Top 5 Trends in Cloud Native Software Testing in 2023

As digital threats become more sophisticated, there’s a heightened focus on
security testing, particularly among large enterprises. This trend is about
integrating security protocols right from the initial stages of development.
Tools that do SAST and DAST are becoming essentials in testing workflows.
... The TestOps trend integrates testing into the continuous development
cycle, echoing the collaborative and automated ethos of DevOps. TestOps
focuses on enhancing communication between developers, testers, and
operations, ensuring continuous testing and quicker feedback loops. It
leverages real-time analytics to refine testing strategies, ultimately
boosting software quality and efficiency. Extending the principles of DevOps,
GitOps uses Git repositories as the backbone for managing infrastructure and
application configurations, including testing frameworks. ... The rise of
ephemeral test environments is a game-changer. These environments are created
on demand and are short-lived, providing a cost-effective way to test
applications in a controlled environment that closely mirrors production
Dump C++ and in Rust you should trust, Five Eyes agencies urge
Microsoft, CISA observes in its guidance, has acknowledged that about 70
percent of its bugs (CVEs) are memory safety vulnerabilities, with Google
confirming a similar figure for its Chromium project and that 67 percent of
zero-day vulnerabilities in 2021 were memory safety flaws. Given that, CISA is
advising that organizations move away from C/C++ because, even with safety
training (and ongoing efforts to harden C/C++ code), developers still make
mistakes. "While training can reduce the number of vulnerabilities a coder
might introduce, given how pervasive memory safety defects are, it is almost
inevitable that memory safety vulnerabilities will still occur," CISA argues.
... Bjarne Stroustrup, creator of C++, has defended the language, arguing that
ISO-compliant C++ can provide type and memory safety, given appropriate
tooling, and that Rust code can be implemented in a way that's unsafe. But
that message hasn't done much to tarnish the appeal of Rust and other memory
safe languages. CISA suggests that developers look to C#, Go, Java, Python,
Rust, and Swift for memory safe code.
How the insider has become the no.1 threat

For the organisation, this means the insider threat has not only become more
pronounced but harder to counter. It requires effective management on two fronts
in terms of managing the remote/mobile workforce and dissuading employees from
swapping cash for credentials/data. For these reasons, businesses need to
reinforce the security culture through staff awareness training and step up
their policy enforcement, in addition to applying technical controls to ensure
data is protected at all times. That’s not what is happening today. The Apricorn
survey found only 14% of businesses control access to systems and data when
allowing employees to use their own equipment remotely, a huge drop from 41% in
2022. Nearly a quarter require employees to seek approval to use their own
devices, but they do not then apply any controls once that approval has been
granted. Even more concerning is that the number of organisations that don’t
require approval or apply any controls has doubled over the past year. This
indicates a hands-off approach that assumes a level of implicit trust, directly
contributing to the problem of the insider threat.
WestRock CIDO Amir Kazmi on building resiliency
There are three leadership principles I would highlight that help build
resilience in the team. First is recognizing the pace of change and responding
to the impact it has on a team. It’s not getting slower; it’s getting faster.
One of the behaviors that can help your team is to ‘explain the why.’ Set the
context before the content behind what needs to be accomplished so we’re all
on the same journey. Second is recognizing that we have to instill a
learning and growth mindset in the culture, in the leadership, and in the
fabric of what we’re trying to achieve. Many businesses are shifting their
business models from product to service, and as leaders, it’s important to
build a level of learning in that journey for your teams. One of the leaders
that I admire and have learned from is John Chambers, who has said, ‘It’s all
about speed of innovation and changing the way you do business.’ If we don’t
reimagine ourselves, we will get disrupted. Third is transparency around what
the key priorities are — because not everything can be a priority — and then
creating flexibility around those priorities and how we get to the
outcomes.
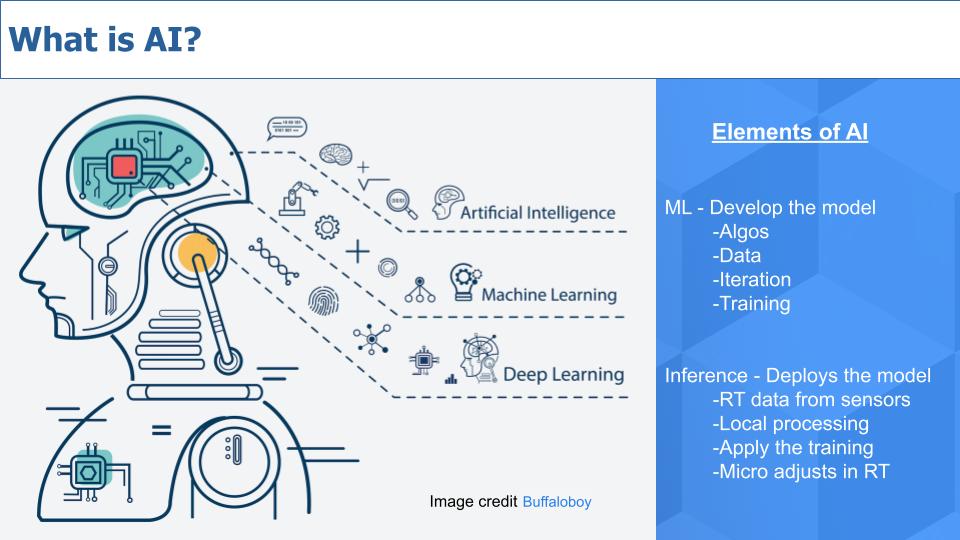
AI Governance in India: Aspirations and Apprehensions

While India’s stance on AI regulation has sometimes appeared to waver, it
is steadily working towards establishing a clear regulatory approach and AI
governance mechanism, especially as the country assumes a more prominent role
in the area of AI-related international cooperation. AI-enabled harms and
security threats exist at all three levels of the AI stack: At the hardware
level, there are vulnerabilities in the physical infrastructure of AI systems.
At a foundational model level, there are concerns around the use of
inappropriate datasets, data poisoning, and issues related to data collection,
storage, and consent. At the application level, there are threats to sensitive
and confidential information as well as the proliferation of
capability-enhancing tools among malicious actors. Therefore, while the
governance of the tech stack is a priority, governance of the organisations
developing AI solutions, or the people behind the technology, could also be
productive. Even as democratisation has made AI more accessible, assigning
responsibility and defining accountability for the operation of AI systems
have become more difficult.
Liability Fears Damaging CISO Role, Says Former Uber CISO
The average person on the street would think it reasonable that a CISO should
be responsible for all aspects of an organization’s security, Sullivan
acknowledged. However, the reality is the CISO role is unique among executive
positions. “The CISO is fighting an uphill fight every day in their job.
They’re begging for resources, they’re trying to get the rest of the company
to slow down and think about the things they care about,” he noted. “Our job
is different from everybody else’s. When you’re the executive responsible for
security, you are the only executive who has active adversaries outside your
organization trying to destroy you,” he added. ... Despite the growing
personal risks for CISOs, Sullivan emphasized that “we should not run away
from the situation,” adding that “if we do, we’ll miss a huge opportunity.” He
believes there is a fundamental shift coming in terms of the regulation that’s
on the horizon in cybersecurity, which will force organizations to revise how
they approach security, and current security professionals must be to
facilitate this change.
Middle East CISOs Fear Disruptive Cloud Breach

Data sovereignty regulations and de-globalization trends, for example, have
led to the deployment of multi-cloud infrastructures that can support regional
regulations and business mandates, according to the March research report, The
Future of Cloud Security in the Middle East. "You will have your own cloud
service provider within each country and already countries are adopting that
culture — be it in the UAE or Saudi Arabia or any other country in the
region," Rajesh Yadla, director head of information security for Al Hilal
Bank, stated in that report. "The reason is to make sure that the cloud
service providers are compliant with all these regulations." Business and
government leaders have taken cybersecurity seriously, however, with security
the top factor in choosing a cloud provider, with 43% of companies
prioritizing security, compared to 19% prioritizing cost, according to the
report. Both Saudi Arabia and the UAE rank in the top 10 nations for
cybersecurity, as measured by the Global Cybersecurity Index 2020, the most
recent cybersecurity rankings of countries across the globe compiled by the
International Telecommunication Union (ITU).
Parenting in the Digital Age: A Guide to Choosing Tech-Enabled Preschools

In recent years, technology integration in preschoolers’ education has become
a game-changer in delivering personalised learning. By making education more
fun and interactive by using a robust arsenal – AR applications, ERP apps and
much more, teachers and parents have been able to tap into the receptivity of
young minds, paving the way for both cognitive and emotional development.
Augmented Reality (AR) being an interactive experience assimilates the real
world and computer-generated content. Additionally, it stimulates multiple
sensory modalities, making a successful mark in opening up new avenues in
preschool education. By allowing young learners to immerse in realistic
experiences, AR elevates the learning process with computer simulations, 3D
virtualisation, etc. making it enhanced, effective and evocative. Departing
from the traditional chalkboard and chart paper educational approach for
preschoolers, parents have seismically shifted their preference to a
tech-integrated curriculum. The augment of AR technology for early childhood
learning brings forth a layer of interactive and engaging
experiences.
Cyber Strategic Ambivalence Will Hit A Tipping Point In 2024

There are indications that technological advances, geopolitics, social
influences, and other externalities are creating the conditions for what
Thomas Kuhn coined the “paradigm shift” (his 1962 book, The Structure of
Scientific Revolutions, described the dynamics and the framework by which
structural change emerges). The conditions for change that will result in a
paradigm shift are the breadth, types and severity of attacks that are ongoing
and will likely increase in 2024. The assessed global cyberattack losses in
2023 amount to $8 trillion, which is larger than any national economy except
for the US and China! In other words, the collective black market – the
illicit profits generated from cybercrime – is a larger economy than Germany
or Japan or India. That is a look at the problem in monetary terms.
Cyberattacks are now regularly compromising critical infrastructure, which
places public safety at risk. In May of 2023, Denmark’s critical
infrastructure network experienced the largest cyberattack ever, which was
highly coordinated and could have resulted in power outages.
How server makers are surfing the AI wave

There appears to be strong demand for high performance computing (HPC)
hardware that includes graphics processing units (GPUs) for accelerating the
performance of workloads and GPU-based servers. ... There is a growing
realisation among many businesses that the hyperscalers are behind the curve
with regards to supporting the intellectual property of their GenAI users.
This is opening up opportunities for specialist GPU cloud providers to offer
AI acceleration in a way that allows customers to train foundational AI models
based on their own data. Some organisations are also likely to buy and run
private cloud servers configured as GPU farms for AI acceleration, fuelling
the significant growth in demand for GPU-equipped servers from the major
hardware providers. HPE recently announced an expanded strategic collaboration
with Nvidia to offer enterprise computing for GenAI. HPE said the
co-engineered, pre-configured AI tuning and inferencing hardware and software
platform enables enterprises of any size to quickly customise foundation
models using private data and deploy production applications anywhere.
Quote for the day:
''Your most unhappy customers are your
greatest source of learning.'' -- Bill Gates