Quote for the day:
"Don't be pushed around by the fears in your mind. Be led by the dreams in your heart." -- Roy T. Bennet
Identify and eliminate the silent killers of developer productivity
 Code reviews are a critical part of the development lifecycle, designed to
improve code quality, share knowledge, and catch bugs before they get to
production. But they are a significant bottleneck when not handled with care.
... This isn’t just a matter of lost time; it’s a killer of flow. Developers are
forced into a constant state of context switching, losing their focus and
momentum. You need to establish clear expectations and protocols for code
reviews. ... Poor documentation forces a constant stream of interruptions and
meetings that pull senior developers away from their own work to answer
questions. It’s a prime example of a process failure that creates a huge amount
of hidden, unproductive work. Make documentation a first-class citizen in
your development process. ... Then there’s the peer who, perhaps with good
intentions, cuts corners. They deliver a feature that “looks like it works” for
a project manager who is hungry for a win. The PM, not seeing the technical debt
or the flawed logic, approves it and pushes for immediate deployment. This
undermines the entire team, as it normalizes a low-quality standard and signals
that bad behavior is rewarded. You must step in and resolve these
interpersonal and process conflicts. Use one-on-one meetings to address these
issues directly and set clear expectations. It’s your job to ensure that the
team’s decisions are respected and that the quality bar is not lowered for the
sake of speed.
Code reviews are a critical part of the development lifecycle, designed to
improve code quality, share knowledge, and catch bugs before they get to
production. But they are a significant bottleneck when not handled with care.
... This isn’t just a matter of lost time; it’s a killer of flow. Developers are
forced into a constant state of context switching, losing their focus and
momentum. You need to establish clear expectations and protocols for code
reviews. ... Poor documentation forces a constant stream of interruptions and
meetings that pull senior developers away from their own work to answer
questions. It’s a prime example of a process failure that creates a huge amount
of hidden, unproductive work. Make documentation a first-class citizen in
your development process. ... Then there’s the peer who, perhaps with good
intentions, cuts corners. They deliver a feature that “looks like it works” for
a project manager who is hungry for a win. The PM, not seeing the technical debt
or the flawed logic, approves it and pushes for immediate deployment. This
undermines the entire team, as it normalizes a low-quality standard and signals
that bad behavior is rewarded. You must step in and resolve these
interpersonal and process conflicts. Use one-on-one meetings to address these
issues directly and set clear expectations. It’s your job to ensure that the
team’s decisions are respected and that the quality bar is not lowered for the
sake of speed.Industry leaders urge strong strategies for post-quantum readiness
 Questions remain about the readiness of cryptographic solutions to withstand
future quantum attacks. Sinha addressed these concerns directly: "Post quantum
cryptography is here. DigiCert has been working along with other cryptography
experts. We've been collaborating with the National Institute of Standards and
Technology, NIST. Last year...NIST had announced the first three post quantum
cryptography algorithms. One for encryption and two for authentication. They are
the FIPS 203, 204 and 205 standards." ... Panelists underscored the
importance of cryptographic inventory. "Creating the cryptographic inventory is
the step zero of beginning any migration. And the complexity of creating...the
cryptographic inventory cannot be overstated. It's a...real hard task, but it's
really essential. It's the step zero because the inventory gives you the
roadmap. How do you begin the journey? How do you start prioritising your
systems and your applications?" said Chauhan. Luke Valenta added, "A
cryptographic inventory is never going to be complete. So it's all really about
the...process, and, and journey of putting that together. At Cloudflare in our
migration, we started this inventory and we used that to figure out what are the
highest priority systems to transition to post quantum first." Reilly noted,
"Just raising the awareness and visibility of all the places where an enterprise
uses cryptography - it can be a shock when that depth and breadth of the
required transformation becomes apparent..."
Questions remain about the readiness of cryptographic solutions to withstand
future quantum attacks. Sinha addressed these concerns directly: "Post quantum
cryptography is here. DigiCert has been working along with other cryptography
experts. We've been collaborating with the National Institute of Standards and
Technology, NIST. Last year...NIST had announced the first three post quantum
cryptography algorithms. One for encryption and two for authentication. They are
the FIPS 203, 204 and 205 standards." ... Panelists underscored the
importance of cryptographic inventory. "Creating the cryptographic inventory is
the step zero of beginning any migration. And the complexity of creating...the
cryptographic inventory cannot be overstated. It's a...real hard task, but it's
really essential. It's the step zero because the inventory gives you the
roadmap. How do you begin the journey? How do you start prioritising your
systems and your applications?" said Chauhan. Luke Valenta added, "A
cryptographic inventory is never going to be complete. So it's all really about
the...process, and, and journey of putting that together. At Cloudflare in our
migration, we started this inventory and we used that to figure out what are the
highest priority systems to transition to post quantum first." Reilly noted,
"Just raising the awareness and visibility of all the places where an enterprise
uses cryptography - it can be a shock when that depth and breadth of the
required transformation becomes apparent..."Tech Debt: Why Fixing the Foundation Comes Before Building the Castle
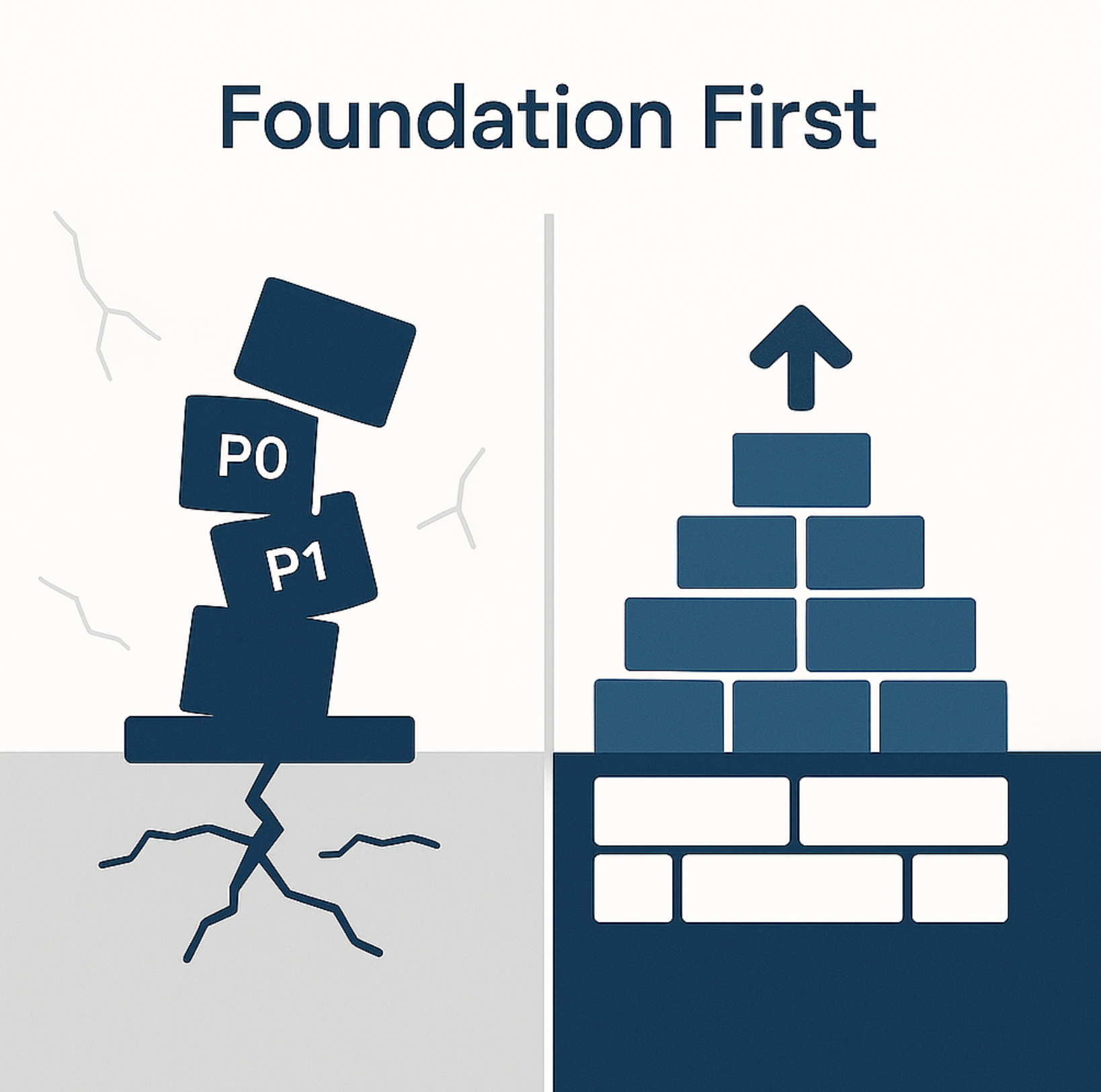 Tech debt is about everything that stems from unstable foundations. I had to
learn this during our scaling journey. Early on, we made quick decisions to ship
features fast. But as we grew, those shortcuts started choking our growth.
Companies pay an additional 10 to 20 percent to address tech debt on top of the
costs of any project, and we felt every percentage point. The real killer isn't
just the extra time – it's the opportunity cost. While your team is fixing
yesterday's shortcuts, your competitors are building tomorrow's features.
Developers working on the right things can accelerate a company's move into new
markets or product areas and help companies differentiate themselves at
disproportionate rates. But there's a human cost too. Nobody likes working with
a significant handicap and being unproductive day after day. ... Here's where
most companies get it wrong. They think innovation means constantly adding new
features, launching new products, exploring new markets. But true innovation
requires a stable foundation. 30 percent of CIOs surveyed believe that more than
20 percent of their technical budget ostensibly dedicated to new products is
diverted to resolving issues related to tech debt. You're essentially pouring
money into a bucket with holes in it. I've learned that the most innovative
companies aren't necessarily the ones building the flashiest features – they're
the ones who've mastered the discipline of maintaining clean, stable systems
that can support rapid innovation.
Tech debt is about everything that stems from unstable foundations. I had to
learn this during our scaling journey. Early on, we made quick decisions to ship
features fast. But as we grew, those shortcuts started choking our growth.
Companies pay an additional 10 to 20 percent to address tech debt on top of the
costs of any project, and we felt every percentage point. The real killer isn't
just the extra time – it's the opportunity cost. While your team is fixing
yesterday's shortcuts, your competitors are building tomorrow's features.
Developers working on the right things can accelerate a company's move into new
markets or product areas and help companies differentiate themselves at
disproportionate rates. But there's a human cost too. Nobody likes working with
a significant handicap and being unproductive day after day. ... Here's where
most companies get it wrong. They think innovation means constantly adding new
features, launching new products, exploring new markets. But true innovation
requires a stable foundation. 30 percent of CIOs surveyed believe that more than
20 percent of their technical budget ostensibly dedicated to new products is
diverted to resolving issues related to tech debt. You're essentially pouring
money into a bucket with holes in it. I've learned that the most innovative
companies aren't necessarily the ones building the flashiest features – they're
the ones who've mastered the discipline of maintaining clean, stable systems
that can support rapid innovation.Regulatory bodies close in on AI chatbots as LLMs face greater scrutiny
 As regulators roll out online safety laws designed to protect kids from harms
associated with porn and social media, a new threat has crept up behind them
that could overshadow both. AI chatbots – exemplified by OpenAI’s large
language model, ChatGPT – have been around long enough to prove themselves
popular, and risky. ... Inman-Grant says schools have “been reporting that 10-
and 11-year-old children are spending up to six hours per day on AI
companions.” Moreover, it’s not just that they’re befriending LLMs – it’s that
they’re often friends with benefits, or “sexualized chatbots.” “We don’t need
to see a body count to know that this is the right thing for the companies to
do,” says the commissioner. “I don’t want to see Australian lives ruined or
lost as a result of the industry’s insatiable need to move fast and break
things.” ... Brazilian authorities are pressuring Meta to immediately remove
AI chatbots that “simulate child profiles and engage in sexual conversations
with users.” According to PPC Land, the bots in question are those created
using Meta AI Studio, a tool for developing custom AI chatbots. In mid-August,
Brazil’s Attorney General (AGU) issued an “extrajudicial notice” giving Meta
72 hours to remove the erotic kiddie chatbots. It references Article 217-A of
Brazil’s Penal Code, which criminalizes sexual acts with minors under 14 years
old.The AGU argues that this includes simulated sexual interactions with AI.
Under Brazilian law, platforms are liable for harmful content hosted on their
services.
As regulators roll out online safety laws designed to protect kids from harms
associated with porn and social media, a new threat has crept up behind them
that could overshadow both. AI chatbots – exemplified by OpenAI’s large
language model, ChatGPT – have been around long enough to prove themselves
popular, and risky. ... Inman-Grant says schools have “been reporting that 10-
and 11-year-old children are spending up to six hours per day on AI
companions.” Moreover, it’s not just that they’re befriending LLMs – it’s that
they’re often friends with benefits, or “sexualized chatbots.” “We don’t need
to see a body count to know that this is the right thing for the companies to
do,” says the commissioner. “I don’t want to see Australian lives ruined or
lost as a result of the industry’s insatiable need to move fast and break
things.” ... Brazilian authorities are pressuring Meta to immediately remove
AI chatbots that “simulate child profiles and engage in sexual conversations
with users.” According to PPC Land, the bots in question are those created
using Meta AI Studio, a tool for developing custom AI chatbots. In mid-August,
Brazil’s Attorney General (AGU) issued an “extrajudicial notice” giving Meta
72 hours to remove the erotic kiddie chatbots. It references Article 217-A of
Brazil’s Penal Code, which criminalizes sexual acts with minors under 14 years
old.The AGU argues that this includes simulated sexual interactions with AI.
Under Brazilian law, platforms are liable for harmful content hosted on their
services.The Value-Driven AI Roadmap
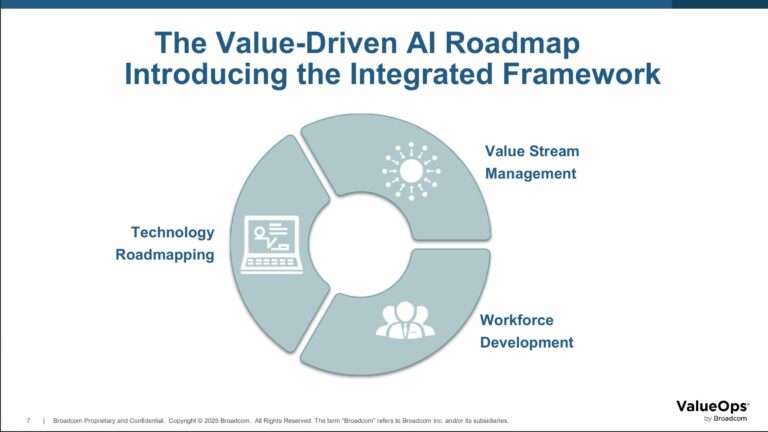 The use of value stream management helps organizations map their processes,
identifying impediments to delivering software that has value, and using
automation to collect metrics that give insights into those processes – and
even anticipate where the next hurdles might pop up, Knight said. “I’m going
to map the process out, look at where things are and say, hey, I could put an
AI agent here, then create a program and a plan to do that in a technology
roadmap to line up with it,” he explained. Technology roadmapping involves
aligning AI – what the organization is using now and what its needs might be a
few years down the road – with business value. Staying on top of technology
involves changes being driven by the market, the level of capability maturity
within the organization, and finding where the gaps in your technology exist.
“Roadmapping is more about helping organizations line up the change of
different technologies and how to roll that out,” he said. Finally, Knight
pointed out, assessing the skills within your workforce, where training is
needed, and how willing the workers are to change, is critical. “It’s about
how people in the future, in organizations, will have AI agents that work for
them. And you think about it having extra capabilities where I’m going to have
this set of skills with these people, but I may have an agent that works for
me,” Knight said. “Maybe that agent does paralegal work for me.
The use of value stream management helps organizations map their processes,
identifying impediments to delivering software that has value, and using
automation to collect metrics that give insights into those processes – and
even anticipate where the next hurdles might pop up, Knight said. “I’m going
to map the process out, look at where things are and say, hey, I could put an
AI agent here, then create a program and a plan to do that in a technology
roadmap to line up with it,” he explained. Technology roadmapping involves
aligning AI – what the organization is using now and what its needs might be a
few years down the road – with business value. Staying on top of technology
involves changes being driven by the market, the level of capability maturity
within the organization, and finding where the gaps in your technology exist.
“Roadmapping is more about helping organizations line up the change of
different technologies and how to roll that out,” he said. Finally, Knight
pointed out, assessing the skills within your workforce, where training is
needed, and how willing the workers are to change, is critical. “It’s about
how people in the future, in organizations, will have AI agents that work for
them. And you think about it having extra capabilities where I’m going to have
this set of skills with these people, but I may have an agent that works for
me,” Knight said. “Maybe that agent does paralegal work for me.The Hidden Cost of Overuse and Misuse of Data Storage
 At first glance, storing everything might not seem like a huge problem. But
when you factor in rising energy prices and ballooning data volumes, the
cracks in that strategy start to show. Over time, outdated storage practices,
from legacy systems to underused cloud buckets, can become a surprisingly
expensive problem. ... what often gets overlooked are the hidden costs: the
backup of low-value data, the power consumption of idle systems, or the
surprise charges that come from cloud services which are not being monitored
properly. Then there’s the operational cost. Disorganised or poorly labelled
data makes access slower and compliance tougher. It also increases security
risks, especially if sensitive information is spread across uncontrolled
environments. The longer these issues go unchecked, the more danger there is
of a snowball effect. ... Cutting storage costs is an obvious benefit but it’s
far from the only one. A smarter, edge-driven strategy helps businesses build
a more efficient, resilient, and sustainable digital infrastructure ... By
processing and filtering data locally, organisations reduce the energy demands
of transmitting and storing large volumes centrally, supporting both carbon
reduction targets and lower utility costs. As sustainability reporting becomes
more critical, this can also help meet Scope 2 emissions goals.
At first glance, storing everything might not seem like a huge problem. But
when you factor in rising energy prices and ballooning data volumes, the
cracks in that strategy start to show. Over time, outdated storage practices,
from legacy systems to underused cloud buckets, can become a surprisingly
expensive problem. ... what often gets overlooked are the hidden costs: the
backup of low-value data, the power consumption of idle systems, or the
surprise charges that come from cloud services which are not being monitored
properly. Then there’s the operational cost. Disorganised or poorly labelled
data makes access slower and compliance tougher. It also increases security
risks, especially if sensitive information is spread across uncontrolled
environments. The longer these issues go unchecked, the more danger there is
of a snowball effect. ... Cutting storage costs is an obvious benefit but it’s
far from the only one. A smarter, edge-driven strategy helps businesses build
a more efficient, resilient, and sustainable digital infrastructure ... By
processing and filtering data locally, organisations reduce the energy demands
of transmitting and storing large volumes centrally, supporting both carbon
reduction targets and lower utility costs. As sustainability reporting becomes
more critical, this can also help meet Scope 2 emissions goals.9 cloud strategy questions every IT leader must answer
 Cloud platforms are increasingly procured by non-IT teams. Establishing a
unified decision framework that brings together expertise from across the
enterprise to guide the cloud lifecycle, from selection to sunsetting, is key.
Without this, “organizations face fragmented architectures, redundant tools, and
compliance gaps,” says CIO Mentor’s Topinka ... Working with multiple cloud
partners can offer negotiating leverage and access to best-of-breed services,
but it also compounds complexity and requires a range of expertise. ... “The
maturity and advancement of cloud solutions depend on the team’s culture and
their ability to operate and innovate within the cloud,” Hackett Group’s Nathan
adds. ... “Clear visibility into consumption patterns, resource allocation, and
usage metrics is essential,” says Nathan, noting that cloud financial management
practices help maintain accountability and prevent cost overruns, particularly
in multicloud environments. Allocating cloud costs directly to business units or
product teams also increases transparency and encourages more efficient use of
cloud resources, according to Kocherlakota. ... Cloud adoption without attendant
legacy modernization can backfire, S&P Global’s Kocherlakota says. “Simply
using the cloud as a data center while maintaining legacy applications can lead
to cost creep,” he says. “Investing in transforming legacy systems optimizes
infrastructure and boosts efficiency.”
Cloud platforms are increasingly procured by non-IT teams. Establishing a
unified decision framework that brings together expertise from across the
enterprise to guide the cloud lifecycle, from selection to sunsetting, is key.
Without this, “organizations face fragmented architectures, redundant tools, and
compliance gaps,” says CIO Mentor’s Topinka ... Working with multiple cloud
partners can offer negotiating leverage and access to best-of-breed services,
but it also compounds complexity and requires a range of expertise. ... “The
maturity and advancement of cloud solutions depend on the team’s culture and
their ability to operate and innovate within the cloud,” Hackett Group’s Nathan
adds. ... “Clear visibility into consumption patterns, resource allocation, and
usage metrics is essential,” says Nathan, noting that cloud financial management
practices help maintain accountability and prevent cost overruns, particularly
in multicloud environments. Allocating cloud costs directly to business units or
product teams also increases transparency and encourages more efficient use of
cloud resources, according to Kocherlakota. ... Cloud adoption without attendant
legacy modernization can backfire, S&P Global’s Kocherlakota says. “Simply
using the cloud as a data center while maintaining legacy applications can lead
to cost creep,” he says. “Investing in transforming legacy systems optimizes
infrastructure and boosts efficiency.”
Has Cloud Security Reached Its Breaking Point?
Probably Secure: A Look at the Security Concerns of Deterministic vs Probabilistic Systems
What do cybercriminals know about the retail sector that we don’t?
 “Stolen customer data is valuable to fraudsters. So, retail is particularly
vulnerable because retailers store large quantities of consumer data.” With so
much to lose, retailers should be taking more care to protect themselves, but
that is no easy feat. The scale of their operations means their businesses have
many moving parts. Their supply chains are long and complex, involving an
intricate and ever-changing network of suppliers. ... While external
cybersecurity advisors are often called in after a breach has occurred, it is
also wise to have them on board as a pre-emptive measure, as Kirsten Whitfield,
co-head of law firm Fieldfisher’s cyber breach team in London, explains “Get a
forensics provider on board to help close down an incident, and engage them in
advance, as they could stress test the systems against common attack vectors
from their knowledge of hacking groups,” she says. “Even engage a professional
ransomware negotiator who can profile attackers.” On the technical front, the
biggest challenge is to keep pace with the growth in AI. Hackers are using it,
so retailers need to invest in defensive AI to fight fire with fire. “Investing
as regulators expect you to will not necessarily mean you are iron clad,” says
Whitfield. “Hackers are increasingly sophisticated and use tools like AI, so it
is a good idea to invest in it, too, though you don’t want to rush into buying
AI that you think will protect you but has not been fully understood.”
“Stolen customer data is valuable to fraudsters. So, retail is particularly
vulnerable because retailers store large quantities of consumer data.” With so
much to lose, retailers should be taking more care to protect themselves, but
that is no easy feat. The scale of their operations means their businesses have
many moving parts. Their supply chains are long and complex, involving an
intricate and ever-changing network of suppliers. ... While external
cybersecurity advisors are often called in after a breach has occurred, it is
also wise to have them on board as a pre-emptive measure, as Kirsten Whitfield,
co-head of law firm Fieldfisher’s cyber breach team in London, explains “Get a
forensics provider on board to help close down an incident, and engage them in
advance, as they could stress test the systems against common attack vectors
from their knowledge of hacking groups,” she says. “Even engage a professional
ransomware negotiator who can profile attackers.” On the technical front, the
biggest challenge is to keep pace with the growth in AI. Hackers are using it,
so retailers need to invest in defensive AI to fight fire with fire. “Investing
as regulators expect you to will not necessarily mean you are iron clad,” says
Whitfield. “Hackers are increasingly sophisticated and use tools like AI, so it
is a good idea to invest in it, too, though you don’t want to rush into buying
AI that you think will protect you but has not been fully understood.”
No comments:
Post a Comment