Industrial IoT, fog-networking groups merge to gain influence

“By expanding our pool of resources and expert collaborators, we will continue to accelerate the adoption of not only fog, but a wealth of technologies that provide the underpinnings to IoT, AI and 5G,” wrote Matt Vasey, chairman and president, OpenFog Consortium, in a blog about the merger. “Machines, things, and devices are becoming increasingly intelligent, seamlessly connected, and capable of massive storage with the ability to be autonomous and self-aware. Robots, drones and self-driving cars are early indicators of small and mobile clouds. Distributed intelligence that interacts directly with the world and is immersive with all aspects of their surrounding is the concept behind fog,” he said. Merging the two groups is a natural fit and helps consolidate an overly fragmented collection of groups striving to create standards in the large IoT market, said Christian Renaud, research vice president, internet of things, 451 Research, in a blog about the unification.
RaptorDB - The Document Store

The main driving force behind the development of RaptorDB is making the developer's and support jobs easier, developing software products is hard enough without complete requirements which becomes even harder when requirements and minds change as they only do in the real world. ... Document databases or stores are a class of storage systems which save the whole object hierarchy to disk and retrieve the same without the use of relational tables. To aid the searching in such databases most Document store databases have a map function which extracts the data needed and saves that as a "view" for later browsing and searching. These databases do away with the notion of transactions and locking mechanism in the traditional sense and offer high data through-put and "eventually consistent" data views. This means that the save pipeline is not blocked for insert operations and reading data will eventually reflect the inserts done ( allowing the mapping functions and indexers time to work).
How to Make Cross-Functional Operations a Team Effort
Cross-functional collaboration, if done right, can make a company leaner and more innovative from the ground-up by reducing groupthink, because all decisions are taken through a cooperative and creative process with singular focus on the achievement of each organizational goal. Data supports this observation. A study of over 1100 companies shows that companies that embraced collaborative working are five times as likely to be high performing than those that don’t. If cross-functional teams are so awesome, why don’t we see more of them? Because they’re devilishly hard to manage and steer towards delivering real results, that’s why. Behnam Tabrizi, who teaches transformational leadership at Stanford University, reveals a shocking insight from his research– nearly 75% of cross-functional teams are dysfunctional! So we have two facts that are equally compelling. First, well-oiled cross-functional teams are exponentially more successful than “regular” teams. Second, getting a cross-functional team to perform to their potential is hard, but definitely not impossible.
Mobile security needs a rethink for the 5G era

“We are expecting the first 5G enabled services to come to market next year and we are already doing significant work across the UK test beds,” said Rahim Tafazolli, University of Surrey Regius professor and founding director of the 5GIC. “The benefits of being prepared for what 5G offers are clear for all to see. “Performance risk in such a complex network means that we need to reconsider many of our digital security processes. We believe that with the sound recommendations made in this paper, the UK will be in a good position to continue our leadership position in 5G innovation, development and deployment.” Peter Claydon, project director of AutoAir, said: “Since the age of 2G, mobile networks have been some of the most secure things on the planet, helped by the fact that each one is controlled by a single network operator. 5G opens up mobile networks, allowing network operators to provide ‘slices’ of their networks to customers.
Top smart city predictions for 2019

It will be a breakthrough year. We will see a move from pilots/proof of concepts to at-scale implementations. As with any first wave of adoption, this will result in exciting breakthroughs and early learnings. There will be citizen impact; in general, citizens will be more engaged and will push city leaders for impact. Millennials and social media will play a more vocal role in the smart cities conversations and start influencing electability. Equitable access and growth will be a key focus. The focus will move from an umbrella conversation to the top specific use cases: public safety, transportation, resilience and sustainability, and new business models. Infrastructure with vision/sensing capabilities will become real. Teamwork makes the dream work. A global fraternity of cities will start manifesting itself. We will see a much greater trend of cities reaching out and sharing key learnings. The cross-pollination of human talent between public and private sector as it relates to smart cities will be visible. This will help accelerate the overall adoption.
Chinese hackers tap into EU diplomatic communications network
An assessment of Chinese military capabilities conducted by the US Department of Defense (DoD) suggested that the country "saw cyber operations as a low-cost deterrent that can demonstrate capabilities and challenge an adversary." Deterrent it may be, but China has been accused of being behind a range of cyber assaults for years. The US has charged a number of hackers for allegedly belonging to the PLA and conducting cyberattacks of political interest on the unit's behalf. Despite an agreement forged between the US and China in 2015, US government officials warned this year that Chinese hacking activity has increased. Chinese officials have always denied such allegations. The researchers say that the threat actors responsible were able to compromise the network via a successful phishing campaign. However, the team also claims that the attack is part of a larger scheme which has also targeted the United Nations and the American Federation of Labor and Congress of Industrial Organization
Security Architecture for Smart Factories
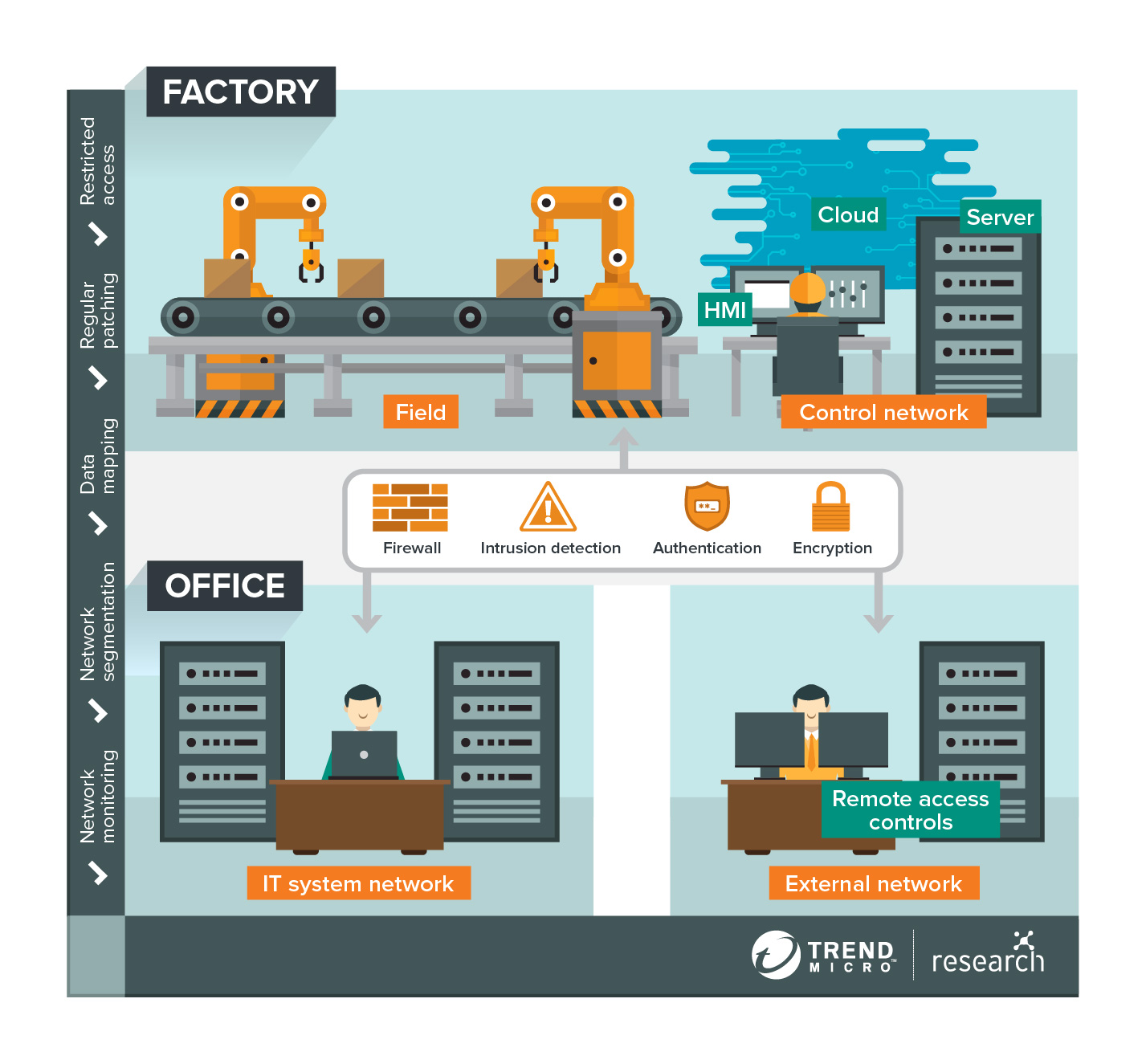
Smart factory operations are data-driven. The abundance of data a smart factory harnesses can include the amount of raw materials it has in storage, the production speeds of its machines, the location of ongoing deliveries, and a great deal more, depending on its industry. Big data allows the smart factory to paint a virtual copy of physical operations that is used to carry out functions such as predicting outcomes and making autonomous decisions. Organizations should be prepared for the vast amount of data this entails. They should be able to identify the types of data to be used and map out its course from collection and transfer to processing and storage. Mapping also means noting all possible exit and entry points. Personnel, for example, can move information from the office to the factory using external storage devices like USB flash drives. Terminals can also be taken in and out of factories for servicing. Aside from setting security protocols for personnel in handling such scenarios, tools should also be used to make sure that these portable devices are clean and virus-free before being connected or reconnected to the factory’s systems.
What Is Shadow DOM, and How Do You Use It?
Shadow DOM may have a name that conjures images of a dark world. But it’s actually a pretty neat feature of modern browsers, allowing for easy encapsulation of DOM elements and smart web components. If you‘re a front-end developer, you’ll likely benefit from understanding how Shadow DOM works and what it can do for you. That’s what this article explains. Keep reading for an introduction to Shadow DOM. ... One interesting thing to note is that, while JavaScript events are retargeted to the parent element in order to avoid exposing access to the internal Shadow DOM elements, these same elements can be interacted with using CSS as long as you know what the elements are and how to access them. But, as cool as it is, how can we best utilize the ... Because none of the code inside a Shadow DOM element can affect anything outside of it, the Shadow DOM is an excellent tool for encapsulation. In some circumstances, obscuring elements may be used as well; however, this method is hardly fool proof, so you are better off reaping the benefits of the encapsulation and management features instead.
Threat Hunting for the Holidays

How will you know for sure if a threat has evaded detection and is now inside your network? Yes, you can scour through every piece of research available about the threat. You can then comb through stacks of network logs across your environment to find anomalies and suspicious behavior. But won’t it take you days or weeks to find out how the threat got in, all the places it has been, and everything it did? And, will your boss have the patience to wait for your definitive response? There’s a better way. Cisco helps boost your ability to conduct threat hunting and incident response activities with a set of integrated tools that allows you to proactively search for threats and understand the full scope of a compromise. And upon seeing a threat in one place, Cisco gives you the ability to automatically block it everywhere else. As part of this integrated security architecture, Cisco Threat Response speeds threat hunting by gathering, combining, and correlating threat intelligence available from: 1) your recorded network and security data, 2) Cisco Talos, 3) other Cisco products, and 4) third-party solutions.
The Manual Regression Testing Manifesto
The manual regression testing manifesto provides a couple of things. First, it helps define a clear line differentiating feature testing from regression testing, a difference that is often a challenge for testers and management. Each core principle in the manifesto focuses on two elements that both have value in testing. By contrasting their relative value, we define expectations for testing throughout the release cycle. It’s not that one is bad and the other good, it’s that there is a time a place for each and testers need to be able to speak to that difference. Second, it provides a framework to start discussing quality and how testers contribute to it. It’s easy for people to typecast testers as nefarious breakers of software, when in reality we probably love the software we are testing as much or more than the developers writing it. We don’t have the bond of the creator yet we spend countless hours working with it just trying to ensure its success. Teams spend a great deal of time discussing coding standards and practices, but code is much more tangible and measurable than testing and quality.
Quote for the day:
"Leaders are more powerful role models when they learn than when they teach." -- Rosabeth Moss Kantor
No comments:
Post a Comment