
The banking CFO’s future looks promising, but there are barriers to success. Banks have been relatively late adapters of some important new technologies; for example, nearly half (43%) of banks told us they do not have a cloud strategy in place or have only started to implement basic cloud practices. Bank CFOs often need to work around a legacy architecture that hampers access to big data and makes it more difficult to plug in analytics, perform stress-testing and satisfy regulatory demands for high-quality, comprehensive data. The to-do list for banking industry CFOs is a long one – they must demonstrate the benefits of technology in their own functions, recruit data scientists and other needed talent to new roles in finance, and champion innovation throughout the organization. But, as respondents told us, there has never been a more exciting time to work in finance. The digital transformation of banking should position CFOs not only as trusted advisers but as the developers of new sources of value for their organizations.
An Interview with Greg DeArment, Head of Infrastructure at Palantir
Modern applications are developed to run in “containers”, a way of packing applications and necessary dependencies in a portable, standardized format. This makes deploying easier and more repeatable across environments than deploying software directly on bare bones operating systems. Enterprise architects and developers are probably familiar with the container solution Docker, but there are many others and even a standard for containers called OCI for Open Container Initiative (OCI). Whatever the container solution, there is a need for better orchestration and management of the containers. This is where Kubernetes comes in. ... Most open-source compute platforms today, such as Hadoop Yarn, lead to a trade-off between security and robustness of the toolset users have at their disposal to empower their business. With Kubernetes, we can enable Foundry users to work with the tools of their choice without compromising the security posture of the platform and putting at risk the security of our customers’ data.
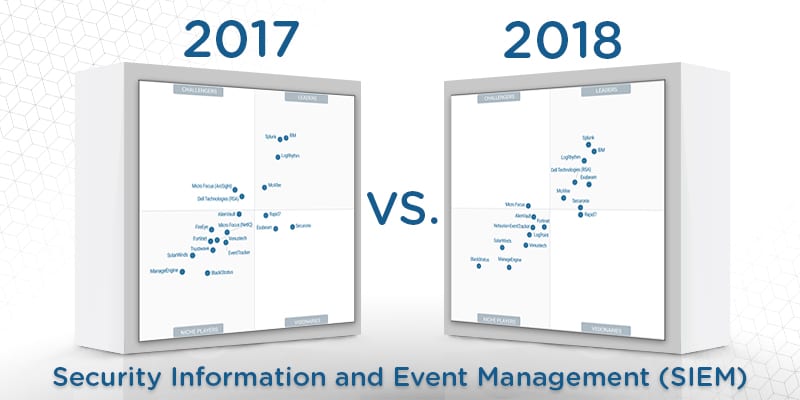
Gartner readjusts its Magic Quadrant evaluation criteria, usually in response to market changes, each year. Therefore, vendors who appeared in the MQ report one year may not return for the next one. By the same token, vendors who once did not make the cut in a previous report may find themselves on the next iteration. Gartner’s states in its report that a vendor’s appearance or disappearance from the quadrant is not a reflection of a change in quality or in opinion, but simply a result of market changes and updated inclusion criteria. LogPoint made the cut for the 2018 SIEM Magic Quadrant, having met all of Gartner’s inclusion criteria. By the same token, three vendors who previously appeared did not meet the inclusion criteria in this year’s report. Gartner excluded Trustwave and FireEye, as both vendors shift focus from SIEM to managed services and platforms. In addition, Micro Focus (NetIQ) Sentinel lost Gartner’s coverage as the vendor focuses on its ArcSight product instead.
Warding off security vulnerabilities with centralized data
Centralizing information also means that no information should be stored on local devices. USB keys are one of the biggest offenders. These devices are often lost or stolen. In late 2017, a USB stick with highly confidential Heathrow Airport security data was found on the street. The drive’s files included detailed airport security and anti-terror measures. Moreover, people tend to use USB keys that they’ve gotten for free from conferences. It’s possible that these devices have been intentionally infected with viruses. A security event in Taiwan recently awarded quiz winners USB sticks that contained malware designed to steal personal information. That’s not all, the list of USB drive-related incidents goes on. There is also the possibility that your phone or laptop will be lost or stolen. Those odds become even greater when you’re traveling or running between meetings, events, and other appointments. If you have all of your files saved directly on your physical laptop or phone, you’re presented with an obvious problem.
Network Innovation or Iteration? – A Matter of Perspective

Enterprises have taken notice of what the web scale providers, like Amazon, are achieving, and want to duplicate those strategies. The problem is, most companies do not have teams of developers to build custom network infrastructures, nor the resources to support them. In addition, the network traditionally is not included as a key part of the core business plan. Rather, the network is just one of many tools in IT’s toolbox, often deployed ‘out of the box’ and relied upon to perform and support the demands of the business. So, while they want the same network agility and manageability the web scale companies enjoy, enterprises struggle to achieve agility and performance based on the available iterations of technology presented to them by known vendors. In addition, network innovation presents an exceptional challenge due to the silos created around network roles and the need for IT staff to manage the network. Because of this isolation, it is easier to pass through iterative solutions as new and continue the cycle of inefficiency.
New chip techniques are needed for the new computing workloads

Intel has designed a new approach. Called Foveros, it allows many different chips built with different technology “nodes” and of different functionality to be stacked on top of each other with very fast communications between them. It also has sufficient power and heat transfer to make the resulting device nearly as effective as a monolithic chip. This type of technology has always been attractive, but it’s only now that Intel has found a way to make its performance and cost of manufacture competitive. ... Some would say Intel is moving down this route because it lost its once two- to three-year advantage in process technology to more nimble players (e.g., TSMC). Certainly Intel has much to do to fix its process manufacturing problems. But many future chips will need circuits that don’t always lend themselves to the most modern process (e.g., FPGAs for AI programming, non-volatile memories, Input/Output and communications/5G), nor do well being embedded in massive monolithic system chips.
Does AI Truly Learn And Why We Need to Stop Overhyping Deep Learning

Whether neural network, Naïve Bayes or simply linear regression, data scientists train their machine learning models on carefully constructed piles of training examples then claim their algorithms have “learned” about the world. Yet, machine learning is in reality merely another form of machine instruction, different from purely expert manual coding of rules, but still guided, with the algorithms and workflows manually tuned for each application. Why does this matter? It matters because as we increasingly deploy AI systems into mission critical applications directly affecting human life, from driverless cars to medicine, we must understand their very real limitations and brittleness in order to properly understand their risks. Putting this all together, in the end, as we ascribe our own aspirations to mundane piles of code, anthropomorphizing them into living breathing silicon humans, rather than merely statistical representations of patterns in data, we lose track of their very real limitations and think in terms of utopian hyperbole rather then the very real risk calculus needed to ensure their safe and robust integration into our lives.
How Governments Are Adopting Blockchain and AI In Advanced Economies

The government of Denmark is looking into the use of AI and the blockchain in digital identity, healthcare, business support and its welfare system. Denmark is one of those countries which have ensured that most of its service provision to citizens is done digitally. Indeed, 90% of Denmark’s governmental services are already being done digitally (Basu, 2017). But the people want more. Danish citizens are demanding even faster response and delivery times for government services. Denmark is also being forced into the blockchain evolution by the country’s population demographics. Denmark’s ageing population means that fewer younger people are available to get into the public service. Therefore, this is a classical case where augmentation of the human workforce using the blockchain and AI is desirable. For Denmark, this has become a necessity, even though it can be quite controversial. Denmark has a welfare system which caters to retirees, vulnerable groups and pensioners.
Brute force and dictionary attacks: A cheat sheet

Brute force attacks involves repeated login attempts using every possible letter, number, and character combination to guess a password. An attacker using brute force is typically trying to guess one of three things: A user or an administrator password, a password hash key, or an encryption key. Guessing a short password can be relatively simple, but that isn't necessarily the case for longer password or encryption keys—the difficulty of brute force attacks grows exponentially the longer the password or key is. The most basic form of brute force attack is an exhaustive key search, which is exactly what it sounds like: Trying every single possible password solution (i.e., lowercase letters, capital letters, numbers, and special characters) character by character until a solution is found. Other brute force methods attempt to narrow the field of possible passwords by using a dictionary of terms (which is covered in more detail below), a rainbow table of precomputed password hashes, or rules based on usernames or other characteristics known about the account being targeted.
Practical CIO: Agility, speed, and business alignment
IT leadership is becoming proficient in all aspects of the business, whether it's marketing, whether it's HR, whether it's legal, whether it's advertising, whether it's the medical side. You have to become knowledgeable on how to apply that technology to get those wins and put game changers, from an IT standpoint, into the business so that you get future growth, you get further merger and acquisitions, scalability and flexibility but, at the same time, keeping it easy and simple. Typically, it's through research. It's peers, other CIOs across the industry, in other industries as well and, in my background, I've been in several different verticals within IT and in leadership, so transportation, retail, insurance, and so bringing that background, some of that background, that experience within healthcare. IT is IT, but how you solve those problems, I think you can bring experience and expertise. You can apply those and get wins in other verticals as well.
Quote for the day:
"Increasingly, management's role is not to organize work, but to direct passion and purpose." -- Greg Satell
No comments:
Post a Comment