from on-prem, where you
could deploy things and leave them running 24/7 without affecting the cost
(bar energy). In the cloud, everything is based on the amount of time you
use it, either on a per hour, per minute, per request, per amount or per
second basis.
Five ways to avoid digital transformation fatigue
Change fatigue stems from uncertainty and a lack of clarity around the
strategic intent and implementation of the program. Too often,
digitalisation and new tools are being taken into the company without proper
project planning and thinking about how the benefits will be explained to
the employees. Have a deep-dive into the thinking of the value proposition
narrative before the new digital tool is implemented. Start by finding out
if the management and leadership teams are aligned on the transformation's
strategic intent and outcomes. If not, then you need to go back to the
drawing board. This should ideally map out clear target business outcomes as
well as the impact of the transformation to the people, processes, and tools
of what’s happening and how it will affect them. Many workers might feel
that they should be doing their 'actual job' instead of learning how to
navigate with something that they are not sure will benefit them. Be ready
to present to each role the necessities of the new tool, and avoid
explaining it so that it sounds like the company is the only one that will
benefit from it. Incentives for the employees should be clearly stated
before the change starts.
Quote for the day:
"Don't just see what others do to you. Also see what you do to others." -- The Golden Mirror
No comments:
Post a Comment