The India Enterprise Architecture Framework, aptly called IndEA, was formally notified by the Government of India as a national standard. Needless to mention, for me the journey from development to notification has been challenging and extremely fulfilling at the same time, both at a professional and personal level. Ever since the success of ePragati in Andhra Pradesh, many Ministries, States, Departments, and other public sector entities have shown growing interest in Enterprise Architecture. The elevation and notification of IndEA as a national standard is absolutely a move in the right direction to accentuate and accelerate such activities. The rise of IndEA as a framework will trigger a flurry of activities across the entire ecosystem from consulting firms, system integrators, accredited training providers, to the professional architect community-at-large.
“Ultimately, the goal of the FRP [Facial Recognition Pilot] is to identify if facial recognition technologies can be of assistance to the USSS in identifying known subjects of interest prior to initial contact with law enforcement at the White House Complex," it says. At the moment, the FRP is restricted to only identifying staff that have volunteered to test the technology. Cameras have been set up in two locations that will capture images of people walking along the public streets and parks next to the White House. The images of the faces captured in the video feed will be matched against a database containing the faces of the volunteers. Only pictures that correspond to a positive match will be kept, negative matches will be deleted automatically. A match will send an alert to the USSS, where it will be confirmed by staff. DHS said it would be transparent about its process and has provided a public notice and written notice to volunteers. After the tests have been carried out, the faces kept on the database will be deleted.

Transactions made via blockchain technology cannot be manipulated, hidden or hacked, as the technology is not controlled by centralized financial institution or governments. In order for its authenticity to be compromised, almost the entire network of hundreds of thousands of individually operated nodes, distributed all across the world, would need to be coordinated and altered at the same time. Additionally, the encryption technology feature of blockchain ensures both privacy and verifiability simultaneously on the public audit trail. The Feb-2018 McAfee Report, estimates that cybercrime is on course to costing the world $600 billion in 2018. ... While existing financial services providers have enjoyed an oligarchy over the secure payments industry for over a decade, the technological mechanisms they employ have remained essentially the same during that period. This lack of development has made them vulnerable to cybercrime, which drives up the regulatory costs and is reflected in the consumer’s fees.
Code Churn — A Magical Metric for Software Quality
While designing test plans, the basic question to ask would be to find out what code changes are done in the software. There are multiple contexts to this; one is from the functional perspective and another from a code perspective. The functional perspective would help to do black box testing. If you understand the functionality well and what has been changed in the current feature, then it would be easy to come up with an effective test plan to test the modified functionality. However, in legacy or enterprise level software, it is not sufficient. The code written to change or add a functionality would have many side effects, like: Direct dependent code; Reused code; and Business rules changing, especially various code paths. In such cases, black box testing would not be enough. It is important to know the code churn
Why the fast pace of IT is outpacing project management
The success of agile methods taught us that software development processes are better when they are adaptable to variables such as the ever-changing technology landscape or the need to pivot around product-market fit. The fact that project management is suited to solving well-defined problems causes some major disconnects. For example, the uncertain nature of a new software product could mean that long projects are padded with such large time and cost buffers that the market and technology landscape will change significantly during the project’s delivery. In that scenario, it renders the assumptions made at the start of the project useless. Because it’s closely tied into business inputs, budgeting is one of the first places that you see the breakdown when trying to manage software delivery with a project-oriented approach. By design, project budgets need to bake in all of the uncertainty and risk of a software project.
The 6 reasons why Huawei gives the US and its allies security nightmares

Huawei claims its equipment connects over a third of the world’s population. It’s also handling vast amounts of data for businesses. That’s why there’s fear in Western intelligence circles that back doors could be used to tap into sensitive information using the firm’s equipment. This would be tricky to do undetected, but not impossible. Huawei doesn’t just build equipment; it can also connect to it wirelessly to issue upgrades and patches to fix bugs. There’s concern that this remote connectivity could be exploited by Chinese cyber spies. ... Huawei has repeatedly stressed it’s a private company that’s owned by its employees. The implication is that it has no incentive to cause customers to lose confidence in the integrity of its products. On the other hand, its governance structures are still something of a mystery, and its founder, Ren Zhengfei, who was once an officer in the Chinese People’s Liberation Army, keeps a low profile. Such things “make you question just how much independence it really has,” says Adam Segal, a cybersecurity expert at the Council on Foreign Relations in New York.
Understanding the Potential of Artificial Intelligence
If your computer system is not making a decision and then learning whether that decision was good or bad and adapting its own internal model of the world, I would argue that it’s not true AI. And it’s OK for companies at the moment to be calling machine learning AI. So for me, the true [definition] of AI [involves] systems that can learn and adapt themselves without the aid of a human. Adaptability is synonymous with intelligence. In fact, most companies don’t have machine learning problems — they have optimization problems. Optimization is the process of allocating resources to achieve an objective, subject to some constraints. Optimization problems are exceptionally hard to solve. For example, how should I route my vehicles to minimize travel time, or how do I allocate staff to maximize utilization, or how do I spend marketing money to maximize impact, or how do I allocate sales staff to opportunities to maximize yield?
How blockchain is bringing staffing innovation
Blockchain is already poised to seriously disrupt the staffing industry, for instance, because it’s helping companies expedite resume validation. Similarly, it’s easier now than ever before for many businesses to churn out short-term contracts, which has enabled them to prosper from the rise of freelancers in the international economy. Where businesses were once relatively constrained in their staffing practices, blockchain technology and the development of the gig economy has made it easy for HR departments to remain flexible with short-term hires. The decentralized nature of blockchain ledgers make them ideal for the contemporary economy because they can’t be monopolized by anyone; blockchain by its very nature is democratic, meaning it can be of use to anyone. Massive corporations and small-town entrepreneurs alike are already beginning to realize that the can both use blockchain applications at the same time precisely because its costs are so affordable and its advantages so universal.
The Analytics Platform seen through Enterprise Architecture
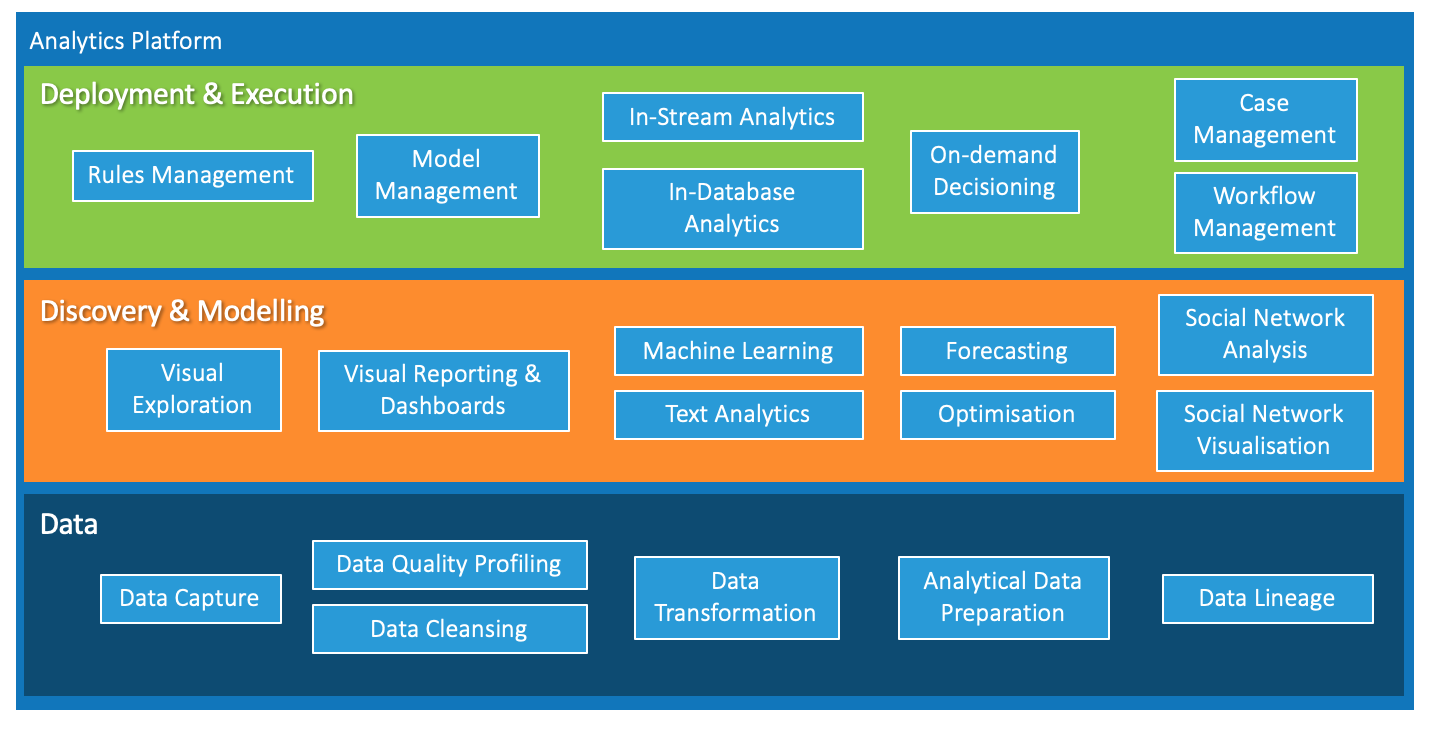
Data analytics and AI is now on the agenda of every organisation. After years of being the back-room preserve of analysts, it is now out in the open, in the boardroom and being proclaimed as central to business strategy and transformation. If this were not enough, the data analytics processes actually running in the organisation are no longer just reports or ad hoc queries by individual users but are now integrated with on-line transactional systems and enable business-critical activities. Analytics has made the transition from end-user computing to an enterprise capability requiring support and governance by IT. The journey has not always been easy with analysts and IT often experiencing a culture clash. All this has come to the attention of the people responsible for planning IT capabilities: the Enterprise Architects. Analytical systems now need a defined place in the Enterprise Architecture alongside transactional systems, CRM systems, data warehouses, communication systems and other core systems.
Reference Architecture & Frameworks: A Consolidation
The use of a reference architecture in an organization also requires governance to enforce that organizations commit to its use. Reference architectures are only valuable if people use them as intended and follow their guidance—otherwise the whole idea of reusing industry best practices breaks down. For example, the business functions of a typical insurance company are largely similar to those of its competitors, as are many of its business processes. Competitive differences will most likely be in its products, pricing, customer segments, and customer relationships. Reusing industry best practices provided by reference architectures ensures that you are not behind the curve on these non-competitive aspects. We also see this in the implementation of many IT systems, where vendors such as SAP provide reference processes for large parts of an organization. Reference architecture should be community-based.
Quote for the day:
"Your first and foremost job as a leader is to take charge of your own energy and then help to orchestrate the energy of those around you." -- Peter F. Drucker


No comments:
Post a Comment