Quote for the day:
"Life isn’t about getting and having, it’s about giving and being." -- Kevin Kruse
Browser agents don’t always respect your privacy choices
 A key issue is the location of the language model. Seven out of eight agents use
off device models. This means detailed information about the user’s browser
state and each visited webpage is sent to servers controlled by the service
provider. When the model runs on remote servers, users lose control over how
search queries and sensitive webpage content are processed and stored. While
some providers describe limits on data use, users must rely on service provider
policies. Browser version age is another factor. Browsers release frequent
updates to patch security flaws. One agent was found running a browser that was
16 major versions out of date at the time of testing. ... Agents also showed
weaknesses in TLS certificate handling. Two agents did not show warnings for
revoked certificates. One agent also failed to warn users about expired and self
signed certificates. Trusting connections with invalid certificates leaves
agents open to machine-in-the-middle attacks that allow attackers to read or
alter submitted information. ... Agent decision logic sometimes favored task
completion over protecting user information, leading to personal data
disclosure. This resulted in six vulnerabilities. Researchers supplied agents
with a fictitious identity and observed whether that information was shared with
websites under different conditions. Three agents disclosed personal information
during passive tests, where the requested data was not required to complete the
task.
A key issue is the location of the language model. Seven out of eight agents use
off device models. This means detailed information about the user’s browser
state and each visited webpage is sent to servers controlled by the service
provider. When the model runs on remote servers, users lose control over how
search queries and sensitive webpage content are processed and stored. While
some providers describe limits on data use, users must rely on service provider
policies. Browser version age is another factor. Browsers release frequent
updates to patch security flaws. One agent was found running a browser that was
16 major versions out of date at the time of testing. ... Agents also showed
weaknesses in TLS certificate handling. Two agents did not show warnings for
revoked certificates. One agent also failed to warn users about expired and self
signed certificates. Trusting connections with invalid certificates leaves
agents open to machine-in-the-middle attacks that allow attackers to read or
alter submitted information. ... Agent decision logic sometimes favored task
completion over protecting user information, leading to personal data
disclosure. This resulted in six vulnerabilities. Researchers supplied agents
with a fictitious identity and observed whether that information was shared with
websites under different conditions. Three agents disclosed personal information
during passive tests, where the requested data was not required to complete the
task. What CISOs should know about the SolarWinds lawsuit dismissal
 For many CISOs, the dismissal landed not as an abstract legal development, but
as something deeply personal. ... Even though the SolarWinds case sparked a
deeper recognition that cybersecurity responsibility should be a shared
responsibility across enterprises, shifting policy priorities and future
administrations could once again put CISOs in the SEC’s crosshairs, they warn.
... The judge’s reasoning reassured many security leaders, but it also exposed
a more profound discomfort about how accountability is assigned inside modern
organizations. “The area that a lot of us were really uncomfortable about was
the idea that an operational head of security could be personally responsible
for what the company says about its cybersecurity investments,” Sullivan says.
He adds, “Tim didn’t have the CISO title before the incident. And so there was
just a lot there that made security people very concerned. Why is this
operational person on the hook for representations?” But even if he had had
the CISO role before the incident, the argument still holds, according to
Sullivan. “Historically, the person who had that title wasn’t a quote-unquote
‘chief’ in the sense that they’re not in the little room of people who run the
company,” Sullivan says. ... If the SolarWinds case clarified anything, it’s
that relief is temporary and preparation is essential. CISOs have a window of
opportunity to shore up their organizational and personal defenses in the
event the political pendulum swings and makes CISOs litigation targets
again.
For many CISOs, the dismissal landed not as an abstract legal development, but
as something deeply personal. ... Even though the SolarWinds case sparked a
deeper recognition that cybersecurity responsibility should be a shared
responsibility across enterprises, shifting policy priorities and future
administrations could once again put CISOs in the SEC’s crosshairs, they warn.
... The judge’s reasoning reassured many security leaders, but it also exposed
a more profound discomfort about how accountability is assigned inside modern
organizations. “The area that a lot of us were really uncomfortable about was
the idea that an operational head of security could be personally responsible
for what the company says about its cybersecurity investments,” Sullivan says.
He adds, “Tim didn’t have the CISO title before the incident. And so there was
just a lot there that made security people very concerned. Why is this
operational person on the hook for representations?” But even if he had had
the CISO role before the incident, the argument still holds, according to
Sullivan. “Historically, the person who had that title wasn’t a quote-unquote
‘chief’ in the sense that they’re not in the little room of people who run the
company,” Sullivan says. ... If the SolarWinds case clarified anything, it’s
that relief is temporary and preparation is essential. CISOs have a window of
opportunity to shore up their organizational and personal defenses in the
event the political pendulum swings and makes CISOs litigation targets
again.Global uncertainty is reshaping cloud strategies in Europe
 Europe has been debating digital sovereignty for years, but the issue has
gained new urgency amid rising geopolitical tensions. “The political
environment is changing very fast,” said Ollrom. A combination of trade
disputes, sanctions that affect access to technology, and the possibility of
tariffs on digital services has prompted many European organizations to
reconsider their reliance on US hyperscaler clouds. ... What was once largely
a public-sector concern now attracts growing interest across a wide range of
private organizations as well. Accenture is currently working with around 50
large European organizations on digital-sovereignty-related projects, said
Capo. This includes banks, telcos, and logistics companies alongside clients
in government and defense. ... Another worry is the possibility that cloud
services will be swept up in future trade disputes. If the EU imposes
retaliatory tariffs on digital services, the cost of using hyperscaler cloud
platforms could hike overnight, and organizations heavily dependent on them
may find it hard to switch to a cheaper option. There’s also the prospect that
organizations could lose access to cloud services if sanctions or export
restrictions are imposed, leaving them temporarily or permanently locked out
of systems they rely on. It’s a remote risk, said Dario Maisto, a senior
analyst at Forrester, but a material one. “We are talking of a worst-case
scenario where IT gets leveraged as a weapon,” he said.
Europe has been debating digital sovereignty for years, but the issue has
gained new urgency amid rising geopolitical tensions. “The political
environment is changing very fast,” said Ollrom. A combination of trade
disputes, sanctions that affect access to technology, and the possibility of
tariffs on digital services has prompted many European organizations to
reconsider their reliance on US hyperscaler clouds. ... What was once largely
a public-sector concern now attracts growing interest across a wide range of
private organizations as well. Accenture is currently working with around 50
large European organizations on digital-sovereignty-related projects, said
Capo. This includes banks, telcos, and logistics companies alongside clients
in government and defense. ... Another worry is the possibility that cloud
services will be swept up in future trade disputes. If the EU imposes
retaliatory tariffs on digital services, the cost of using hyperscaler cloud
platforms could hike overnight, and organizations heavily dependent on them
may find it hard to switch to a cheaper option. There’s also the prospect that
organizations could lose access to cloud services if sanctions or export
restrictions are imposed, leaving them temporarily or permanently locked out
of systems they rely on. It’s a remote risk, said Dario Maisto, a senior
analyst at Forrester, but a material one. “We are talking of a worst-case
scenario where IT gets leveraged as a weapon,” he said.What the AWS outage taught CIOs about preparedness
For many organizations, the event felt like a cyber incident even though it
wasn’t, but it raised a difficult question for CIOs about how to prepare for a
disruption that lives outside your infrastructure, yet carries the same
operational and reputational consequences as a security breach. ... Beyond
strong cloud architecture, “Preparedness is the real differentiator,” he says.
“Even the best technology teams can’t compensate for gaps in scenario
planning, coordination, and governance.” ... Within Deluxe, disaster recovery
tests historically focused on applications the company controlled, while cyber
tabletops focused on simulated intrusions. The AWS outage exposed the gap
between those exercises and real-world conditions. Shifting its applications
from AWS East to AWS West was swift, and the technology team considered the
recovery a success. Yet it was far from business as usual, as developers still
couldn’t access critical tools like GitHub or Jira. “We thought we’d
recovered, but the day-to-day work couldn’t continue because the tools we
depend on were down,” he says. ... In a well-architected hybrid cloud setup,
he says resilience is more often a coordination problem than a spending
problem, and distributing workloads across two cloud providers doesn’t
guarantee better outcomes if the clouds rely on the same power grid, or
experience the same regional failure event. ... Jayaprakasam is candid about
the cultural challenge that comes with resilience work.
 “Four or five years ago, we were seeing sub-ten-kilowatt racks, and today
we're being asked for between 100 and 150 kilowatts, which makes a whole
magnitude of difference,” says Osian. “And this trend is going to continue to
rise, meaning we have to mobilize for tomorrow’s power challenges, today.”
Rising power demands also require higher available fault currents to safely
handle larger, more dynamic surges in the circuit. Supporting equipment must
be more resilient and reliable to maintain safe and efficient distribution.
With change happening so quickly, adopting a long-term strategy is essential.
This requires building critical infrastructure with adaptability and
flexibility at its core. ... A modular approach offers another tactical
advantage: speed. With a traditional RPP setup, getting power physically
hooked up from A to B on a per-rack basis is time and resource-consuming,
especially at first installation. By reducing complexity with a plug-and-play
modular design slotted in directly over the racks, the busway delivers the
swift reinforcements modern facilities need to stay ahead. ... “One of the
advancements we've made in the last year is creating a way for users to add a
circuit from outside the arc flash boundary. While the Starline busway is
already rated for live insertion – meaning it’s safe out of the box – we’ve
taken safety to the next level with a device called the Remote Plugin
Actuator. It allows a user to add a circuit to the busway without engaging any
of the electrical contacts directly.”
“Four or five years ago, we were seeing sub-ten-kilowatt racks, and today
we're being asked for between 100 and 150 kilowatts, which makes a whole
magnitude of difference,” says Osian. “And this trend is going to continue to
rise, meaning we have to mobilize for tomorrow’s power challenges, today.”
Rising power demands also require higher available fault currents to safely
handle larger, more dynamic surges in the circuit. Supporting equipment must
be more resilient and reliable to maintain safe and efficient distribution.
With change happening so quickly, adopting a long-term strategy is essential.
This requires building critical infrastructure with adaptability and
flexibility at its core. ... A modular approach offers another tactical
advantage: speed. With a traditional RPP setup, getting power physically
hooked up from A to B on a per-rack basis is time and resource-consuming,
especially at first installation. By reducing complexity with a plug-and-play
modular design slotted in directly over the racks, the busway delivers the
swift reinforcements modern facilities need to stay ahead. ... “One of the
advancements we've made in the last year is creating a way for users to add a
circuit from outside the arc flash boundary. While the Starline busway is
already rated for live insertion – meaning it’s safe out of the box – we’ve
taken safety to the next level with a device called the Remote Plugin
Actuator. It allows a user to add a circuit to the busway without engaging any
of the electrical contacts directly.”
Winning the density war: The shift from RPPs to scalable busway infrastructure in next-gen facilities
 “Four or five years ago, we were seeing sub-ten-kilowatt racks, and today
we're being asked for between 100 and 150 kilowatts, which makes a whole
magnitude of difference,” says Osian. “And this trend is going to continue to
rise, meaning we have to mobilize for tomorrow’s power challenges, today.”
Rising power demands also require higher available fault currents to safely
handle larger, more dynamic surges in the circuit. Supporting equipment must
be more resilient and reliable to maintain safe and efficient distribution.
With change happening so quickly, adopting a long-term strategy is essential.
This requires building critical infrastructure with adaptability and
flexibility at its core. ... A modular approach offers another tactical
advantage: speed. With a traditional RPP setup, getting power physically
hooked up from A to B on a per-rack basis is time and resource-consuming,
especially at first installation. By reducing complexity with a plug-and-play
modular design slotted in directly over the racks, the busway delivers the
swift reinforcements modern facilities need to stay ahead. ... “One of the
advancements we've made in the last year is creating a way for users to add a
circuit from outside the arc flash boundary. While the Starline busway is
already rated for live insertion – meaning it’s safe out of the box – we’ve
taken safety to the next level with a device called the Remote Plugin
Actuator. It allows a user to add a circuit to the busway without engaging any
of the electrical contacts directly.”
“Four or five years ago, we were seeing sub-ten-kilowatt racks, and today
we're being asked for between 100 and 150 kilowatts, which makes a whole
magnitude of difference,” says Osian. “And this trend is going to continue to
rise, meaning we have to mobilize for tomorrow’s power challenges, today.”
Rising power demands also require higher available fault currents to safely
handle larger, more dynamic surges in the circuit. Supporting equipment must
be more resilient and reliable to maintain safe and efficient distribution.
With change happening so quickly, adopting a long-term strategy is essential.
This requires building critical infrastructure with adaptability and
flexibility at its core. ... A modular approach offers another tactical
advantage: speed. With a traditional RPP setup, getting power physically
hooked up from A to B on a per-rack basis is time and resource-consuming,
especially at first installation. By reducing complexity with a plug-and-play
modular design slotted in directly over the racks, the busway delivers the
swift reinforcements modern facilities need to stay ahead. ... “One of the
advancements we've made in the last year is creating a way for users to add a
circuit from outside the arc flash boundary. While the Starline busway is
already rated for live insertion – meaning it’s safe out of the box – we’ve
taken safety to the next level with a device called the Remote Plugin
Actuator. It allows a user to add a circuit to the busway without engaging any
of the electrical contacts directly.”Building a data-driven, secure and future-ready manufacturing enterprise: Technology as a strategic backbone
A central pillar of Prince Pipes and Fittings’ digital strategy is data democratisation. The organisation has moved decisively away from static reports towards dynamic, self-service analytics. A centralised data platform for sales and supply chain allows business users to create their own dashboards without dependence on IT teams. Desai further states, “Sales teams, for instance, can access granular data on their smartphones while interacting with customers, instantly showcasing performance metrics and trends. This empowerment has not only improved responsiveness but has also enhanced user confidence and satisfaction. Across functions, data is now guiding actions rather than merely describing outcomes.” ... Technology transformation at Prince Pipes and Fittings has been accompanied by a conscious effort to drive cultural change. Leadership recognised early that democratising data would require a mindset shift across the organisation. Initial resistance was addressed through structured training programs conducted zone-wise and state-wise, helping users build familiarity and confidence with new platforms. ... Cyber security is treated as a business-critical priority at Prince Pipes and Fittings. The organisation has implemented a phase-wise, multi-layered cyber security framework spanning both IT and OT environments. A simple yet effective risk-classification approach i.e. green, yellow, and red, was used to identify gaps and prioritise actions. ... Equally important has been the focus on human awareness.The Next Fraud Problem Isn’t in Finance. It’s in Hiring: The New Attack Surface
 The uncomfortable truth is that the interview has become a transaction. And
the “asset” being transferred is not a paycheck. It’s access: to systems,
data, colleagues, customers, and internal credibility. ... Payment fraud works
because the system is trying to be fast. The same is true in hiring. Speed is
rewarded. Friction is avoided. And that creates a predictable failure mode: an
attacker’s job is to make the process feel normal long enough to get to
“approved.” In payments, fraudsters use stolen cards and compromised accounts.
In hiring, they can use stolen faces, voices, credentials, and employment
histories. The mechanics differ, but the objective is identical: get the
system to say yes. That’s why the right question for leaders is not, “Can we
spot a deepfake?” It’s, “What controls do we have before we grant access?” ...
Many companies verify identity late, during onboarding, after decisions are
emotionally and operationally “locked.” That’s the equivalent of shipping a
product and hoping the card wasn’t stolen. Instead, introduce light identity
proofing before final rounds or before any access-related steps. ... In
payments, the critical moment is authorization. In hiring, it’s when you
provision accounts, ship hardware, grant repository permissions, or provide
access to customer or financial systems. That moment deserves a
deliberate gate: confirm identity through a known-good channel, verify
references without relying on contact info provided by the candidate, and run
a final live verification step before credentials are issued.
The uncomfortable truth is that the interview has become a transaction. And
the “asset” being transferred is not a paycheck. It’s access: to systems,
data, colleagues, customers, and internal credibility. ... Payment fraud works
because the system is trying to be fast. The same is true in hiring. Speed is
rewarded. Friction is avoided. And that creates a predictable failure mode: an
attacker’s job is to make the process feel normal long enough to get to
“approved.” In payments, fraudsters use stolen cards and compromised accounts.
In hiring, they can use stolen faces, voices, credentials, and employment
histories. The mechanics differ, but the objective is identical: get the
system to say yes. That’s why the right question for leaders is not, “Can we
spot a deepfake?” It’s, “What controls do we have before we grant access?” ...
Many companies verify identity late, during onboarding, after decisions are
emotionally and operationally “locked.” That’s the equivalent of shipping a
product and hoping the card wasn’t stolen. Instead, introduce light identity
proofing before final rounds or before any access-related steps. ... In
payments, the critical moment is authorization. In hiring, it’s when you
provision accounts, ship hardware, grant repository permissions, or provide
access to customer or financial systems. That moment deserves a
deliberate gate: confirm identity through a known-good channel, verify
references without relying on contact info provided by the candidate, and run
a final live verification step before credentials are issued. Agent autonomy without guardrails is an SRE nightmare
 Four-in-10 tech leaders regret not establishing a stronger governance
foundation from the start, which suggests they adopted AI rapidly, but with
margin to improve on policies, rules and best practices designed to ensure the
responsible, ethical and legal development and use of AI. ... When considering
tasks for AI agents, organizations should understand that, while traditional
automation is good at handling repetitive, rule-based processes with
structured data inputs, AI agents can handle much more complex tasks and adapt
to new information in a more autonomous way. This makes them an appealing
solution for all sorts of tasks. But as AI agents are deployed, organizations
should control what actions the agents can take, particularly in the early
stages of a project. Thus, teams working with AI agents should have approval
paths in place for high-impact actions to ensure agent scope does not extend
beyond expected use cases, minimizing risk to the wider system. ... Further,
AI agents should not be allowed free rein across an organization’s systems. At
a minimum, the permissions and security scope of an AI agent must be aligned
with the scope of the owner, and any tools added to the agent should not allow
for extended permissions. Limiting AI agent access to a system based on their
role will also ensure deployment runs smoothly. Keeping complete logs of every
action taken by an AI agent can also help engineers understand what happened
in the event of an incident and trace back the problem.
Four-in-10 tech leaders regret not establishing a stronger governance
foundation from the start, which suggests they adopted AI rapidly, but with
margin to improve on policies, rules and best practices designed to ensure the
responsible, ethical and legal development and use of AI. ... When considering
tasks for AI agents, organizations should understand that, while traditional
automation is good at handling repetitive, rule-based processes with
structured data inputs, AI agents can handle much more complex tasks and adapt
to new information in a more autonomous way. This makes them an appealing
solution for all sorts of tasks. But as AI agents are deployed, organizations
should control what actions the agents can take, particularly in the early
stages of a project. Thus, teams working with AI agents should have approval
paths in place for high-impact actions to ensure agent scope does not extend
beyond expected use cases, minimizing risk to the wider system. ... Further,
AI agents should not be allowed free rein across an organization’s systems. At
a minimum, the permissions and security scope of an AI agent must be aligned
with the scope of the owner, and any tools added to the agent should not allow
for extended permissions. Limiting AI agent access to a system based on their
role will also ensure deployment runs smoothly. Keeping complete logs of every
action taken by an AI agent can also help engineers understand what happened
in the event of an incident and trace back the problem. Where Architects Sit in the Era of AI
/filters:no_upscale()/articles/architects-ai-era/en/resources/128figure-2-1765966955803.jpg) In the emerging AI-augmented ecosystem, we can think of three modes of
architect involvement: Architect in the loop, Architect on the loop, and
Architect out of the loop. Each reflects a different level of engagement,
oversight, and trust between an Architect and intelligent systems. ... What
does it mean to be in the loop? In the Architect in the Loop (AITL) model, the
architect and the AI system work side by side. AI provides options, generates
designs, or analyzes trade-offs, but humans remain the decision-makers. Every
output is reviewed, contextualized, and approved by an architect who
understands both the technical and organizational context. This is where the
Architect is sat in the middle of AI interactions ... What does it mean to be
on the loop? As AI matures, parts of architectural decision-making can be
safely delegated. In the Architect on the Loop (AOTL) model, the AI operates
autonomously within predefined boundaries, while the architect supervises,
reviews, and intervenes when necessary. This is where the architect is firmly
embedded into the development workflow using AI to augment and enhance their
own natural abilities. ... What does it mean to be out of the loop? In the
AOOTL model, we see a world where the architect is no longer required in the
traditional fashion. The architectural work of domain understanding, context
providing, and design thinking is simply all done by AI, with the outputs of
AI being used by managers, developers, and others to build the right systems
at the right time.
In the emerging AI-augmented ecosystem, we can think of three modes of
architect involvement: Architect in the loop, Architect on the loop, and
Architect out of the loop. Each reflects a different level of engagement,
oversight, and trust between an Architect and intelligent systems. ... What
does it mean to be in the loop? In the Architect in the Loop (AITL) model, the
architect and the AI system work side by side. AI provides options, generates
designs, or analyzes trade-offs, but humans remain the decision-makers. Every
output is reviewed, contextualized, and approved by an architect who
understands both the technical and organizational context. This is where the
Architect is sat in the middle of AI interactions ... What does it mean to be
on the loop? As AI matures, parts of architectural decision-making can be
safely delegated. In the Architect on the Loop (AOTL) model, the AI operates
autonomously within predefined boundaries, while the architect supervises,
reviews, and intervenes when necessary. This is where the architect is firmly
embedded into the development workflow using AI to augment and enhance their
own natural abilities. ... What does it mean to be out of the loop? In the
AOOTL model, we see a world where the architect is no longer required in the
traditional fashion. The architectural work of domain understanding, context
providing, and design thinking is simply all done by AI, with the outputs of
AI being used by managers, developers, and others to build the right systems
at the right time.Cloud Migration of Microservices: Strategy, Risks, and Best Practices
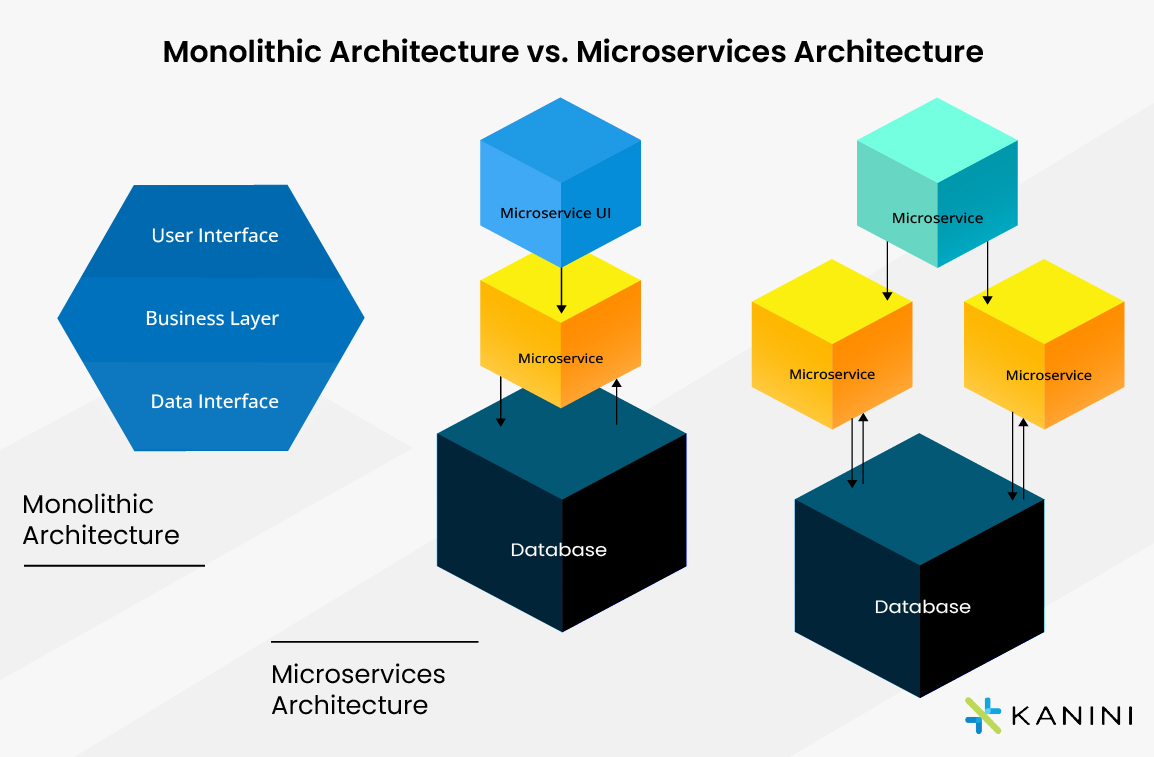 The migration of microservices to the cloud is a crucial step in the digital
transformation process, requiring a strategic approach to ensure success. The
success of the migration depends on carefully selecting the appropriate
strategy based on the current architecture's maturity, technical debt,
business objectives, and cloud infrastructure capabilities. ... The simplest
strategy for migrating to the cloud is Rehost. This involves moving
applications as is to virtual machines in the cloud. According to research,
around 40% of organizations begin their migration with Rehost, as it allows
for a quick transition to the cloud with minimal costs. However, this approach
often does not provide significant performance or cost benefits, as it does
not fully utilize cloud capabilities. Replatform is the next level of
complexity, where applications are partially adapted. For example, databases
may be migrated to cloud services like Amazon RDS or Azure SQL, file storage
may be replaced, and containerization may be introduced. Replatform is used in
around 22% of cases where there is a need to strike a balance between speed
and the depth of changes. A more time-consuming but strategically beneficial
approach is Refactoring (or Rearchitecting), in which the application
undergoes a significant redesign: microservices are introduced, Kubernetes,
Kafka, and cloud functions (such as Lambda and Azure Functions) are utilized,
as well as a service bus.
The migration of microservices to the cloud is a crucial step in the digital
transformation process, requiring a strategic approach to ensure success. The
success of the migration depends on carefully selecting the appropriate
strategy based on the current architecture's maturity, technical debt,
business objectives, and cloud infrastructure capabilities. ... The simplest
strategy for migrating to the cloud is Rehost. This involves moving
applications as is to virtual machines in the cloud. According to research,
around 40% of organizations begin their migration with Rehost, as it allows
for a quick transition to the cloud with minimal costs. However, this approach
often does not provide significant performance or cost benefits, as it does
not fully utilize cloud capabilities. Replatform is the next level of
complexity, where applications are partially adapted. For example, databases
may be migrated to cloud services like Amazon RDS or Azure SQL, file storage
may be replaced, and containerization may be introduced. Replatform is used in
around 22% of cases where there is a need to strike a balance between speed
and the depth of changes. A more time-consuming but strategically beneficial
approach is Refactoring (or Rearchitecting), in which the application
undergoes a significant redesign: microservices are introduced, Kubernetes,
Kafka, and cloud functions (such as Lambda and Azure Functions) are utilized,
as well as a service bus.
No comments:
Post a Comment