Defining the web3 stack
 There are a lot of differences in the way that we interact with and build on
top of blockchains versus databases in the traditional tech stack. With
blockchains, data isn’t stored in a format that can efficiently or easily be
consumed directly from other applications or front ends. Blockchains are
optimized for write operations. You often hear the innovation happening centered
around transactions per second, block time, and transaction cost. Blockchain
data is written in blocks over the course of time, making anything other than
basic read operations impossible. In most applications, you need features like
relational data, sorting, filtering, full text search, pagination and many other
types of querying capabilities. In order to do this, data needs to be indexed
and organized for efficient retrieval. Traditionally, that’s the work that
databases do in the centralized tech stack, but that indexing layer was missing
in the web3 stack. The Graph is a protocol for indexing and querying
blockchain data that makes this process much easier and offers a decentralized
solution for doing so. Anyone can build and publish open GraphQL APIs, called
subgraphs, making blockchain data easy to query.
There are a lot of differences in the way that we interact with and build on
top of blockchains versus databases in the traditional tech stack. With
blockchains, data isn’t stored in a format that can efficiently or easily be
consumed directly from other applications or front ends. Blockchains are
optimized for write operations. You often hear the innovation happening centered
around transactions per second, block time, and transaction cost. Blockchain
data is written in blocks over the course of time, making anything other than
basic read operations impossible. In most applications, you need features like
relational data, sorting, filtering, full text search, pagination and many other
types of querying capabilities. In order to do this, data needs to be indexed
and organized for efficient retrieval. Traditionally, that’s the work that
databases do in the centralized tech stack, but that indexing layer was missing
in the web3 stack. The Graph is a protocol for indexing and querying
blockchain data that makes this process much easier and offers a decentralized
solution for doing so. Anyone can build and publish open GraphQL APIs, called
subgraphs, making blockchain data easy to query.The rise and rebirth of P2P file sharing – and why it will matter in 2022
 The Internet itself was designed from the very beginning to be decentralised.
The fact that most of our data and computing ended up being centralised on Big
Tech’s cloud platforms is something of an evolutionary fluke. To understand why,
it is helpful to have some historical context. We can think of the evolution of
the Internet as being divided into four distinct phases. The First Internet (the
“Al Gore Internet”) was about connecting computers together over a global
network for the first time. The Second Internet was about getting people and
businesses online and conducting commerce digitally for the first time. The
Third Internet, the one we’re still in now, was all about mobile computing. The
scale challenges created by the sudden demand for smartphones and their apps
created intense economic pressure to centralise. Housing millions of similar
servers in gigantic data centres was and is more economically efficient, and
technically “good enough” for the mobile apps of the day.
The Internet itself was designed from the very beginning to be decentralised.
The fact that most of our data and computing ended up being centralised on Big
Tech’s cloud platforms is something of an evolutionary fluke. To understand why,
it is helpful to have some historical context. We can think of the evolution of
the Internet as being divided into four distinct phases. The First Internet (the
“Al Gore Internet”) was about connecting computers together over a global
network for the first time. The Second Internet was about getting people and
businesses online and conducting commerce digitally for the first time. The
Third Internet, the one we’re still in now, was all about mobile computing. The
scale challenges created by the sudden demand for smartphones and their apps
created intense economic pressure to centralise. Housing millions of similar
servers in gigantic data centres was and is more economically efficient, and
technically “good enough” for the mobile apps of the day.
Former Uber CSO Faces New Charge for Alleged Breach Cover-Up
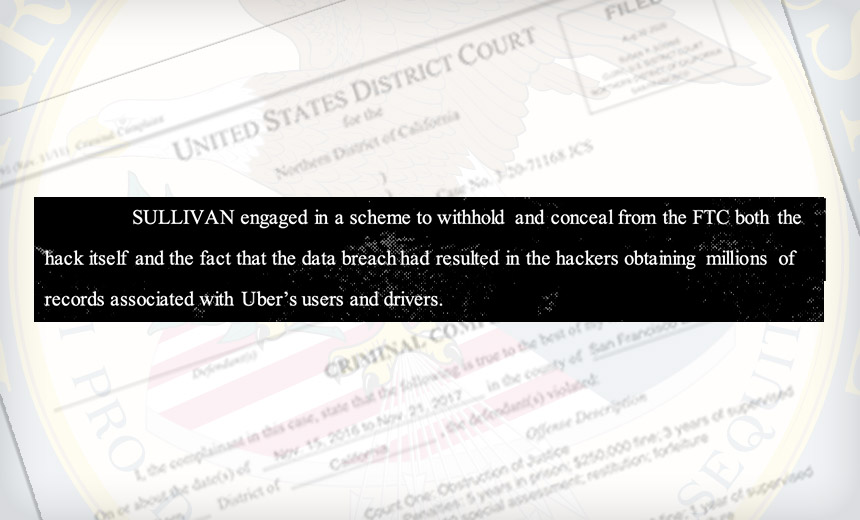 The government's case hinges on Sullivan's alleged failure to report a 2016 data
breach to authorities, which prosecutors accuse him of having mischaracterized
as a less severe security incident, together with his allegedly paying hackers
"hush money" to conceal the breach. When hackers emailed Uber in November 2016
to inform it of a breach they had perpetrated, the ride-sharing service was in
the process of providing detailed answers to the Federal Trade Commission,
stemming from a September 2014 breach. Prosecutors say that as the person
nominated by Uber to provide sworn testimony to the FTC, Sullivan should have
immediately disclosed the breach to the FTC and - in accordance with
California's data breach notification law - Uber should have notified all
affected state residents that their personal details had been obtained by
attackers. "Institutions that store personal information of others must comply
with the law," says Stephanie M. Hinds, the acting U.S. Attorney for the
Northern District of California, where Sullivan formerly served as a federal
prosecutor.
The government's case hinges on Sullivan's alleged failure to report a 2016 data
breach to authorities, which prosecutors accuse him of having mischaracterized
as a less severe security incident, together with his allegedly paying hackers
"hush money" to conceal the breach. When hackers emailed Uber in November 2016
to inform it of a breach they had perpetrated, the ride-sharing service was in
the process of providing detailed answers to the Federal Trade Commission,
stemming from a September 2014 breach. Prosecutors say that as the person
nominated by Uber to provide sworn testimony to the FTC, Sullivan should have
immediately disclosed the breach to the FTC and - in accordance with
California's data breach notification law - Uber should have notified all
affected state residents that their personal details had been obtained by
attackers. "Institutions that store personal information of others must comply
with the law," says Stephanie M. Hinds, the acting U.S. Attorney for the
Northern District of California, where Sullivan formerly served as a federal
prosecutor.
Council Post: Reflecting On The Cost Of Our Dream To Build The Coveted General AI
 The powerful language models and the newer zero-shot text-to-image generation
models are all marching really fast towards the intended goal of performing
tasks for which they were not trained. Each one is outwitting the previous one
for its applications and uses. DeepMind, one of the most well known AI
research institutes (owned by Alphabet), has centred its ultimate goal at
achieving AGI. Interestingly, this year, the lab published a paper titled
‘Reward Is Enough‘, where the authors suggested that techniques like reward
maximisation can help machines develop behaviour that exhibits abilities
associated with intelligence. They further concluded that reward maximisation
and reinforcement learning, in extension, can help achieve artificial general
intelligence. Let’s take a closer look at GPT-3 created by DeepMind’s closest
competitor, OpenAI, which created a major buzz in the scientific community. It
was widely considered a massive breakthrough when achieving General AI.
The powerful language models and the newer zero-shot text-to-image generation
models are all marching really fast towards the intended goal of performing
tasks for which they were not trained. Each one is outwitting the previous one
for its applications and uses. DeepMind, one of the most well known AI
research institutes (owned by Alphabet), has centred its ultimate goal at
achieving AGI. Interestingly, this year, the lab published a paper titled
‘Reward Is Enough‘, where the authors suggested that techniques like reward
maximisation can help machines develop behaviour that exhibits abilities
associated with intelligence. They further concluded that reward maximisation
and reinforcement learning, in extension, can help achieve artificial general
intelligence. Let’s take a closer look at GPT-3 created by DeepMind’s closest
competitor, OpenAI, which created a major buzz in the scientific community. It
was widely considered a massive breakthrough when achieving General AI.How AI, VR, AR, 5G, and blockchain may converge to power the metaverse
 Several of the technologies that will enable the metaverse, including virtual
and augmented reality and blockchain, have been slow to mature but are
approaching a level of capability that is critical for success. Each has been
missing the killer app that will drive development and widespread adoption
forward. The metaverse could be that app. For VR, most headsets still need to
be tethered to a PC or gaming console to achieve the processing power and
communication speed required for smooth and immersive experiences. Only Meta’s
Oculus Quest 2 has so far broken free of this cable constraint. But even that
headset remains bulky, according to one of Meta’s VPs. With ever faster
processors and higher speed wireless communications on the near horizon,
better visual resolution and untethered experiences should emerge over the
next few years. AR has achieved mostly niche adoption. In part, AR prospects
likely suffered due to the high-profile market failure of Google Glass when
introduced in 2012.
Several of the technologies that will enable the metaverse, including virtual
and augmented reality and blockchain, have been slow to mature but are
approaching a level of capability that is critical for success. Each has been
missing the killer app that will drive development and widespread adoption
forward. The metaverse could be that app. For VR, most headsets still need to
be tethered to a PC or gaming console to achieve the processing power and
communication speed required for smooth and immersive experiences. Only Meta’s
Oculus Quest 2 has so far broken free of this cable constraint. But even that
headset remains bulky, according to one of Meta’s VPs. With ever faster
processors and higher speed wireless communications on the near horizon,
better visual resolution and untethered experiences should emerge over the
next few years. AR has achieved mostly niche adoption. In part, AR prospects
likely suffered due to the high-profile market failure of Google Glass when
introduced in 2012. The Dark Web Has Its Own People's Court
 Threat actors operating in large underground forums often are quick to comply
with underground court decisions because they want to protect their
reputations. "Criminals work hard to build their reputation on these forums,"
DiMaggio says. "These forums are where ransomware affiliate recruiting takes
place as well as malware sales, breach, and exploit access, and even hacking
services are offered." Losing trust or getting banned from a forum can have a
huge negative impact on a threat actor's ability to operate in the cyber
underground, he says. In some extreme cases, threat actors have exposed the
true identities of the cybercriminals — including physical address, social
media profiles, and phone numbers — that might have scammed them, Analyst1
said. John Hammond, senior security researcher at Huntress, says practically
every cybercrime forum or bulletin board has a sort of judicial system, or a
"people's court" for handling disputes among criminals. "It's a strange sort
of sportsmanship or code of conduct, where hackers, thieves, and scammers
should not cross each other," he says.
Threat actors operating in large underground forums often are quick to comply
with underground court decisions because they want to protect their
reputations. "Criminals work hard to build their reputation on these forums,"
DiMaggio says. "These forums are where ransomware affiliate recruiting takes
place as well as malware sales, breach, and exploit access, and even hacking
services are offered." Losing trust or getting banned from a forum can have a
huge negative impact on a threat actor's ability to operate in the cyber
underground, he says. In some extreme cases, threat actors have exposed the
true identities of the cybercriminals — including physical address, social
media profiles, and phone numbers — that might have scammed them, Analyst1
said. John Hammond, senior security researcher at Huntress, says practically
every cybercrime forum or bulletin board has a sort of judicial system, or a
"people's court" for handling disputes among criminals. "It's a strange sort
of sportsmanship or code of conduct, where hackers, thieves, and scammers
should not cross each other," he says.Digital transformation: 4 tips to be a successful IT leader in 2022
 Digital transformation can be overwhelming. You may be tempted to hand over
the reins to a consulting service that has a track record of success
implementing these new initiatives. It is important to know how to determine
if this is the right option for your organization. Digital transformation
often requires disruptive, cross-organizational change. Bringing in an outside
expert can be the right answer. A transformation expert can help smooth
transitions and have previous success to show as evidence for why the change
is beneficial. If you do decide to bring in an outside partner, make sure that
the team has subject matter experts familiar with your vertical. When vetting
consulting partners, choose a team that is committed to learning the history
of your business, the processes you have in place, and even your internal
relationships. Bringing on a partner that is interested in integrating into
your organization while the transformation happens can reduce friction and
increase your likelihood of success.
Digital transformation can be overwhelming. You may be tempted to hand over
the reins to a consulting service that has a track record of success
implementing these new initiatives. It is important to know how to determine
if this is the right option for your organization. Digital transformation
often requires disruptive, cross-organizational change. Bringing in an outside
expert can be the right answer. A transformation expert can help smooth
transitions and have previous success to show as evidence for why the change
is beneficial. If you do decide to bring in an outside partner, make sure that
the team has subject matter experts familiar with your vertical. When vetting
consulting partners, choose a team that is committed to learning the history
of your business, the processes you have in place, and even your internal
relationships. Bringing on a partner that is interested in integrating into
your organization while the transformation happens can reduce friction and
increase your likelihood of success.
The Secret of Delivering Machine Learning to Production
87% of ML projects are eventually not delivered to production (VB). This article from 2019 is cited in almost every MLOps startup pitch deck, and this number is well-established in the ML discourse. To be totally honest, I have tried to trace back this number and figure out how it was retrieved — and didn’t find any reliable source or research to support it. However, this number seems quite reasonable if you also consider projects that were stopped at an early stage of PoC. The more painful number is the relative amount of projects that were already committed to the management or even to customers, in which significant efforts have already been invested — that were terminated before (or after) hitting production. In my previous post: “how to run due diligence for ML teams”, I give a high-level overview of the ingredients of successful ML teams. Here, you can find some practical advice on how to build high-impact ML teams. Companies invest millions in ML teams, employing top talent and paying accordingly, and the question hanging over this is: “does it worth it?”IoT predictions for 2022: the what, why and how of the year ahead
 Internet everywhere is gaining traction, as satellite narrowband IoT is poised
to plug the gap between terrestrial mobile connectivity services and
non-cellular IoT networks. At present, ground-based connectivity services are
far from ubiquitous, with vast tranches of the Earth’s surface not covered by
cellular networks. This presents a colossal opportunity for satellite IoT,
which solves the problem of mobile connectivity in remote locations. Potential
applications include asset tracking, oil and gas industries, utilities,
manufacturing and construction. Although Starlink is probably the most
prominent exponent of satellite IoT, there’s a growing number of companies
lining up to harness this new technology. 2022 could be a watershed year for
the tech, helping to spawn new sectors and bring niche markets towards the
mainstream. Digital twins are nothing new, but the terminology is
beginning to cut through into everyday tech language. Being able to interpret
physical objects in digital form with overlaid data to create a digital twin
allows for highly complex simulations.
Internet everywhere is gaining traction, as satellite narrowband IoT is poised
to plug the gap between terrestrial mobile connectivity services and
non-cellular IoT networks. At present, ground-based connectivity services are
far from ubiquitous, with vast tranches of the Earth’s surface not covered by
cellular networks. This presents a colossal opportunity for satellite IoT,
which solves the problem of mobile connectivity in remote locations. Potential
applications include asset tracking, oil and gas industries, utilities,
manufacturing and construction. Although Starlink is probably the most
prominent exponent of satellite IoT, there’s a growing number of companies
lining up to harness this new technology. 2022 could be a watershed year for
the tech, helping to spawn new sectors and bring niche markets towards the
mainstream. Digital twins are nothing new, but the terminology is
beginning to cut through into everyday tech language. Being able to interpret
physical objects in digital form with overlaid data to create a digital twin
allows for highly complex simulations. How Space Shapes Collaboration: Using Anthropology to Break Silos
In general, office space or architecture must be considered one of the aspects that can improve or hinder collaboration, but it is not the only one. Ideally, there should be a good mix of rituals, spaces, and rules that make people's work easier and make them feel connected to their co-workers. Another wonderful example is a ritual from a London marketing agency. Every Friday a different person on the staff pushed a trolley filled with wine and beer offering one glass of something to each employee. The person had to introduce themselves if they were new and ask the colleague how their week had gone. From the boss to the doorman, everyone had to push the trolley at some point. ... company culture and framework can significantly lower barriers, even in virtual space. Companies like Accenture, Cisco or Lego work with Scaled Agile (SAFe). This framework actively facilitates collaboration, at the team level, at the role level, and also between colleagues on different teams.Quote for the day:
"Remember teamwork begins by building trust. And the only way to do that is to overcome our need for invulnerability." -- Patrick Lencioni
No comments:
Post a Comment