IT threat evolution Q3 2021

Earlier this year, while investigating the rise of attacks against Exchange
servers, we noticed a recurring cluster of activity that appeared in several
distinct compromised networks. We attribute the activity to a previously unknown
threat actor that we have called GhostEmperor. This cluster stood out because it
used a formerly unknown Windows kernel mode rootkit that we dubbed Demodex; and
a sophisticated multi-stage malware framework aimed at providing remote control
over the attacked servers. The rootkit is used to hide the user mode malware’s
artefacts from investigators and security solutions, while demonstrating an
interesting loading scheme involving the kernel mode component of an open-source
project named Cheat Engine to bypass the Windows Driver Signature Enforcement
mechanism. ... The majority of GhostEmperor infections were deployed on
public-facing servers, as many of the malicious artefacts were installed by the
httpd.exe Apache server process, the w3wp.exe IIS Windows server process, or the
oc4j.jar Oracle server process.
USB Devices the Common Denominator in All Attacks on Air-Gapped Systems

There have been numerous instances over the past several years where threat
actors managed to bridge the air gap and access mission-critical systems and
infrastructure. The Stuxnet attack on Iran — believed to have been led by US and
Israeli cybersecurity teams — remains one of the most notable examples. In that
campaign, operatives managed to insert a USB device containing the Stuxnet worm
into a target Windows system, where it exploited a vulnerability (CVE-2010-2568)
that triggered a chain of events that eventually resulted in numerous
centrifuges at Iran's Natanz uranium enrichment facility being destroyed. Other
frameworks that have been developed and used in attacks on air-gapped systems
over the years include South Korean hacking group DarkHotel's Ramsay,
China-based Mustang Panda's PlugX, the likely NSA-affiliated Equation Group's
Fanny, and China-based Goblin Panda's USBCulprit. ESET analyzed these malware
frameworks, and others that have not be specifically attributed to any group
such as ProjectSauron and agent.btz.
How to do data science without big data

When you have visibility on the organizational strategy and the business
problems to be solved, the next step is to finalize your analytics approach.
Find out whether you need descriptive, diagnostic, or predictive analytics and
how the insights will be used. This will clarify the data you should collect. If
sourcing data is a challenge, phase out the collection process to allow for
iterative progress with the analytics solution. For example, executives at a
large computer manufacturer we worked with wanted to understand what drove
customer satisfaction, so they set up a customer experience analytics program
that started with direct feedback from the customer through voice-of-customer
surveys. Descriptive insights presented as data stories helped improve the net
promoter scores during the next survey. Over the next few quarters, they
expanded their analytics to include social media feedback and competitor
performance using sources such as Twitter, discussion forums, and double-blind
market surveys. To analyze this data, they used advanced machine learning
techniques.
Applying Social Leadership to Enhance Collaboration and Nurture Communities
Social leadership seems to differ as it is not a form of leadership that is
granted, as is often the case in formal hierarchical environments.
Organisations that have more “traditional management” structures and
approaches tend to grant managers authority, accountabilities and power. Also,
as I imagine you have seen, there has been much commentary over the years on
the fact that management and leadership are not the same things. Some years
ago when I was undertaking the Chartered Manager program with the Chartered
Management Institute(CMI), I came across the definition that Management is
“doing things right,” whereas leadership is “doing the right thing”. I find
this succinct explanation of the difference refreshing and have continued to
use this within my own coaching and mentoring work since. It feels to me that
“doing the right thing” is the modus operandi of the social leader. Also, we
talk a lot about the problems with accidental managers: those who have been
promoted into managerial roles, often by having in the past been successful in
their technical domains.
Report: APTs Adopting New Phishing Methods to Drop Payload
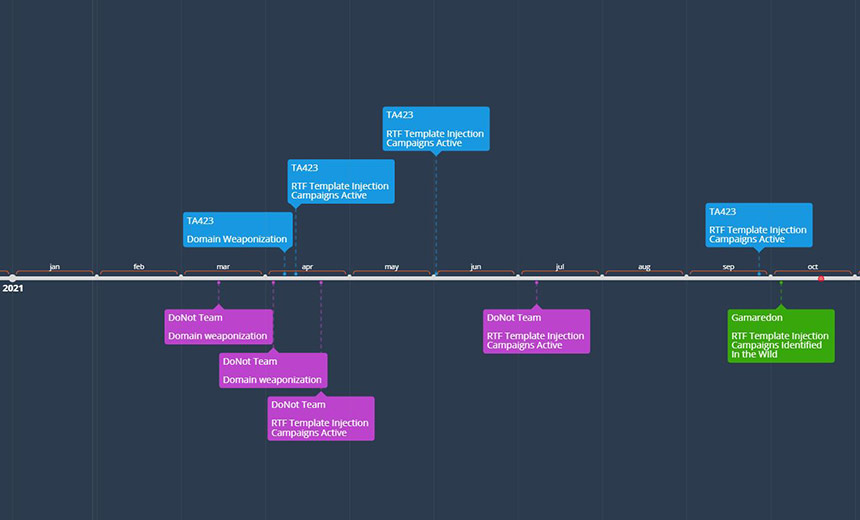
"When an RTF Remote Template Injection file is opened using Microsoft Word,
the application will retrieve the resource from the specified URL before
proceeding to display the lure content of the file. This technique is
successful despite the inserted URL not being a valid document template
file," Raggi says. Researchers demonstrated a process in which the RTF file
was weaponized to retrieve the documentation page for RTF version from a URL
at the time the file is opened. "The technique is also valid in the .rtf
file extension format, however a message is displayed when opened in Word
which indicates that the content of the specified URL is being downloaded
and in some instances an error message is displayed in which the application
specifies that an invalid document template was utilized prior to then
displaying the lure content within the file," Raggi says. The weaponization
part of the RTF file is made possible by creating or altering an existing
RTF file’s document property bytes using a hex editor, which is a computer
program that allows for manipulation of the fundamental binary data.
A blockchain connected motorbike: what Web 3.0 means for mobility and why you should care

We’ve been hearing about the potential of Web 3.0 for years – a
decentralized web where information is distributed across nodes, making it
more resistant to shutdowns and censorship. Specifically, its foundation
lies in edge computing, artificial intelligence, and decentralized data
networks. But what we haven’t talked enough about, is the massive impact Web
3.0 will have on mobility. Web 3.0 aims to build a new scalable economy
where transactions are powered by blockchain technology, eschewing the need
for a central intermediary or platform. And in the mobility space, there are
lots of things happening. ... Pave Bikes connect to a private blockchain
network. When you get your bike, you receive a non-fungible token (NFT).
This is effectively a private key or token-based on ERC721. It is used to
unlock the ebike via the Pave+ App. To be exact, the Pave mobile app is
technically a dApp, a decentralized application connected to the blockchain.
It enables riders to securely authenticate their proof of purchase and
access their bike using Bluetooth, even without an internet connection.
Open banking will continue its exponential rise in the UK in 2022

Over the next year and beyond, it will be interesting to see how Variable
Recurring Payments (VRPs) will continue to develop to allow businesses to
connect to authorised payment providers to make payments on the customer’s
behalf. Direct debits, which is the main mechanism in use today, are
expensive, slow and have a painful, mainly paper-based process today. This
is long overdue for digital transformation. I anticipate 2022 will be the
year we begin to see VRPs in full effect. This will provide countless
opportunities for consumers to find new ways to manage their finances. As
VRPs progress, we will discover that they will do far more than simply
paying bills and will unlock aspects of smart saving, one-click payments,
and control over subscriptions. It will also be important to address
issues that work against the great benefits of open banking in the near
future. The 90-day reauthorisation rule, which requires open banking
providers to re-confirm consent with the customer every 90 days, must be
addressed. This rule currently undermines the principles of convenience
and ease that open banking has been working on showcasing.
Major trends in online identity verification for 2022
As both consumer and investor demand for fintech startups continues to
heat up, we expect to see even more neobanks and cryptocurrency investment
platforms launching in the coming year. Unfortunately, bad actors are
ready and they often target these nascent platforms, with the expectation
that fraud prevention may be an afterthought at launch. But we expect
that, as these startups go to market, these companies will shift their
initial focus from purely optimizing for new user sign-ups to preventing
fraud on their platforms, shifting from the required risk and compliance
checks to more comprehensive anti-fraud solutions. Fortunately, there are
ID verification solutions that can help with both, preventing fraud while
still optimizing for sign-up conversions. Likewise, the tight hiring
market for software developers will lead these new fintech firms to look
for no-code or low-code ID verification and compliance solutions, rather
than attempting to build them in-house.
AI-Based Software Testing: The Future of Test Automation

The success of digital technologies, and by their extension, businesses,
is underpinned by the optimal performance of the software systems that
form the core of operations in these enterprises. Many times, such
enterprises make a trade-off between delivering a superior user experience
and a faster time to market. As a consequence, the quality of the software
systems often suffers from inadequacies, and enterprises cannot make much
of their early ingress into the market. This results in the loss of
revenue and brand value for such enterprises. The alternative is to go for
comprehensive and rigorous software testing to find and fix bugs before
the actual deployment. In fact, methodologies such as Agile and DevOps
have given enterprises the means to achieve both: a superior user
experience and a faster time to market. This is where AI-based automation
comes into play and makes testing accurate, comprehensive, predictive,
cost-effective, and quick. Artificial Intelligence, or AI, has become the
buzzword for anything state-of-the-art or futuristic and is poised to make
our lives more convenient.
Will Automation Fill Gaps Left by the ‘Great Resignation’?
From Lane’s perspective, the main areas DevOps teams should be looking to
automate are continuous integration and continuous delivery (CI/CD), IaC
and AIOps-enabled incident management platforms. “By taking the manual
nature of day-to-day work off of DevOps engineers’ plates, they are freed
to focus on digital transformation,” he said. “The number-one stumbling
block is not starting with process.” Lane noted unless you understand all
the steps in a procedure that you’re trying to automate, it is very
difficult to maximize the power of automation tools. “Much of the process
that is still adhered to today is outdated for the digital age,” he said.
“Spend the time up front to map out what you hope to achieve with an
automation project, what all the touchpoints are and how one can measure
the quality of automation when it’s implemented.” Michaels added that
while the internet is flooded by companies shouting they have the “best”
tools, that proclamation of “best” is going to be determined by budget and
known languages.
Quote for the day:
"Leadership is familiar, but not
well understood." -- Gerald Weinberg
No comments:
Post a Comment