Doxxing: What It Is How You Can Avoid It

Doxxing means publishing private information about someone online to harass or intimidate them. It has ruined reputations and caused untold distress to hundreds of people. On occasion, doxxing has resulted in injury or even death. Being doxxed can have serious consequences for your safety and privacy. How can you prevent it? Doxxing and cyberbullying often go hand in hand, although doxxing has also been used — controversially — by journalists in pursuit of public interest stories. It’s a relatively new phenomenon grown out of early internet subculture, but it’s gaining both popularity and efficacy, driven partly by social media. Information obtained in doxxing attacks is generally gathered from public or semi-public sources: website logs, WHOIS records, social media profiles,and simple Google searches or directories. In some cases, it’s harvested by more sinister means like hacking or social engineering.

The temptation to measure everything is understandable, but that can be the road to ruin. "Pick something that you don't like," Wallgren said. "Pick something that drives you nuts. Pick something that takes too long. Pick something that fails too often. Just pick something and then figure out a way to measure that and drive a better outcome for that thing. And then move on to the next thing." If you continue to find ways to get better, be it with mean time to recovery, release frequency or any number of other DevOps metrics, you should be able to deliver better software and keep your customers happy. Adopting DevOps metrics does not mean you should count the lines of code produced. While that may be an objective measurement, it's not in any way relevant to outcomes. Concentrate on a few things that help you make better decisions, experts insist, even if those items don't seem like they make an enormous difference to IT overall.
Q&A on the Book Digital Transformation at Scale
For many organisations, agile teams represent a very new way of working. It isn’t really possible to learn that in a classroom, or even be coached towards it. To really establish agile within an organisation, you need to bring in the full team, not just ones and twos (‘the unit of delivery is the team’ was a GDS mantra). That team should be given the conditions that allow them to deliver quickly, work in the open, and become a visible and tangible demonstration of what an agile team is. Some of that is intensely practical - having a decent workspace for them to all sit together, for example. Some of it is more challenging for institutions - moving to governance that is based on show and tells rather than steering boards is a big culture shock for many. Without that team showing what it means for real, agile is just words on a page for people, and not very clear ones at that.
6 Ways to Anger Attackers on Your Network

"Make no mistake: It is happening. Companies are hacking back," he explains, and much of their activity is arguably in violation of the CFAA. That said, he isn't aware of any prosecutions under CFAA against organizations engaged in what is often called "active defense activities." Legal trouble aside, getting into a back-and-forth with attackers is dangerous, Straight cautions. "Even if you're really, really good and know what you're doing, the best in the business … will tell you it's very hard to avoid causing collateral damage," he explains. Chances are good your adversaries will see your "hack back" and launch a more dangerous attack in response. The worst thing you can do is go after the wrong party, the wrong network, or the wrong machines, he continues. Most hackers aren't using their own equipment when they attack. "There are times when I have really wanted to strike back, but you can't and you don't," says Gene Fredriksen, chief information security strategy for PCSU.
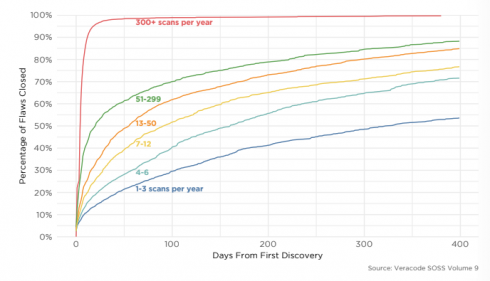
According to Veracode’s State of Software Security (SOSS) report, 87.5 percent of Java applications, 92 percent of C++ applications, and 85.7 percent of .NET application contain at least one vulnerability. In addition, over 13 percent of applications contain at least one critical vulnerability. “Our annual SOSS data puts hard evidence on the table to explain why so many security professionals experience anxiety when they think about application security (AppSec),” the report stated. “There is no way to sugar coat it: the sheer volume of flaws and percentage of vulnerable apps remain staggeringly high.” Among the vulnerabilities, SQL injection flaws and cross-site scripting (XSS) remained most common, which is consistent with previous years. SQL injection flaws were found in about one in three applications, while XSS vulnerabilities were present in about half of the applications.
Best tools and methods for designing RESTful APIs

API visualization is one of the fundamental steps in design, because it frames a graphical view of the API for users and enables users to interact with services that use a type of generalized API GUI. Most interactive development environments have visualization tools available, but these tools only offer basic capabilities. Swagger UI is a popular API visualization example that makes the in/out data structure of an API visible; it also exhibits simulated responses to given API caller requests. An API catalog is the central element of any API design strategy. Catalogs hold API definitions and make them available to developers. In some cases, catalogs may also drive API management processes, like access control or load balancing. Most API management suites will include a catalog, and separate API catalog tools are available from companies like Swagger, Oracle and IBM, as well as in open source form, like ReDoc.
Three key trends that will change cybersecurity strategies in 2019
Traditional VM tools identify thousands of vulnerabilities at any given time for a large enterprise, making it near impossible for security teams to know which vulnerabilities to prioritize and address first. As Gartner pointed out, advanced risk-based VM tools take into consideration the impact to the business of each vulnerability if exploited, and produce a clear, prioritized list of actions for the security team to take. As devastating breaches at organizations large and small, public and private, continue to make headlines, companies will gravitate toward risk-based tools to more effectively and efficiently avoid getting breached. Cybercriminals are constantly evolving their attack methods, and in response, security teams must advance their approaches to protecting their data. This means rethinking antiquated processes and tools. 2019 is sure to bring new challenges, but companies will also be taking steps in the right direction to properly secure data and proactively prevent breaches.
As Bitcoin sinks, industry startups are forced to cut back

The latest victim is Bitmain, a provider of bitcoin mining hardware that very recently submitted its IPO prospectus to the Stock Exchange of Hong Kong. The company confirmed to CoinDesk this week that cutbacks would begin imminently: “There has been some adjustment to our staff this year as we continue to build a long-term, sustainable and scalable business,” a spokesperson for Bitmain told CoinDesk . “A part of that is having to really focus on things that are core to that mission and not things that are auxiliary.” Beijing-based Bitmain hasn’t clarified just how many of its employees will be impacted, though rumors — which Bitmain has since denied — on Maimai, a Chinese LinkedIn-like platform, suggest as many as 50 percent of the company’s headcount could be laid off. This news comes after the crypto mining giant confirmed it had shuttered its Israeli development center, Bitmaintech Israel, laying off 23 employees in the process. Bitmain employs at least 2,000 people, up from 250 in 2016, according to PitchBook, as the company’s growth has skyrocketed.
Tracking Analytics with Artificial Intelligence

As we head into 2019, it’s hard to find an industry that has been untouched by the data revolution. Even segments known for the hands-on nature of its work, like construction, are being reimagined with 3D-printed buildings, augmented reality and robots. The three industries below stand somewhere between those most and least affected by digital transformation. ... The worst kind of usage for a car is when a vehicle is driven mostly in traffic while the best is when it’s mostly highway driving, with less stopping and starting. An automaker in that case can offer everyone the same warranty for the first year but then can offer a different warranty package in the next year based on usage. Though no automakers have done so yet, this type of warranty package (similar to how the car insurance industry uses in-car tracking devices) can save automakers a lot of money and reward drivers who are gentler on their cars. For example, one of our auto clients was able to reduce warranty costs by 35% using sensor data.
When quantum computing threats strike, we won't know it

If a country was able to develop and successfully implement quantum computing for the purpose of breaking RSA encryption, they're not going to tell anyone. At some point, academia or the private sector will make advances that might show that it's plausible. But I think we have to be realistic and understand that the largest investors in this area are doing so such that it is highly unlikely that we will actually be aware when they are successful. ... You can assume that none of the people with access to the data were insider threats, but can you be 99.99% sure? Could that actually be the way the data was leaked? Or could it be flaws in the implementation of existing algorithms? It's not just good enough to have strong algorithms, we need strong implementations of the algorithm. If data all of a sudden is leaked, was it because the algorithm was cracked or one of these other government agencies identified a vulnerability that they chose not to disclose?
Quote for the day:
"When you practice leadership,The evidence of quality of your leadership, is known from the type of leaders that emerge out of your leadership" -- Sujit Lalwani
No comments:
Post a Comment