What is an SSD? How solid state drives work
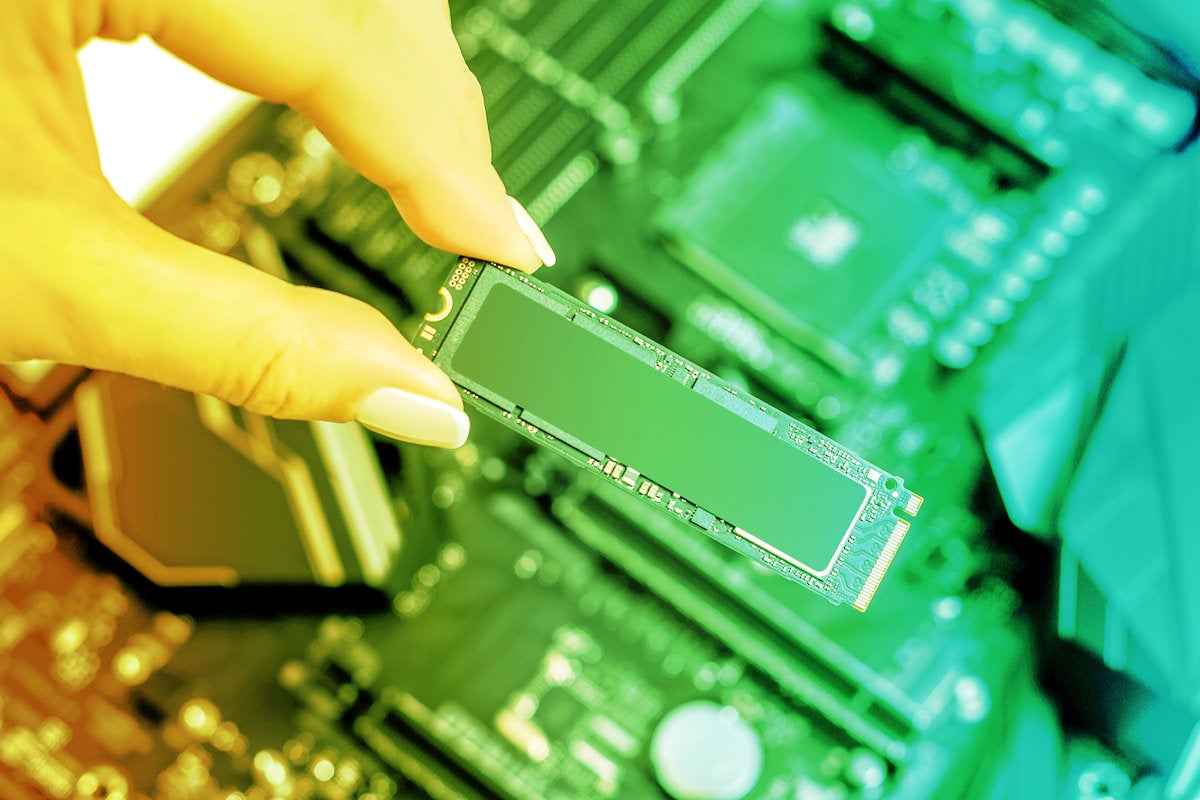
A simple USB flash drive (or thumb drive) is an example of solid-state drive technology. An SSD is a larger, more complex device that aggregates pools of NAND flash storage, the type of storage also found in MP3 players and digital cameras. Unlike RAM, which doesn’t retain data when the machine shuts off, SSD flash memory is non-volatile, which means data is retained whether the device is powered on or not. With SSDs, every block of data is accessible at the same speed as every other block, no matter the location. This makes SSDs inherently faster than hard drives, where platters are spinning and drive heads are moving to the right location. With HDDs, large files can be broken up and tucked into unused nooks and crannies of the drive, and data can be easily updated in place. This allows for efficient use of the total drive capacity. On the other hand, scattered data obviously takes longer to locate, which is why defragmenting a hard drive has become a standard part of device maintenance.
Online Shopping – Not so old but worth much more!
People under the Researcher category exhibit that they have crossed the awareness stage are now into the consideration stage. They are considering their potential options. If a person is conducting research about anything, it means he/she is looking for details. Details that can satiate their confused mind, provide answers to their underlying questions. Researchers are a notch above browsers in terms of potential buyers. If a website provides a detailed explanation of products, trustworthy support, easy navigation, and crisp product images, they may more incline towards buying from that website. Hence trust is the most important factor for researchers. Simply providing consistent information and clear to the point product descriptions work here. Since trust is mentioned here, product reviews or user reviews become the most influential factor here. Researchers will tend to trust previous customers who have bought similar items. Comprehensive user reviews and ratings act as a catalyst.
Will the imminent death of Microsoft Edge lead to an insecure browser monoculture?
As Callan says, Microsoft certainly has the ability to adopt Google’s HTML rendering engine without abdicating other browser interface and technology decisions, but the possibility definitely looms of the new Microsoft browser becoming little more than a re-skinned version of Chrome, whatever it is called. "In the certificate space, this monoculture could lessen the influence of many important voices," Callan warns. "Interoperability requirements have caused public PKI mechanisms such as TLS certificates to be governed by standards bodies such as the IEFT and the CA/Browser Forum." And for good reason as these bodies incorporate the unique expertise of not only browser manufacturers but also CAs, information providers, auditing firms and others to create a robust ecosystem that defends against myriad attack vectors."As a single browser manufacturer gains the ability to flex its muscle and make decisions unilaterally that all others must comply with," Callan said, "these other viewpoints and their valuable knowledge threaten to be lost..."
New Microsoft Teams calling features narrow gap with Skype

Three of the advanced features -- group call pickup, call park and shared line appearance -- should become available within the next several weeks. A fourth feature, location-based routing, is slated for release in the first quarter of 2019. Group call pickup improves an existing feature that lets users automatically forward incoming calls to groups of colleagues. The system can ring each member of the group simultaneously or one at a time in a predetermined order. The update lets users customize the appearance and type of notifications that members of the group receive with incoming calls. Call park is a sophisticated way to put callers on hold. Parking a call generates a code, which gets sent -- in a text message, for example -- to the employee the caller is attempting to reach. That employee can then answer the call in the Teams app. Shared line appearance lets businesses create user accounts with multiple phone lines. The incoming calls to those lines are all automatically forwarded to other users.
HONOR: The Force of Innovation
In pursuit of innovation, HONOR has often played the long game, ignoring the latest hot trends if it believed certain technologies were not ready to be commercialized. “Virtual reality and augmented reality, for instance, still have unsolved concerns and matters that need to be addressed,” Zhao said. “Blockchain application on mobile phones is nothing more than a gimmick. At HONOR, we have our own mechanism for deciding what to invest in and innovate. Once we have set the direction, we will go all-in.” That determination has come to fruition in HONOR’s AI breakthroughs, which have been at the center of HONOR’s development strategy from the beginning. Long before the industry came to realize the importance of AI, HONOR had already invested heavily in R&D and building the AI ecosystem. “We have spent six years developing the chipset, system and application,” Zhao said. “We believe AI assists human brains in making decisions. If mobile phones have broadened our minds and experiences as users, then AI will narrow the gap between us and the experts.
What is digital trust? How CSOs can help drive business

Even if companies understand the value of trust, many simply overestimate their own standing in their customers eyes and how they compare to the competition. The report outlined an average of a 14-point gap between the level of trust customers have in whether organizations handle personal data appropriately compared to how much organizations think they are trusted. The report claims this illustrates how “dangerously out of touch” organizations are with their customers. Just a third of customers said their trust in organizations had increased over the last two years, compared to the 84 percent of business leaders who believe that trust has increased. Ninety percent of those business leaders claim they are very good or excellent at protecting customer data, and 93 percent say that it is a differentiator over the competition. Considering the number of organizations that admitted a data breach in the study, this clearly does not add up.
Quantum computers pose a security threat that we’re still totally unprepared for

The report cites an example of encryption that protects the process of swapping identical digital keys between two parties, who use them to decrypt secure messages sent to one another. A powerful quantum computer could crack RSA-1024, a popular algorithmic defense for this process, in less than a day. Such machines, which would require a couple of thousand “logical” qubits, are probably at least a decade away, say the US experts. Qubits’ delicate quantum state can be disrupted by things like tiny changes in temperature or very slight vibrations, so it can require thousands of linked qubits to produce a single logical one that can be reliably used for computation. Still, complacency would be a mistake. William Oliver, an MIT physics professor and a member of the group that produced the academies’ report, notes that governments and businesses like banks often need to keep data secure for decades. They therefore need to be thinking now about potential future threats to the encryption they’re using.
Brexit implications for data protection

GDPR brought massive changes to data protection legislation and expanded what was expected of data controllers and data processors. One of the biggest changes brought about by GDPR is that organisations must now have technical measures that enforce their data sharing policy. “You used to have a contract that said you would not misuse data, but GDPR says you now must have technology in place that prevents the misuse of data,” says Gary Lefever, CEO of Anonos. As the internet has become an integral part of our society, data protection has become a legislative necessity to ensure the sharing of personal information is conducted in a fair, secure and responsible manner. The requirements for data storage, sharing and processing have been articulated in the GDPR, which is necessary reading for any company with any form of online presence. According to both the GDPR and the UK Data Protection Act 2018, when a country leaves the EU, it will cease to be covered by the GDPR, and as such will be considered as a third country, which is any country or territory other than an EU member state.
Innovative anti-phishing app comes to iPhones

Traditional security protection systems such as virus checkers and firewalls are still mandatory, but they are far less effective against the complex attack scenarios prevalent in today's digital economy. When it comes to enterprise security, network monitoring, location-based protection and cooperative sharing of security-related datasets are becoming key components of switched-on, 24/7, situation-awareness security protection systems. Within this landscape, MetaCert’s system seems a useful adjunct to existing systems. I imagine we’ll see this kind of alert-based security systems become components of future operating systems in the future, certainly within those from vendors that actually care about customer security, and privacy, come to that. On iOS, this new solution works with most email services, including Thunderbird and Apple Mail, with Outlook and Gmail support in development. The company is running a public beta test, so you can test this system for yourself.
Juniper ATP appliance gets broader device support
In the latest announcement, Juniper has made it possible for a Juniper ATP appliance to collect logs from security devices through their system logging facility, or syslog. To separate security-related log events, an administrator would go to the JATP user interface and create a log filter using one of its supported formats, such as XML, JSON and CSV. The admin can then create a parser that maps the log field from a firewall, for example, into the JATP's event fields to look for possible security threats, a Juniper spokesperson said in an email. Also, through the JATP UI, admins can see statistics on incoming logs and delete unneeded logs. Before the syslog support, easily collecting security data was limited to Juniper's SRX firewalls and devices made by the company's partners, such as Fortinet and Palo Alto Networks. "With the custom data collector capability, the integrations can be created from within the product by security personnel via an easy-to-use UI," the spokesperson said. Juniper plans to release the new capabilities in a software upgrade scheduled for release this month.
Quote for the day:
"Setting an example is not the main means of influencing others, it is the only means." -- Albert Einstein

No comments:
Post a Comment